Elastic Security 7.6 is built based on the Elastic Endpoint Security and Elastic SIEM advantage, through a unified interface for excellent visibility and threat detection performance. This version can automatically detect threats in a centralized SIEM applications, and improve endpoint detection capability on the Windows host. Access the new data sources and improved by Elastic SIEM applications, security can be further enhanced ability of employees, thus speeding up the detection and the response speed. Our detailed look at the new features in 7.6 Elastic safety bar.
With the new detection engine and SIEM MITRE ATT & CK ™ in line with the rules, and strive to zero latency
Elastic Security SIEM 7.6 introduced a new detection engine to automate threat detection that minimize the average detection time (MTTD), and let your security team to make time to complete the need to rely on human intuition and skills of security tasks. Elastic SIEM (core Elasticsearch) has currently security incident investigation time from hours to minutes. With this new auto-detection function, we exposed through other methods may miss threaten to further reduce latency.

 Dump failed to re-upload canceled
Dump failed to re-upload canceled
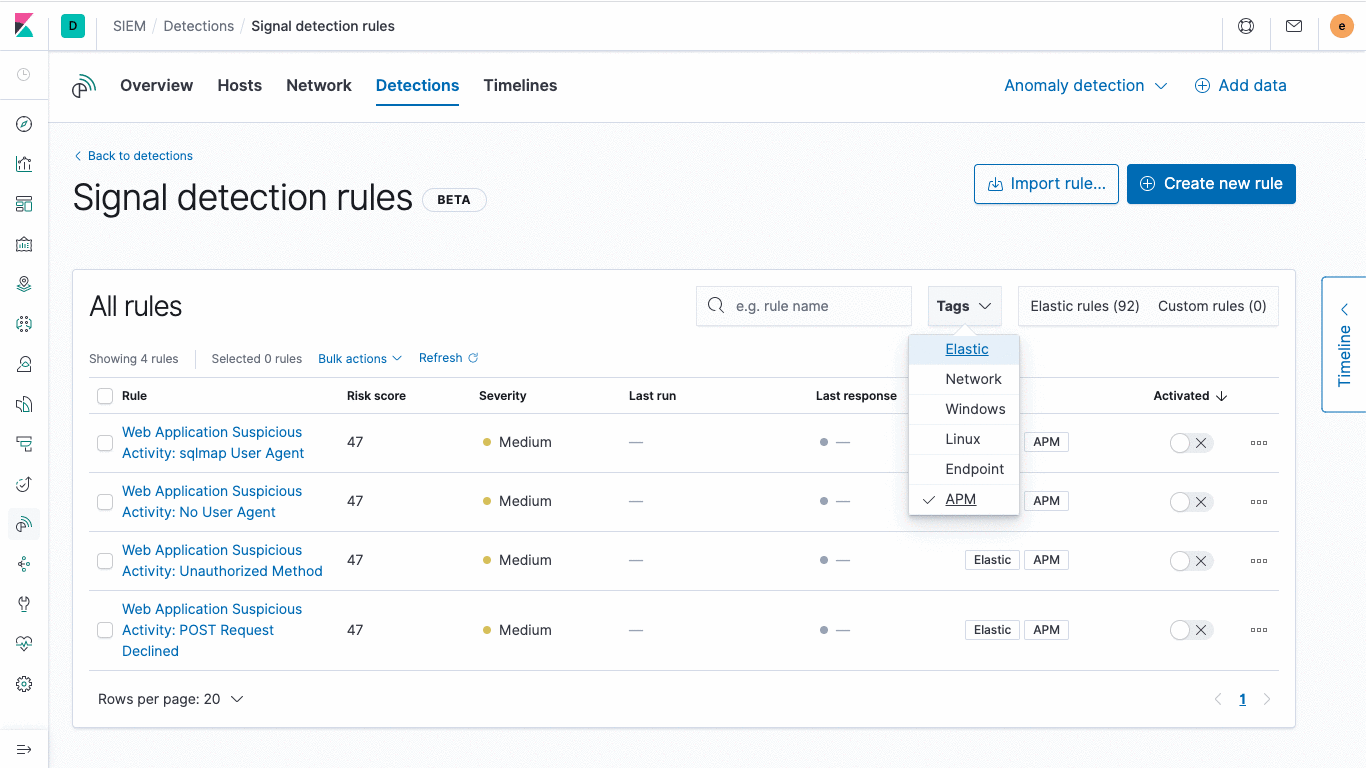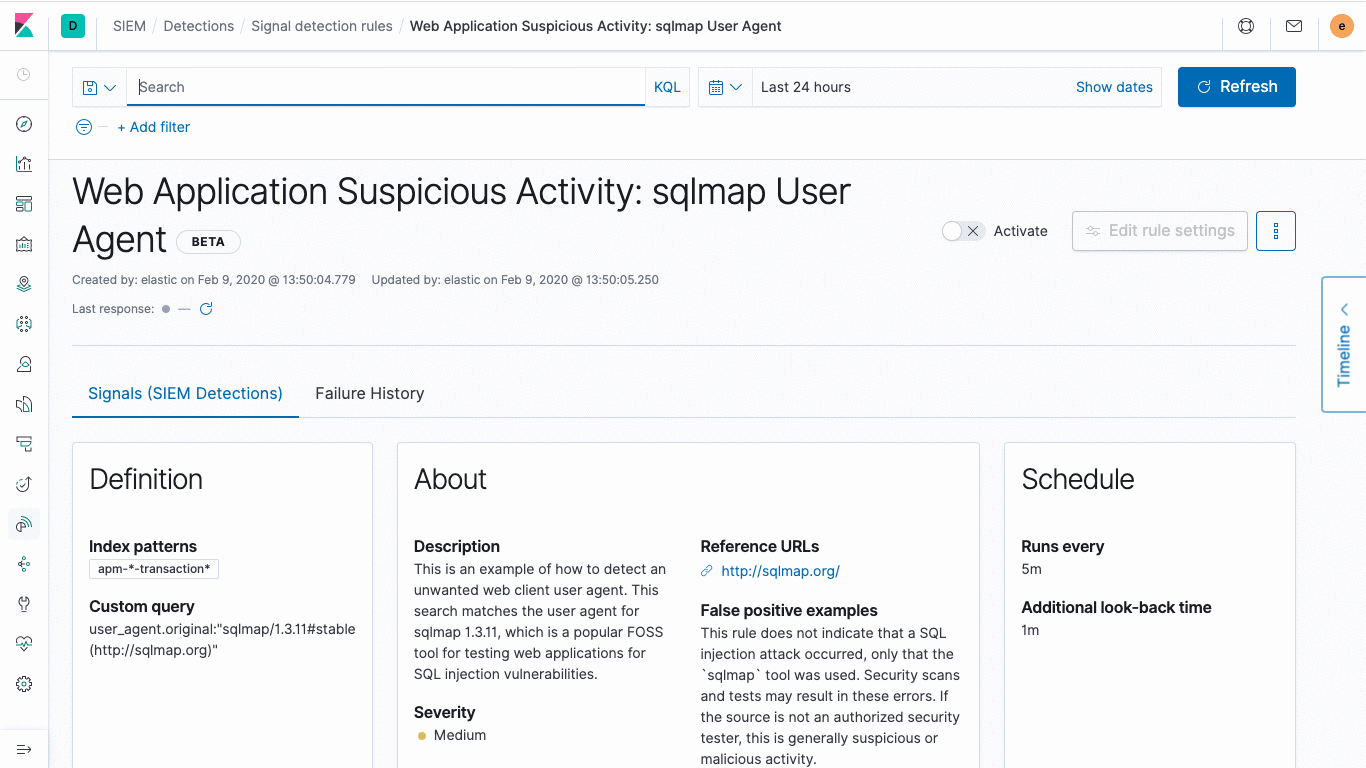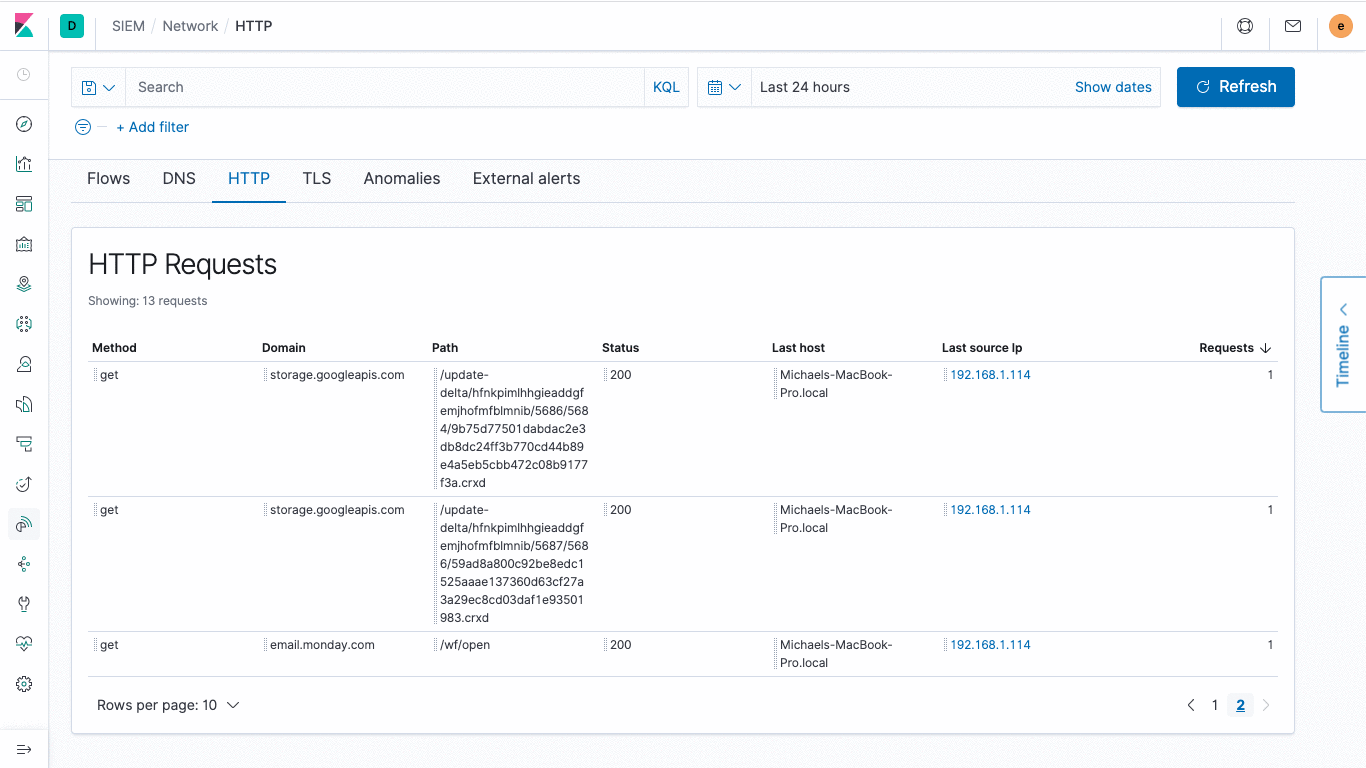
See SIEM detection (signal) detected by the engine SIEM automatically generated based on out-of-rule type
Elastic also released an initial set of nearly 100 consistent with ATT & CK Knowledge cash into the rules for signs of threats to other tools often overlooked. Elastic these rules by security experts to create and maintain, can automatically detect the tools, policies and procedures have been signs of threat activity, and will continue to be updated to deal with new threats. Detection engine will generate a signal for risk and severity score, this information can help analysts quickly sorted the problem and then focus on the most valuable work.
"Elastic not only provides us with efficient search millions of logs required tools will also reduce the number of warning to the level that we can deal with, precisely because these two points, our security team was able to focus on what really matters." Maxim Verreault security manager Skytech Communications, said, "with the release of 7.6, we can automatically analyzed by Elastic SIEM in-the-box-type signal detection rules for all observable data, and real-time detection and response to security threats. Elastic security 7.6 also provides security community a good opportunity to contact each other, because we are able to share custom signal detection rules, so that everyone can benefit and detect new and emerging threats. "
For collected from Windows, macOS and Linux systems comply with Elastic Common Schema (ECS) data specification, as well as network information from other sources, these rules can play a role. Security teams can choose to create or customize rules, but never need to add to their environment and in accordance with the new data source specification ECS rewrite rules.
