introduction
Open source has far-reaching significance for the development of software that can say that it helps us to share the results, re-use software libraries developed by others, allowing us to focus on our own innovation, which promoted the rapid development of technology. According to incomplete statistics, 78 percent of enterprises are using open source, but there are many companies concerned about the security of third-party reliance park opened it? Of which only 13% of safety as the first consideration. The good news is there are still 50% of enterprises will be listed as the second or third security considerations, more and more companies starting to focus on the safety of third-party dependencies.
Why shut the security of third-party dependencies
Imagine Software Application we deliver a cake, our own development accounted for only a small part of the code, as shown below:
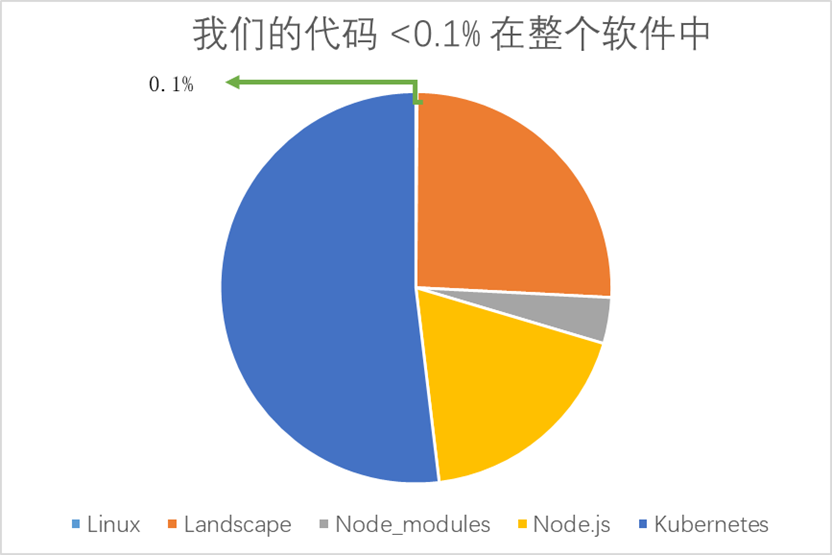
Open source is not tantamount to rely on safe, of course, does not mean unsafe, since 2000, only a few manufacturers contributions to open source, including Apache, Linux, IBM, OpenSSL etc., to 2015, anyone in contribution to the open source community, following figure is a mainstream software development library, a huge number
