- After clear all cookies Open any details page of a book, open console Network. , The first browser request issued XHR FIG as follows
/bind, wherein DeviceToken, nonce, Token data are submitted POST.
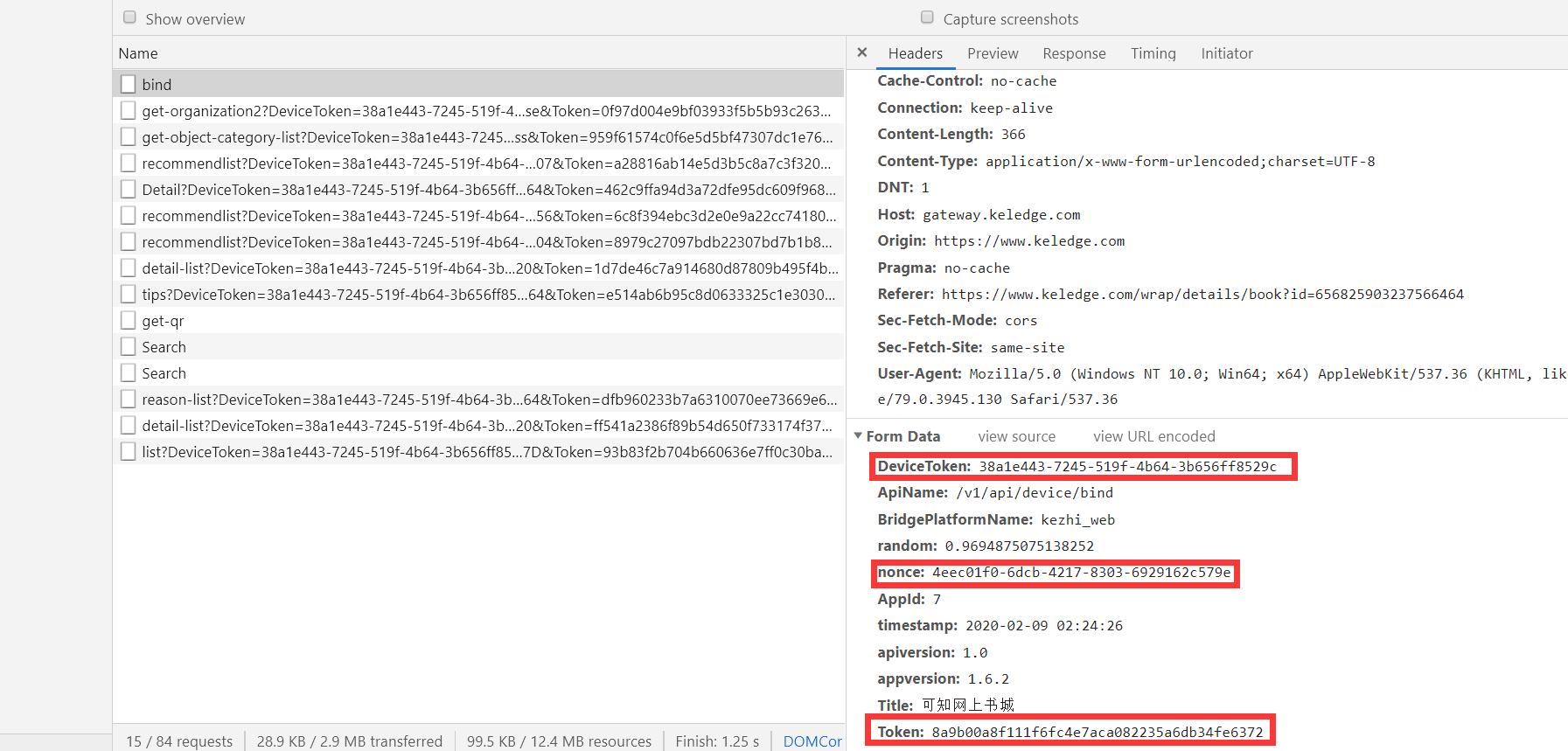
- Find the requested access to the web page, as shown below, set-cookie header field returns no, it is judged DeviceToken, nonce, Token js are generated.
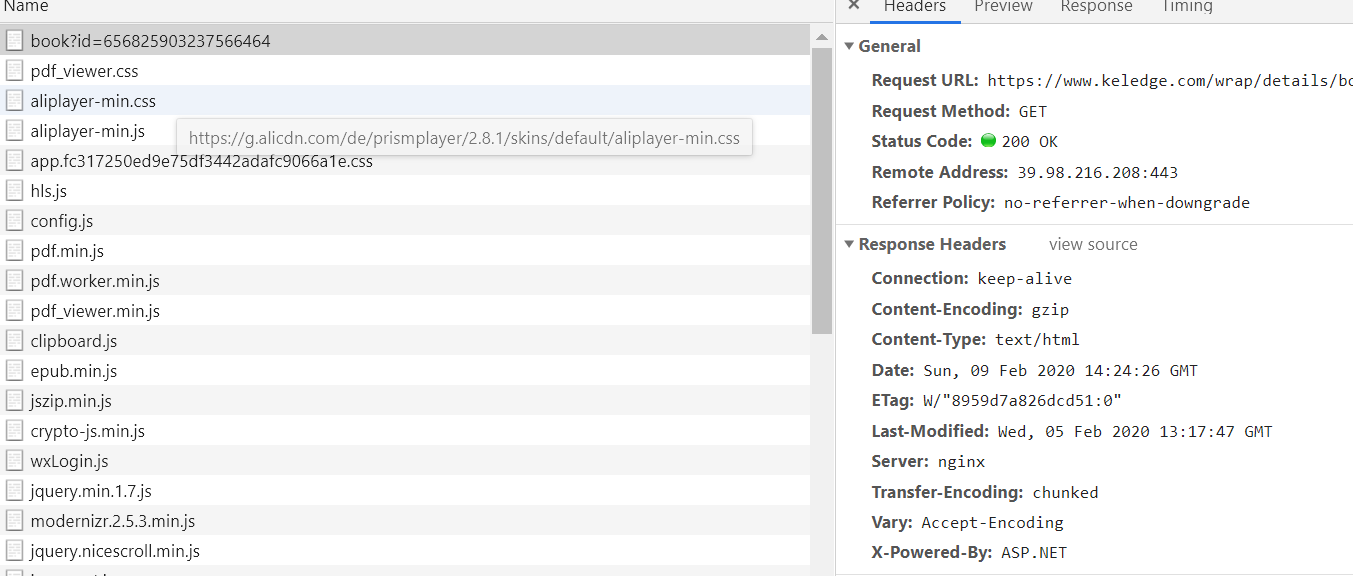
- Found send
/bind/Initiator request, and found that onlyvendor.*.jstheapp.*.jsrelevant, and the emergence ofwebpackJsonp,computed,updateRouteand other fields, guess the site is built using vue-cli. - Download and decoding
vendor.*.jsandapp.*.js, inapp.*.jsthe search/bindto find relevant code.
