
Part1 Preface
Due to some errors in the previous article, the original article ABC_123 has been deleted. The article was corrected and republished last weekend.
Hello everyone, my name is ABC_123 . I previously wrote an article titled "The Most Serious APT Supply Chain Attack in History, Flow Chart Analysis and Analysis of Attacking Europe and the United States with Solarwinds (Part 1)" and the response was pretty good. Since this APT supply chain attack is extremely complex, approximately 5 to 6 articles will need to be written . This issue continues to share the second article, describing the design ideas of the Sunburst backdoor used in it, and how it bypasses traffic detection.
ABC_123 summarizes a large number of analysis articles on the Internet, excludes binary analysis content that most people cannot understand, and strives to use the most understandable language to let everyone understand the design ideas of this top backdoor and bring inspiration to everyone's offense and defense. I believe that after reading the article, everyone will intuitively experience how powerful the backdoor designed by the top APT organization is.
It is recommended that everyone set the public account "Xitan Laboratory" as a star, otherwise you may not see it! Because official accounts can now display large image push only for frequently read and starred official accounts. How to operate: Click [...] in the upper right corner, and then click [Set as Star].

Part2 Sunburst backdoor review
Sunburst design ideas and workflow chart
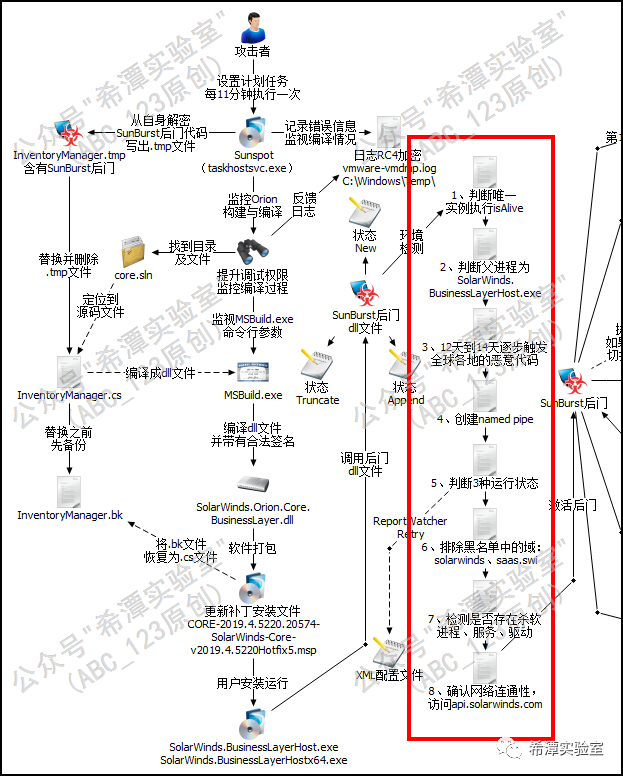
As usual, we will first release a picture of the design ideas and flow chart of the Sunburst backdoor in the Solarwinds supply chain attack drawn by ABC_123, which is summarized from a large number of Sunburst backdoor sample analysis articles. Next, based on this picture, the entire process will be explained in detail. Backdoor working process.
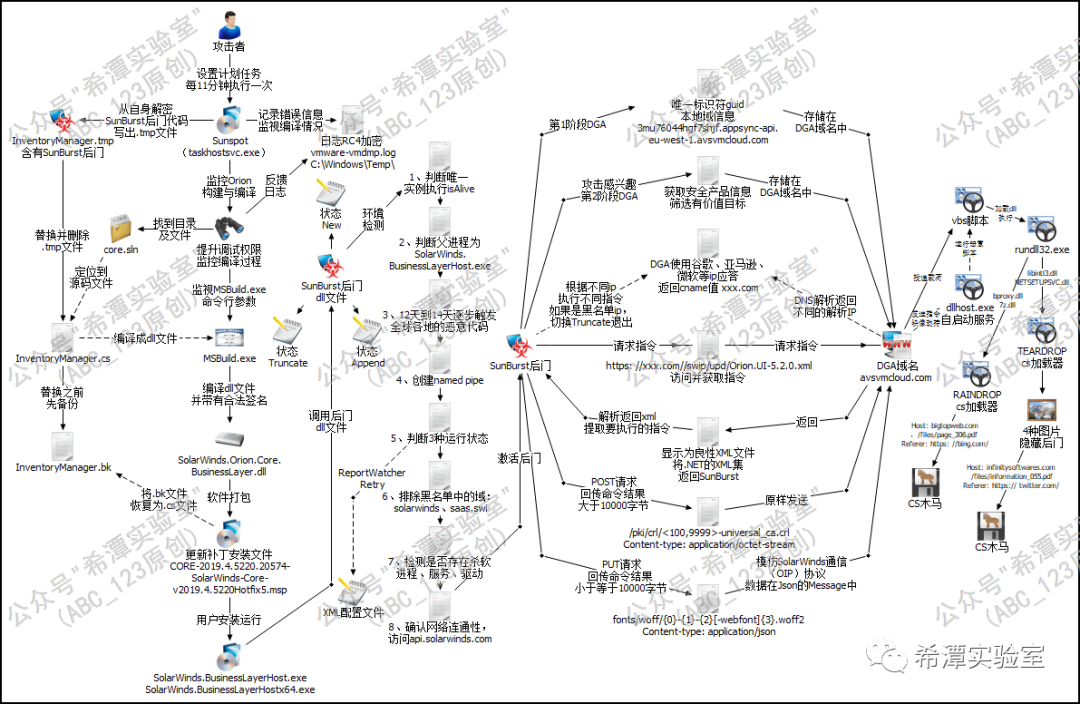
How the Sunburst backdoor is compiled into the Orion software is described in detail in the previous article, so I will not describe it here . Sunburst carries the legal Solarwinds legal digital signature, which has a built-in whitelist effect and perfectly bypasses various protection measures. Finally, the dll file was packaged in the update patch of Orion network management software. Once the victim installs this patch, it will cause the Sunburst backdoor to be triggered. However, it does not run immediately. It will go through a series of complex initialization conditions to determine whether it is in the real environment. Running in the victim's computer environment, whether there is anti-virus protection, whether the parent process is reasonable, etc.
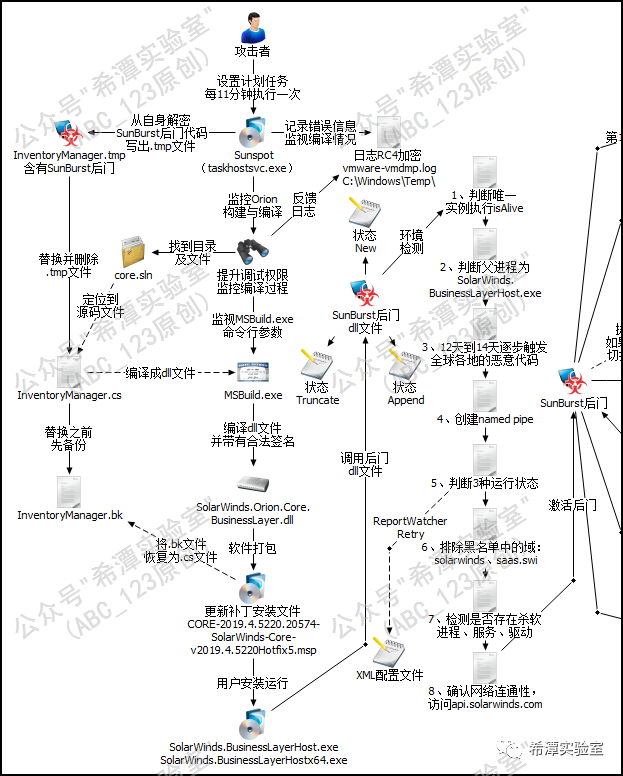
Three states of Sunburst backdoor
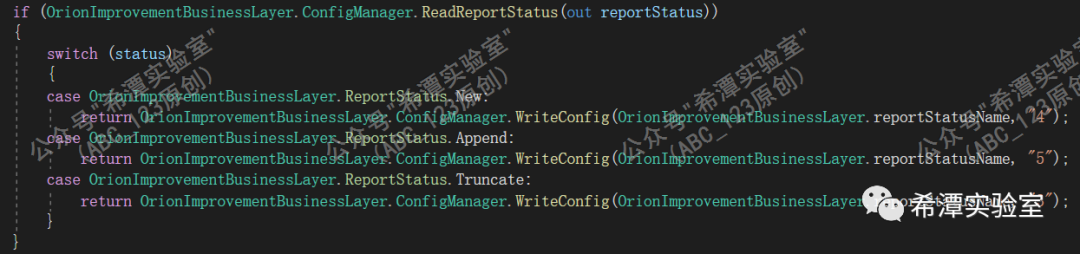
The Sunburst backdoor will read the value of ReportWatcherRetry from the XML configuration file in Solarwinds' Orion software to determine whether to continue running. It will only continue to run if its value is not 3.
