Another application of this look at the Firewall scenario, the Azure, if we want to access the Azure PaaS in VNET service, internet traffic does not go in, but Microsoft's backbone access, but this is actually not the most better path, traffic will actually come to like internet access as a gateway, and then went through the gateway service paas, in PaaS service you will see the source VM's IP access is public ip, if you want direct access vm paas service, you can vnet endpoint by Azure.
Look at the introduction of endpoint
Virtual network (VNet) service endpoints can VNet virtual network identified by the private address space and is directly connected to the extended service Azure. Use can protect critical endpoints Azure service resources, allowing only the customer's own virtual network to access it. Sent to the Azure services from VNet flow always remains in the Azure backbone network.
Service endpoint provides the following benefits:
Improve the security of Azure service resources : VNet private address space may overlap, and therefore can not be used to uniquely identify traffic from VNet of. You can access the Azure service will be limited resources to your virtual network by VNet identification extension to service, service endpoint. After the service endpoint is enabled in the virtual network, virtual network rules can be added to the resource, protecting Azure service resources in the virtual network. This completely eliminates the possibility of access to resources through the public Internet, and only allow traffic from their own virtual networks, thereby improving safety.
Azure service the best route traffic from virtual networks : currently, the virtual network to force Internet traffic destined for any route in the local and / or virtual devices (known as mandatory tunnel) will force the Azure service traffic using the same routing and Internet traffic . Service endpoint to provide the best route for traffic Azure.