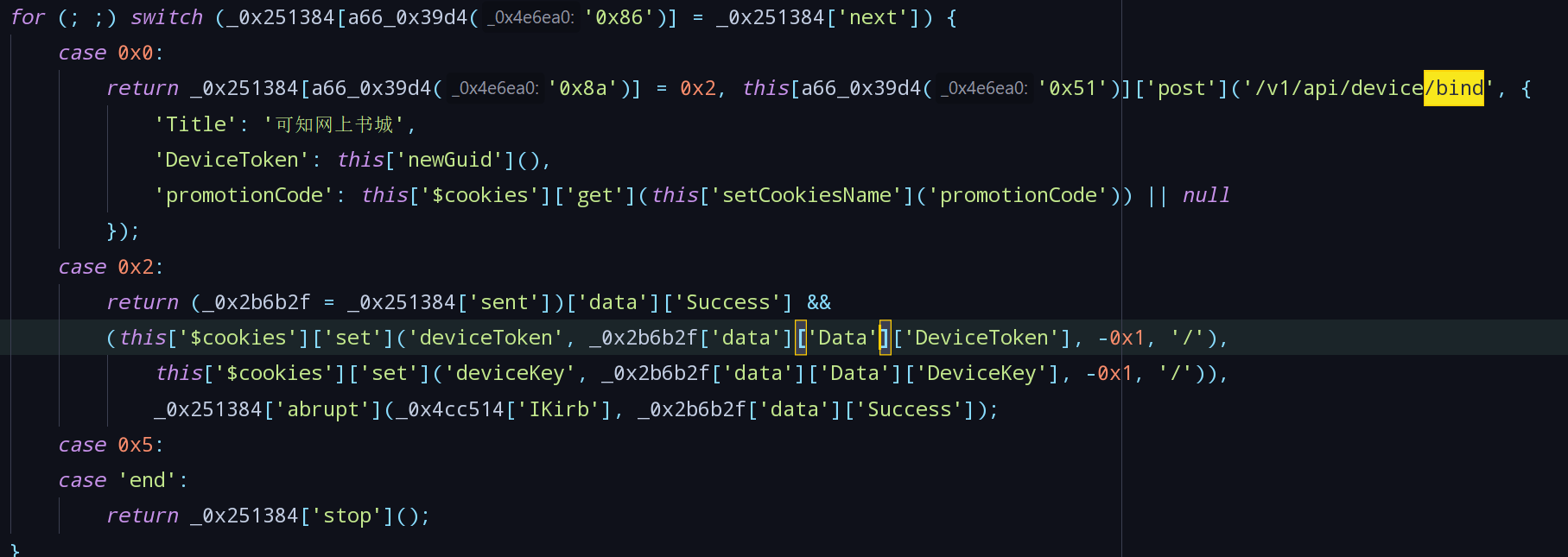
The flow section substantially function to send/binda request to the rear, if the result returnedSuccessfield is true, the dataDeviceToken,DeviceKeyinto the cookie. TransmittedDeviceTokenby thenewGuid()generating function.- Locate the section function named function
registerApp, search call.
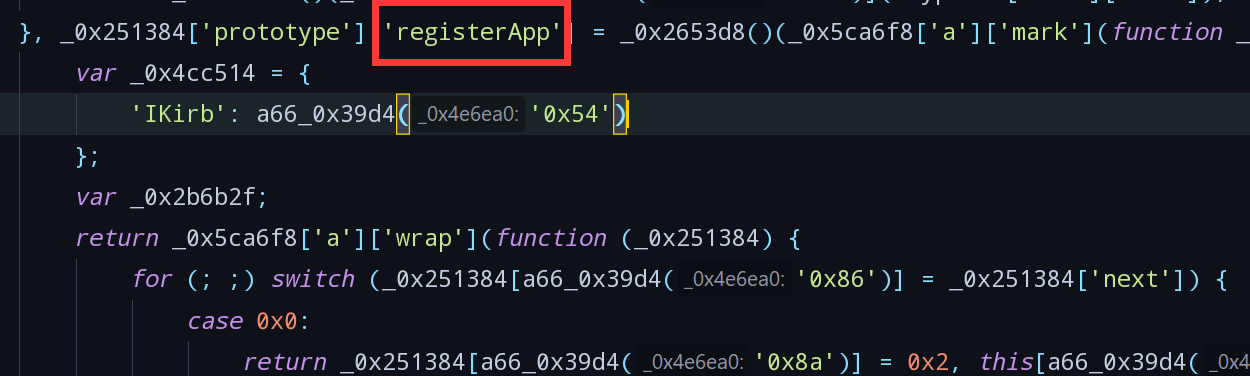
- Found calling
registerAppcode, according to the abovewatchandmethodscan be judged that this is a component of vue, monitoring changes to the call routingregisterApp

- We can easily come to draw all exposed to this function names are present in variable
66_0x3458in.