The ReportWatcherRetry value of the XML configuration file will return three values: 3, 4, and 5, which correspond to the three persistence states of Truncate, New, and Append respectively . The default value is 4 (New). 4 (New) indicates that the backdoor is running for the first time, 5 (Append) indicates that the backdoor has been running on the system before, but exited due to predetermined conditions (such as active anti-virus software), and 3 (Truncate) means that the backdoor should be run immediately Stop running.
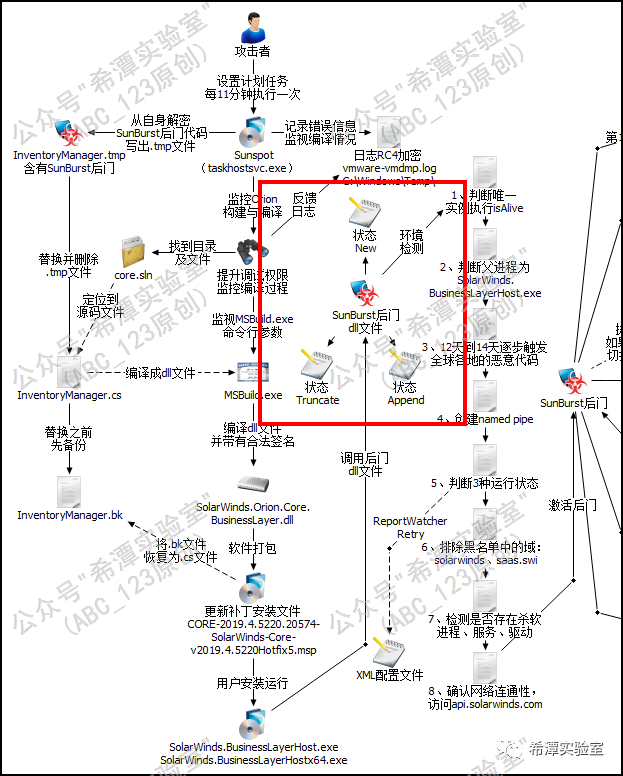
Part3 8 necessary conditions for backdoor triggering
Note: During the execution condition judgment phase, the Sunburst backdoor will frequently use the OrionImprovementBusinessLayer.DelayMin() method to randomly sleep/delay for 30-120 minutes to delay the code execution speed, which can reduce the probability of being discovered by automated analysis and protection software.
1 Determine the execution of the only instance
Determine through the isAlive method in the C# code.
2 Determine the parent process
By calculating the hash value of the parent process name, it is determined whether the running process is SolarWinds.BusinessLayerHost.exe or SolarWinds.BusinessLayerHostx64.exe, and the hash algorithm is customized. This step is to avoid sandbox detection or debugging tools, and avoid automated sandbox detection or analysis by security personnel.
3 Wait for 10 days before running
Randomly set the backdoor activation time and wait for 12 to 14 days to gradually trigger the malicious code. The purpose of this is to gradually bring the controlled servers of more than 18,000 Orion software users around the world online to avoid centralized online detection and alarms by traffic monitoring equipment , which will lead to the plan being exposed. Many units will clear logs after 7, so sufficient waiting time can also reduce log records.
4Create named pipes to prevent multiple instances from running
The backdoor creates a named pipe named 583da945-62af-10e8-4902-a8f205c72b2e and places multiple examples to run.
5 Check configuration file status parameters
Check the value of the XML configuration item ReportWatcherRetry to determine the current state of the Sunburst backdoor. If it is in the New or Append state, continue running.
6 Local domain name blacklist check
1. Obtain the AD domain and use Hash and regular expressions to determine whether it is a value in the blacklist, such as swdev.local, swdev.dmz, saas.swi, etc., where swi corresponds to "SolarWInds Internal" and swdev corresponds to "SolarWinds Develop". 2. Cannot contain the solarwinds keyword. 3. The domain name must not match the regular expression (?i)([^az]|^)(test)([^az]|$). Simply put, it cannot look like a test environment domain name.
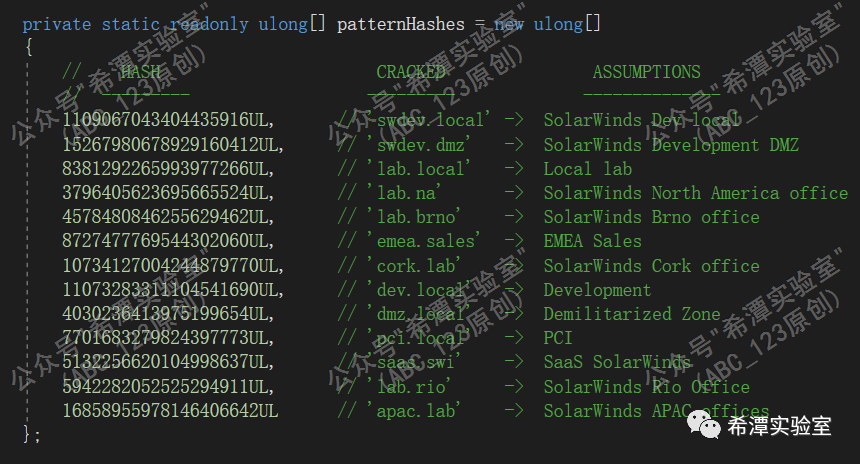
7 Detect whether there are anti-software processes, services, and drivers
1. Process blacklist check
Use the SearchAssemblies method to check whether there is a process blacklist, and check whether there are processes such as Windbg, Winhex, Autoruns, Wireshark, dnSpy, apimonitor-x64, fiddler, idaq64, ollydbg, procdump64, x64dbg, etc.
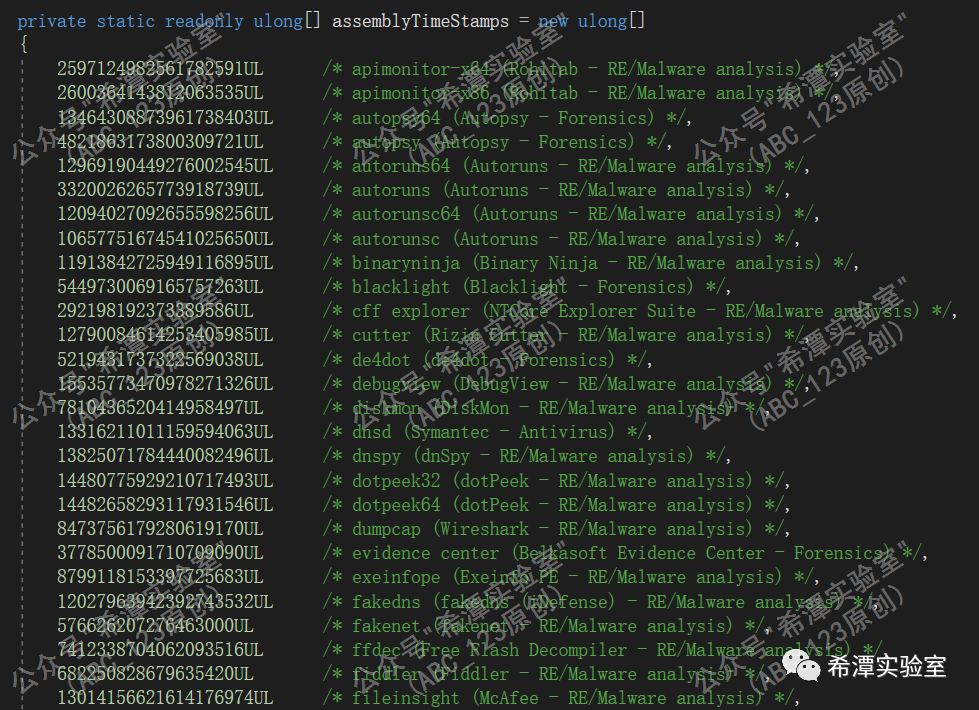
2. Service blacklist check
Use the SearchServices method to detect whether there are blacklist service names, such as Windows Defender, Carbon Black, Crowdstrike Falcon, FireEye - EDR, etc. If a blacklisted service is encountered, Sunburst will disable the service by modifying the registry.