These built-in Elastic SIEM threat detection rules created and maintained by the security experts Elastic, can complement SIEM application of Machine Learning-driven anomaly detection jobs, and host-based protection of Elastic Endpoint Security.
A substantial increase in the visibility of Windows endpoints
Since the Windows system is very popular, while also using loose-user license model, it is a major target; Elastic Security 7.6 can significantly increase the visibility and protection for Windows systems. This version of the Windows version deepened the visibility of activities and the flexibility to collect and enrich the data from the position vulnerable to the threat of advanced evasion techniques is.
The new out of the box-type detection will use the data to detect an attempt to capture keyboard input, load malicious code into other processes and other behavior. Practitioner can detect these events and rule generating an automatic response (e.g., forced off process) used in combination to achieve the prevention of delamination. With this visibility and protection, plus both the prevention, detection and response capabilities for macOS and Linux systems, Elastic Endpoint Security users throughout the environment subject to full protection.
 Dump failed to re-upload canceled
Dump failed to re-upload canceled
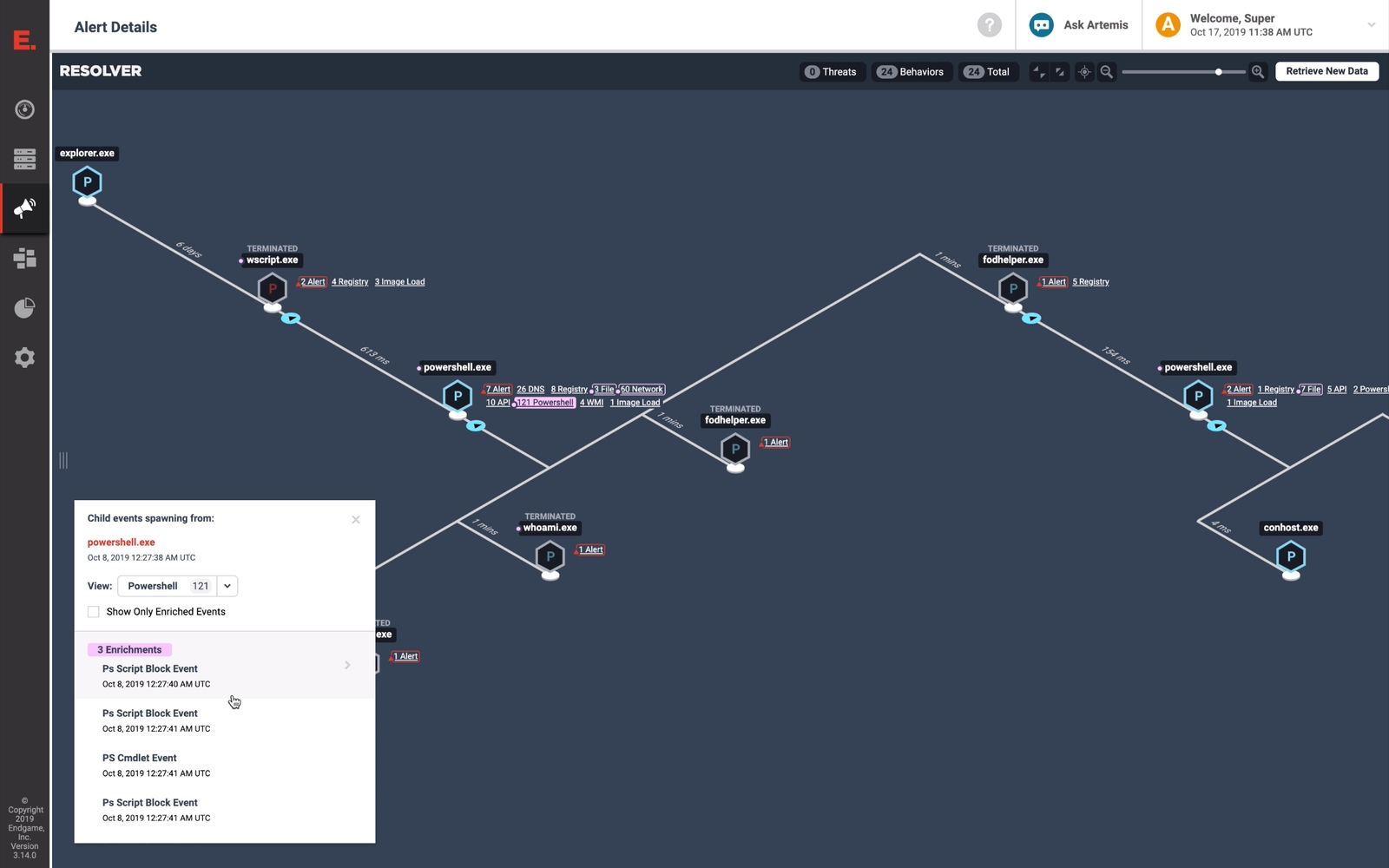
Use Elastic Endpoint Security in View Resolver process end to end attacks
 Dump failed to re-upload canceled
Dump failed to re-upload canceled
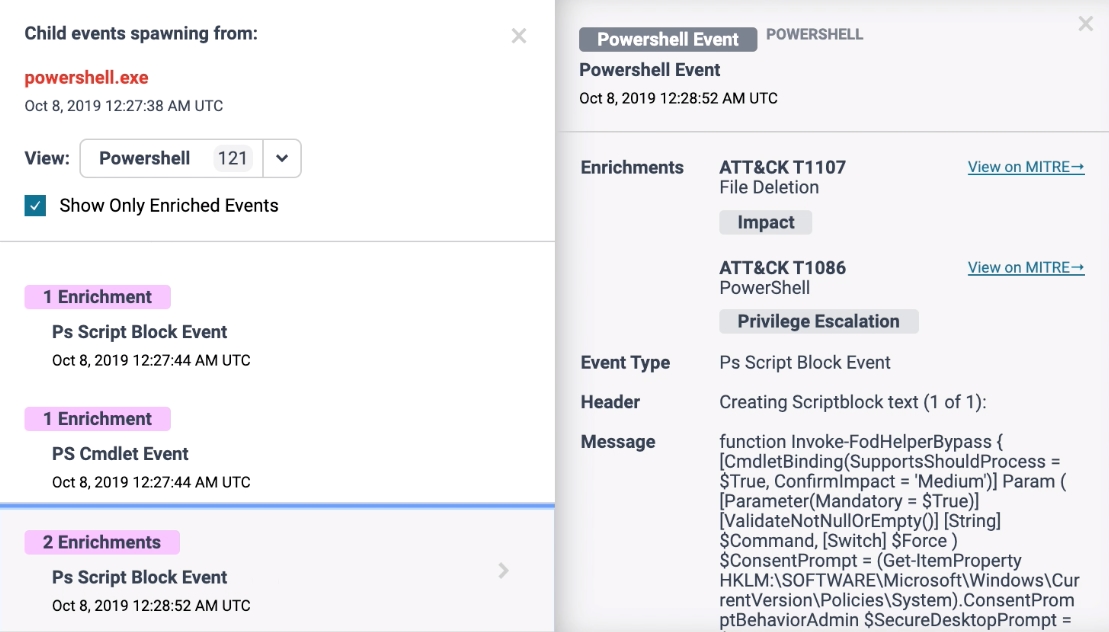
PowerShell event of a substantial increase in visibility
By quickly see the most important part, shorten the average detection time
With Elastic SIEM application of new "overview" page as well as a wide range of workflow improvements, security practitioners can quickly hunt and investigate threats. Open the timeline to see the latest detection signal, and view from an external source (eg Elastic Endpoint Security, through the Palo Alto Networks warning, Suricata, Zeek, etc.), the user can carry out investigations directly. No matter anywhere in the SIEM applications, you just tap the mouse, you will be able to experience its integrated threat detection and anomaly detection.