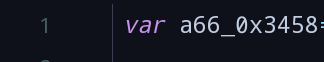
- It will be
newGuidconverted to utf-8 encoding, to\x6E\x65\x77\x47\x75\x69\x64find it in a variable66_0x3458position
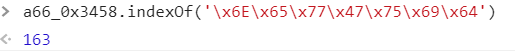
- 将163转为16进制为a3,在
app.*.js中搜索0xa3,找到定义。
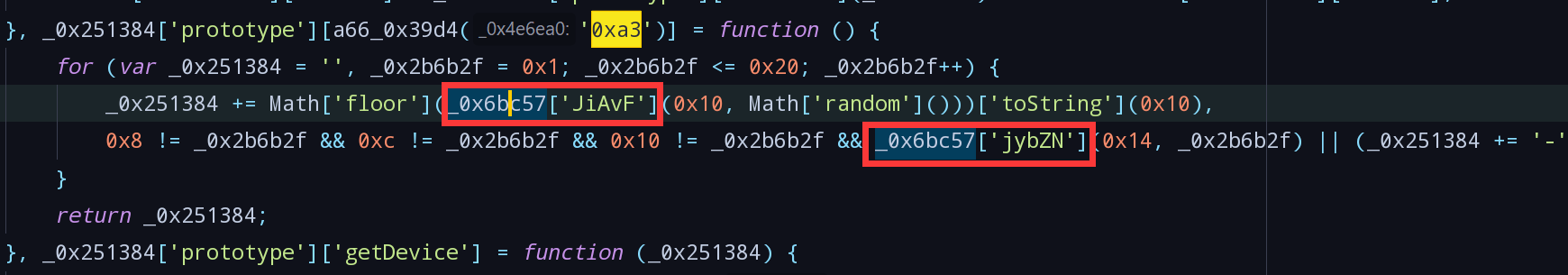
_0x6bc57['JiAvF']与_0x6bc57['jybZN']为调用的其他函数,分别搜索得出对应函数:
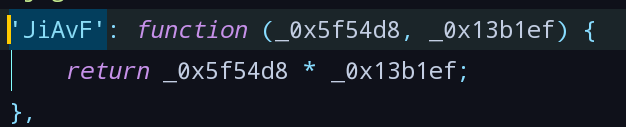
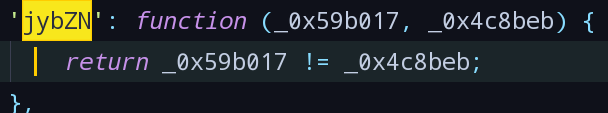
- 用对应代码替换上述函数,丢进jsnice转换:
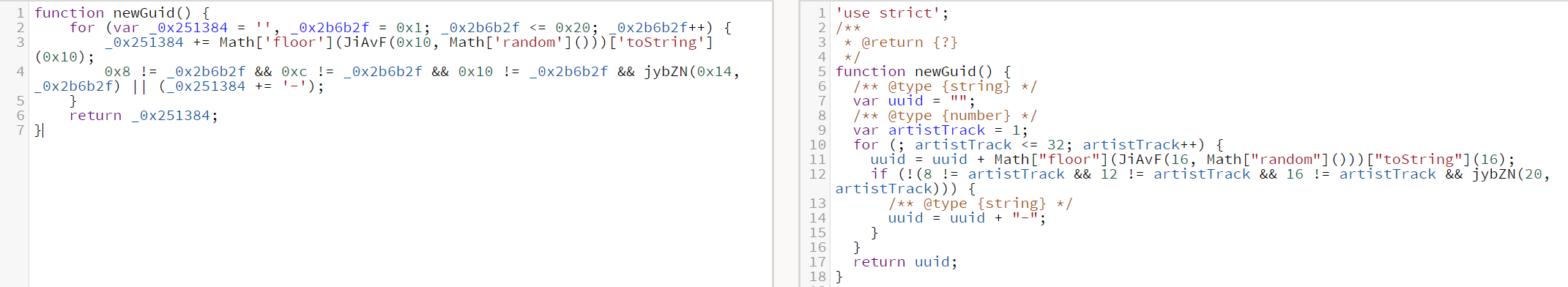
- 重命名变量,最后得出
newGuid的代码如下,生成一个32的uuid:
function newGuid() { let uuid = "", i = 1; for (; i <= 32; i++) { uuid = uuid + Math.floor(16 * Math.random()).toString(16); if (!