3. Security software driver blacklist check
Call WMI query through the SearchConfigurations method, Select * From Win32_SystemDriver to detect whether there is a driver blacklist, such as groundling32.sys, etc.
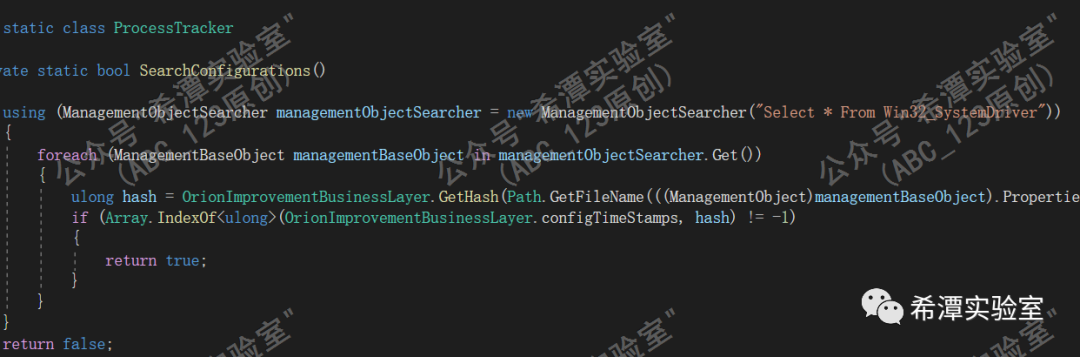
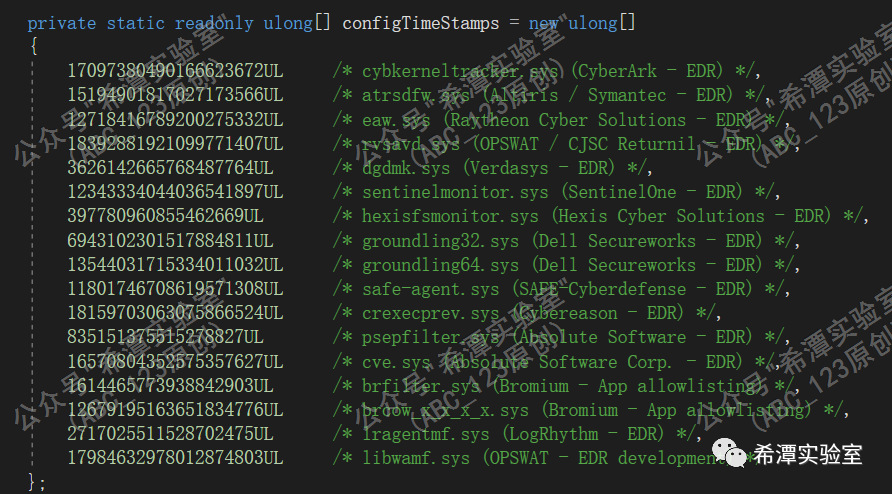
8 Confirm network connectivity
Use the CheckServerConnection method to parse the api.solarwinds.com domain name and perform network connectivity testing. Only if it passes the test will it be executed further, otherwise it will exit and wait for the next execution.
Part4 Backdoor DGA domain name communication stage
Prerequisite knowledge of dga domain name communication stage
1 Overview of dga domain name communication stage
After the above environment tests are passed, the Sunburst backdoor will enter the DNS communication stage using the dga domain name. DGA domain name communication includes two stages: the first stage mainly feeds back the computer domain name information to the attacker C2, so that the attacker can filter targets based on this information; the second stage mainly feeds back the status information of the security protection software, so that the attacker can understand the target anti-virus software. , edr and other deployment situations. This information is encrypted and hidden in the first segment of the DGA domain name. Based on the computer domain name information and security protection software information collected by the Sunburst backdoor, the Sunburst backdoor attackers selected about 100 valuable targets for intranet lateralization.
2 unique identifier userid
The basic information of some victims' computers is too large (for example, the computer domain name is too long), and it is necessary to send multiple DGA domain name requests to completely transmit the computer domain name information. In order to distinguish dga domain name requests from different computers, Sunburst will decrypt and combine the segmented information of dga domain names from the same computer together. Sunburst will calculate a unique identifier userid for each computer.
For each infected computer, userid consists of the victim's MAC address, windows domain name, and windows computer unique identifier GUID (that is, the registry value randomly generated during Windows installation and stored in HKLM\SOFTWARE\Microsoft\Cryptography\MachineGuid). The unique userid is calculated from the 3 values through a custom encryption algorithm.
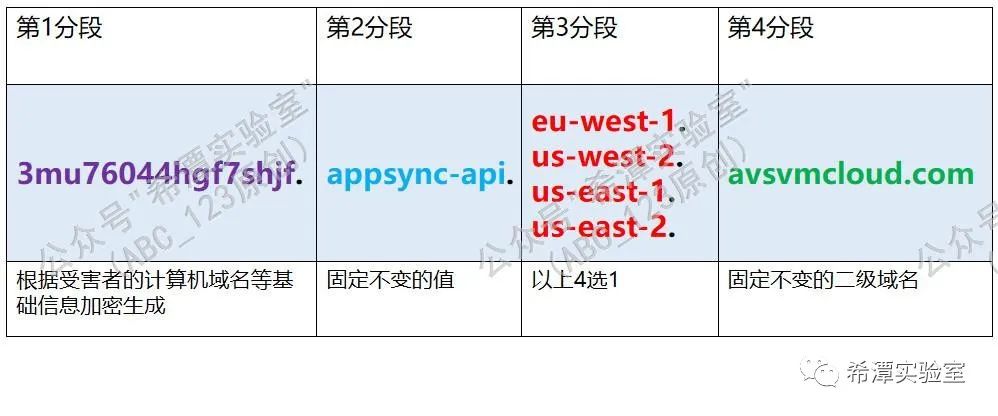
3 Backdoor DGA domain name generation format
The dga domain name used by Sunburst has been handled very cleverly. The general format is as follows:
*.appsync-api.eu-west-1.avsvmcloud.com (* represents the subdomain name of DGA)
*.appsync-api.us-west-2.avsvmcloud.com (* represents the subdomain name of DGA)
*.appsync-api.us-east-1.avsvmcloud.com (* represents the subdomain name of DGA)
*.appsync-api.us-east-2.avsvmcloud.com (* represents the subdomain name of DGA)
Among them, the three segments on the right side of each DGA domain name come from hard-coded strings in the backdoor program, and the asterisk part of the first segment of the DGA domain name is dynamically generated based on the computer domain name and other information in the victim server. The following is an example of a domain name generation algorithm in the DGA stage.
DGA domain name communication stage of the backdoor
1 Phase 1 DGA Domain Name Communication
At this stage, Sunburst's main task is to put the victim's computer domain name into the DGA domain name after several layers of encryption, and then pass it back to C2. If the domain name of some computers is too long, the Sunburst backdoor will split the information, send 14 characters each time, and send multiple DNS requests to complete the information transmission. If the attacker is interested in this computer domain name, he will enter the second stage of DGA domain name communication , and then the Sunburst backdoor will be activated and change to the "Append" state.