 Dump failed to re-upload canceled
Dump failed to re-upload canceled
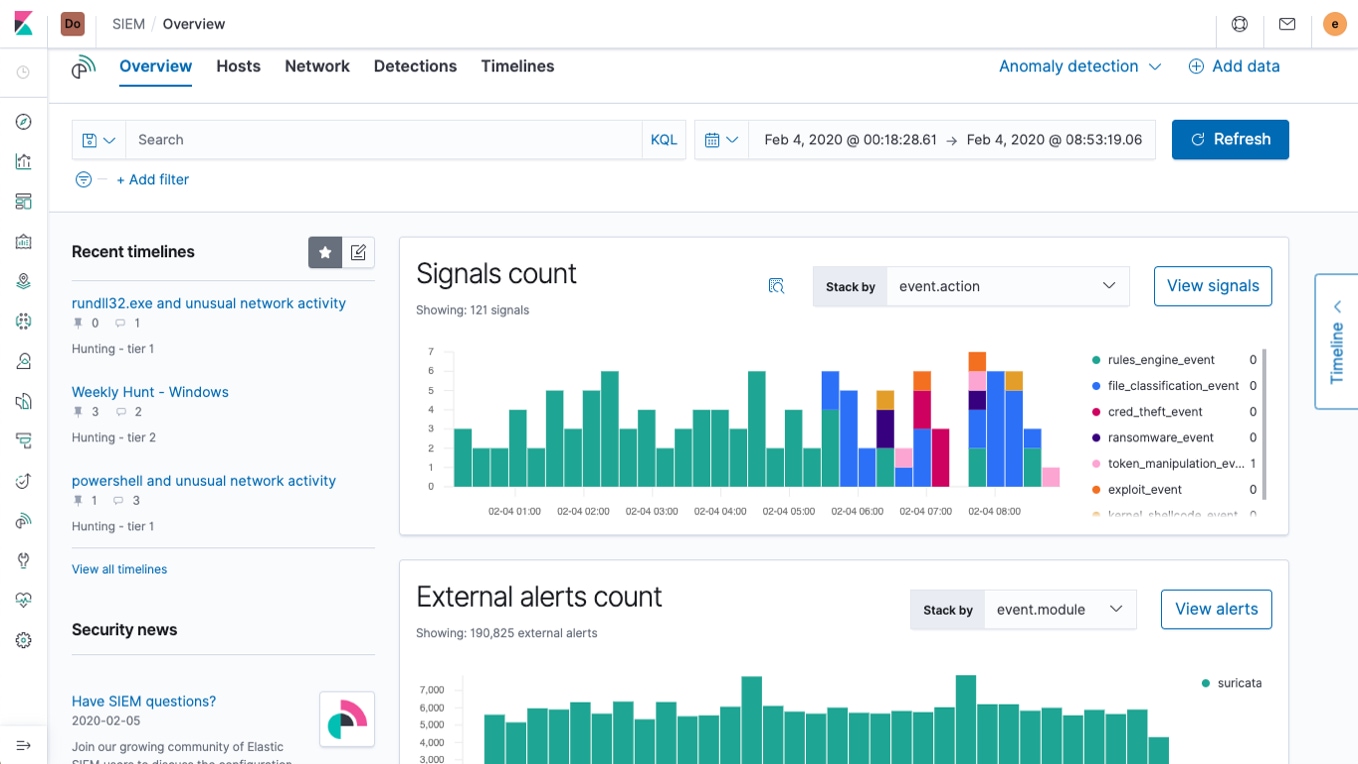
With Elastic SIEM application of new "overview" page, security monitoring easier
By a new event, alarm and signal histogram, analysts can better understand the operating conditions can also explore the "host" and "network" in view of the new and improved visualization to see a more detailed analysis of professional content.
