Http in Auth:
Divided into two kinds:
- authorization: permissions. eg: non-administrator backend call interface 403 (insufficient privileges)
- authentication: Authentication for user name and password to log in. Error code is 401. (not logged in)
How to authenticate the identity of HTTP:
http is stateless cause a problem:
To sign in the first request, the second time when a request to perform a number of operations in this request is a request I do not know trail is already logged in, so the second time a request is stateless. How to ensure that the server request 2nd request is logged into a client just once again initiated?
Auth authentication method:
1.Session (the old way)
session configuration is stored in the server-end storing the key-value in memory.
http request first login, the server will record a complete login and sessionId value. If the value contains metadata information, and to send to the client under sessionId, such as when the next one will sessionId request to the server to the Cookie, the server will be based on the Cookie in sessionId go, a match is found on the this user authentication is completed. Then may return some of the information. .
Disadvantage: session stored by default in the current server, if a distributed processing nginx reverse proxy machine to 3, wherein a first request to a machine, the second request may obtain registration completion information, at this time may the reason is because the load balancing hit a stage other two machines, with no corresponding session on the machine at this time, resulting in that there is no login. Solution: nginx configuration is based on a balanced program load client ip hash of the session or saved to a shared sever.
There are species they want to solve the stateless problem: every request to bring a username and password verification, and then check for other operations successfully. [This is a very formal way, it seems stupid]
2. Authorization: Header of an Http, formatted request in the form of: TYPE XXXX
Its two forms:
- Basic: The user name and password directly into the content part. I each request will bring the Authorization Header. That is, each carries a username and password to upload. Of course, the user name and password for a simple process:. Base64 (username, password) server, parses for Header Basic type is found, the contents of the decode Base64.decode out of. (Do not worry intercepted requests generally on https, not caught packet capture all down.) [] Simple and crude but effective (drawback: each visit is required to come up with username password authentication and database comparison, time-consuming)
- Bearer: subsequent access token. token is a token. There are many token is generated. Is more representative of JWT (json web token)
For example, users first login to submit a user name and password to the server, the server after successful authentication using a symmetric encryption algorithm AES (userid, key) containing userid, etc. to fight from a string, and then use the security key, the key is the server I know it is a long text. The encrypted cipher text to the client. Client next request will be carried to the token passed to the Authorization header in the server, the server and the token by the AES decryption algorithm to decrypt the metadata information, and then the user's identity is authenticated.
Code practical operation:
Here to express the node mounting frame and a presentation package basic-auth:
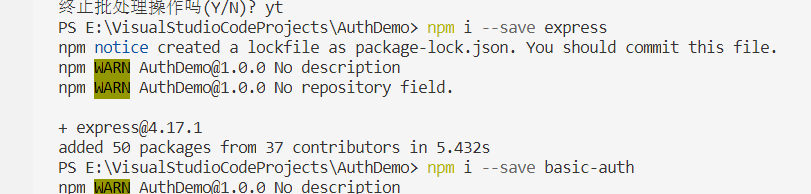

