Author: pmiaowu
article: https: //www.yuque.com/pmiaowu/web_security_1/sq87w6
You should use a micro-blog account to a vendor account with two
condition:
1, micro-blog account: 182 ** 77 (the attacker)
2, a vendor account A: 33*[email protected] (attacker)
3, a vendor account B: 28*[email protected] (innocent victims)
Using the method:
Step 1: The attacker - Sign microblogging
Step 2: attacker - A sign in using a vendor account
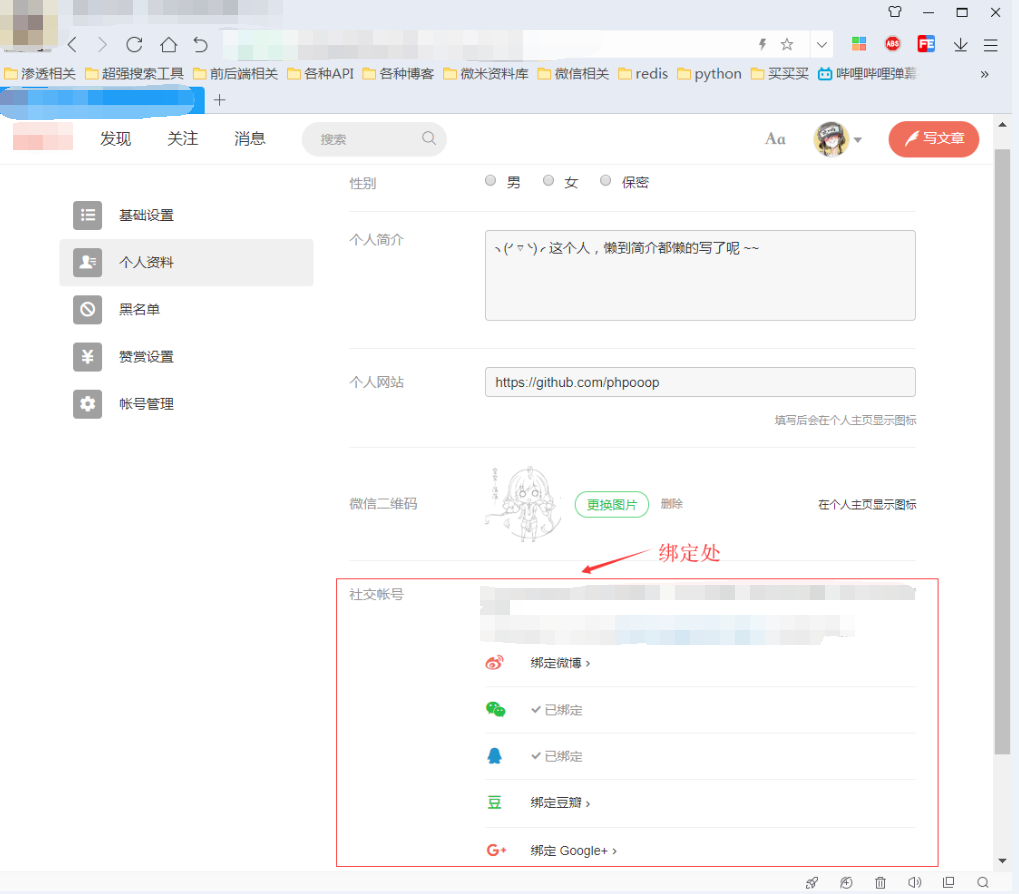
In fact, there are many ways to bind fast login account when viewed from above, but the user microblogging binding is certainly less so we use it
Step 3: The attacker - Click bind microblogging capture

Binding microblogging url: https://www.a.test.com/users/auth/weibo/callback?state={"can_transfer"%3A"true"}&code=c593bc150745c37a4d5ec05332d406af
the url of code is my micro-blog a one-time token
Step 4: innocent victims - B using a vendor account login

The url is sent to open the account B:https://www.a.test.com/users/auth/weibo/callback?state={"can_transfer"%3A"true"}&code=c593bc150745c37a4d5ec05332d406af

Then success prompted binding ~ ~ ~ hey hey hey
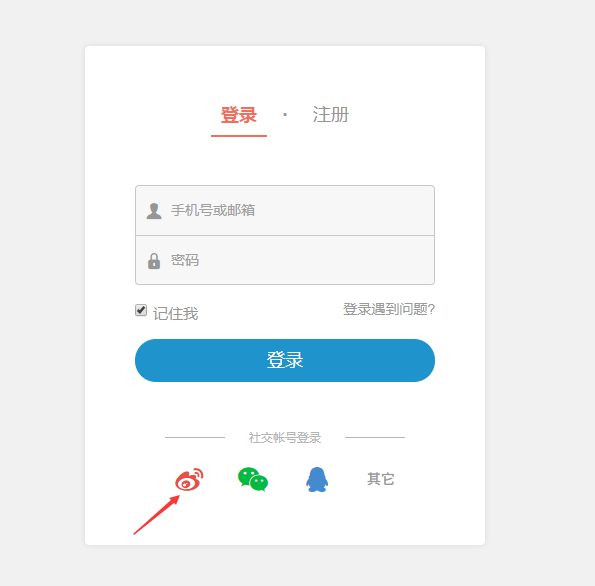
Step 5: The attacker - opening the browser, select the microblogging Login
Summary:
1, OAuth2.0 third step of requesting Client Access Token request carries user information resources to the Server Resource , without the addition of check parameters for CSRF defense
have encountered 2, prior to this, when, for example, when there are state test parameters, You can also try delete key state, it can be bypassed binding