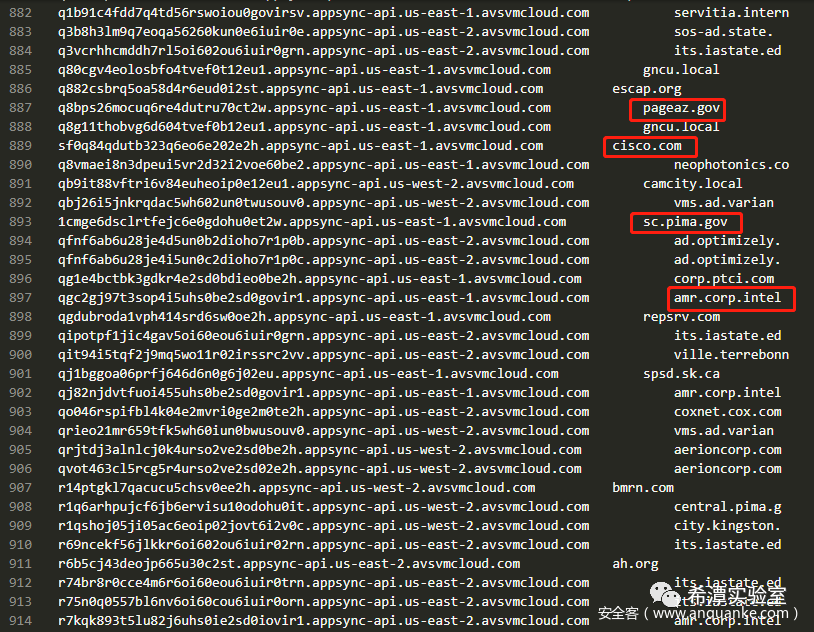
As shown in the figure below, these are the traffic samples of the dga domain name of Sunburst's dga domain name communication in the first stage captured from the traffic. The second column is the decrypted victim domain name collected by Sunburst. The attacker uses the decrypted domain name information to determine whether the target victim unit is valuable . By decoding and analyzing these domain names, we found that many technology companies, including Cisco and Intel, as well as many universities and government agencies in the United States are suspected to be victims of this attack.
2 Phase 2 DGA Domain Name Communication
At this stage, the Sunburst backdoor mainly completes the transmission of the antivirus protection status information of the victim's computer to the C2 server. When the Sunburst backdoor status is Append (activated), the second phase of the DGA domain name begins. The generated DGA domain name will include the computer's unique identifier and the security product test status information of the built-in service blacklist (including whether it exists and whether it is still running). , whether it has been closed, etc.) and whether the communication with the last DNS C2 phase was successful.
3 IP address used as command trigger to bypass traffic monitoring
When we usually query DNS, for example, when accessing google.com, the domain name will be converted to 142.250.*.*, and the IP address is stored in the A record. The Sunburst backdoor will also parse the C2 domain name to obtain IP addresses,
but the purpose of Sunburst is not to use these IP addresses for communication, but to trigger different malicious operations based on the IP addresses in different IP segments resolved by the C2 domain name. This is very clever and
very Concealed command and control form, difficult to detect by traffic monitoring equipment.
The attacker controls the resolution IP address range of the C2 domain name to belong to IP addresses in the Google, Amazon, and Microsoft segments, rather than randomly selecting IP addresses to trigger different behaviors. This is to reduce the chance of detection. Again, malware does not communicate with these IP addresses.
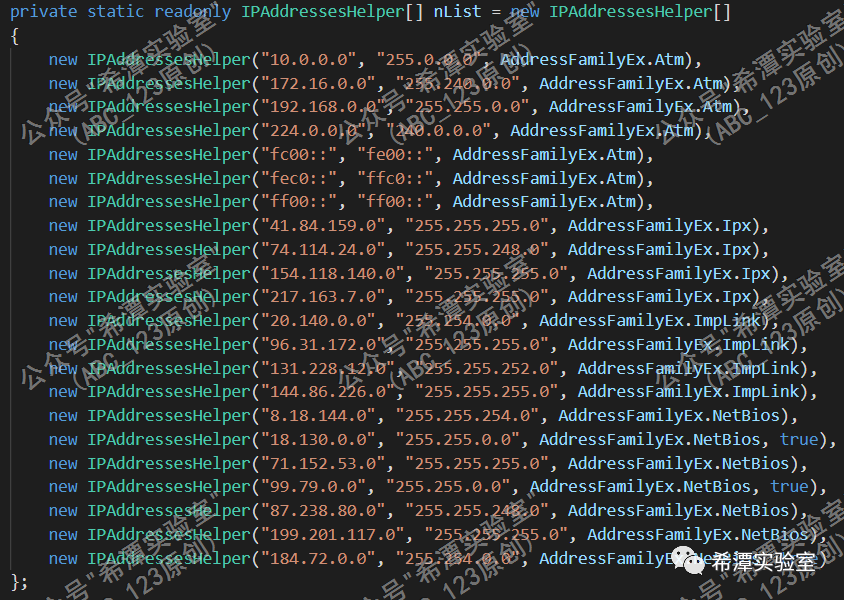
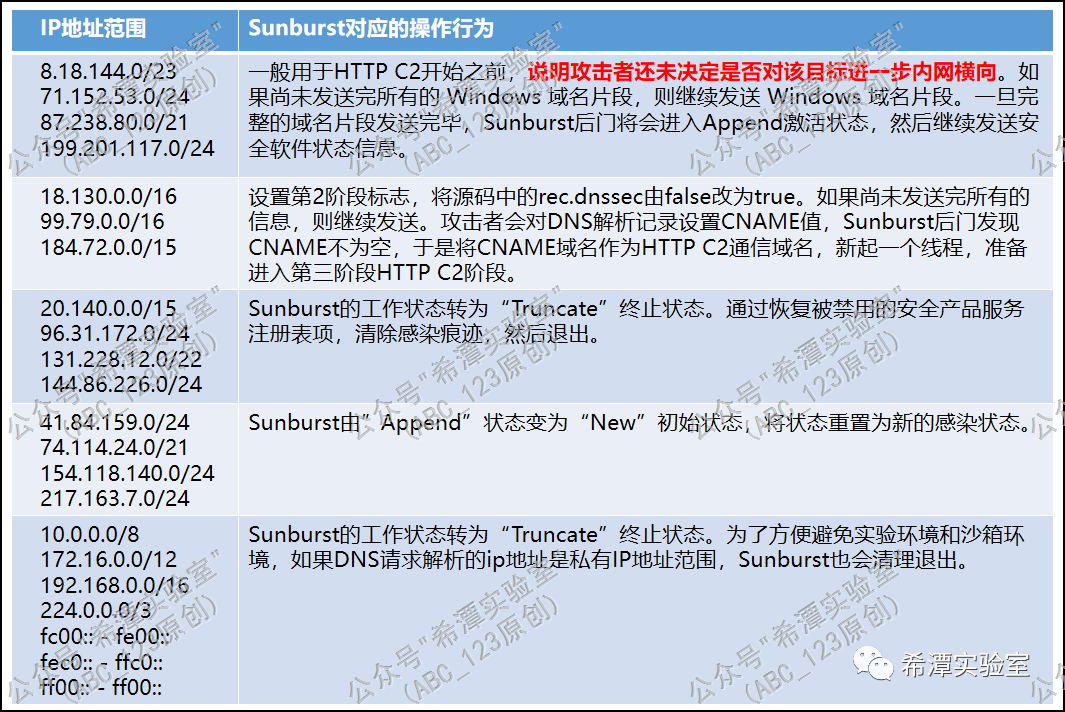
As shown in the figure above, Sunburst developers define the IP address in an AddressFamilyEx structure. Sunburst will trigger different malicious behaviors based on different IP addresses returned by DNS resolution . By reading the C# code of the Sunburst backdoor, we found that based on C2 resolving domain names to different categories of IP addresses, the Sunburst backdoor will perform about 5 major types of operations:
1. Continue to send the untransmitted domain name fragment information; 2. Send the status information of the security protection product of the target computer; 3. Execute the C2 channel in the second stage; 4. Clean up and exit; 5. Reset to the initial state, and then Like the first execution.
