Today Tencent Cloud suddenly sent me a message saying that there is a loophole, because I reset the system yesterday, installed pagoda and wordpress using the mirror system, and then a loophole suddenly appeared, so it seems that some loopholes should have been removed when I first bought it. Everything is solved for you. After resetting the system, the vulnerability may not be fixed due to version problems.
Vulnerability description
A foreign research team discovered the sudo heap overflow vulnerability (CVE-2021-3156), which has been hidden for ten years. Ordinary users can use this vulnerability to gain root privileges on the default sudo host. The details of the vulnerability have been made public on the Internet, and Tencent security experts remind Linux system administrators to fix it as soon as possible. Sudo is a powerful utility that is included in most Unix and Linux based operating systems. A successful exploitation of this vulnerability could allow any unprivileged user to gain root privileges on a vulnerable host. Researchers have independently verified the vulnerability on Ubuntu 20.04 (Sudo 1.8.31), Debian 10 (Sudo 1.8.27) and Fedora 33 (Sudo 1.9.2) and developed multiple exploits and gained full root privileges, among other actions Systems and distributions may also be exploited.
repair
Redhat/CentOS
My system is CentOS8.

Implementation process
yum makecache
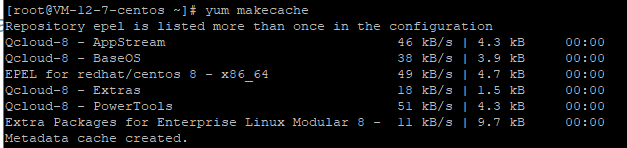
yum install sudo -y

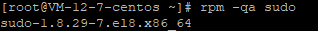
rpm -qa sudo
Ubuntu

official
Refer to Tencent's official repair method
https://s.tencent.com/research/report/1238.html