First, information collection
Introduction 1.1 domain
This domain name (Domain Name) is the name on the Internet there are a bunch of dots division name consisting of a computer or group of computers for data transmission in the process is to identify the orientation of the electronic computer browsing the site obtained from the corresponding domain names DNS server IP addresses
1.2 Whois
Whois query whether the domain name has been registered and the database (for all domain names, domain name registrars) details of registered domain names
1.web Query Interface
https://whois.aliyun.com
https://www.whois365.com/cn
http://whois.chinaz.com
https://whois.aizhan.com
2. whois command-line inquiry
whois aliyun.com
1.3 ICP for the record
English name: Internet Content Provider, Chinese name: Internet content providers. ICP can be understood as to provide customers with Internet information services and value-added services for telecom operators, is officially operating companies or departments approved by the state authorities.
Second, the information collection sub domain
顶级域名:.com .net .org .cn
Why do not collect information phone top-level domain, and he ran to collect secondary or third-level domain?
Top-level domain is a lot of protection, if the top-level domain hung up, then the sub-domain followed hang, but the subdomain hung up, top-level domain will be very difficult, and most go all top-level domain, in order to prevent safety do top-level domain protection
2.1 subdomain of mining tools
1.Maltego CE
2.wydomain
GitHub地址:https://github.com/ring04h/wydomain
在kali终端:git clone https://github.com/ring04h/wydomain
cd wydomain
pip3 install -r requests.txt
python dnsburte.py -h # 查看帮助文档
python dnsburte.py -d xxx.com # 把结果保存到log
cat bruteforce.log # 可以看到网站的子域名
3. Search Engine Mining
Enter the Google site: sina.com
4. Third Party website
http://tool.chinaz.com/subdomain
https://dnsdumpster.com
https://phpinfo.me/domain/
Third, the port information gathering
Introduction 3.1 port:
If the IP address for a house than the port is out of the house door. The real house only a few doors, but a port IP address can have 65,536. Ports are labeled by the port numbers, port number only integer in the range from 0 to 65535
3.2 Tool Principle:
使用TCP或者UDP等协议向目标端口发送指定标志位等的数据包,等待目标返回数据包, 以此来判断端口状态
1.使用nmap探测
nmap -A -v -T4 目标
2.使用在线网站探测,不能探测本地
http://tool.chinaz.com/port/
3.3 port attack
1, has a different attack methods for different ports
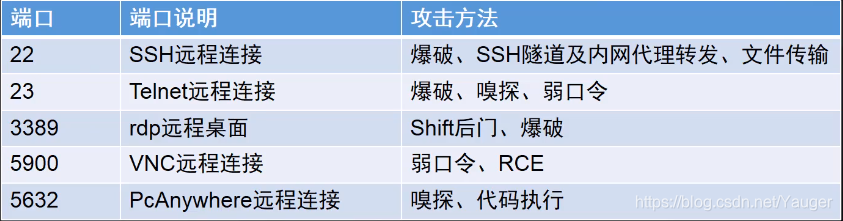
2, defensive measures
1.关闭不必要的端口
2.对重要业务的服务端口设置防火墙
3.经常更换用户密码
4.经常更新软件,打补丁
3, the importance of collecting sensitive information
For some security to do a good target, directly through the technical level is not complete penetration testing. In this case, you can use the search engine to search for information related targets exposed on the Internet. For example: the database file, SQL injection, server configuration information, and even locate the site leaked source code through Git, and Redis and other unauthorized access. So as to achieve a penetration test
4, Google hacking grammar
google hack is the use of Google and other search engines for certain search network host vulnerabilities, find vulnerabilities in order to achieve rapid vulnerability of a specific host or hosts
intext:——搜索正文内容 例如intext:网站管理
intitle:——搜索标题内容 例如intitle:后台管理
filetype:——搜索指定文件格式 例如filetype:txt
inurl:——搜索特定URL。 例如.php?id
site:——制定搜索特定的站点 例如:site:baidu.com
info:——指定搜索网页信息 例如:info:baidu.com
4. The real IP address harvesting
4.1 CDN stands for Content Delivery Network, ie, content delivery network
-
The basic idea is as far as possible to avoid bottlenecks and links may affect the data transmission speed and stability of the Internet, the content delivery faster and more stable. By placing a layer of intelligence on the existing Internet-based server nodes throughout the network composed of the virtual network, in accordance with the CDN system capable of real-time and network traffic of each node connected to the load conditions and the user's response time and the distance and other comprehensive information to the user's request to redirect the service node closest to the user.
-
Its purpose is to enable users to obtain the required content of the nearest address the Internet network congestion condition and improve the response speed of the user access to the site.
4.2 CDN advantage
(1) CDN node to solve the problem of cross-regional and inter-operator access, access latency is greatly reduced;
(2) the majority of requests completed CDN edge node, CDN has played a diversion effect, reduces the load on the source station.
4.2 CDN features
- Local Cache accelerates : improve the corporate site (in particular, a lot of images and static pages site) access speed, and greatly improve the stability of the above nature of the site.
- Mirroring service : eliminates the effects of interconnection between different operators bottlenecks, to achieve the inter-carrier network acceleration, to ensure that different network users can get access to good quality.
- Remote acceleration : Remote Access users to automatically select Cache DNS server based intelligent load balancing technology, choose the fastest Cache server to speed up remote access.
- Bandwidth Optimization : Automatic generation server remote Mirror (mirror) cache server, remote users accessing the data read from the cache server, reduce bandwidth remote access, sharing of network traffic, reduce the primary site WEB server load and other functions.
- Cluster anti-attack : widespread CDN node coupled with intelligent redundancy mechanisms between nodes, can be effective in preventing hacking and reduce the impact of various DDoS attacks on websites, while ensuring a better quality of service.
4.3 CDN cache
Cache is an example of a space for time everywhere present. By using extra space, we were able to get faster.
