The main causes of vulnerability resulting in a systematic mechanism and coding standards in terms of both the openness of the network protocol, currently the majority of Web vulnerabilities
A typical system with regard to the mechanism of the vulnerability JavaScript / CSS history hack, while the typical normative loopholes encoded with efforts vulnerability (Heart Bleed).
In a certain understanding of the concept of vulnerability, we will set up a test site for CSS cheat, SQL injection and CSRF attacks carried out experimental tests.
JavaScript / CSS history hack vulnerability
Vulnerability: the attacker can obtain some of the history of the user's browser.
Attacks: Using the browser to automatically query history, and CSS for visited and unvisited hyperlinks different rendering styles. For example, Baidu this link is purple, because you recently visited Baidu. The self https server CA certificate to build this link is black, because you are not currently visited my last blog. If it is purple, refresh after deleting access history will turn black.
Attack: Because JavaScript can read the CSS element of any information, they are able to distinguish the browser which style is applied to determine whether a user has visited the link. An attacker can set up their own websites, some sites define the hyperlinks above. When other users access the site, the browser will automatically determine the user based on the history of what was once visited URLs, which is presented to the user in a different color.
The attacker's website background can be user visited the site back to the server, to the effect that can detect whether a user has visited a site, but not direct access to the history of user access.
The vulnerability has been fixed, although now able to see the different display hyperlinks state, but has been unable to get to js color differences.
Heart Bleed Vulnerability
Also known as heartbleed, number (CVE-2014-0160)
The origin of vulnerability: the vulnerability Google white hat Neil Mehta (Neel Mehta) suggested that he may get random logbook from 64k on a particular server, the whole process as phishing, attacks can be continued again, by a large number of sensitive data leak .
Cause: failed before calling user input in memcpy () encoding, the length of bounds checking. An attacker can input bytes out of range, and then returns the cached content equal length.
Attack:
OpenSSL has called Heartbeat (heartbeat) to expand the so-called heartbeat detection, is to create a Client Hello inquiries to detect the other party is not a normal online server, the server sends back Server hello, indicate normal SSL communications. Just as we would ask each other when called "Hey you hear me?" The same.
Just a test blog has introduced a hyperlink on the SSL and https
Every inquiry will append a character length of the inquiry, if the character length is greater than the actual length, the server will still return the same size of the character information, thus forming a cross-border access memory information.
Vulnerability Impact: Every initiate a heartbeat, the server will be able to leak a little bit of data (theoretically leak up to 64K), where such data may include user login account password, e-mail and even encryption keys and other information, may not contain these information, but the attacker can continue to use the "heartbeat" for more information. In this way, bit by bit server more and more information leaks, like a slowly bleeding heart, bleeding heart hence the name, loophole has now repaired, but whether it has been utilized before the vulnerability was made on unknown.
The above is a brief introduction of two types of vulnerabilities, the following will deceive CSS, SQL injection and CSRF attacks experiment
CSS cheat
As the name suggests, CSS cheat primarily as a means of deception to the browser user presents false information.
虽然是很简单的手段,但是应用却十分广泛Deceive principle: by targeting and CSS pseudo-classes, implement web content coverage
html such as human bones, css is the appearance of decorative effect similar to nerve js control page, CSS deception is the use of CSS rendering of the page.
About targeting methods and pseudo-classes
CSS There are four ways of positioning of page elements:
- Static positioning (static): default targeting all the elements, the elements can be positioned in a static position, the so-called static default position is that each element in an HTML document flow position.
- Relative positioning (relative): flows without departing from the document, the reference position by the self-static top, bottom, left, right positioning, and may be classified by hierarchical z-index.
- Absolute positioning (absolute): from the normal flow through the top bottom, left, right select its nearest parent element is positioned, when the position of the parent static, absolute coordinate origin body element will be positioned to be the z-index hierarchical classification.
- Fixed positioning (fixed): The fixed target current visible window (browser window) and not the body or parent element, page scrolling does not move, can be hierarchically classified by z-index.
Common targeting method: Parent with child Jedi
- When the sub-elements are absolutely positioned, relatively positioned parent element, parent container so that both can retain the position of the original document stream, the sub-elements can be referred to the parent container absolute positioning.
CSS pseudo class can be used with the use of CSS classes, there are anchor pseudo-classes, first-child pseudo like.
The anchor pseudo-class:
- a: link {color: # FF0000;} / * unvisited link * /
- a: visited {color: # 00FF00;} / * * visited links /
- a: hover {color: # FF00FF;} / * * mouse across the link /
- a: active {color: # 0000FF;} / * selected link * /
Cases of fraud are: the early years of the Taobao shop fitting directly using css control page display, some companies store this information to make false.
The following information is a shop of 2012

information is not true shop information presented in the figure.