Finally, a general picture is given:
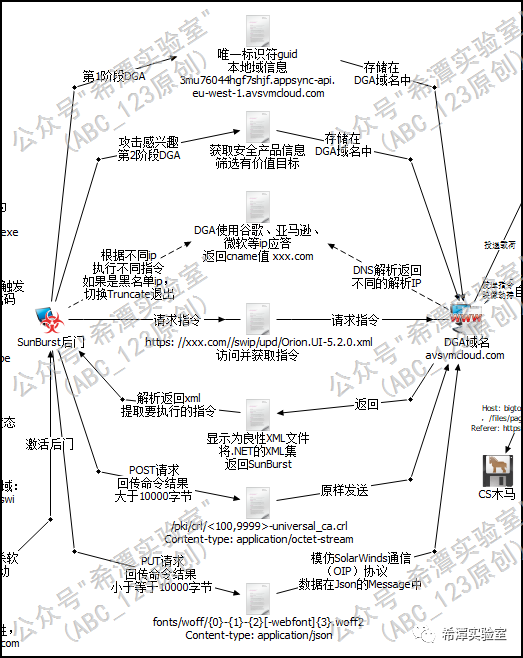
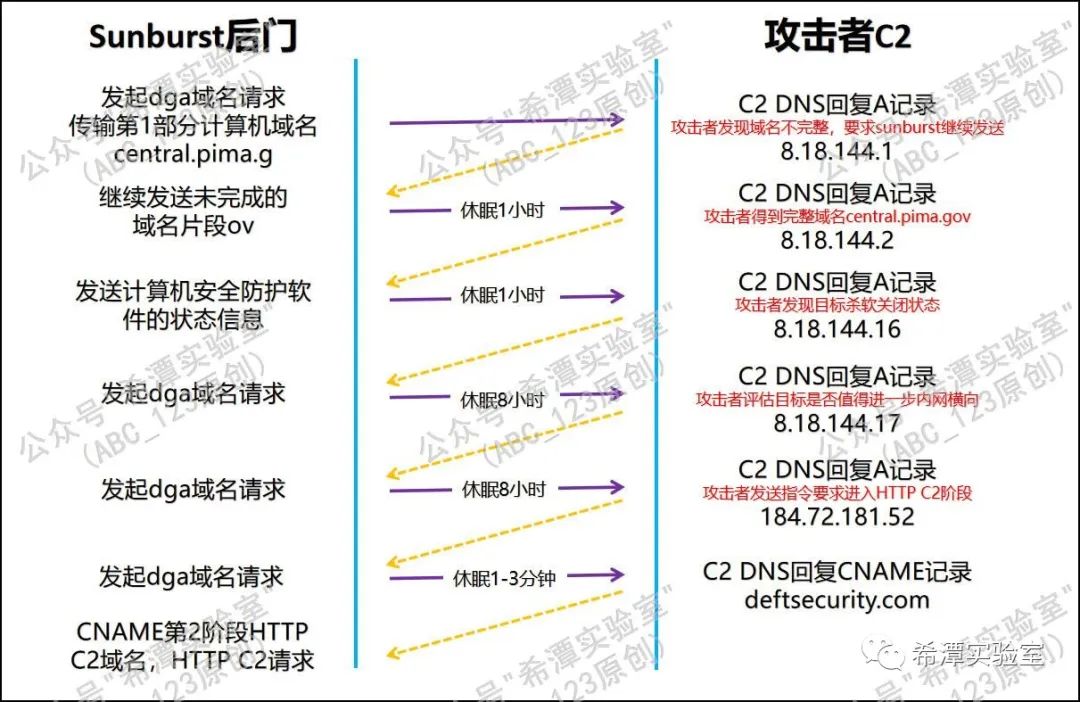
4 C2 controls domain name resolution IP and indirectly controls Sunburst flow chart
Next, ABC_123 produced a flow chart that demonstrated the entire process of how the C2 end controlled the Sunburst backdoor behavior by controlling the resolution of the DGA domain name to different IPs during the actual combat process. Since the communication process is very complicated, ABC_123 will write a special article to explain the whole process in detail .
Part5 HTTP C2 communication stage (obtain attack instructions and execute them)
Through the DGA domain name communication in the previous two stages, the attacker selected valuable targets, and the Sunburst backdoor entered the next stage: the HTTP C2 communication stage. At this stage, there will be a CNAME record in the DNS return data, and the Sunburt backdoor will use this domain name for HTTP C2 communication .
At this stage, Sunburst will start a new thread to execute the HttpHelper.Initialize method in order to process the HTTP C2 communication phase request, receive and execute the instructions sent by the attacker, and then encrypt the instruction execution results and mix them with normal traffic. The packet is fed back to the attacker's C2 server. The attacker who developed the Sunburst backdoor designed an extremely clever traffic encryption method at this stage in order to monitor traffic. Next, ABC_123 will explain it in detail to open your eyes.
First, three different URL access forms of the Sunburst backdoor in the HTTP C2 communication phase are posted, corresponding to three situations:
1. Sunburst will continuously access the .xml URL and actively obtain instructions from the C2 side. The URL format is as follows:
hxxps://3mu76044hgf7shjf.appsync-api.eu-west-1.avsvmcloud.com/swip/upd/Orion.Wireless.xml
2. Sunburst returns the instruction execution result to the C2 end. When the data is greater than 10,000, the URL format is as follows:
hxxps://3mu76044hgf7shjf.appsync-ap.us-east-2.avsvmcloud.com/pki/crl/492-ca.crl
3. Sunburst returns the instruction execution result to the C2 end. When the data is less than or equal to 10,000, the URL format is as follows:
hxxps://3mu76044hgf7shjf.appsync-api.us-east-1.avsvmcloud.com/fonts/woff/6047-freefont-ExtraBold.woff2
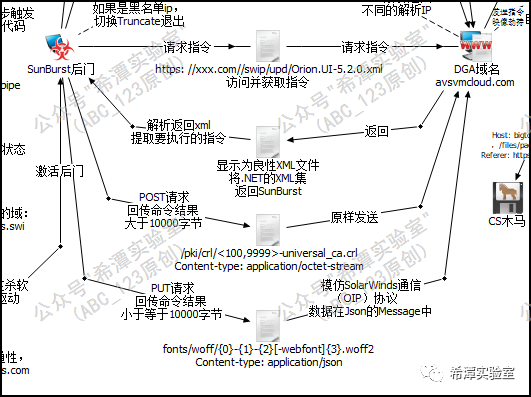
Next, we will explain the three processes in which the Sunburst backdoor obtains C2 instructions and executes them, and then sends the execution results back to the C2 side.
1 Sunburst accesses the .xml URL to receive instructions
In order to obtain the instructions sent by the attacker, the Sunburst backdoor will continuously initiate http GET requests to access the URL ending in .xml on the C2 side, and after each request, it will sleep for the time set by setTime. These XML files will be disguised as a normal XML file related to a .NET assembly, and the instructions issued by the attacker are hidden in them through various steganography techniques . Sunburst will read the contents of the XML file returned by the C2, and use a unique decryption algorithm to extract the instructions sent by the attacker from the XML file and execute them.
The URL path used by Sunburst to initiate a GET request is random and constructed randomly according to a certain algorithm. This is also done to resist IOCs detection . For the following URL:
hxxps://3mu76044hgf7shjf.appsync-api.eu-west-1.avsvmcloud.com/swip/upd/Orion.Wireless.xml
The Sunburst backdoor changes the URL request mainly in the yellow part: /swip/upd/<random components>.xml. The value selection algorithm of <random components> is relatively complex, and each small segment is randomly selected with different proportions set. It is worth noting that the last digit of the error code is not a random character, but takes a value of 0 or 1, indicating whether the previous command request was successful. Usually 0 indicates success, 1 or other value indicates error, and the .xml suffix is added at the end.