(8 !== i && 12 !== i && 16 !== i && i !== 20)) { uuid = uuid + "-"; } } return uuid; } - Locate the section function named function
- 返回
/bind的代码,请求中的data实际只有三个字段,与看到XHR请求中字段数量不一致,判断是做了一个拦截器,而一般的vue-cli项目中使用的http请求库为axios,所以直接搜索interceptors找到拦截器代码。
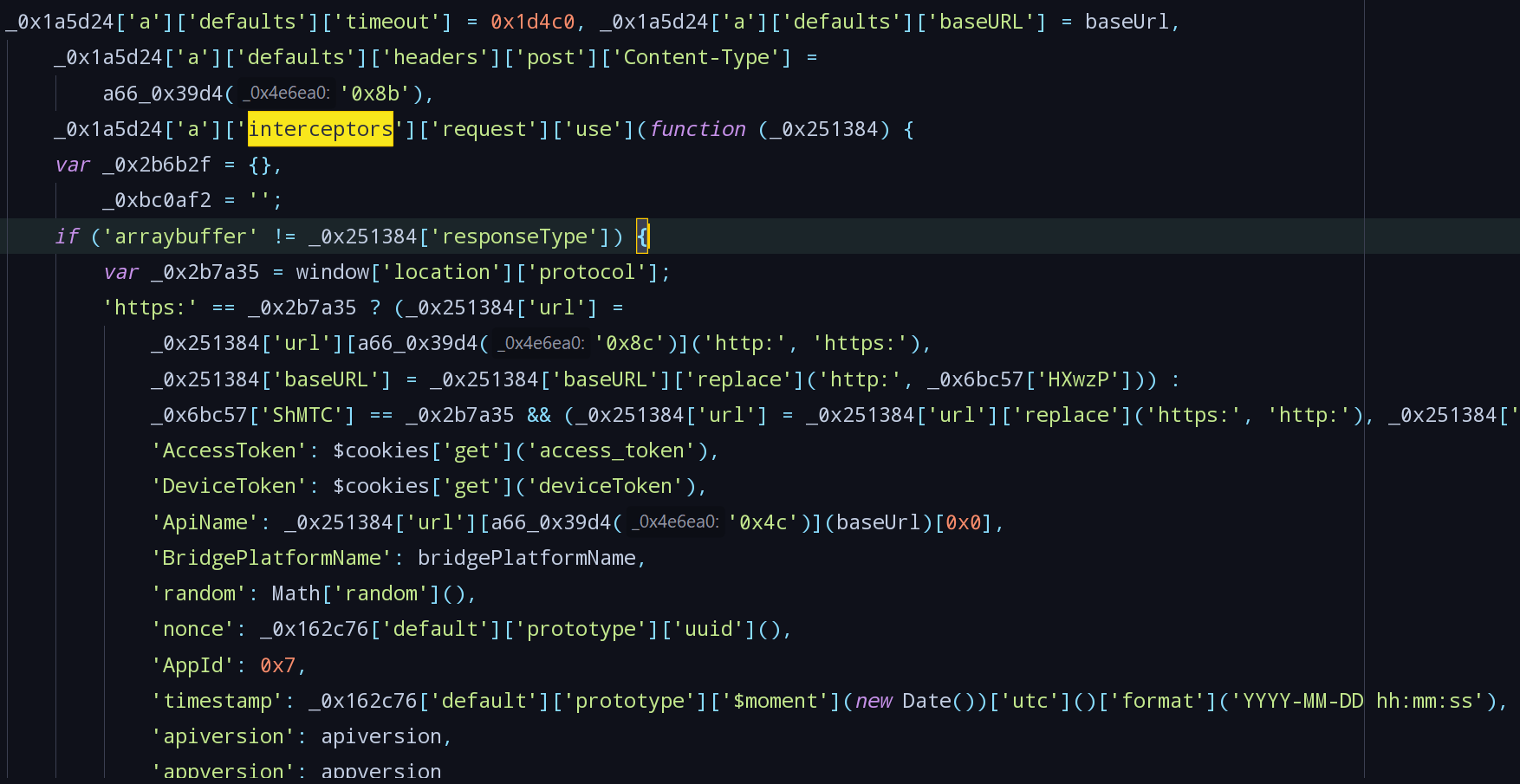
- 所有的字段均在拦截器中定义吗,其中nonce字段为调用的uuid函数,直接搜索
['prototype']['uuid'],找到函数定义:
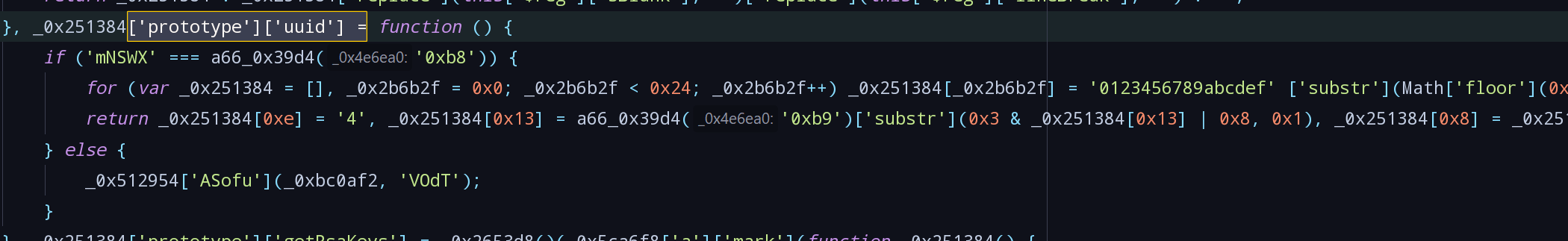
- 函数中仅有
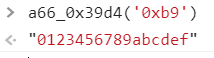
a66_0x39d4('0xb9')是未知的,调用函数,找到对应数值为'0123456789abcdef':
- 拖进jsnice,再稍加修饰,发现nouce是生成一个36位的uuid:
function uuid() { let s = []; for (let i = 0; i < 36; i++) s[i] = '0123456789abcdef'.substr(Math.floor(16 * Math.random()), 1); s[14] = '4'; s[19] = '0123456789abcdef'.substr(3 & s[19] | 8, 1); s[8] = s[13] = s[18] = s[23] = '-'; return s.join(''); } - 函数中仅有
- 最后剩下Token字段,在拦截器代码中找到定义:
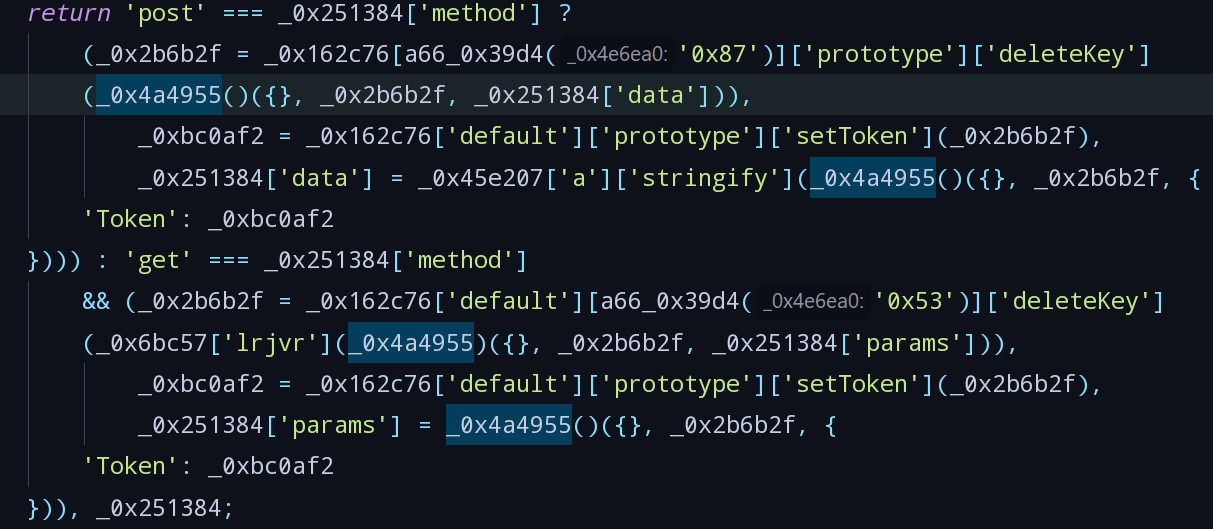
- 其中a66_0x39d4('0x87')为default,a66_0x39d4('0x53')为prototype,可以判断两者处理方式完全一致,都是将data拷贝一份,调用deleteKey函数后,再调用setToken函数,将Token赋值进data,再发送。
- 搜索
['prototype']['deleteKey']找到deleteKey函数:
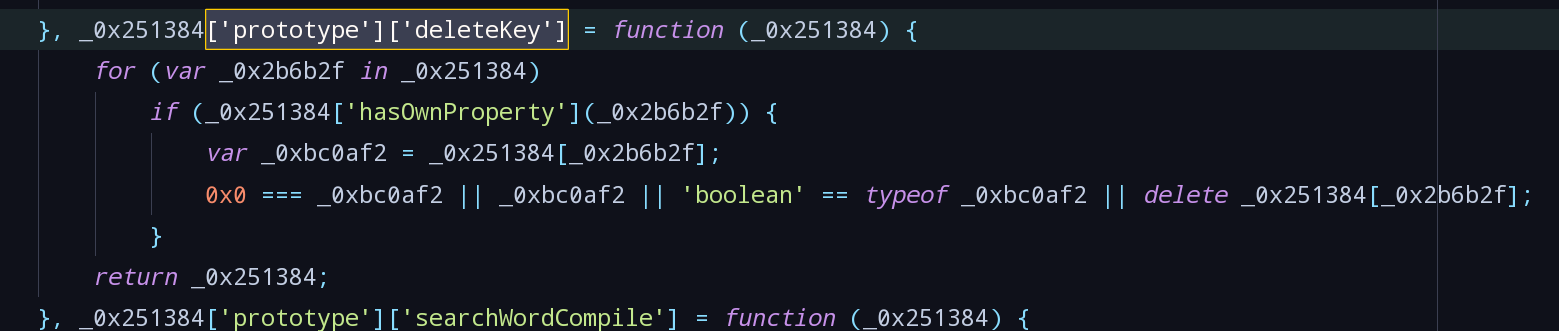
- 稍加修饰,deleteKey函数就是删除无用字段:
function deleteKey(data) { for (let word in data) { if (data.hasOwnProperty(word)) { const val = data[word]; if (!(0 === val || val || "boolean" == typeof val)) { delete data[word]; } } } return data; } - 搜索