30 days actual sales value of 0, set the background through the shop decoration, showing the words 580.

"Shopping Guide" is background disguised as "high-quality business seven days no reason to return."

Evaluation and transaction details are recorded using the same background false propaganda.

The actual evaluation and no buyers, just add a background image.
Why CSS deceive simple but widely used?
Personally web browsing experience, the 4G or 4G before the beginning of that time, this picture do use fake page is very common.
最近一次是2018年双十一时候,在某电商平台申请退款,商家一直不理会,在平台进行投诉时发现提交投诉的按钮怎么点都没反应。一开始以为是手机显示不兼容,后来发现那个页面下半部分是张图片,提交按钮只是图片的一部分。
不过双十一也可以理解,但是就大多数没什么计算机基础的网民而言,CSS欺骗还是很有效的。
下面将会先介绍SQL注入,然后再将CSS欺骗与SQL注入结合,在搭建的测试网站上实现利用SQL注入前端代码进行CSS欺骗。
SQL注入
SQL注入即是指web应用程序对用户输入数据的合法性没有判断或过滤不严,攻击者可以在web应用程序中事先定义好的查询语句的结尾上添加额外的SQL语句,在管理员不知情的情况下实现非法操作,是目前最常见危险的漏洞之一。
SQL注入不是一个过期的安全问题,恰恰相反,它是一种非常容易被使用的攻击方式,SQL注入并不需要高深的攻击手段便可以轻易使敏感的数据库信息被非法浏览或删除。
一般注入过程:
- SQL注入点探测。
通过适当的分析应用程序,判断什么地方存在SQL注入点。通常只要带有输入提交的动态网页,并且动态网页访问数据库,就可能存在SQL注入漏洞。 - 收集后台数据库信息。
不同数据库的注入方法、函数都不尽相同,在注入之前先要判断一下数据库的类型。可以输入特殊字符如单引号,让程序返回错误信息,根据错误信息提示进行判断;还可以使用特定函数来判断,比如输入“1 and version()>0”,程序返回正常说明version()函数被数据库识别并执行,而version()函数是MySQL特有的函数,因此可以推断后台数据库为MySQL。 - 猜解用户名和密码。
数据库中的表和字段命名一般都是有规律的,通过构造特殊SQL语句在数据库中依次猜解出表名、字段名、字段数、用户名和密码。
网站搭建与SQL注入测试
如果有简单网站的搭建经验,只需要理解了SQL注入的原理,就可以构建自己的测试。
下图是搭建的测试网站的登陆界面:

先注册一个userA的账号并登录:

网站有三个简单的页面,分别是Home、Users、Transfer:
- Home: 显示用户的zoobars(当前网站用户的虚拟货币)数量,设置用户的个人简介。

- Users:可以搜索其他用户并显示用户财富和简介。

- Transfer:可以将自己的zoobars转给其他用户。

以下有两种SQL注入可以使得自己的zoobars变多:
- 通过填写个人简介修改自己的zoobars,会改动数据库zoobars数量
- 通过填写个人简介注入CSS代码,使得别人搜索自己时zoobars看上去变多,不会改动数据库zoobars数量
方法一
注入代码:
userA的个人简介', Zoobars='20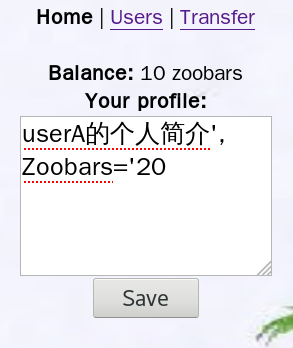
保存个人简介后刷新页面,userA的zoobars变成了20,简介显示“userA的个人简介”:

这种方法直接改动了数据库数据,后台更新个人简介的php代码如下:
<?php
if($_POST['profile_submit']) { // Check for profile submission
$profile = $_POST['profile_update'];
$sql = "UPDATE Person SET Profile='$profile' ".
"WHERE PersonID=$user->id";
$db->executeQuery($sql); // Overwrite profile in database
}
$sql = "SELECT Profile FROM Person WHERE PersonID=$user->id";
$rs = $db->executeQuery($sql);
$rs = mysqli_fetch_array($rs);
echo $rs["Profile"];
?>第4、5行的$sql值是数据库要执行的语句,方法1使得实际执行的sql语句变成了:
UPDATE Person SET Profile='userA的个人简介', Zoobars='20' WHERE PersonID=userA方法二
由于场景不同,有时候会使用方法二注入,仅修改网页的显示进行CSS欺骗:
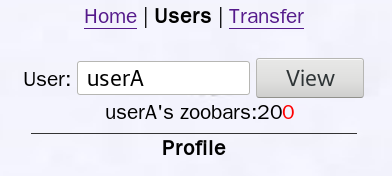
userA的zoobars数量是20,通过SQL注入前端代码,可以使得这个网站的用户在搜索userA时看到的数量为200,这里为了方便观察,欺骗的字体设置了红色。
注入代码:
<span style="color:#000000;position:relative;left:60px;top:-54px;">0</span>
与之前介绍淘宝商家用CSS直接设置背景图片不同,这里是通过SQL注入在个人简介里写了个相对定位的标签,当网站用户搜索userA的个人简介时,个人简介里的html代码会被浏览器解释渲染成数字0,并显示在zoobars数量的后面。
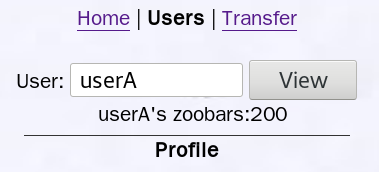
下面将介绍与浏览器机制相关的另一种攻击方式。
CSRF攻击
CSRF(Cross-site request forgery),即跨站请求伪造。
引诱浏览器用户访问自己的攻击网站进行跨站访问,通过浏览器保存用户原网站cookie的机制,在攻击网站获取用户的身份权限并伪造请求进行攻击。
浏览器机制:
当用户登录某一网站后,本地会保存一份cookie用于身份认证,如果cookie没有过期,就不需要反复进行登录操作。与JavaScript/CSS history hack不同的是,CSRF暂时无法像修改CSS或JS引擎那样进行漏洞修补,因为目前的浏览器需要这种机制。
场景模拟:程序员登录博客园浏览博客,发现一篇不错的博客后打算分享到朋友圈,但第一次分享时网页会要求先登录朋友圈。当登录分享成功后,没过多久程序员又发现一篇不错的博客,打算再次分享,以此往复循环,浏览器会怎么做?
目前浏览器的机制是会在第一次登陆后保存用户的cookie,使得用户在有效期内不必反复认证身份,所以后续的跨站不需要再登录。(没有实际操作过,也可能博客园分享每次都需要登录,只是举个例子模拟网页跨站情景)
浏览器保存cookie的机制是需要的,但同时给了攻击者可乘之机。
web中用户身份验证的漏洞:
简单的身份验证只能保证请求发自某个用户的浏览器,却不能保证请求本身是用户自愿发出的。也就是说,用户的浏览器发送了一条请求,同时浏览器的cookie也能证明用户身份,但是并不能保证这条请求是用户主动在原网站上进行的操作。
以搭建的网站为例进行攻击演示
攻击步骤:
- 搭建一个网页,用于伪造请求,请求内容是从被攻击者的账户转1个zoobar到自己账户
- 在攻击者申请的网站账户里,填写个人简介,SQL注入一个自己的网站连接
- 诱导其他用户点击攻击者账号个人简介上的网页链接进行攻击
搭建网页
原网页与代码:

Transfer界面点击Send按钮会发送一条请求,执行转账操作。
攻击者需要制作一个自己的网站,在网站上编写攻击操作。
这里直接将原网站的界面代码复制了一份,然后Send的金额写入默认值1,转账对象默认设置成攻击者的userA账户,再通过JS代码让网站在加载时自动执行Send按钮的提交操作。
Attack on the page and the code:

Although it looks the same, but we can see this through another web browser's address for the site mock attacks.
And then injected into a hyperlink Profile in:
<a href="https://localhost/myzoo/send.php">点击获取</a>URL is the attacker's own Web site

then when other users search for userA, see the following introduction:

the number of zoobars currently userB is 9, if click this link, will jump to the attacker's site and automatically switch to userA a zoobar, after 21 becomes the number of userA, userB only 8.
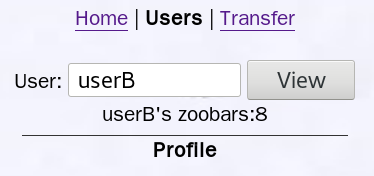

Attacks is through cookie authentication is actually saved the user's browser, a user request forgery.
There are ways to deal with a lot of CSRF attacks, there is a site Referer field is the source of judgment requested by checking the request, but this is a process of attack and defense, the attacker may also be further attacks tampering Referer field.
summary
- JavaScript / CSS history hack
takes advantage of loopholes in the browser mechanism for the convenience of users to browse and query history, certified by our CSS / JS repair. - Effort vulnerability
code does not regulate data due to disclosure vulnerability has been patched. - CSS deceive
common spoofing technique, requires a combination of other attacks based on specific scenarios. - SQL Injection
One of the most common security vulnerabilities, one of the main data leakage, high security risk than buffer overflow vulnerability to a certain extent, can be avoided. - CSRF
exploit browser vulnerabilities mechanism, not directly cure, the process is the same as a SQL injection attack and defense.