Chinese People's Public Security University
Chinese people’ public security university
Network Warfare Technology
experimental report
| The second experiment |
| Network sniffing and spoofing |
| student name |
Wang Xuan |
| grade |
201621450007 |
| District Team |
Net 6 17 |
| mentor |
Your opinion |
Institute of Technology and Information Network Security
2016 Nian 11 Yue 7 Ri
Master experimental task
2016-2017 school year, Di Yi semester
First, the purpose of the experiment
1. Deepen and digest this course lectures, review what they have learned through the Internet search techniques, methods and techniques;
2. Become familiar with commonly used network sniffer way to master the common packet capture and filtering techniques to use software can analyze network basic behavior of a given data packet; master the basic principles of ARP spoofing, DNS-based attacks and ARP spoofing;
3. The purpose of the consolidation of curriculum knowledge and practical application.
Second, the experimental requirements
1. Carefully read the contents of each experiment, we need to capture the title, to be clear screenshots and annotate screenshots and descriptions.
2. Documentation Requirements clear structure, graphic expression accurate labeling specifications. Reasoning was objective, reasonable and logical.
3. Software tools can be used office2003 or 2007, CAIN, Wireshark and so on.
4. After the experiment, to retain electronic documents.
Third, the experimental procedures
1. ready
Experimental preparation well in advance, should learn more about the purpose of the experiment, test requirements and test content before the experiment, familiar with the software tools and ready with a good experiment, in accordance with the requirements of experimental content and experimental content ready ahead of time.
2. lab environment
