Brief introduction
Reproduce the original question: https://github.com/CTFTraining/zjctf_2019_final_web_nizhuansiwei/
Examine knowledge: logical loopholes, JWT forgery, python deserialization
Online Platform: https://buuoj.cn (Beijing Union University public platform CTF) can be used within the interior of Yulin College Principal Association CTF training platform to find this title
Brief introduction
Open to see this piece of information to see

Binding list of products below have generally read 500 pages to write a V6 under py find! ! !
import requests from bs4 import BeautifulSoup for i in range(1,500): url="http://3e78514d-0c20-4179-a892-cab68cf70145.node3.buuoj.cn/shop?page="+str(i) r=requests.get(url) soup=BeautifulSoup(r.content,'lxml') title_all=soup.find_all(name='img',attrs={'src':'/static/img/lv/lv6.png'}) if(title_all): print(i)
When you find there is not enough money to buy a logical flaw modify discount 0.0000000008 this money is enough!
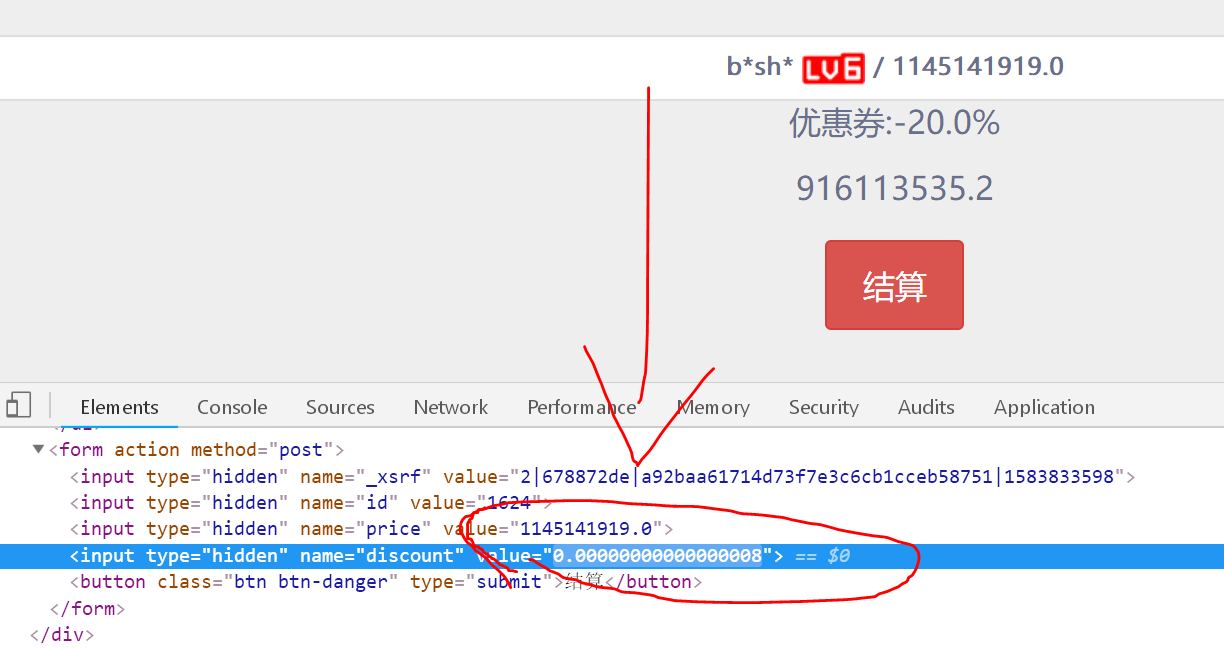
The problem again .......
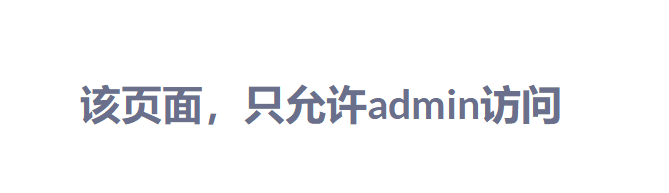
Wp Look here first to learn about the use of forged JWT JWT
JWT basis can be seen here: https: //www.cnblogs.com/xhds/p/12457560.html
We can see the path our jwt data in a cookie
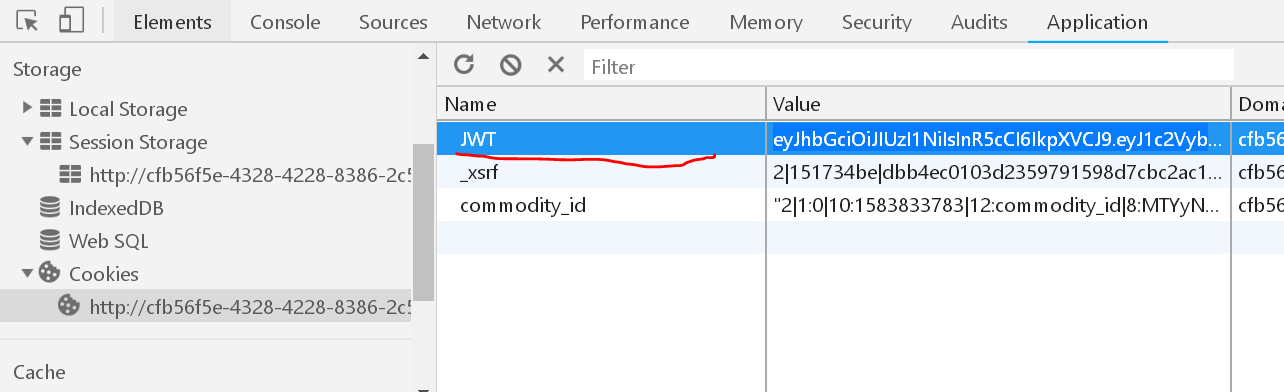
Copy to be decoded https://jwt.io
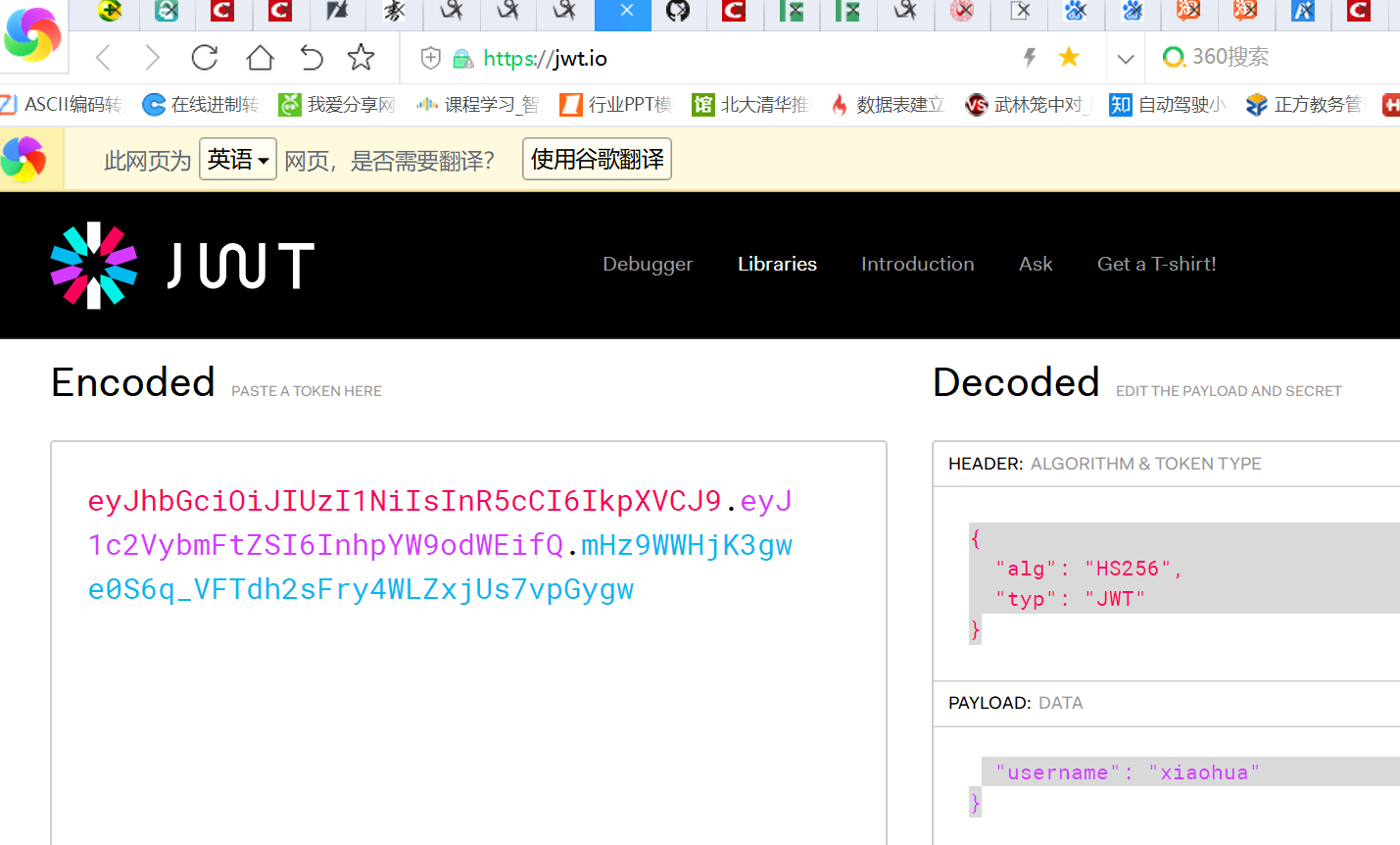
Use blasting tool: https: //github.com/brendan-rius/c-jwt-cracker input into the jwt
apt-get install libssl-dev
./jwtcrack eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InhpYW9odWEifQ.mHz9WWHjK3gwe0S6q_VFTdh2sFry4WLZxjUs7vpGygw

We may burst key input into the payload inside the username admin signature into which you can get into 1kun new JWT

After the browser by clicking a button or submit BP become a major member
Brief introduction
111
Brief introduction
111