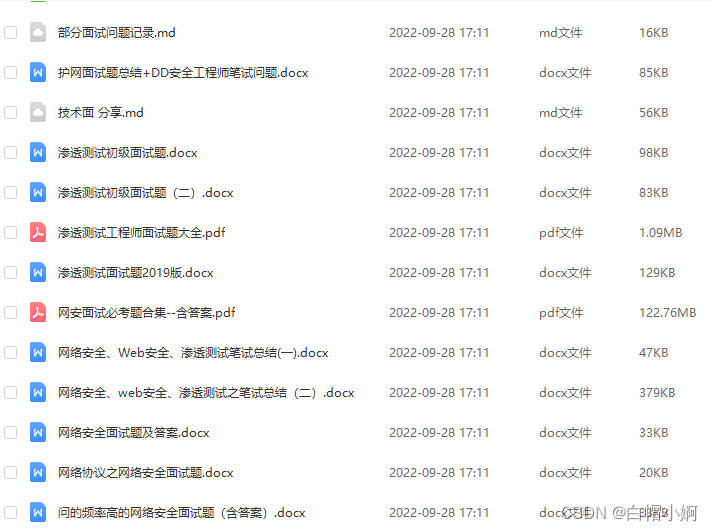
Recently, many small partners came to consult:
- How should I prepare for a technical interview if I want to find a job in cybersecurity?
- I have worked for less than 2 years and want to change jobs to see opportunities. Are there any relevant interview questions?
In order to better help you get a high-paying job, today I will share with you two network security engineer interview questions. There are a total of 164 real interview questions . I hope they can help you avoid detours and get offers faster in the interview!
93 Cyber Security Interview Questions
1. What is SQL injection attack
2. What is an XSS attack
3. What is a CSRF attack
4. What is a file upload vulnerability
5. DDos attack
6. Distribution map of important agreements
7. The working principle of the arp protocol
8. What is RARP? Working principle
9. What is dns? How does dns work?
10. What is the rip protocol? The working principle of rip
11. Disadvantages of RIP
12. OSPF protocol? How does OSPF work?
13. Summary of the difference between TCP and UDP?
14. What is three-way handshake and four-way handshake? Why does tcp need three-way handshake?
15. The difference between GET and POST
16. The difference between cookies and sessions
17. The working principle of session? 1
8. A complete HTTP request process
19. The difference between HTTPS and HTTP
20. What are the seven layers of the OSI model?
21. The difference between http long connection and short connection
22. How does TCP ensure reliable transmission?
23. What are the common status codes?
24. What is SSL? How does https ensure the security of data transmission (how does SSL work to ensure security)
25. How to ensure that the public key is not tampered with?
26. PHP burst absolute path method?
27. What are your commonly used penetration tools, and which one is the most commonly used?
28. The use of xss blind typing to the intranet server
29. Spear Attacks and Watering Hole Attacks
30. What is virtual machine escape?
31. Man-in-the-middle attack?
32. TCP three-way handshake process?
33. Seven-story model?
34. Understanding of cloud security
35. Have you understood websocket?
36. What is DDOS? What are they? What is CC attack? What is the difference?
37. What is a land attack?
38. How will you collect information?
39. What is CRLF injection attack?
40. To prevent XSS, two angles at the front end and back end?
41. How to protect the security of a port?
42. Webshell detection ideas?
43. What is GPC? How to bypass it if it is enabled?
44. What are the commonly used encryption algorithms on the web?
45. What else can XSS do besides get cookies?
46. Carrier (or other) network hijacking
47. What is DNS spoofing
48. The principle and defense of buffer overflow
49. Emergency response to network security incidents
50. Enterprise Internal Security
51. Before the business goes online, how to test and from which angles to test
52. The application has a loophole, but it cannot be repaired or disabled, what should you do?
53. How to protect against CSRF?
54. File upload bypass method?
55. Use points related to verification codes
56. What content will you test for cookies?
57. Name several types of business logic vulnerabilities?
58. Brief description file contains loopholes
59. What are the examples of business logic loopholes and arbitrary password resets by users, and what factors cause them?