Services will always flow directly from the endpoint of the virtual network services on Azure forwarded to the backbone network. Azure traffic will remain on the backbone network through continuous auditing and monitoring force tunneling outbound Internet traffic from virtual networks without affecting service flow.
Set up a simple, less administrative overhead : no longer need to retain public IP address of the virtual network resources through IP protection Azure firewall. You can set the service endpoint or gateway device without using NAT. Subnet single click, you can configure the service endpoint. With no endpoint maintenance-related overhead.
Sounds good, but the endpoint is actually a regional service, for example, you have a vnet in the North, paas a service in the East, such a scenario would not have even opened the endpoint effect
In fact, this time in conjunction with Azure firewall can be resolved, provided that the azure firewall deployed in the East
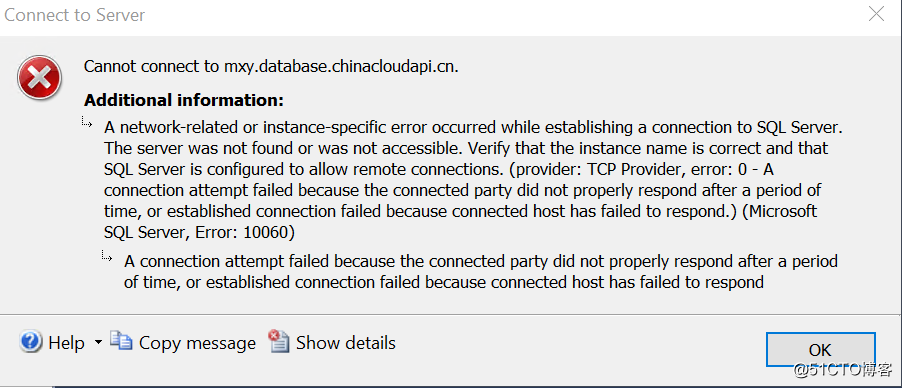