- 搜索
setToken找到setToken函数,初步判断setToken主要是将Object类型的data根据一定格式转为字符串后加入混淆字符OI2W_YeeUw%OHutl后再加密:
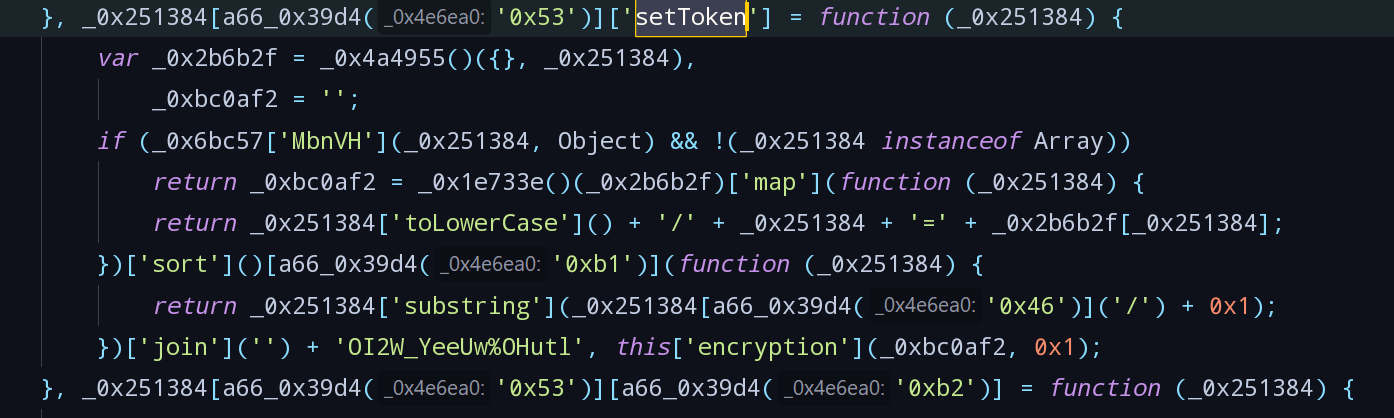
- 搜索
MbnVH找到MbnVH函数,用来判断变量类型
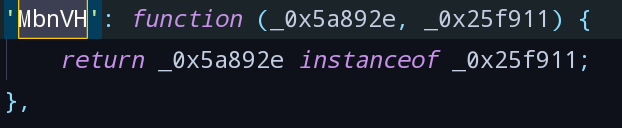
- 搜索_0x1e733e找到定义,发现其上方的与_0x591b6a有关。
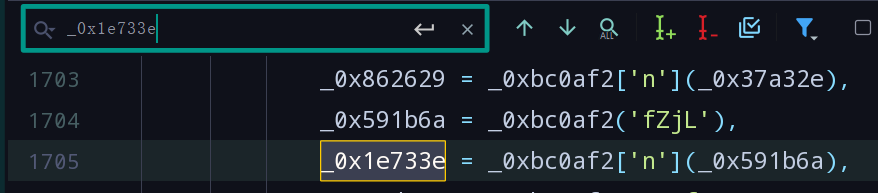
- 在
app.*.js中搜索fZjL无果,转到vendor.*.js中搜索,找到定义:
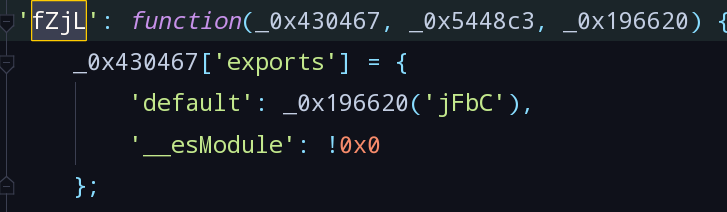
- 继续在
vendor.*.js中搜索jFbC,找到定义:
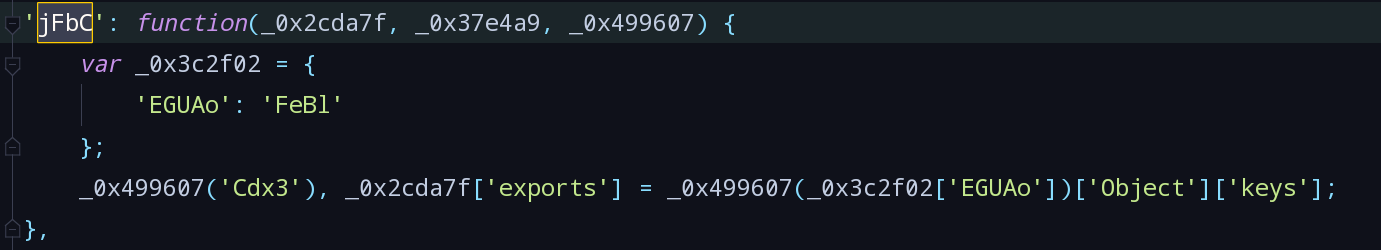
- 将未知量替换后,setToken代码如下:
function setToken(data) { let c = Object.assign({}, data); let s = Object.keys(c).map(function (k) { return k.toLowerCase() + "/" + k + "=" + c[k]; }).sort().map((vo) => { return vo.substring(vo.indexOf("/") + 1); }).join("") + "OI2W_YeeUw%OHutl"; return encryption(s,1); } - 搜索
- Token的值最终与encryption函数有关,将encryption转为utf-8编码\x65\x6E\x63\x72\x79\x70\x74\x69\x6F\x6E,找到位置:
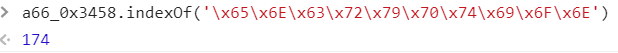
- 将174转为16进制为0xae,在
app.*.js中找到定义:
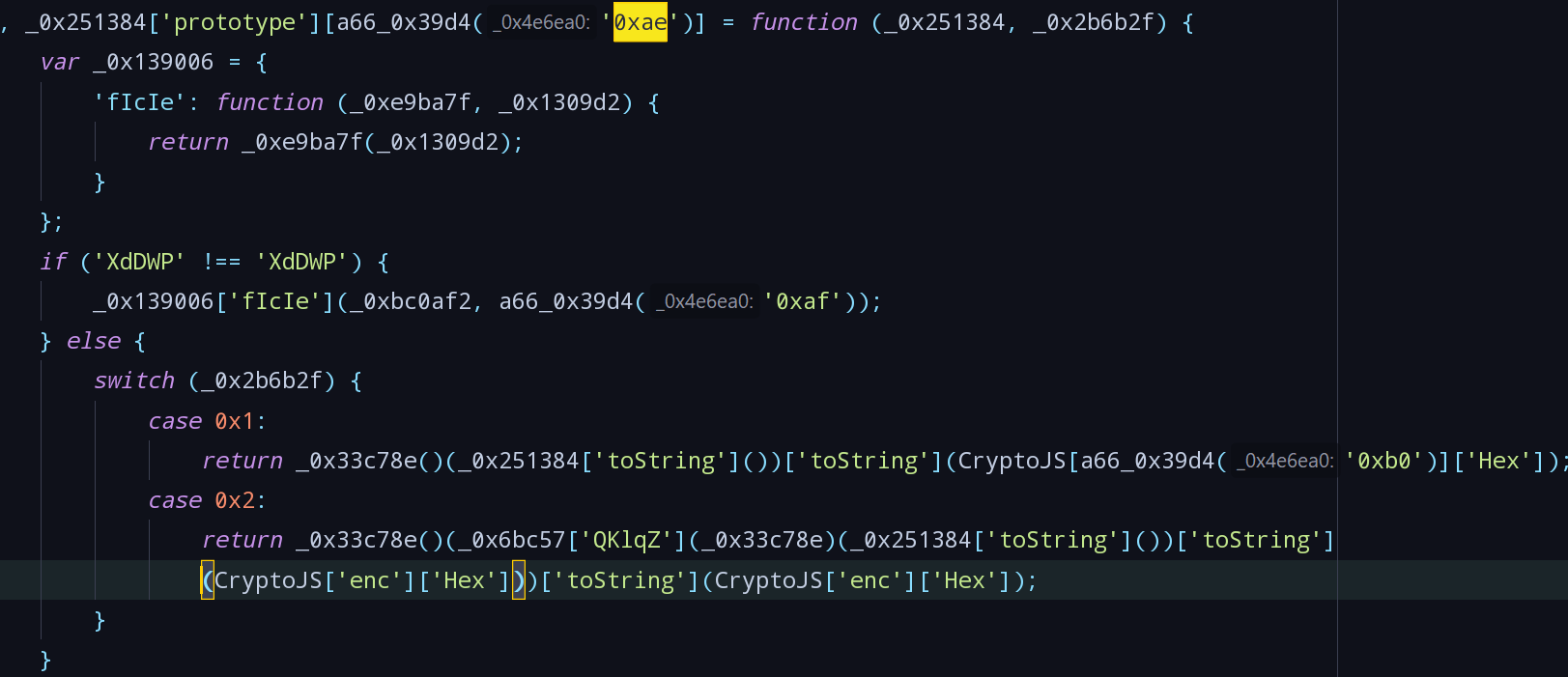
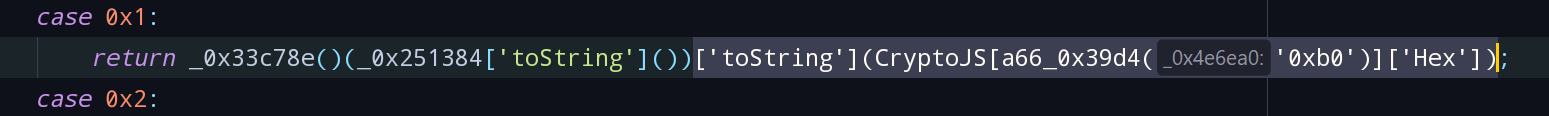
- 传入的参数值为*,1时,只调用case 0x1中的代码,看到
['toString'](CryptoJS[a66_0x39d4('0xb0')]['Hex']),初步判断是将字符串进行SHA1或MD5加密后,再进行Hex编码。
- 搜索_0x33c78e找到定义,发现其与_0x7558ee有关,简单搜索发现_0x7558ee的值为_0xbc0af2('Ff/Y'):
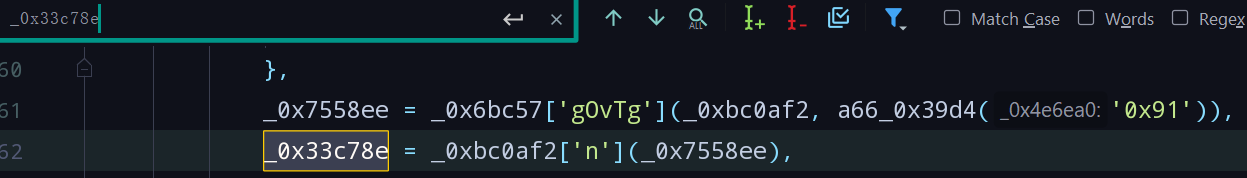

