First statement: This is a not-so-technical to popular science articles, designed to allow those who do not have much knowledge of computer network students can have a more intuitive understanding of these tools and surfing GFW used in science, understand their principles
A, SSR? (Not drawn card oh)
A long time ago, life has not been so much the routine, the famous 404 site also can be accessed directly, our Internet is also very simple.
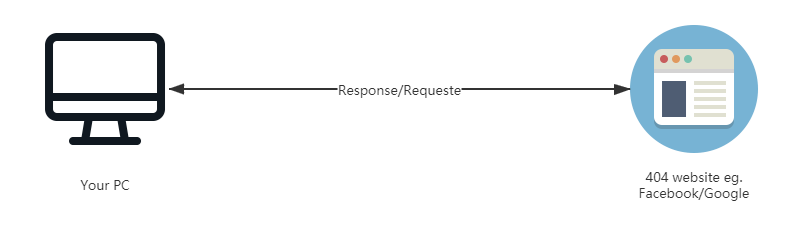
User's request to the service provider, the service provider to its data / information back to the user
Later, it all changed, the network becomes cloudy again, this time the network is managed by GFW. It is this relationship strong third party, it is in the middle users and services, dispose of it does not like the message. Each request and will return after GFW, every time access to information will be passed filtering rules it set in.
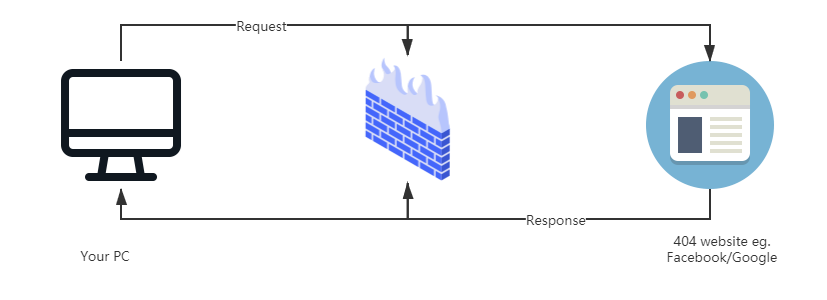
If you trigger filtering rules ? Such a response would be content Connection Reset, there is no way to receive regular content.
Deep packet inspection (Deep packet inspection, DPI) in the application layer is a data transfer on the network detection and processing technology is widely used in intrusion detection, traffic analysis and data mining. To consider the literal meaning, the term "depth" relative to the ordinary terms --DPI detecting packets of the message content and protocol characteristics detected. Based on the necessary hardware facilities, appropriate detection model and the corresponding pattern matching algorithms, GFW be able to accurately and quickly determine the suspicious traffic contrary to the standards expected from a real-time network environment, and this timely review which is expected to deal measures.
Is there a way to bypass the GFW filtering rules it? There are three proxy means
- Socks may agent TCP and UDP connections, but in plaintext packets, still can not escape the detection;
- HTTP can have TLS blessing, but only proxy TCP connections on UDP invalid;
- VPN proxy can include TCP / UDP including a variety of connections, but almost all of the VPN will forward the data, while access to Google, and may not be able to see some of the fan drama Bilibili the (copyright issues).
clowwindy open his program, this is what we usually referred to the SS.
Before speaking ss we come to talk about SSH Tunnel and Socks , in fact, we think a lot of ways to bypass the GFW, but SSH Tunnel this method a lot of people, relatively strong vitality, so we have to introduce it in detail.
SSH principles are contained in the following picture inside this:
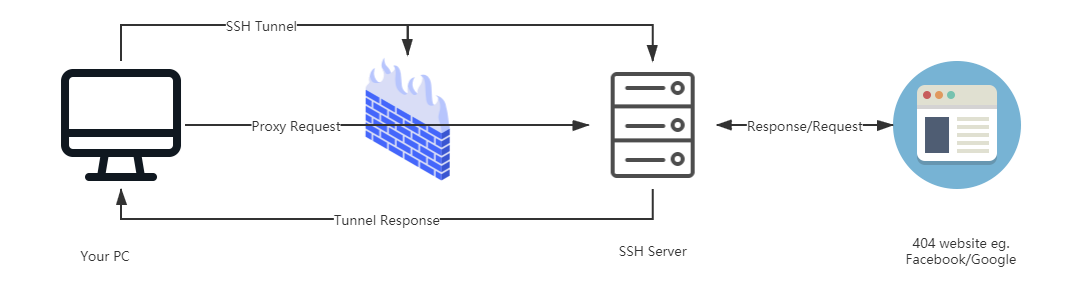
Users and foreign-based servers set up SSH encrypted channel, the user through this channel to the true identity of SSH Server service sends a request, the information returned through the SSH Server, create good SSH Tunnel before passing back to the user.