60. During the penetration test, I found a function that can only upload zip files. What are the possible ideas?
61. Why does the aspx Trojan have greater authority than asp?
62. What are the ideas for only one login page?
63. Which of the request headers are harmful?
64. Talk about the difference between horizontal/vertical/unauthorized access?
65. What is xss? The hazards and principles of executing stored xss
66. The host is suspected of being invaded, where to look at the log
67. Standard libraries commonly used in python
68. What is the difference between reverse tcp and bind tcp?
69. What problems may occur during the oauth authentication process, and what kind of loopholes may result?
70. How to obtain real IP for a website with CDN
71. How to achieve cross-domain?
72. What is the difference between jsonp cross-domain and CORS cross-domain?
73. Algorithms? What kind of sorting do you know?
74. SSRF exploit?
75. Common backdoor methods?
76. How to bypass open basedir access directory restrictions?
77. What are the points that are prone to problems in PHP code audit?
78. The scene and posture of the red and blue against the middle and blue team against the red team?
79. Linux scheduled tasks, what will hackers do to hide their scheduled tasks?
80. How many common getshell methods are Redis unauthorized?
81. What is the attack method of JWT? (header, payload, signature)
82. Vulnerabilities in JAVA middleware, give a few examples?
83. What vulnerabilities can DNS takeout be used for?
84. Summary of middleware vulnerabilities?
85. Talk about the idea of raising rights in Windows system and Linux system?
86. What frameworks does python have, and what loopholes have appeared in them?
87. The difference between the penetration of small programs and ordinary penetration
88. The four major components of the vulnerability test of the app itself
89. IDS/IPS protection principle and bypass ideas
90. The use of csrf of json
91. What vulnerabilities can be detected by data packets in json format
92. Intranet server, how to collect information?
93. If a certain machine in the boundary layer of the intranet is taken down, how to detect others in the intranet?
Some content shows:
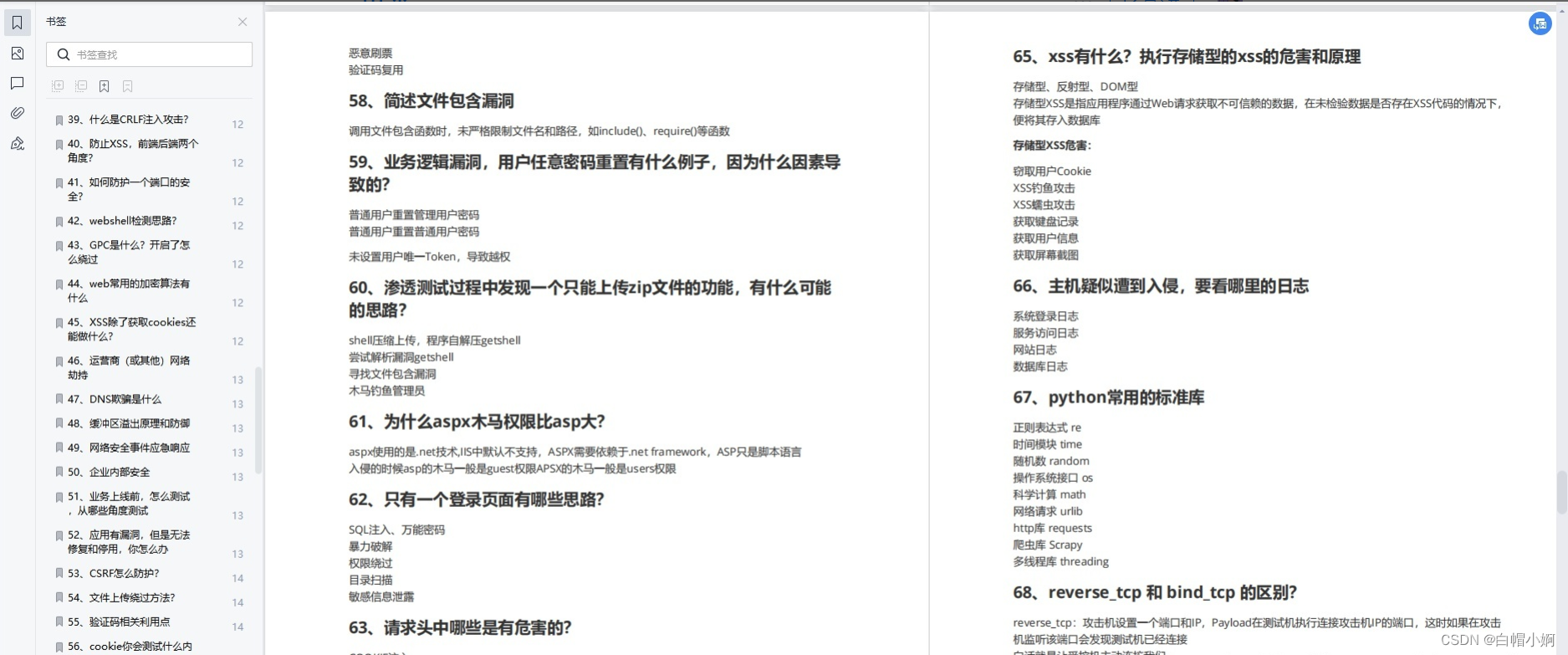

