1. Introduction to FOFA
FOFA is a very powerful search engine. FOFA (Cyberspace Assets Retrieval System) is an IT equipment search engine with more complete data coverage in the world, and has more complete DNA information of global networked IT equipment. Explore the asset information of the global Internet, analyze the impact range of assets and vulnerabilities, apply distribution statistics, and app popularity situational awareness, etc. Compared with shodan, the advantage of FOFA is that it is more localized, has more domain name data, has established the world's largest asset rule set, and now has updated the function of identifying honeypots.
2. Grammar Introduction
For detailed grammar rules, please refer to FOFA official website https://fofa.info/ . The following summarizes common grammar from the perspective of actual combat.
1. title Website title title="beijing" Search for "Beijing" from the title
Generally, it is easy to open the one with a domain name, but pay attention to the pure ip and then open it with garbled characters, which may be a phishing website.
You need to check which services are enabled and which ports are open, and the IP aggregation will be displayed in detail (you need to register and log in to view the details, and some need to be a member to have permission to view)



2.body searches based on the main content of the webpage

Also through IP aggregation to view open services and open ports
3. According to the region where the server is located
country="CN" Search for assets in the specified country (code)
region="Xinjiang" searches for assets in the specified administrative region
city="beijing" Search for assets in the specified city
Exclude locales using !=
4. Search by icon icon
Upload the website title icon (usually xxxx.ico file) to search
5. Search CMS assets by rule list


Keep turning the page to find CMS (you can find other assets in the same way)
Just choose a CMS, and all CMS systems that use this version will be automatically retrieved
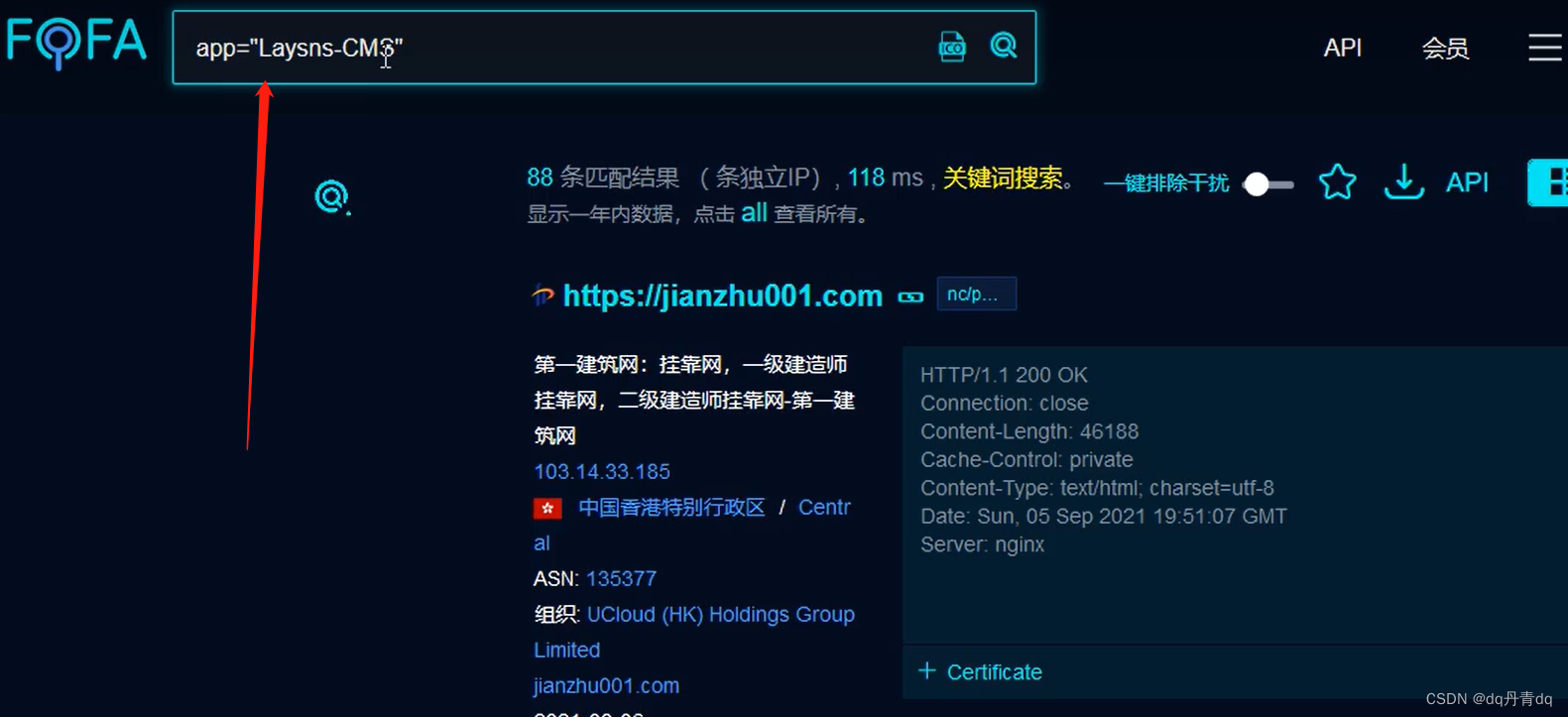
If there is a vulnerability in a certain version, some websites have been repaired, and some have not.
Of course, there are many ways to use it, you can explore it yourself
Talk too much, afraid of being caught
3. Overview and purpose
of passive information collection Information collection methods can be divided into two types: passive and active.
Passive information collection refers to the use of third-party services to access and understand the target, such as Google search.
Active Information Collection: The act of directing traffic through a website by directly visiting it, scanning it. For example: nmap scan port.
The purpose of passive information collection: to obtain the information of the target host through open channels, so as not to interact directly with the target system and avoid leaving traces.