Recently the company using asp.net sites outside of the core measurement environment, the situation always found the lost session. Investigation for a long time, the client .AspNetCore.Session the cookie is not lost, redis main session of the distributed cache used by the copy also found no problems, but also want to use the cookie alternative solutions, but did not solve the fundamental problem, as always feel fish sticks in the throat of hell. Later in the course of the investigation, we found the same client by nginx actually sometimes loaded onto a different web server, nginx checked, is forwarded by ip_hash ah, confused the occasion, the company's operation and maintenance of the phrase broken, the original company is the use of two-wire router. So I guess whether the cookie encryption key storage because there is caused on different servers.
Microsoft's Session open source, first check SessionMiddleware middleware code, which has the following key Source:
var cookieValue = context.Request.Cookies[_options.CookieName]; var sessionKey = CookieProtection.Unprotect(_dataProtector, cookieValue, _logger); if (string.IsNullOrWhiteSpace(sessionKey) || sessionKey.Length != SessionKeyLength) { // No valid cookie, new session. var guidBytes = new byte[16]; CryptoRandom.GetBytes(guidBytes); sessionKey = new Guid(guidBytes).ToString(); cookieValue = CookieProtection.Protect(_dataProtector, sessionKey); var establisher = new SessionEstablisher(context, cookieValue, _options); tryEstablishSession = establisher.TryEstablishSession; isNewSessionKey = true; }
sessionKey is decrypted from the client's cookie out of which CookieProtection from the _dataProtector
|
1
|
_dataProtector = dataProtectionProvider.CreateProtector(nameof(SessionMiddleware));
|
The default injection IDataProtectionProvider picking out:
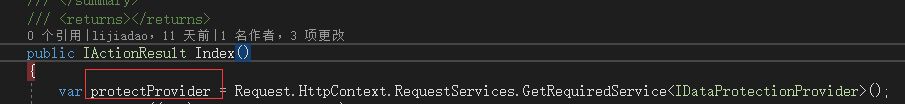
Found IDataProtectionProvider is Microsoft.AspNetCore.DataProtection.KeyManagement.KeyRingProvider, as the IDataProtectionProvider of keyManager
Microsoft.AspNetCore.DataProtection.KeyManagement.XmlKeyManager。
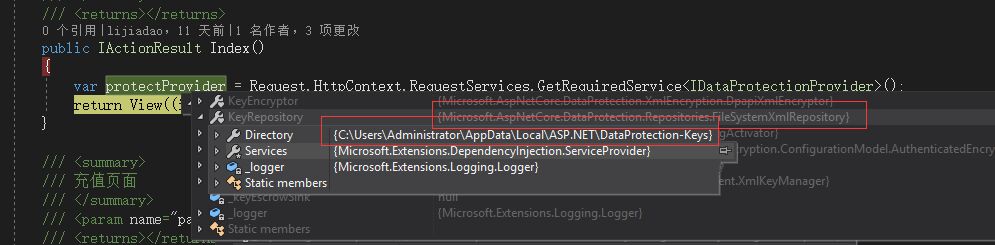
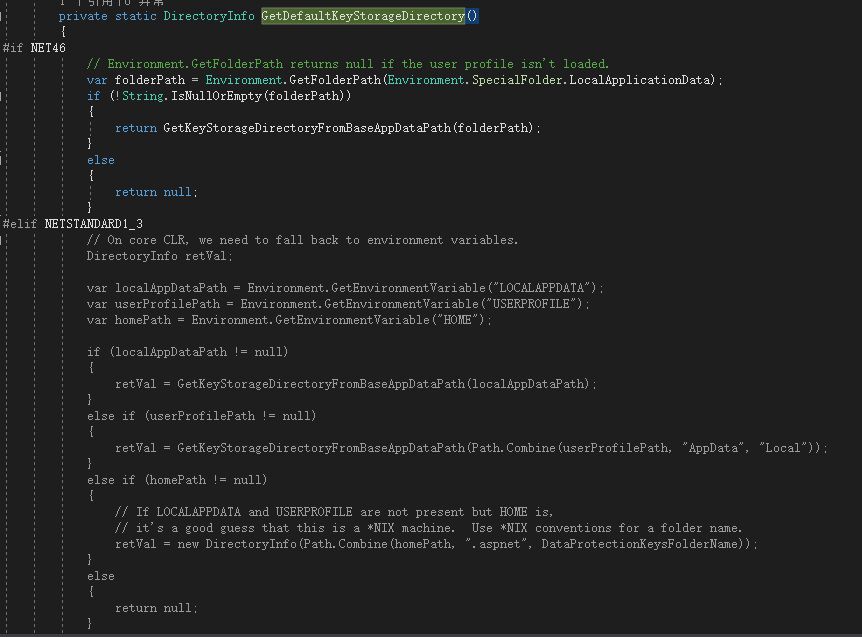
Right on cue, key exist on a single machine, Microsoft's open source DataProtection-dev in view FileSystemXmlRepository get to achieve Key storage path:
Sharp-eyed found that there is a project under the key persistence to achieve the redis:
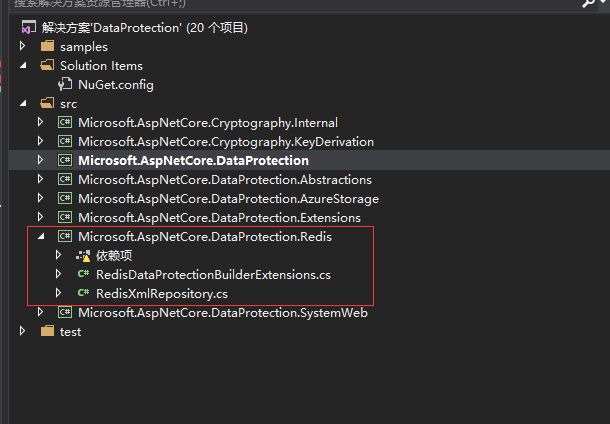
Nuget add the appropriate packet, modifying ConfigureServices method:
services.AddDataProtection()
.PersistKeysToRedis(ConnectionMultiplexer.Connect(redisConnection), dataProtectionKey);
And finally the perfect solution! When using a distributed storage session, the best will be the key dataProtectionProvider also be shared, or if you do ip_hash load balancing, client ip changed, and may load to another server, resulting in cookie store session data decryption out thereby obtaining less session!