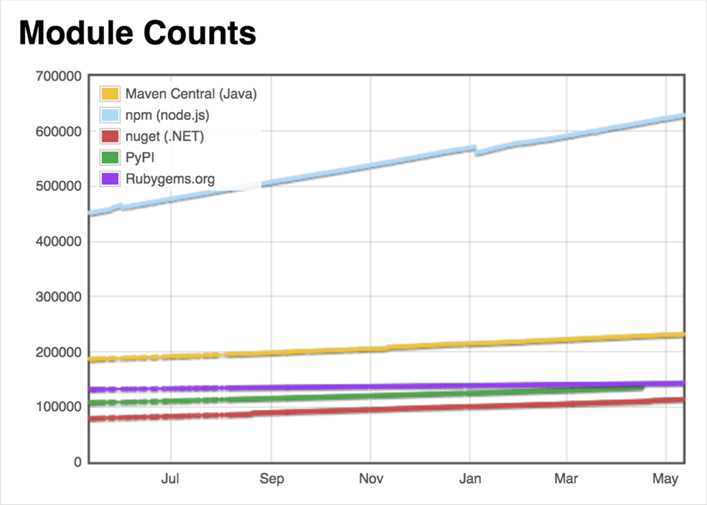
And when we use these dependencies, you must be aware of:
- Open source is often dependent rarely tested for safety
- Open source software developers generally not high on safety awareness
- Open source software provider is no extra budget for safety testing
- The main target for hackers is open source, because a large attack, affected area
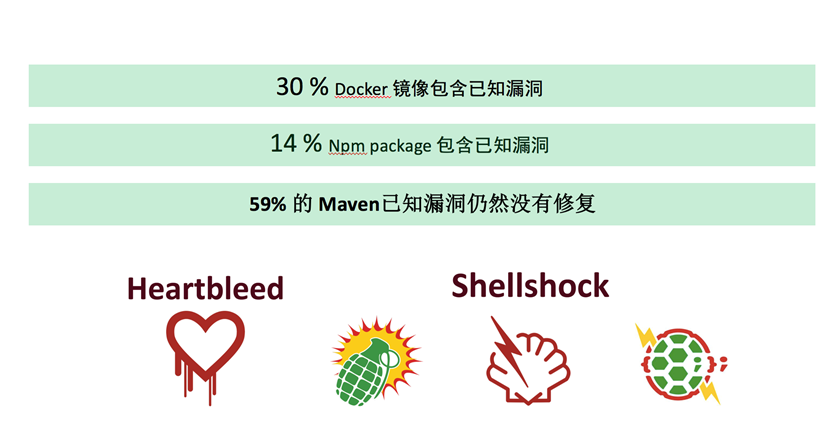
Let's look at survey data sets rely on third-party security together:
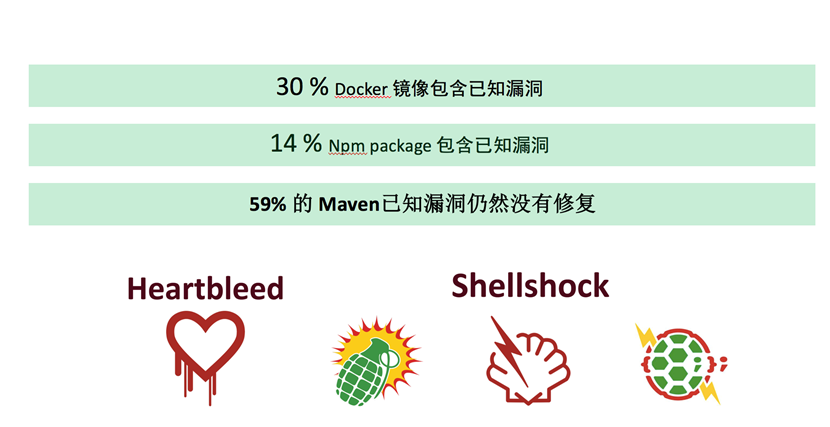
How to manage third-party security dependence
We see that the third party is dependent on the presence of a very large security risk, then we should do it? Do not use third-party reliance is clearly unrealistic, we summarize the four steps
- You have to know what the use of dependence
- You do not need to delete dependence
- Find and fix the currently known vulnerabilities
- Continuously monitors newly discovered vulnerabilities, repeat the first three steps