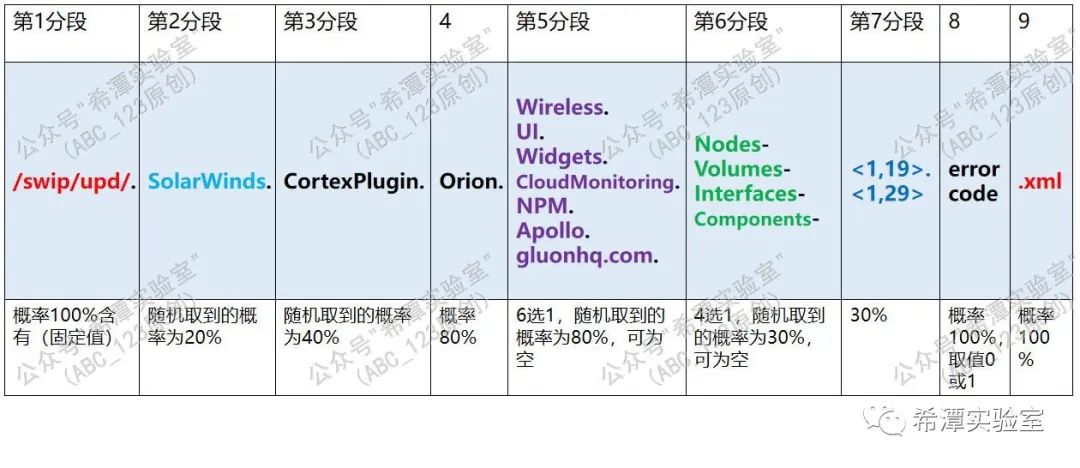
Eventually, Sunburst will randomly construct the following URL based on the algorithm to access the C2 end and obtain the issued instructions:
https[:]//infinitysoftwares.com/swip/upd/SolarWinds.CortexPlugin.Nodes-5.2.1.xml
https[:]//infinitysoftwares.com/swip/upd/Orion.Wireless.UI-3.1.0.xml
https[:]//infinitysoftwares.com/swip/upd/Nodes-1.2.0.xml
For the first 16 requests, a different randomly generated URL path is used each time, but after that it may repeat the previously used randomly generated URL path. At this stage there will be a fixed If-None-Match custom request header, which contains the encrypted previous userId.
As shown in the figure below, this is the XML format content returned by the attacker's C2 server after Sunbrust accesses the GET request for the URL ending in .xml, which encrypts and stores the instructions issued by the attacker:
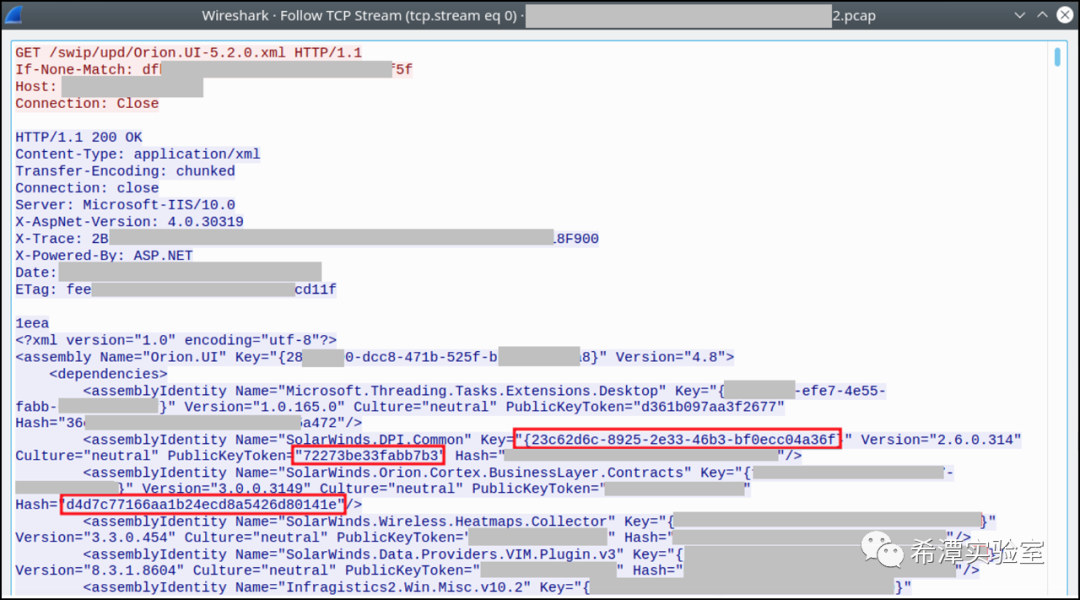
2 Sunburst parses the instructions and executes them
The Sunburst backdoor decrypts and extracts the instructions issued by the attacker from the xml return text, and executes the corresponding instructions through the ExecuteEngine method. It uses the value in JobEngine as a condition to run the command composed of command line parameters . It can be seen from these instructions that the operations performed by the Sunburst backdoor are very limited, which means that if the attacker wants to further expand the results, he must use other tools to perform more complex operations, which is the third stage of the CobaltStrike backdoor.
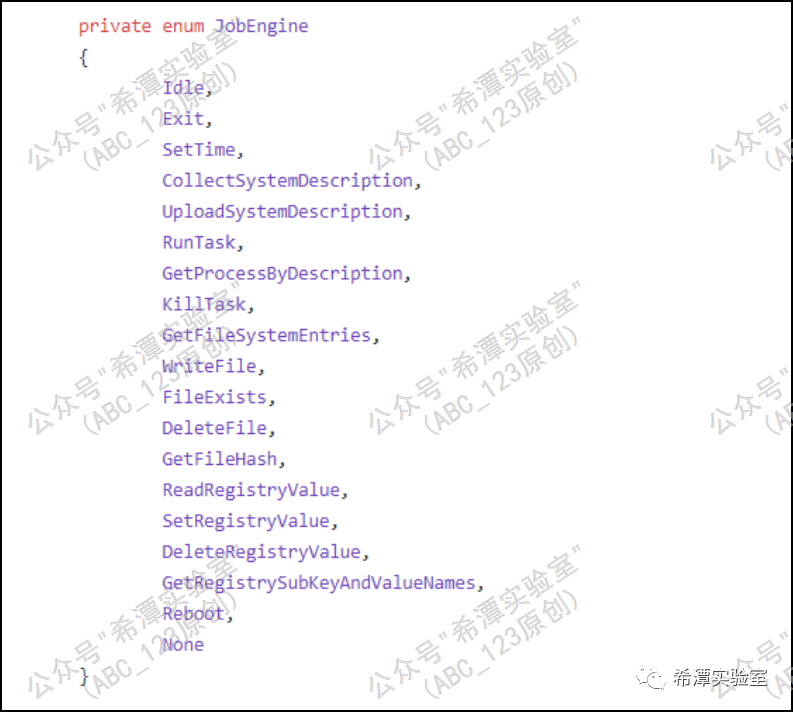
1. When the instruction is parsed as JobEngine.SetTime, set the delay time for each request.
2. When Job.CollectSystemDescription, information will be collected, including computer domain name, Administrator SID, local host name, user name, operating system version information, system path, network adapter status, registered user's company name, registered user name, system version number, system directory, etc.
3. When JobEngine.UploadSystemDescription is used, construct an HTTP request and send the request result to the C2 server.
4. When JobEngine.RunTask is executed, a new process is started based on the given file path and parameters.
5. When JobEngine.GetProcessByDescription is used, the process list is obtained, and the process information is obtained according to the process parameters, including process ID, process name, parent process ID, and user name corresponding to the process.
6. When JobEngine.GetFileSystemEntries, list the file and directory information according to the regular expression in the parameter.
7. When JobEngine.KillTask, Sunburst will kill the process with the specified PID.
8. When JobEngine.SetTime, set the delay seconds. When it is triggered for the second time, if the first set time is less than 300 seconds, a doubled delay will be performed.
9. When JobEngine.FileExists is used, determine whether the specified path exists.
10. When JobEngine.DeleteFile, delete the specified path.
11. Read the value of the registry key when calling JobEngine.ReadRegistryValue.
12. When calling JobEngine.SetRegistryValue, set the name, type, and path of the registry key
13. Delete the registry key when JobEngine.DeleteRegistryValue is used
14. When calling JobEngine.GetRegistrySubKeyAndValueNames, get all specified item names and data
15. When JobEngine.WriteFile, decrypt the incoming base64 string and write it to the file. After writing, the delay function guarantee will be triggered. It can be seen that the attacker is very careful about the file processing process.