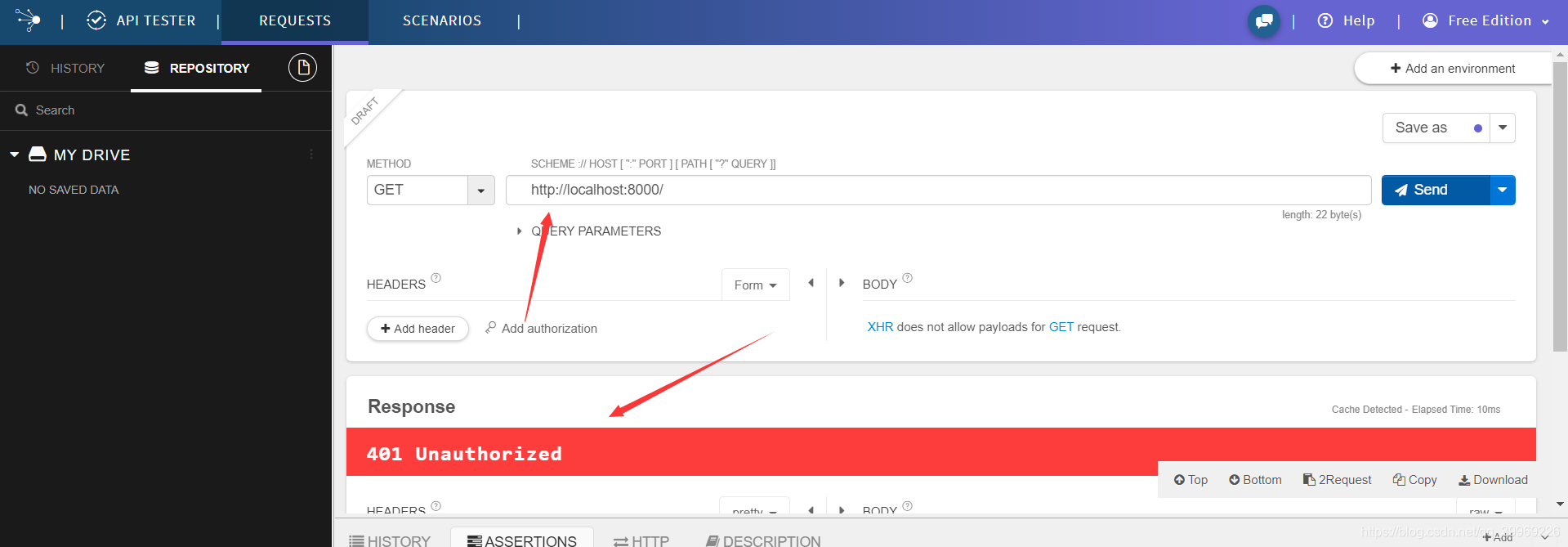

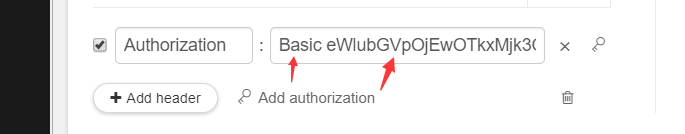
This distortion is to use base64:


For barer form typified by JWT:

Wherein the header part is marked metadata information.
header and playload just been base64 encoded and not encrypted.
The last part is the signature section, the signature is not part of the base64.
HS256 and AES is not the same, it is a Hash algorithm, one-way.
Certification principle:
User login is successful -> Generate jwt
Jwt user uploads again -> the release portion 3 and the front portion 2 and a secret operation hsah again to see whether the same results with the results of the upload.
When the user logs in successfully can record meta-information to the user in playload.
Practical operation: using the library jwt provide complete barer form of authentication
进入github查看使用方式。
需要先安装模块:
npm install jsonwebtoken
jsonwebtoken有提供过期时间。