Dependency analysis
Relatively simple, we use the current dependency management tool can easily do, such as the maven dependency tree
Delete unneeded dependence
We find it in time for developers to maintain dependence, even if the dependent no longer applies, but does not remove, which obviously will expand the scope of hacker attack, so we need to check periodically remove unneeded dependence
Find and fix bugs
第三步开始较为复杂,所幸已有很多开源组织提供了免费的漏洞库,如US-CERT,NVD,OSVDB等漏洞广播源,该类组织集中维护发现的已知漏洞,对外提供表述漏洞数据描述以及漏洞广播,为开源社区安全提供数据支持,有了漏洞数据源之后,判断我们的依赖中是否有依赖就简单了,我们仅需要根据我们的依赖包与漏洞数据库进行对比,就可以发现我们发布的应用中是否包含已知的漏洞,甚至有些开源组织会在漏洞库的基础上提供关于漏洞的修复建议,如 Synk.io,JFrog 和 Sync 合作贡献了一个漏洞数据源(JXray),其中包含主流漏洞数据源,包括刚才提到的几个,这样我们就可以对我们包含对漏洞进行漏洞升级。
JXray 漏洞数据源
持续监听新的漏洞
我们知道漏洞是持续增长的,近几年每年平均都有900左右的新漏洞,我们需要持续监听这些新产生的漏洞,并与我们内部软件生命周期集成,与DevOps有机结合(DevSecOps),这显然需要一套平台或系统帮助我们系统的管理第三方漏洞安全,下面我们整理了一个漏洞扫描平台技术需求设计
漏洞扫描平台技术需求设计

JFrog Xray 介绍
JFrog Xray 是一个通用的漏洞扫描平台,可以满足我们对第三方漏洞安全管理的所有需求,其主要有以下几个特性
支持多语言漏洞扫描
Java,Docker,Npm,Python,Ruby Gems,Nuget,Rpm,Debian等主流语言漏洞扫描,统一对所有开发技术栈进行安全管理
深入扫描能力