First look at the absence of an appropriate endpoint access scenario, because the default route to FW, FW rules if there is no network allows access to Azure SQL, access is denied, even if the addition of Azure SQL whitelist useless
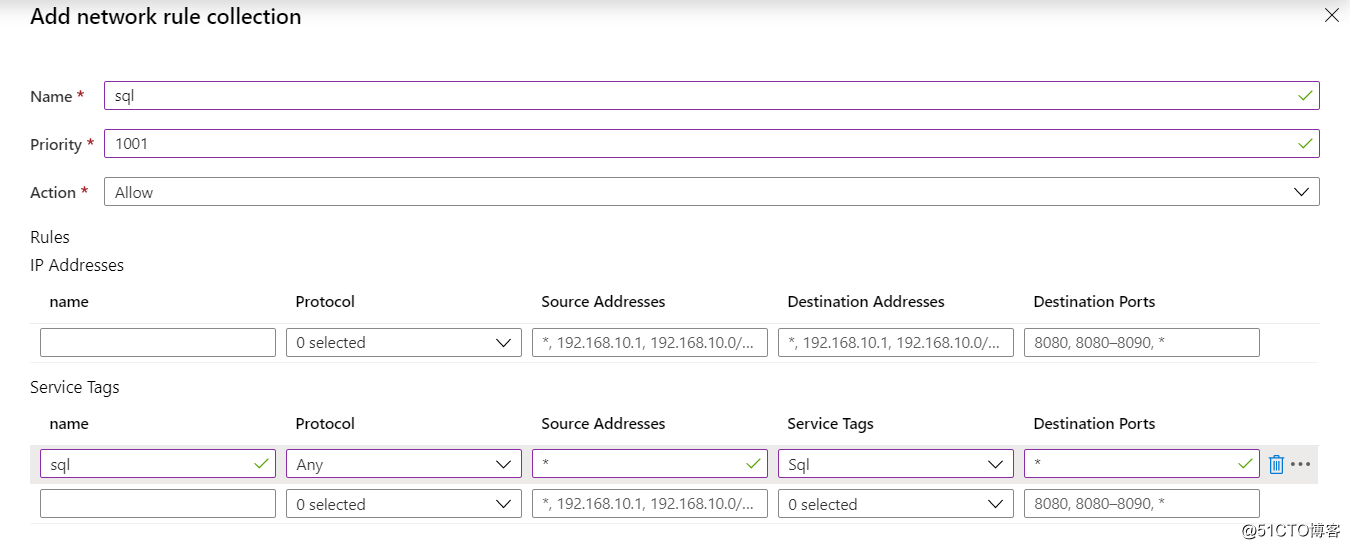
Next, add in the first FW rules allow outbound access to the azure sql, can be seen here, and nsg similar, firewall can also be held in a service tag to add a rule, it is convenient
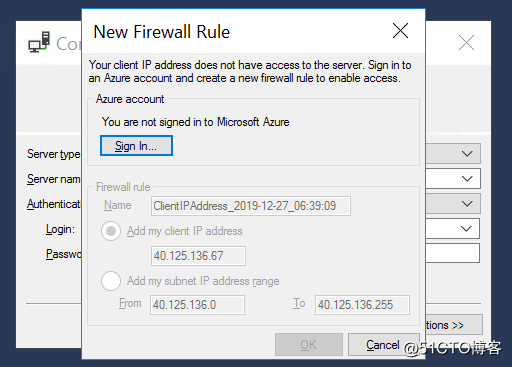
This can be seen, suggesting that we do not add to the white list, but at least through the network must be
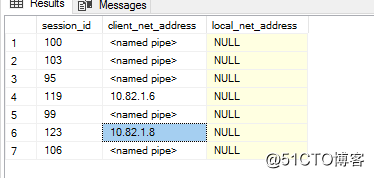
Here's the FW IP added to it, the normal connection
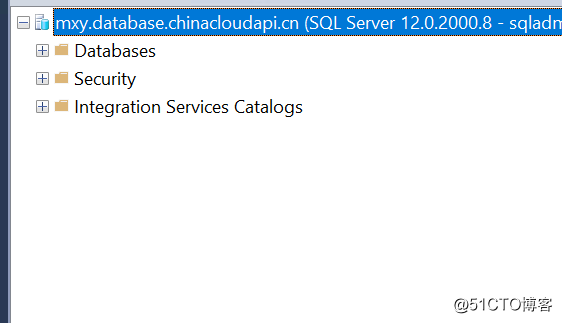
You can see the source IP is the IP of the FW
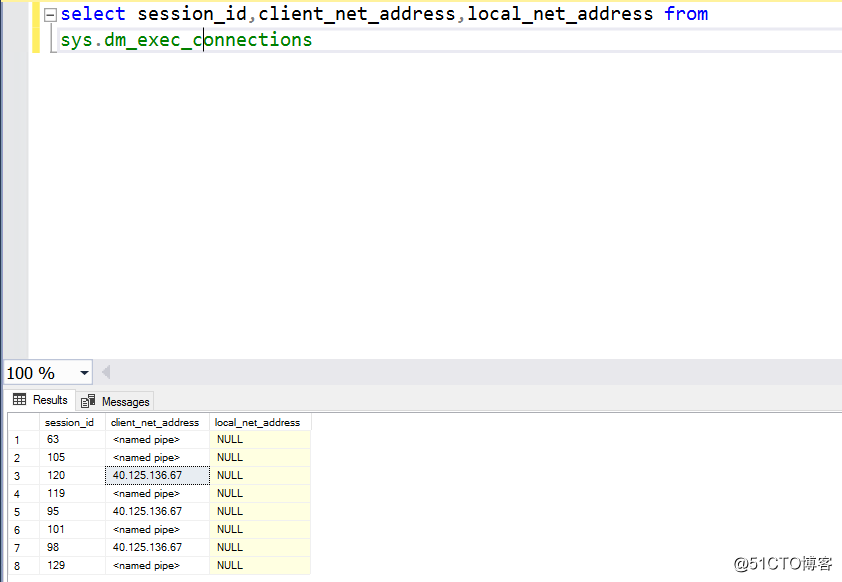
Next, add the sql in the subnet firewall endpoint
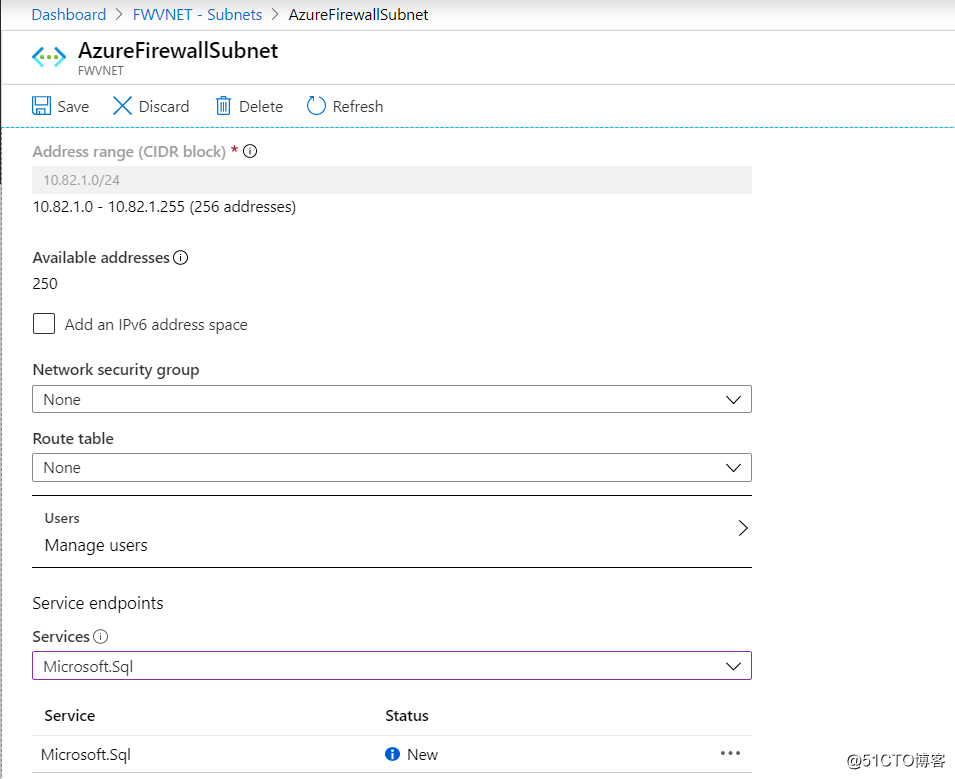
After that, add in the azure sql where the firewall to allow access subnet
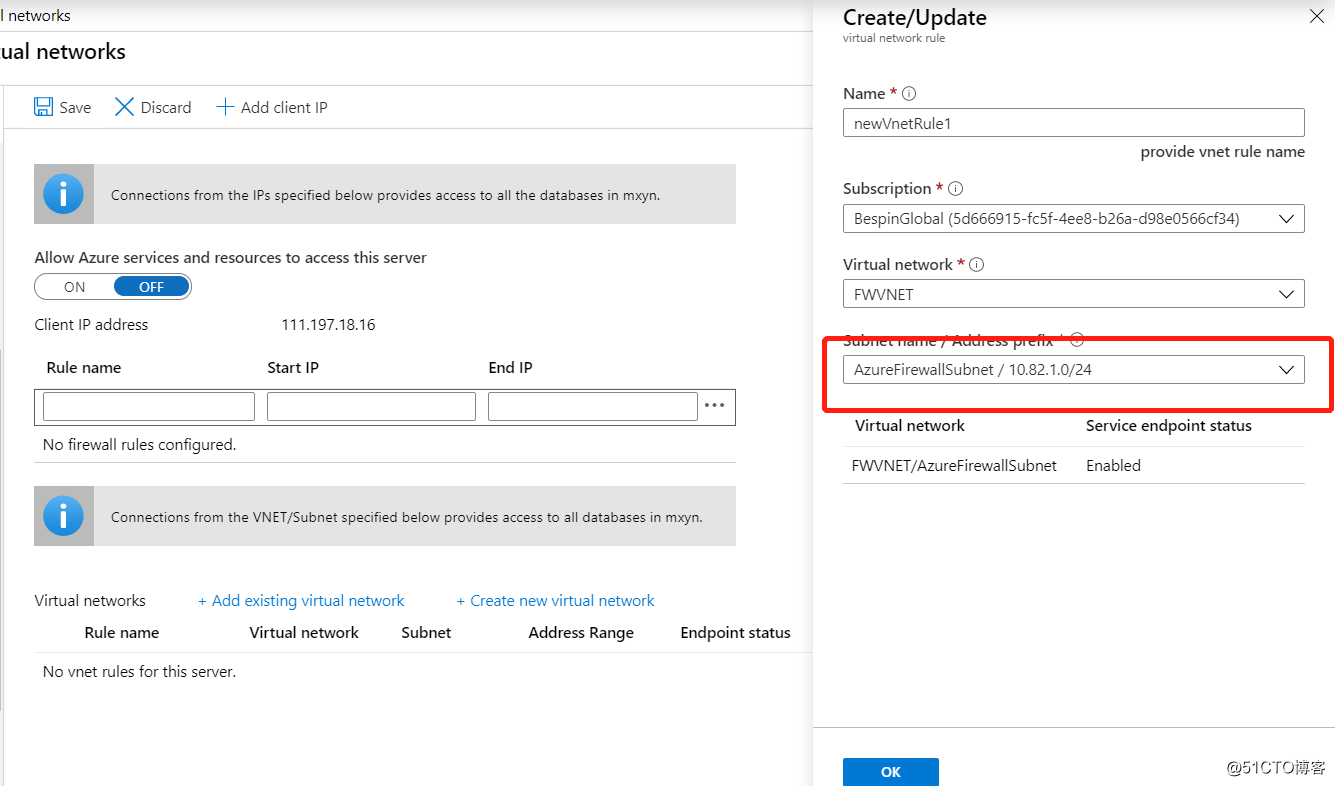
This time try again, can already see IP access network is the firewall of the IP!