table of Contents
Two, SSH principle of free secret landing
2, the public key of the client to the server configuration
A, SSH Introduction
SSH (Secure Shell) is a communications network an encrypted transmission protocol, can provide a safe environment for the transport network service in an insecure network.
SSHIt is done by creating a secure tunnel in the network SSHconnection between the client and the server. Any network services are available through the SSHsecure transmission, SSHthe most common use of remote login system, people often use SSHto transmit the command line interface and remote execution of commands.
Encryption algorithms include: RSA, DSA and so on.
RSA: asymmetric encryption algorithm, based security extremely difficult decomposition of large integers (the product of two prime numbers);
the DSA: is an asymmetric encryption algorithm, based security integer finite field discrete logarithm problem;
scp Transfer files
scp(secure copy)Is linuxthe system based on sshremote login file for secure copy command.
# 传递文件到远程
scp local_file remote_username@remote_ip:remote_file
# 传递文件夹到远程
scp -r local_folder remote_username@remote_ip:remote_folder
# 复制远程文件到本地,只是调换下文件参数位置即可
scp remote_username@remote_ip:remote_file local_fileRemote Copy command therersync,scpless consumption of resources, system load will not improve much , at this point,rsyncit is far less than it.rsyncThan thescpnext will be a little faster, but smaller file more cases,rsyncwill lead to the hard diskI/Ois very high, andscpbasically does not affect the normal use of the system.
And scpsimilar command cp, but cpcan only copy the machine can not be cross-server, it is necessary to sshconstitute a cooperation scpcommand.
We direct use scpto copy files across machines, you will be prompted to enter the password:
# 提示输入server端服务器的work用户密码
[[email protected] ~]$ scp test.php [email protected]:/home/work
[email protected]'s password: The reason is that, scpit is to use sshthe machines connected to the server, and then performs remote copy using the network (cp).
You can refer to the sshprocess:
# 同样的提示输入server端服务器的work用户密码
[[email protected] ~]$ ssh [email protected]
[email protected]'s password: To avoid scp each time to enter your username and password, you can log in via ssh avoid dense resolved.
Two, SSH principle of free secret landing
Three, SSH-free dense landing
Server environment:
| machine | username | password |
|---|---|---|
| 192.168.26.134 master | root | 123456 |
| 192.168.26.131 slave1 | test2 | 123456 |
| 192.168.26.133 slave2 | test4 | 123456 |
1, generates a key
Respectively 192.168.26.131,192.168.26.133,192.168.26.134 machine user's home directory (/ home / username /) down, execute the following commands, encrypted by the RSA algorithm, then you are prompted to enter directly enter without typing anything:
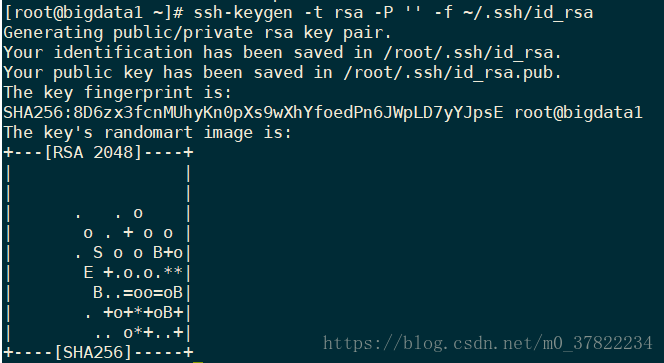
ssh-keygen -t rsa
Will be hidden directory under the home directory /.sshgenerated files:
id_rsa.pub //公钥
id_rsa //密钥
Generate a public key, the private key can directly execute the following commands:
ssh-keygen -t rsa -P '' -f ~/.ssh/id_rsa
Parameters:
-t type of encryption algorithm, is used herein rsa algorithm
-P specified for the private key, may not be not required to specify
-f specify the secret key generation holding position
2, the public key of the client to the server configuration
method one:
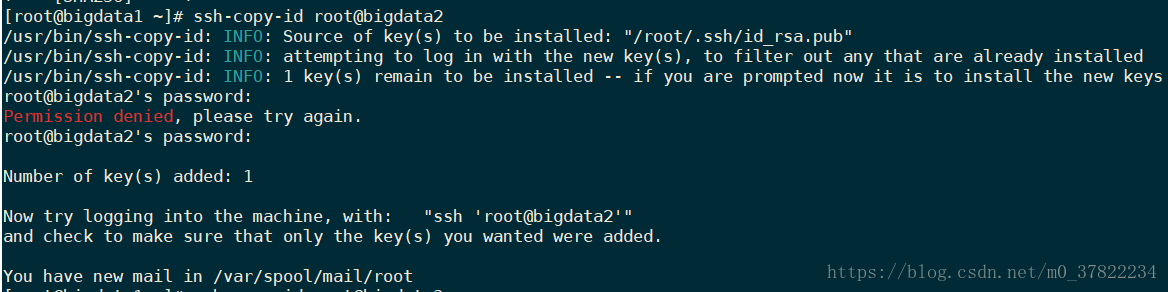
Slave1 client sends a public key server master, use ssh-copy-id
ssh-copy-id [email protected] test2 the command to enter the password to complete the copy of the public key.
NOTE: After ssh-copy-id will receive a public key of the server is added to the server public key corresponding to the user's $ HOME / .ssh / authorized_keys file.
Method Two:
1, additional public
192.168.26.134 on the machine, the id_rsa.pubcontents of written authorized_keysdocuments
cat id_rsa.pub >> authorized_keys
2, sending the other server's public key
Slave1 on the machine, the id_rsa.pubcopy machine to the master /.sshdirectory and rename the place id_rsa.pub.slave1:
scp id_rsa.pub hadoop@master:/home/hadoop/.ssh/id_rsa.pub.slave1
Slave2 on the machine, the id_rsa.pubcopy machine to the master /.sshdirectory and rename the place id_rsa.pub.slave2:
scp id_rsa.pub hadoop@master:/home/hadoop/.ssh/id_rsa.pub.slave2
3, adding other server's public key
On the master machine, the /.sshdirectory will see a file sent from slave1, slave2 over:
id_rsa.pub.slave1
id_rsa.pub.slave2
Append the two public key is written to the master machine /.sshin the directory authorized_keysin which:
cat id_rsa.pub.slave1 >> authorized_keys
cat id_rsa.pub.slave2 >> authorized_keys
4, confirm the contents of the public key
On the master machine, view the authorized_keyscontents of the file, be sure to include slave1, two public content slave2 machine:
cat authorized_keys
5, modify authorized_keys file permissions
Respectively on the master, slave1, slave2 machine to perform, to auhorized_keysmodify permissions, otherwise it will not achieve free Password:
chmod 600 authorized_keys
6, SSH landing test
On the master machine, the master machine to log in via ssh slave1, the first time a password is required to log on without a password after exiting later, other machines similar to these:
//登陆slave1
ssh slave1
//登陆后退出
exit
//重新登陆
ssh slave13、known_hosts
You will each ssh public key (public key) you visited are recorded in the computer's ~ / .ssh / known_hosts. The next time access to the same computer, OpenSSH will verify the public key. If the key is different, OpenSSH will warn you to avoid being attacked DNS Hijack like.
Method of avoiding the warning:
1. Manually delete the content known_hsots inside;
2. modify the configuration file "~ / .ssh / config", add these two lines, restart the server.
NO StrictHostKeyChecking
UserKnownHostsFile / dev / null
Advantages and disadvantages:
1. The need to manually delete every file contents, some automated scripts can not run (failed landing in SSH), but safe;
ignore known_hsots 2. SSH access when landing, but security is low;