71 Cyber Security Interview Questions
1. PHP burst absolute path method?
2. What penetration tools do you use frequently, and which one is the most commonly used?
3. The use of xss blind typing to the intranet server
4. Spear attack and watering hole attack?
5. What is virtual machine escape?
6. Man-in-the-middle attack?
7. TCP three-way handshake process?
8. Seven-layer model?
9. Understanding of cloud security
10. Have you understood websocket?
11. What is DDOS? What? What is a CC attack? What is the difference?
12. What is a land attack
13. How will you collect information?
14. What is CRLF injection attack?
15. To prevent XSS, two angles at the front end and back end?
16. How to protect the security of a port?
17. What is the idea of webshell detection?
18. How to test the loopholes of an IIS website? (depending on version)
19. What is GPC? open how to bypass
20. What are the commonly used encryption algorithms on the web?
21. What else can XSS do besides get cookies?
22. Carrier (or other) network hijacking
23. What is DNS spoofing
24. The principle and defense of buffer overflow
25. Emergency response to network security incidents
26. Enterprise internal security
27. Before the business goes online, how to test and from which angles to test
28. There is a bug in the application, but it cannot be repaired or disabled, what should you do?
29. How to protect against CSRF?
30. How to bypass file upload?
31. Use points related to verification codes
32. What content will you test for cookies?
33. How many types of business logic vulnerabilities can you name?
34. Brief description file contains loopholes
35. What are the examples of business logic loopholes and arbitrary password resets by users, and what factors cause them?
36. During the penetration test, I found a function that can only upload zip files. What are the possible ideas?
37. Why does the aspx Trojan have greater authority than asp?
38. What are the ideas for only one login page?
39. Which of the request headers are harmful?
40. Talk about the difference between horizontal/vertical/unauthorized access?
41. What is xss? The hazards and principles of executing stored xss
42. The host is suspected of being invaded, where to look at the log
43. Standard libraries commonly used in python
44. What is the difference between reverse_tcp and bind_tcp?
45. What problems may arise during the oauth authentication process, and what kind of loopholes may result?
46. How to obtain real IP for a website with CDN
47. How to achieve cross-domain?
48. What is the difference between jsonp cross-domain and CORS cross-domain?
49. Algorithms? Know what sort?
50. SSRF exploit?
51. Common backdoor methods?
52. Open_basedir access directory restriction bypass method?
53. What are the points that are prone to problems in PHP code audit?
54. The scene and posture of the red and blue against the middle and blue team against the red team?
55. Linux scheduled tasks, what will hackers do to hide their scheduled tasks?
56. What are the common ways of getshell without Redis authorization?
57. What is the attack method of JWT? (header, payload, signature)
58. Vulnerabilities in JAVA middleware, give a few examples?
59. What vulnerabilities can DNS takeout be used for?
60. HTTP-Only prohibits JS from reading cookie information, how to bypass this to obtain cookie
61. Summary of middleware vulnerabilities?
62. Talk about the idea of raising rights in Windows system and Linux system?
63. What frameworks does python have, and what vulnerabilities have appeared in them?
64. The difference between the penetration of small programs and ordinary penetration
65. The four major components of the vulnerability test of the app itself
66. IDS/IPS protection principle and bypass ideas
67. The use of csrf of json
68. What vulnerabilities can be detected by data packets in json format
69. Briefly describe the principle and utilization of xxe vulnerabilities
70. Intranet server, how to collect information?
71. If a certain machine in the boundary layer of the intranet is taken down, how to detect others in the intranet?
Partial display