Here we should also see almost understand, in detail talk about the SS the following principles
1) Socks 5 proxy ordinary
Why not use common proxy it? Na Young, Naive
If the direct application Socks5 protocol to interact with the client is your host server and its entire interaction process or exposure across the Internet, if you use this way of seeing the outside world, will soon be GFW find your proxy server ip off the dark room inside
Non-stop to replace ip is undoubtedly a very inefficient and high cost of the stupid way, so we have a more clever SS
2) works of SS
In fact, SS and Socks5 there is not much difference, but we did a cryptographic operations
SS
interaction we Socks5 protocol in the local transmission in the network is carried out to characterize this way by the ciphertext encrypted algorithm, thereby avoiding the transmission of the content to be identified.
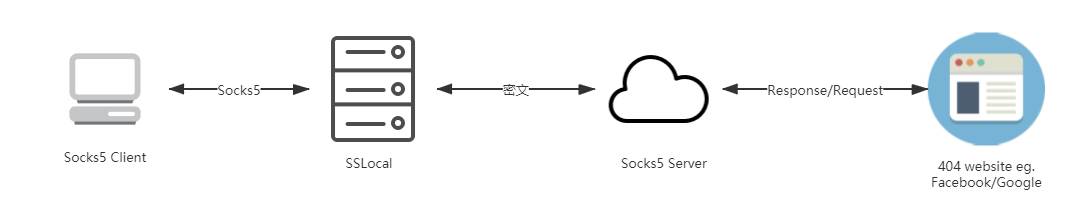
It really is no way to find it? In fact, not so safe imagined
In the eyes of real caring people, these flows to go through Socks5 protocol itself is not "normal." Imagine, your PC using the SS or SSR, large amounts of data to a fixed IP requests by protocol, and data content with ordinary data is completely different, yet secretive content of the communication through encryption, so this is very suspicious ip
如果大家对这个加密算法比较感兴趣的话,可以看一下这个RSA算法原理,这可能是计算机通信中最重要的算法
二、V2&Ray
那么就会有聪明的同学提问了,有更好的办法嘛?你不是说有三种代理手段嘛,我换一种,VPN行不行?可以,但是在这里不讨论VPN,我们来聊点更高(fan)级(suo)的东西,V2&Ray。
如果你是一个Google重度用户,但是还不知道或者是没有使用过V2&Ray,我强烈建议你去接触一下,它的某些特性非常强大。
V2&Ray 使用了它自行研发的 VMess 协议(基于TCP协议),在这里主要介绍一下这个协议
VMess 是一个无状态协议,即客户端和服务器之间不需要握手即可直接传输数据,每一次数据传输对之前和之后的其它数据传输没有影响。 VMess 的客户端发起一次请求,服务器判断该请求是否来自一个合法的客户端。如验证通过,则转发该请求,并把获得的响应发回给客户端。 VMess 使用非对称格式,即客户端发出的请求和服务器端的响应使用了不同的格式。
客户端的请求如下

- 认证信息是一个 16 字节的哈希(hash)值
- 指令部分经过了AES-128-CFB加密
在数据部分,实际的请求数据会被分成若干个部分,由一个两字节的长度L,和L个字节经过加密的数据包组成。当传输结束时,客户端必须发送一个空的数据包,即 L = 0(不加密) 或认证数据长度(有加密),来表示传输结束。
在加密方式这个地方大家也许看的出来,V2%&Ray和ss的区别, ss 很看重加密方式的选择,而在VMess 协议里,加密方式是由客户端来选择的,服务器做自适应。
那么你说了这么多,V2&Ray到底好在哪里呢?我摘抄一段它配置指南上的说明
- Better agreement: V2 & Ray uses a new self-developed VMess agreement, to correct some of the shortcomings of the existing SS, harder to detect GFW
- More powerful performance: network performance better, specific data may see the official blog (404 to hold the links)
- Richer functionality : including the concurrent performance, rich functionality and dynamic routing ports etc.
Explanation
Because the updated version V2 & Ray's really soon, do not know what will become of the future, VMess agreement mentioned in the text are based on the current version, when you read the Notice.
This article is intended to analyze the functions of these protocols and proxy tools, used only for network-related learning, because there are mechanisms for sensitive words, there is no way to break out the full name, we can do a proper understanding
reference
VMess protocol (see the official website)