16. When JobEngine.Reboot, restart the target computer.
17. When JobEngine.Exit, exit the current thread and wait for it to be loaded and executed next time.
18. The third-stage backdoor program, TEARDROP and RAINDROP, will also be delivered according to the instructions, which are used to load the CobaltStrike backdoor.
3 Sunburst sends the command execution result back to C2
Once the Sunburst backdoor decrypts the instructions issued by the attacker from the XML file, the Sunburst backdoor will execute the instructions and return the results back to the C2 server. During the data return phase, the Sunburst backdoor does not send a GET request. Instead, it chooses to send the command execution result back to the C2 server through a POST request or a PUT request based on the size of the returned data result . Sunburst will disguise the request as a legitimate Solarwinds request link or static resource to confuse security personnel, and mistakenly initially evaluate the http request sent by Sunburst as legitimate traffic.
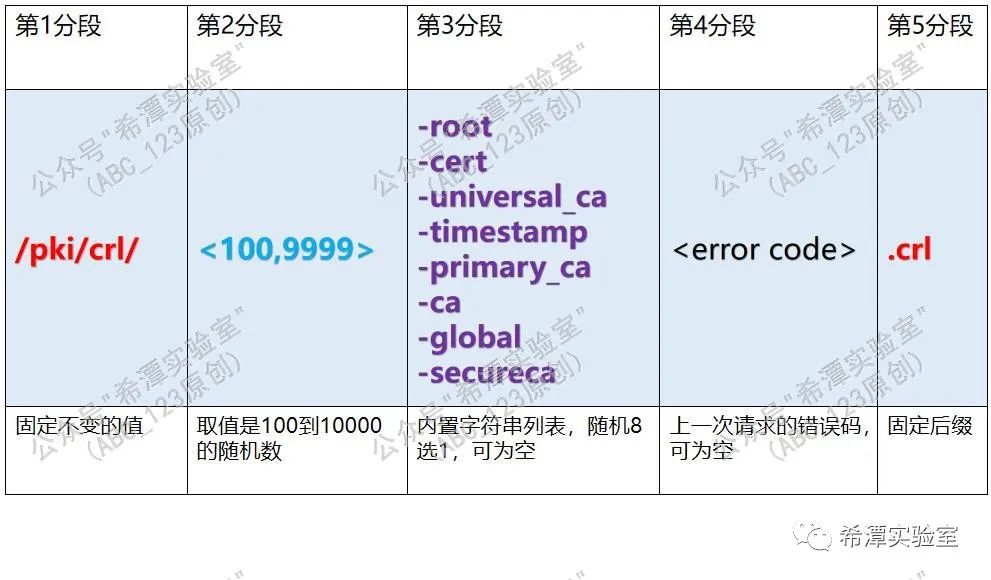
1. When the returned data is greater than 10,000 bytes . Sunburst is sent via POST request. The POST request will set the Content-type field, application/octet-stream. In this case, the URL format is as follows:
hxxps://3mu76044hgf7shjf.appsync-api.us-east-2.avsvmcloud.com/pki/crl/492-ca.crl
The request URI path format is /pki/crl/{2nd segment}{3rd segment}{4th segment}.crl , where {2nd segment} is a random number from 100 to 10000; {3rd segment Section} is a built-in string list, from which one is randomly selected for splicing; {section 4} represents the error code of the last request. In some cases, this value is empty; finally, the .crl suffix is spliced at the end of the URL.
2. When the returned data is less than or equal to 10,000 bytes . Sunburst will send the results of the command execution back to the C2 server through a PUT request. The data returned by the PUT request will be converted into a JSON document similar to the Orion Improvement Plan (OIP) message legally used by Solarwinds. The Message in the json data is the data to be sent. When sending the http request, the request header Content will be set . -type: application/json .
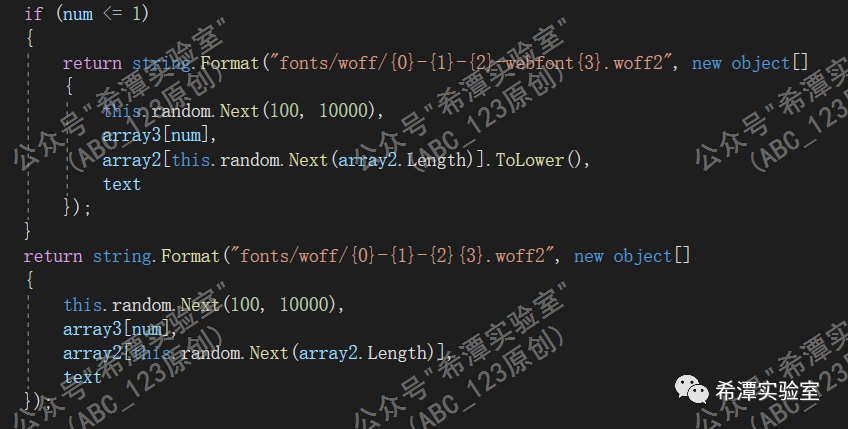
At this stage, the format of the accessed URL is as follows:
hxxps://3mu76044hgf7shjf.appsync-api.us-east-1.avsvmcloud.com/fonts/woff/6047-freefont-ExtraBold.woff2
Among them, the URL format is divided into two situations:
1. /fonts/woff/{paragraph 2}-{paragraph 3}-{paragraph 4}-webfont{paragraph 6}.woff2
{Segment 2} is a random number between 100 and 10,000; {Segment 3} randomly selects one from the built-in list string list; {Segment 4} randomly selects one from the built-in list string list; {Score 6 Segment } represents the error code of the last requested operation.