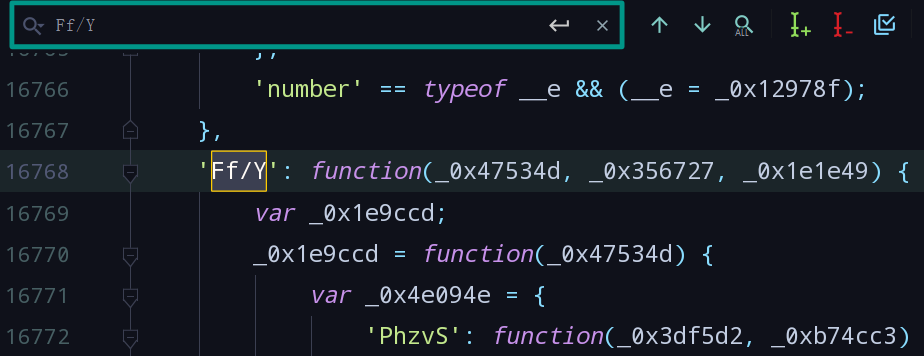
- 在
vendor.*.js中搜索Ff/Y找到代码:
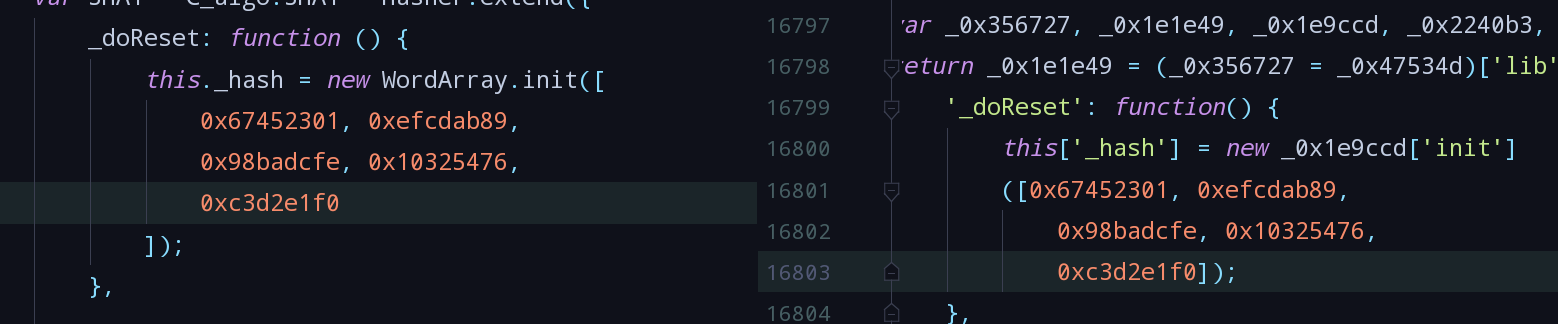
- 根据_doReset中定义的数组与crypto-js中SHA1与MD5代码比对,发现Ff/Y对应的是SHA1:
- 经过修饰,encryption函数的代码如下,将字符串SHA1加密后再Hex编码:
function encryption(val) { return Crypto.SHA1(val.toString()).toString(Crypto.enc.Hex); } - 其中a66_0x39d4('0x87')为default,a66_0x39d4('0x53')为prototype,可以判断两者处理方式完全一致,都是将data拷贝一份,调用deleteKey函数后,再调用setToken函数,将Token赋值进data,再发送。
- 至此已经知道了三个关键字段的构造方法,伪装一个
/bind请求测试,返回结果成功:
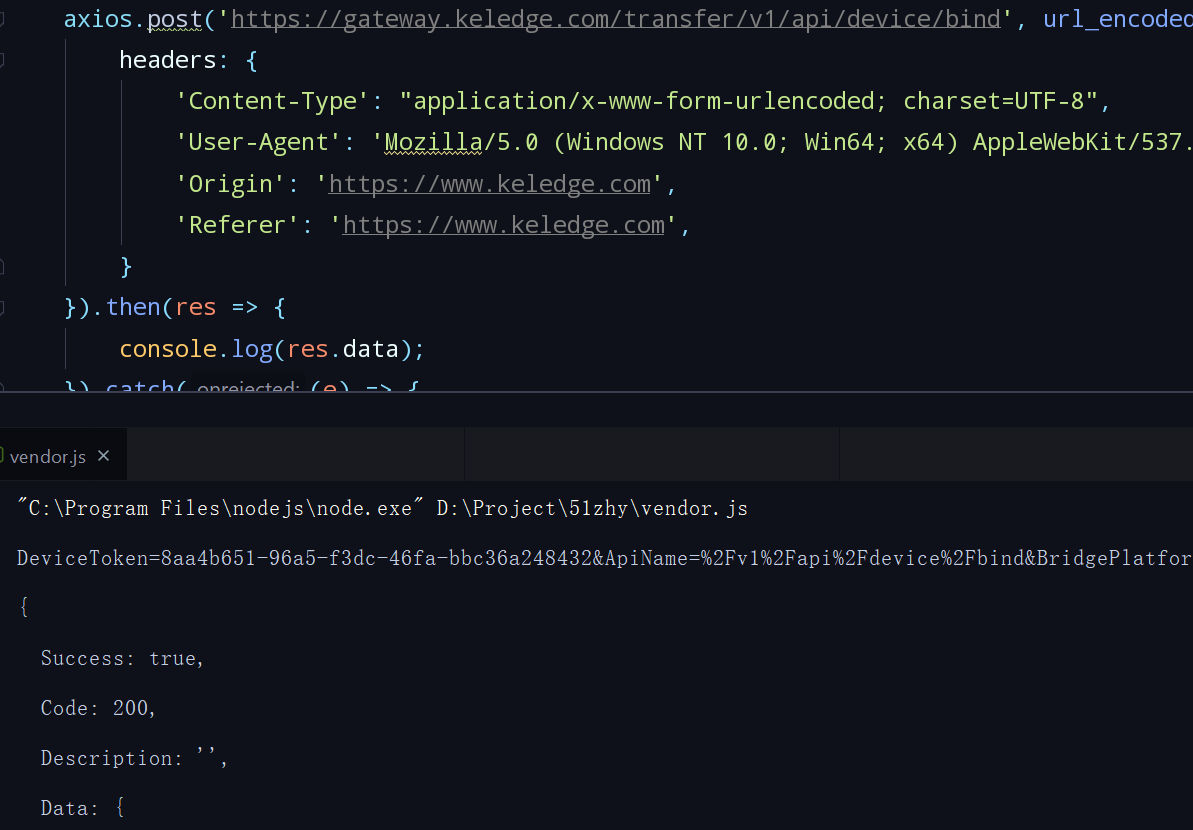
JS anti-aliasing - structure known DeviceToken, nouce with token
Guess you like
Origin www.cnblogs.com/shy-/p/12289242.html
Ranking