Describes the hardware and software environment used in the experiment (including a variety of software tools);
Office2003 boot and start the software or 2007, browser, Wireshark, CAIN.
Tools Download:
CAIN https://pan.baidu.com/s/19qDb7xbj1L_2QnoPm71KzA
Wireshark link: https: //pan.baidu.com/s/1BeXghjVV9Mll_cAmeMCTPg Password: mbpv
Mini FTP https://pan.baidu.com/s/16ms4hXVOmMHhDEe3WraRHQ
NetworkMiner https://pan.baidu.com/s/14e3VluLPjWFKxqNhdpYO9Q
3. experiment procedure
1) Start the system and start-up tool environment.
2) realization of experimental content using software tools.
4. experimental report
Write lab reports in accordance with the standard requirements of the test report format. The document prepared in accordance with the format template embedded test report document, the document written in accordance with the provisions of the written format, the form must be said that the graphics have a table Illustrated.
The first part of the ARP spoofing
1. a set of two students, the following experiment was conducted topology environment shown in FIG.
2. longitudinal spoofing attacks by Arp-a command to verify successful deception (screenshot attached)
3. The process of deception, the host A is turned Wireshark capture, analyze the characteristics of the data packet spoofing attacks APR process. (Screenshot attached)
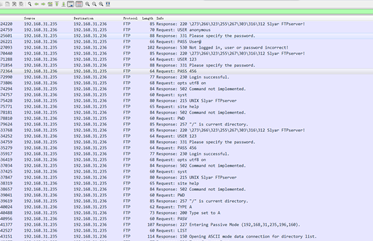
4. The process of deception, open Wireshark capture performed in the host C, analysis of the FTP protocol login procedure (flowchart attached)
5. After the completion of deception, the host C is successfully acquired user name and password FTP (screenshot attached)
ARP spoofing attacks procedure shows (for reference only)
Query the status of the victim host before being deceived
ARP spoofing machine before 192.168.31.235 normal cache table (experiment IP and this IP may not the same),