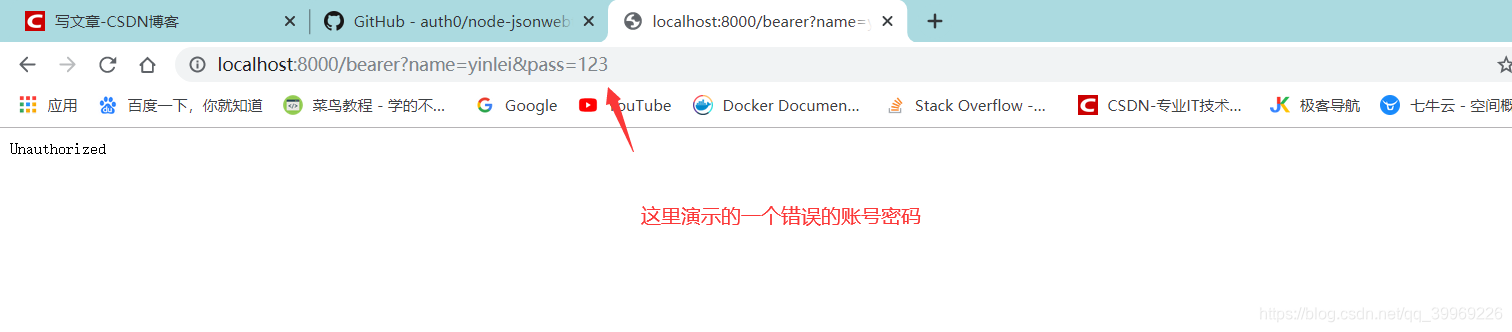
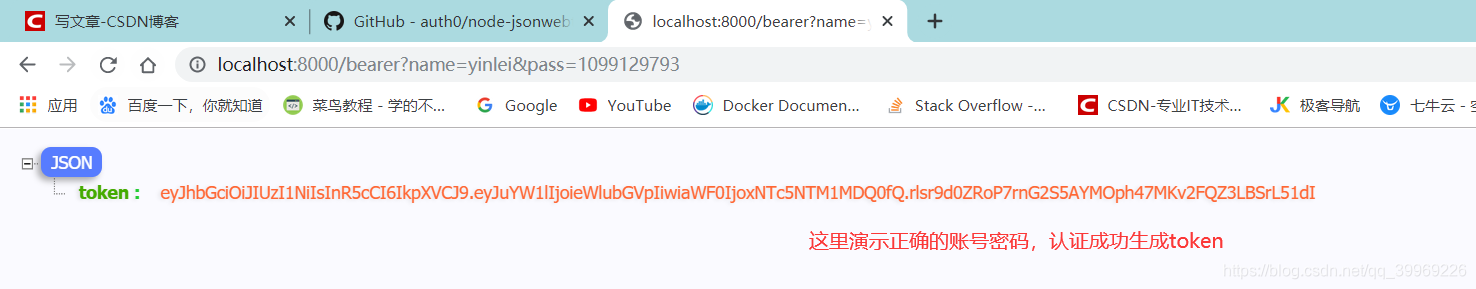
拿到这个token后只能说是登录成功了,我们还需要进行其他的操作。
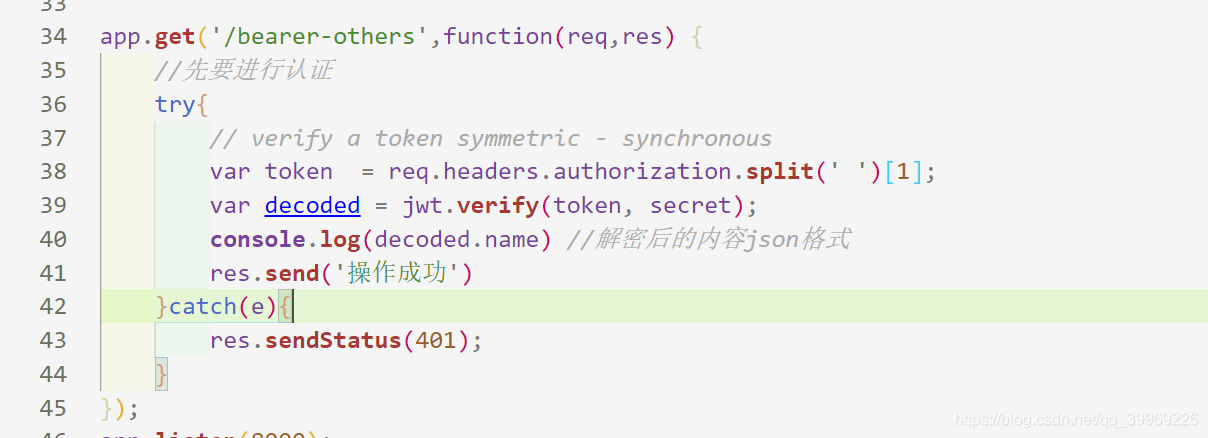
复制token,