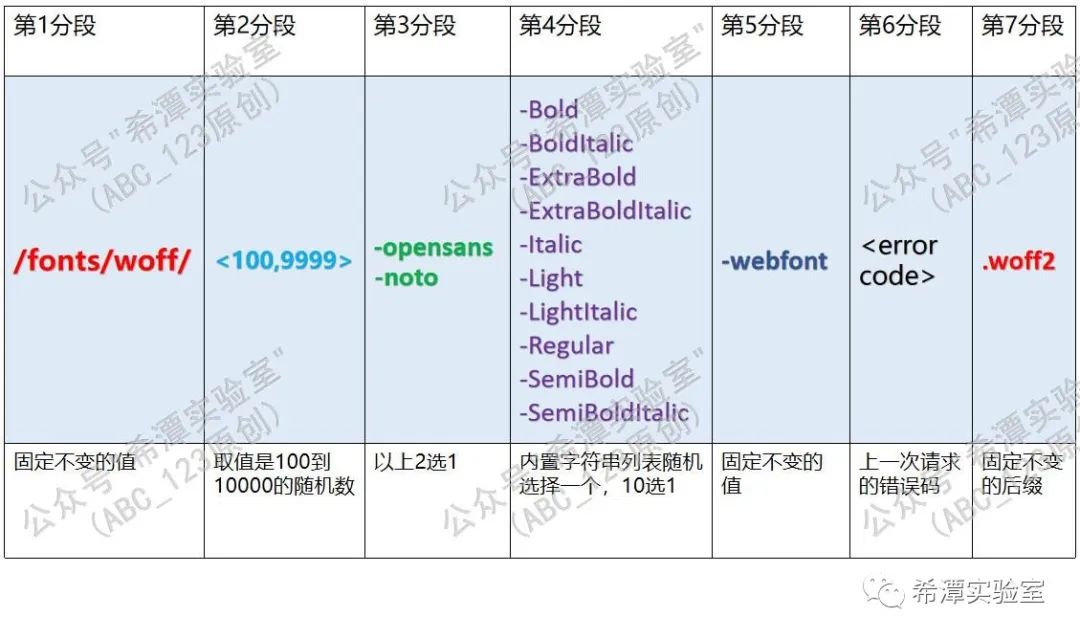
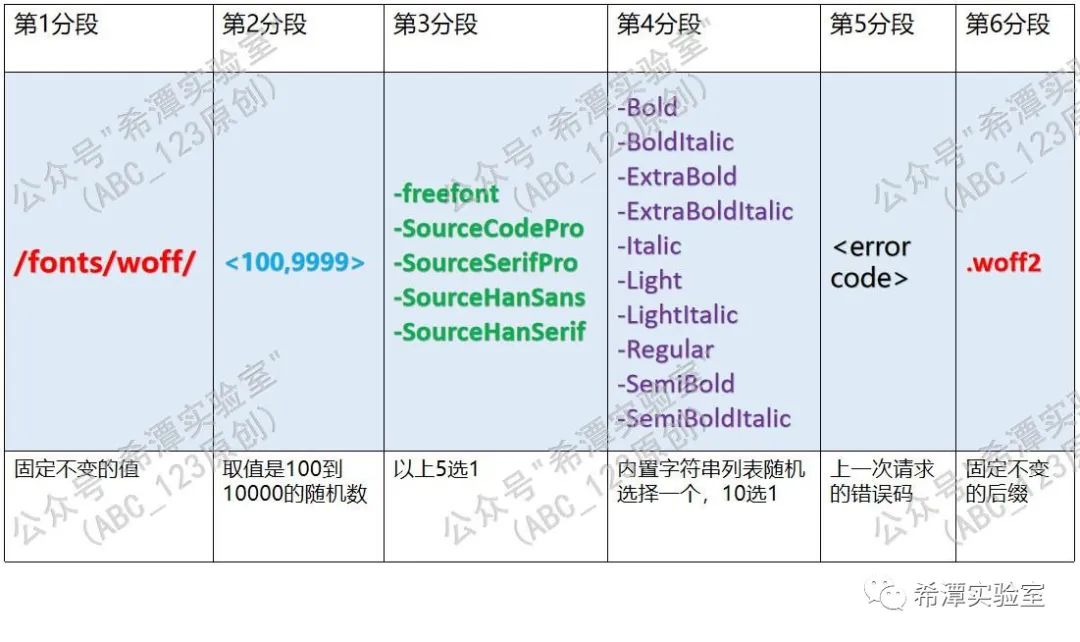
2. /fonts/woff/{paragraph 2}-{paragraph 3}-{paragraph 4}{paragraph 5}.woff2
Where { Second Section} is a random number between 100 and 10,000; {Second Section} selects one randomly from the built-in list string list; {Second Section 4 } randomly selects one from the built-in list string list; { Second Section 5} Segment } represents the error code of the last request.
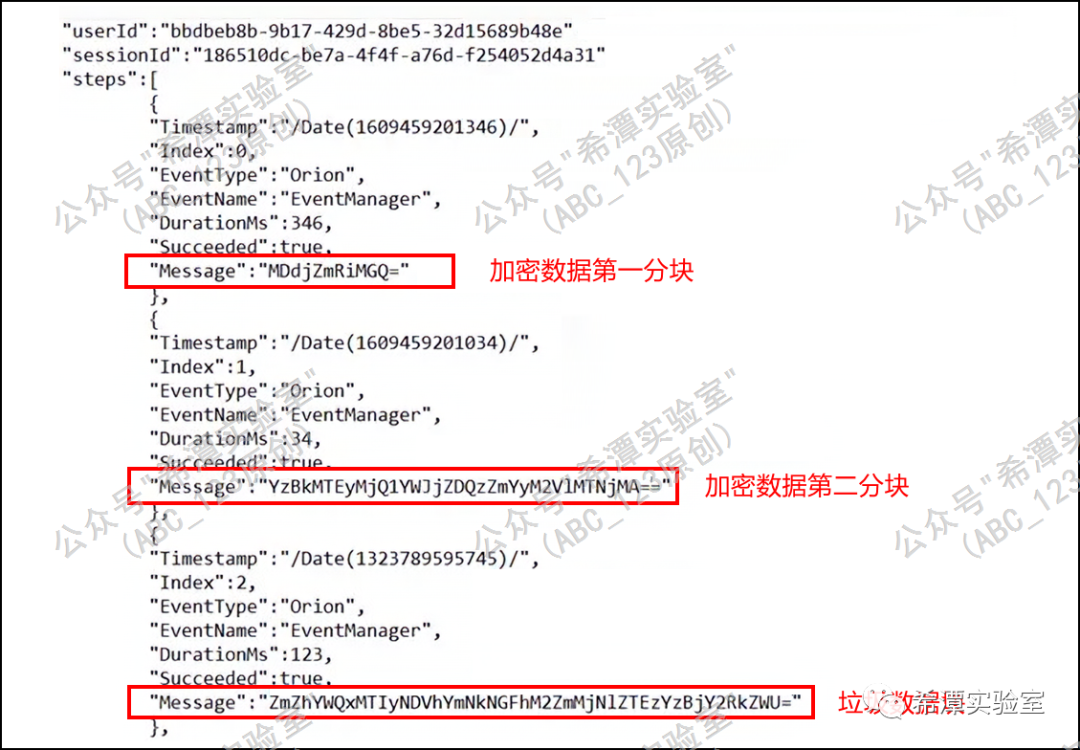
Sunburst hides the instruction execution results in the following POST request packet in JSON format, and then sends it back to the C2 server.
4 Sunburst drops phase 3 weapons
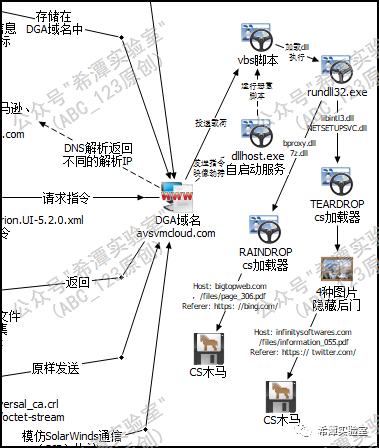
Finally Sunburst will enter the third stage. First, download a vbs script and Loader program, and place them in the C:\Windows\ directory to disguise them as legitimate files. Sunburst then used image hijacking technology to bind dllhost.exe with the wscript.exe C:\Windows\[folder]\[trigger].vbs command by modifying the registry. dllhost.exe is a program that is randomly started under Windows. Next, the attacker will wait quietly for dllhost.exe to execute in order to further execute the vbs script. At this point, the Sunburst backdoor has completed its mission, and subsequent operations will have nothing to do with Sunburst .
Next, the vbs script will perform the following operations: run rundll32.exe, load the malicious dll file from the previous step, clean the image hijacking registry of dllhost.exe, clean up traces, and finally run the Loader program, load the CobaltStrike backdoor, and start lateral operations on the intranet. Regarding the detailed operation of the third stage, ABC_123 will write another article to explain it to you, so stay tuned .
Part6 Summary
1. The Sunburst backdoor must meet the attacker's requirements and the security protection software will continue to execute under the circumstances expected by the attacker. Otherwise, the previous operation of modifying the status of the protection software will be terminated or retried. In this aspect, APT attackers and One of the key differences between ordinary criminals.
2. In order to resist IOCs detection, the author of the Sunburst backdoor designed a clever dga domain name generation algorithm and a random URL path generation algorithm. Moreover, the interval between two dga domain name requests may be as long as a whole day, and the attack process is very covert.
3. During the HTTP C2 communication stage, when Sunburst returns sensitive information from the victim's computer, it encrypts and stores the information in an XML assembly document or a JSON document. Sometimes it also deliberately imitates the communication traffic of the Solarwinds special protocol. This method is used in Difficult to detect in traffic audit.
4. The APT organization indirectly controls the operation of the Sunburst backdoor by resolving the C2 domain name to different IP address segments. This attack behavior is difficult to detect during traffic audit.
5. The attacker writes different numbers 3, 4, and 5 into the XML configuration file of the Orion software, indicating the different states of the Sunburst backdoor. The Sunburst backdoor will read these values and perform different operations. This process is also very covert.

The public account focuses on sharing network security technology, including APT event analysis, red team attack and defense, blue team analysis, penetration testing, code audit, etc. One article per week, 99% original, so stay tuned.
Contact me: 0day123abc#gmail.com(replace # with @)