我们会深入分析软件的依赖及其传递依赖,甚至是Docker 镜像中的操作系统层,如Docker 镜像中ubuntu操作系统Layer中某一个debian包存在漏洞。下图是一个Docker 镜像中包含的一个基础maven jar包含漏洞的分析图
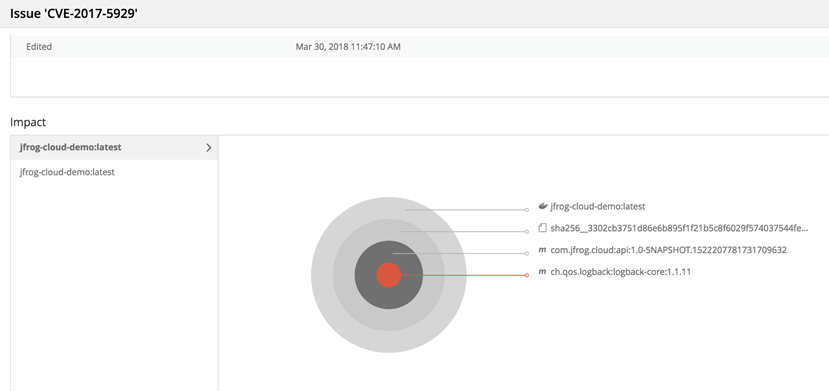
影响范围分析
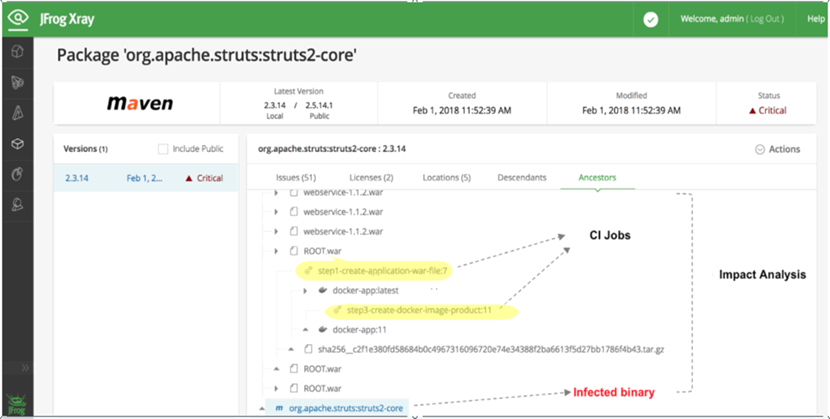
当我们监听到一个新的漏洞后,我们往往很难定为其被哪些项目依赖并试用,极为耗时,且总会有遗漏的情况出现,提高了企业损失的几率。
JFrog Xray 会根据所有收集到的依赖拓扑,进行反向依赖性分析,逐层找到所有包含漏洞包的上层应用。快速分析漏洞的影响范围,评估漏洞上线风险,指导企业进行漏洞修复
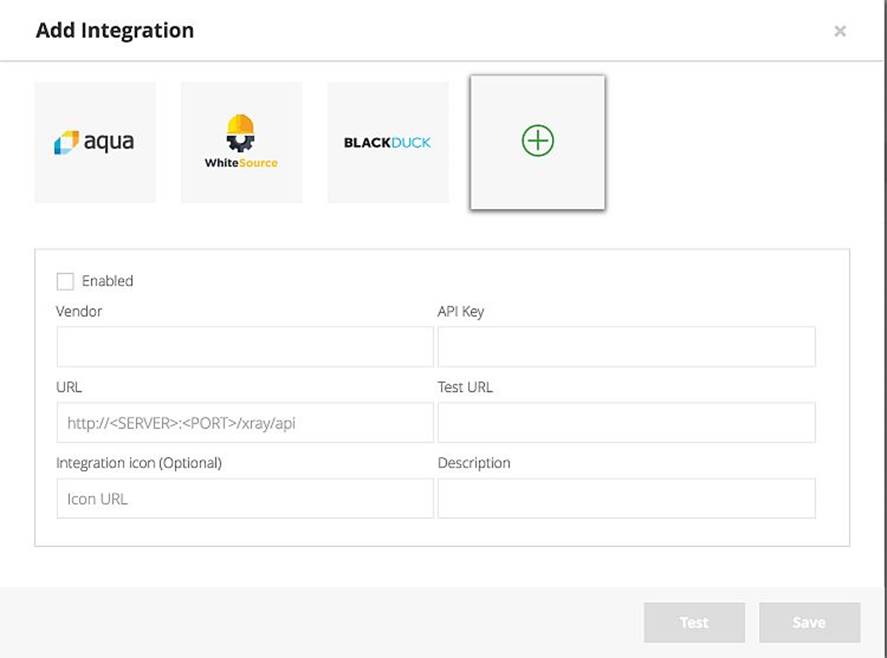
开放式集成
可以扩展与其他第三方漏洞数据平台集成,如Whitesource,Blackduck等,通过Xray 平台提供的Rest Api,甚至可以与企业自己漏洞数据源进行集成,形成企业安全的统一管理闭环。
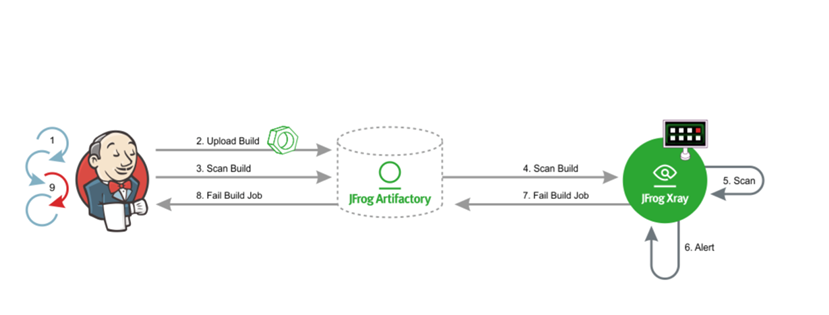
DevOps 集成能力(DevSecOps)
我们可以在软件持续交付流水线中集成漏洞扫描能力,将安全机制集成进来,作为企业软件质量关卡中的一部分,当发现漏洞的时候,阻止漏洞包交付到生产环境,如下图
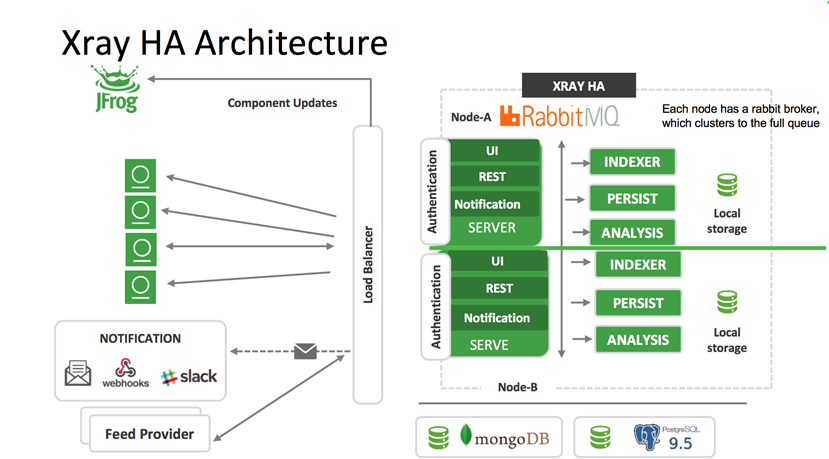
JFrog Xray 架构介绍
JFrog Xray 采用微服务架构设计,其中主要包含以下几个微服务,
l Server,主服务,UI
l Indexer,索引层,进行软件包索引
l Persist,持久层,存储漏洞及扫描结果
l Analysis,分析层,分析依赖拓扑及反向依赖,发现漏洞并告警
JFrog Xray同时支持高可用集群方式,针对企业级安全管理,提高漏洞扫描的效率及稳定性,并且与 JFrog Artifactory 通用二进制包管理系统原生集成,共同组成制品管理统一管理方案。
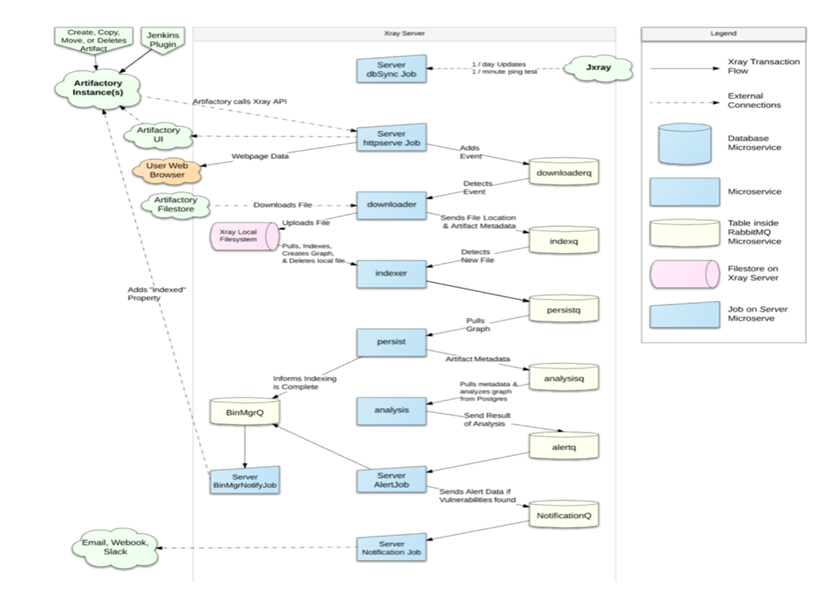
微服务数据流
总结
本次分享,介绍了在使用第三方依赖时的安全隐患,以及针对该类问题,我们应该如何管理第三方依赖的安全,同时介绍了JFrog Xray 的安全管理特性,帮助企业轻松管理第三方漏洞,降低企业安全风险,避免含有漏洞的包上线到生产环境或客户环境中。

扩展阅读
JFrog Xray试用地址:http://www.jfrogchina.com/artifactory/free-trial/