Preface
I wonder if you gohave ever encountered vulnerabilities in some third-party packages or official packages in your development projects. These vulnerabilities may affect the function, performance or security of the code.
Now to address this problem, gothe team has provided govulnchecktools to help developers quickly discover and fix these vulnerabilities.
What is govulncheck
govulncheckIt is goan officially provided binary tool for checking gowhether there are known security vulnerabilities in code or binary files.
principle
goThe security team and community members jointly maintain a vulnerability database govulndb , which collects related vulnerability information since 2018its launch in 2018 .go modulego
govulncheckFirst, the version information of the modules and packages used in the code will be found, then the latest data of the vulnerability library will be called through the interface, and finally the data will be compared, and the affected packages or modules will be listed and output.

The picture above is gothe system architecture diagram provided by the official blog
- Vulnerability collection.
goThe security team will collect vulnerability data from a variety of channels, such as the public vulnerability databaseNational Vulnerability Database(NVD) andGitHub Advisory Databasecommunity feedback https://go.dev/s/vulndb-report-new (we can also use this to report the vulnerabilities discovered by ourselves) reported) andgosecurity vulnerabilities fixed by the team themselves, etc. - Update
govulnerability database. After collecting security vulnerabilities,gothe security team will make an assessment, and if they need to be dealt with, they will be directly entered into the vulnerability database. - Tool integration. After new vulnerabilities are dealt with, the vulnerability description on pkg.go.dev will be updated accordingly and new
govulnchecktools will be released.
Basic usage
Installation and use are relatively simple.
Download the latest version of the tool via the command line
go install golang.org/x/vulndb/cmd/govulncheck@latest
Then execute it in the directory that needs to be checked
govulncheck ./...
The output after execution is as follows, and vulnerability information and suggestions on how to fix it will be given.
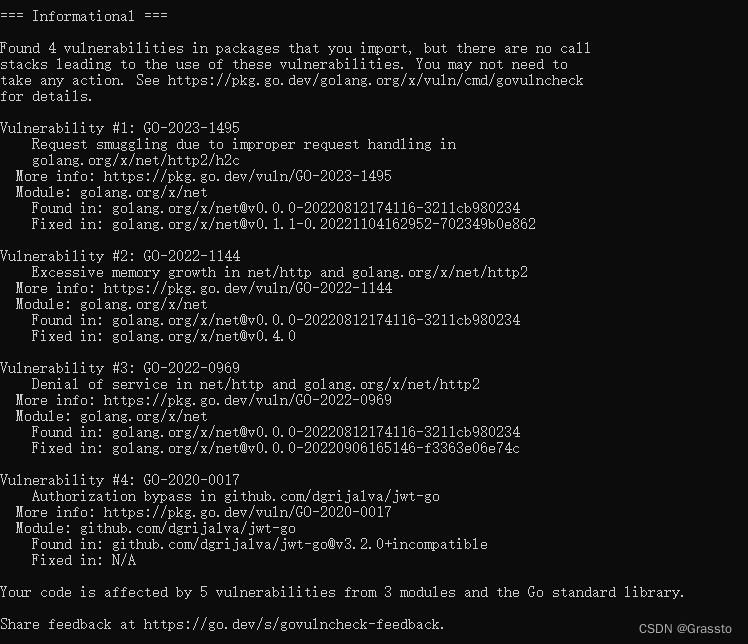
some limitations
- When scanning a binary file for security vulnerabilities, it is required that the binary file must be
go 1.18compiled with or a higher version. Security vulnerability scanning of binary files compiled with lower versions is not supported. - It is not possible to display
gothe call graph ( ) of the security vulnerabilities scanned in the binary filecall graphbecausegothe binary file does not contain detailed call chain information. False positives can also occur for code within binaries. - Only vulnerabilities under the
govulncheckcurrently executinggocompilation environment and configuration ( ) will be reported .GOOS/GOARCHExample: The vulnerability only existslinuxunder , but the development environment iswindowscross-platform development for , which may result in the vulnerability not being detected in the development environment. - Assuming that
go 1.18the vulnerability is only in the standard library, if the versiongovulncheckof the compilation environment where the current execution is , the vulnerability will not be reported.go1.19
Details can be found on: official blog .
Summarize
govulncheckIt is goan official vulnerability checking tool. goThe team collects vulnerabilities from multiple places and stores them in its own vulnerability library, and then uses govulnchecktools to scan codes or binary files for vulnerabilities.
A great tool, it is recommended to introduce vulnerability checking into the daily development process ( CI/CD, code review, etc.), which can help us gobuild high-quality, high-security programs through.