 Dump failed to re-upload canceled
Dump failed to re-upload canceled
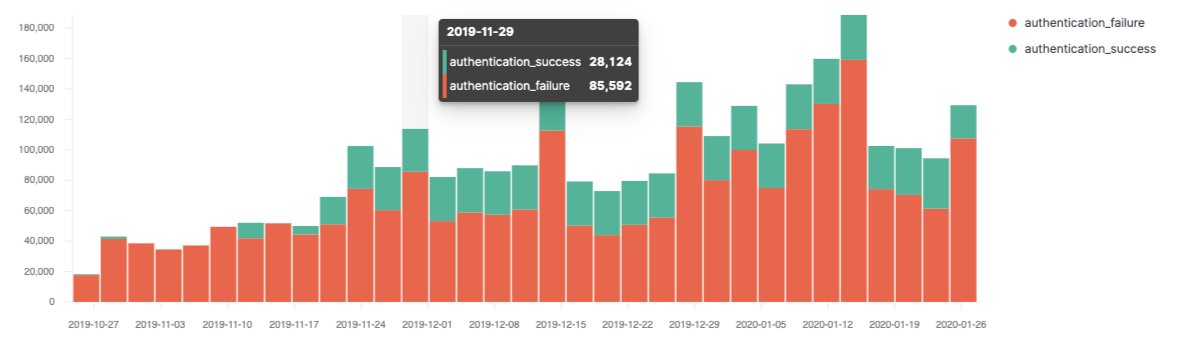
Elastic SIEM overview data through the new histogram
Pay close attention to your application
Elastic SIEM now also offers a selection of content for the HTTP data visibility, allowing you to view the Elastic APM data directly from SIEM applications. More out of the box ready to use Beats module allows you to access more in line with ECS standard HTTP data, makes it easy to check all network transactions in a single unified view and visualization. Take a bit of digging, see if you can find what baby, do not forget to make sure your DevOps (development of operation and maintenance) and friends Come experience oh.
 Dump failed to re-upload canceled
Dump failed to re-upload canceled
Monitor your cloud data
 Dump failed to re-upload canceled
Dump failed to re-upload canceled
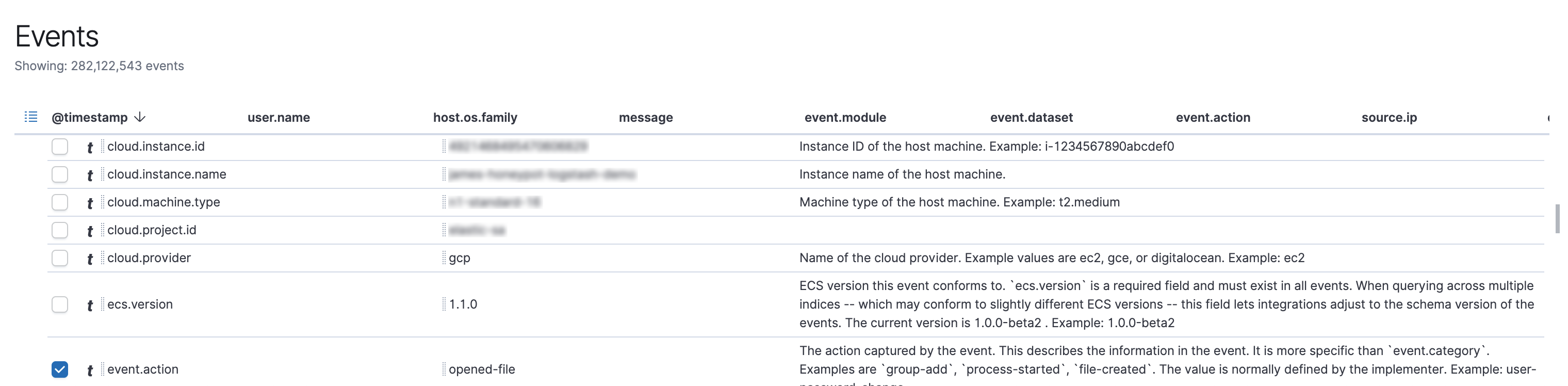
GCP collection event to view the ECS format and in SIEM applications
This time we make it easier for you to collect data to Elastic Stack so centralized visualization and analysis. 7.6 introduced support for AWS CloudTrail data and enhanced support for Google Cloud Platform, allowing you to get essential visibility through the appearance of modern attacks. We have updated the CEF module is suitable for Filebeat, and, as long as the data format for the CEF, whether from the cloud or elsewhere, can be visualized by this module more easily than before.
Start using
Elastic SIEM want to try it? Welcome to the Elasticsearch Service experience our latest version on Elastic Cloud, or you can try Elastic SIEM presentation . Elasticsearch already ECS data format? Just upgrade to Elastic Stack 7.6, you can start hunting a threat.
Hopes Elastic Endpoint Security to ensure the security of your environment? Welcome to register to join the early adopters program .
I want to personally experience the Elastic safe? Welcome to our booth at the RSA (booth # 1427 and # 2227), can also participate in your city Elastic {ON} Tour event.
