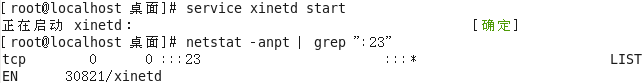
telnet tcp port 23
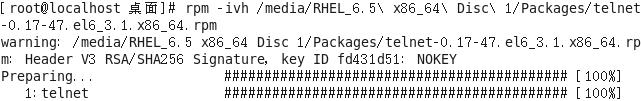
You must install before installing the server installation package dependencies

Modify the configuration file /etc/xinetd.d/telnet open telnet service
![]()

Start the telnet service
![]()
View running telnet port to port 23
Client:
Download installation package
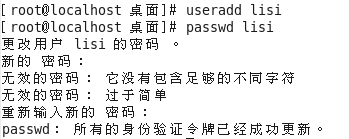
Create a new user John Doe
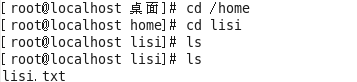
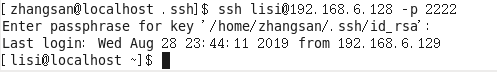
Be telnet connection

Server-side view corresponding files
John Doe View server and related processes
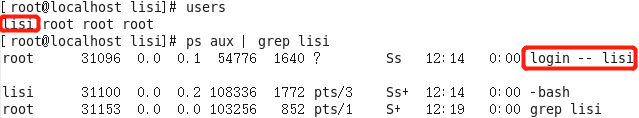
Use finger View

SSH protocol
To provide a safe environment for the client shell for remote management
The default port TCP 22
OpenSSH
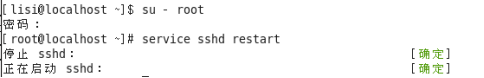
Service Name sshd
Server main program / usr / sbin / sshd
Client main program / usr / bin / ssh
Server configuration file / etc / ssh / sshd_config
Client configuration file / etc / ssh / ssh_config
Linux is behind the service d daemon daemon
Monitor service options
Port number, protocol version, monitor IP address (a little higher security protocol version 2)
Disable reverse lookup
User login control
Prohibit the root user, the user a blank password
Landing time, the number of retries
AllowUsers、DenyUsers
Login authentication objects
Server local user accounts
Login authentication
Password verification: check username password matches
Key validation: checking the customer's private key matches the public key server
Modify the configuration file
![]()


Create a new user the Five

Restart Service

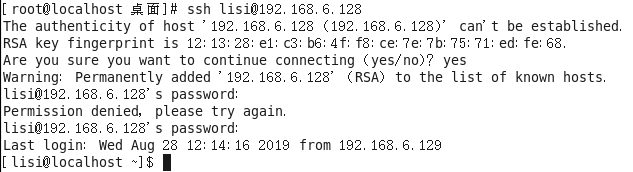
Log in with a user is denied access not allowed
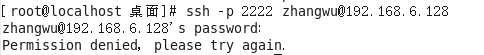
IP landing with not allowed access denied



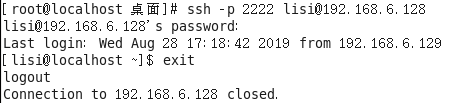
With IP and user is allowed to access
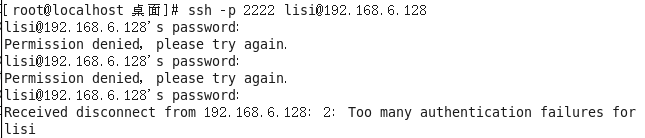
If the password is missed more than three times
Construction of key SSH authentication system for

1. Create a key pair in the client
ssh-keygen command
Available encryption algorithms: RSA or DSA
2. Create a user lisi create the .ssh directory in the SSH server
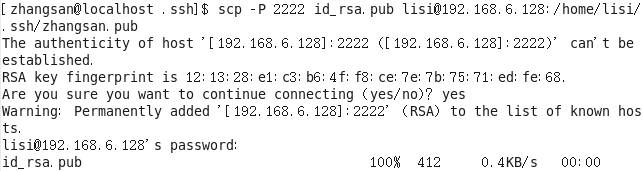
3. Upload the public key file id_rsa.pub
4. import the public key information server SSH
Public libraries: /home/lisi/.ssh/authorized_keys
5. key authentication, login server
Disable SSH password authentication server to enable public key authentication
Log in using the key server authentication
Joe Smith user to establish the client
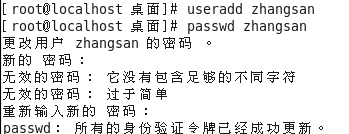
The establishment of key clients in the 123.com

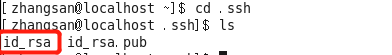
John Doe into the server's user directory created .ssh directory

上传公钥文件到服务器
服务器端查看文件
![]()
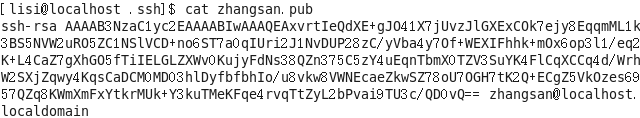
服务器端导出公钥信息

禁用服务器端的密码认证 启用公钥认证
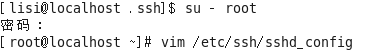

重启服务

使用密钥对验证方式 登陆服务器失败
![]()
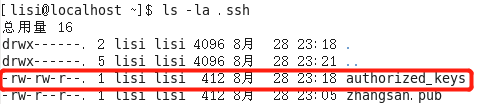
查看客户端相关文件的权限

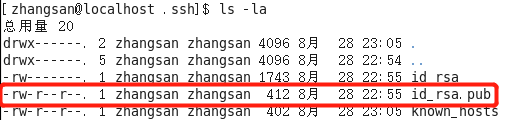
服务器端的相关文件权限

修改权限
![]()
![]()
重新启动服务后登陆 使用密钥对验证方式登陆成功
TCP Wrappers
通过tcpd主程序对其他服务程序进行包装
由其他服务程序调用libwrap.so.*链接库
访问控制策略的配置文件
/etc/hosts.allow
/etc/hosts.deny
策略的应用顺序
先检查hosts.allow 找到匹配则允许访问
否则再检查hosts.deny 找到则允许访问
若两个文件中均无匹配策略 则默认允许访问
设置访问控制策略
策略格式:服务列表:客户机地址列表
服务列表--多个服务器以逗号分隔 all表示所有服务
客户机地址列表
多个地址以逗号分隔 all表示所有地址
允许使用通配符?和* *任意长度 ?单个
网段地址 如192.168.4. 或者 192.168.4.0/255.255.255.0
区域地址 如 .test.com
策略应用 禁止其他所有地址访问受保护的服务
![]()

允许客户机的IP访问

重启服务

用被允许的客户端登陆 登陆成功
用其他IP的客户端登陆


连接失败