ARP spoofing 192.168.31.236 machine before normal cache table (IP experiments possible and this is not the same IP)
2, at 192.168.1.50 (IP experiments and this may be different) No. cain running machine, select the sniffer card (single card, you can default)
3, click on the card icon in the toolbar, then select sniffer page, and then select the lower left corner of the hosts, right click and choose "scan MAC address", active host IP scan LAN and MAC address
In addition to the gateway, to scan the target 192.168.31.135 and 192.168.31.136
3、选中ARP页-》点下列表栏空白处,大加号变为可选-》点大加号,在弹出的窗口中选择要嗅探的目标主机(注意这里的选择和单击欺骗嗅探不一样,左面直接点网关,其它机器自动出现在右侧列表中,这时需要按住ctrl键在右侧选择你需要嗅探的主机,如图所示)
点oK按钮,回到软件主窗体,如图所示(这是欺骗两台机器)
4、点击工具栏第三个图标(start ARP)就可以ARP欺骗了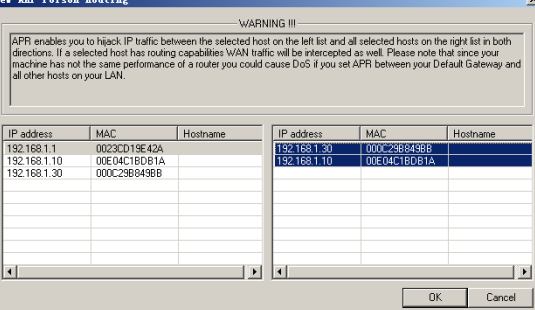
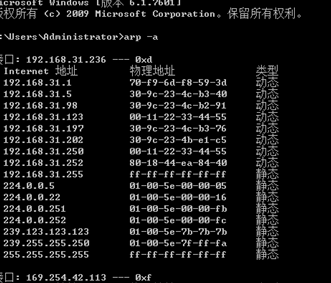
下图为欺骗开始后在192.168.31.236机器上用arp –a命令查询本机arp缓存表的情况,会发现缓存表中的网关对应的MAC地址变成了192.168.31.234号机(实施ARP欺骗的机器)的IP地址

下图为欺骗开始后在192.168.31.235机器上用arp –a命令查询本机arp缓存表的情况,会发现缓存表中的网关对应的MAC地址变成了192.168.31.234号机(实施ARP欺骗的机器)的IP地址
二部分 DNS
1. 两个同学一组,A的IP地址是192.168.31.15,B的IP地址是192.168.31.16
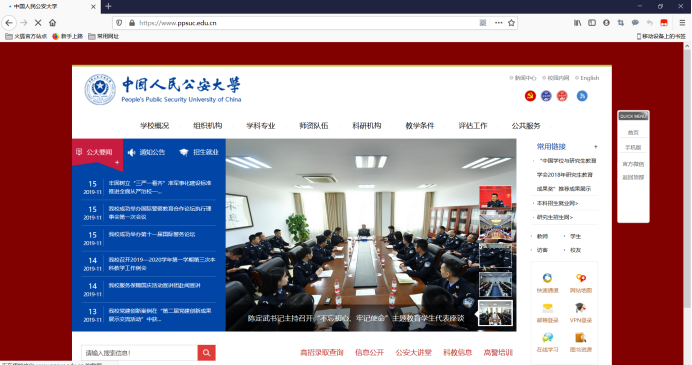
2.A同学正常访问网站www.ppsuc.edu.cn
3.B同学扮演攻击者,设计攻击方法,使用CAIN,通过DNS欺骗的方式,让A同学访问www.ppsuc.edu.cn网址的时候,访问到另外一台机器上的伪造网站
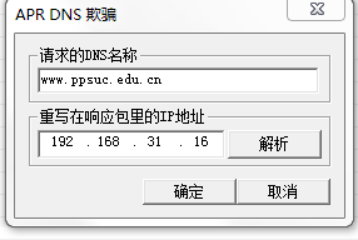
在CAIN中添加DNS欺骗选项
欺骗成功后,在被害机器上查看www.ppsuc.edu.cn的IP 查看是否被解析到了,指定的IP地址上
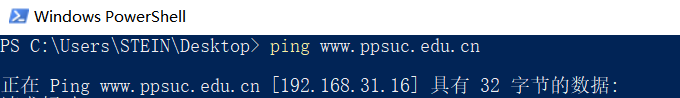
由此可知域名被成功解析到制定IP地址192.168.31.16上
第三部分 FTP协议分析
1、两个同学一组,A的IP地址为192.168.31.245,B的IP地址为192.168.31.246
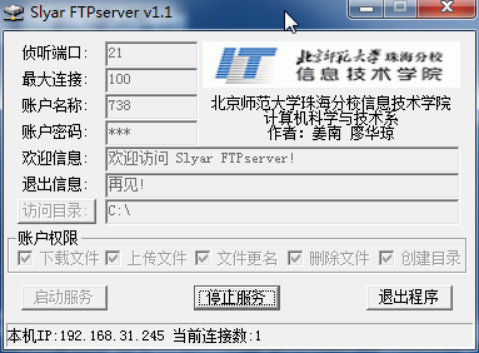
2、A架设FTP服务器,设置用户名和密码,738 / 123
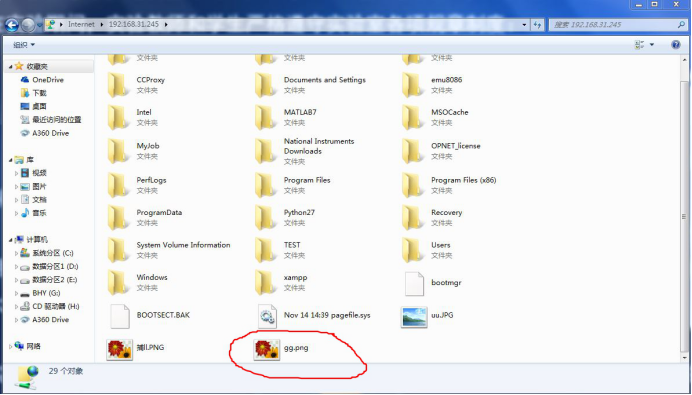
3、B打开Wireshark,之后用用户名和密码登陆A的FTP服务器,并上传一张图片gg.png
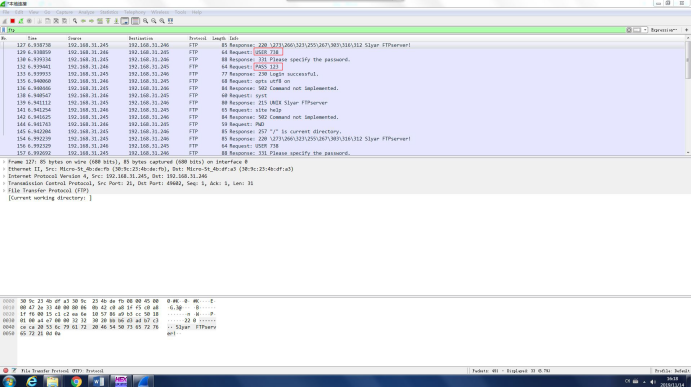
4、B停止Wireshark抓包,并和A一起分析数据包中的FTP登录过程,还原登录用户名和密码,以及上传文件
由此可知登录名为738,密码为123
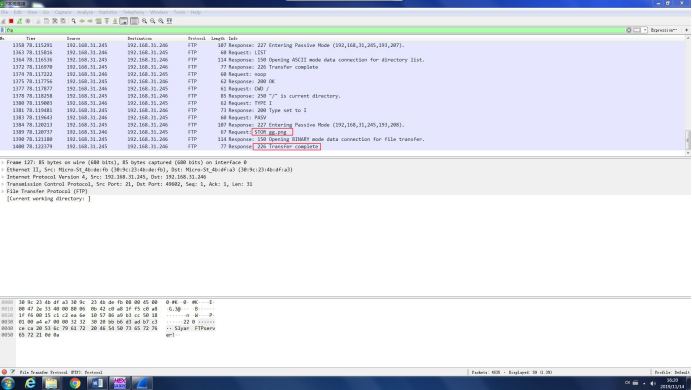
分析传输内容,发现STOR gg.png,意思是上传了文件名为gg,格式为png的文件,后有传输成功的提示。
5、右键选择追踪TCP流
6、将文件保存为temp.bin,用winhex打开,去除多余的头和尾部,将文件另存为gg.png
可知确实是当时上传的图gg.png