--- --- restore content begins
The purpose of solving the problem experienced relatively rough, the title for jpg files hidden flag is a problem, leading to exchange streams of data that can not be hidden so the topic and write a title for a man, and finally the practice has had, but a man out of the question study points starting or exchange streams of data steganography based NTFS.
0x1. What is NTFS Data Interchange stream (ADS)
NTFS data streams (Alternate Data Streams, referred to as ADS) is a characteristic NTFS disk format. In the NTFS file system, each file may be a plurality of data streams, meaning that in addition to the primary file stream may also have many non-host flow in the main master file stream file, the data stream using the NTFS boarding and hidden in the system the non-primary file stream we call ADS stream file. Although we can not see ADS stream files, but they are real. By following a specific example to show create ADS stream files, and the associated hidden process. This paragraph is above Wikipedia content.
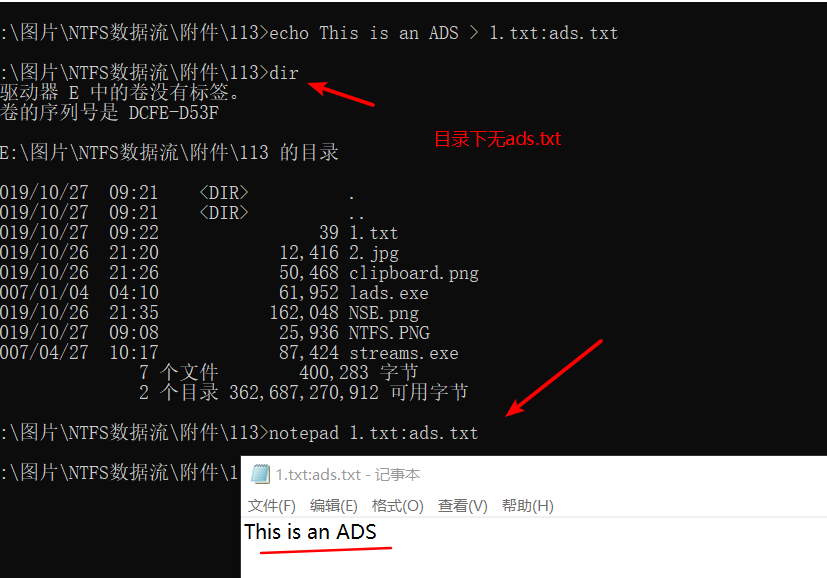
2) create a data stream file and the associated host file, enter "echo This is an ADS> 1.txt: ads.txt" in the DOS window after the carriage return. The meaning of this command is: create a file named ads.txt content "This is an ADS" data stream file 1.txt file with the host association. Check back at this time under the root directory of C, not only 1.txt ads.txt, looking through the contents remain open 1.txt "This is a test file" have not made any changes, the data stream file ads.txt where to go in the end of it? "Dir" command can not view. In this case, enter the DOS window "notepad 1.txt: ads.txt", in the pop-up notepad you can see the contents of ads.txt.
type command is a file that already exists, the exchange data streams with a parasitic manner to another folder.
/ * Parasitic on 1.jpg * / E: \ 113 > of the type 1 .txt >> 1 .jpg: 1 .txt / * parasitic to 113 folders * / E: \ 113 > of the type 1 .jpg >> 113 : 1 .jpg / * parasitic to the executable file on the a.exe * / E: \ 113 > of the type 1 .jpg >> a.exe: 1 .jpg / * parasitic to the root directory of E * / E: \ 113 > of the type 1 .jpg >> E: \: 1 .jpg
0x2. Use NTFS alternate data streams to hide executable files
winXP can be run directly parasitic executable program, later versions of Win7 need to manually create a connection file via this link file to run this parasitic executable file alternate data streams
Examples winXP
type a.exe>>1.txt:a.exe
XP中可以直接通过start命令使用绝对路径来调用这个寄生的可执行文件
start 绝对路径 1.txt:a.exe
0x3. NTFS detected data streams and clarity hidden files
1. notepad using cmd command before you can view hidden txt file, can also be used Ntfs Streams Editor software to view this https://files.cnblogs.com/files/rainbow7/ntfsstreamseditor.zip
Using this software is very easy to do CTF
2. Use the lads, the lads on the directory tool to check the address: https://files.cnblogs.com/files/rainbow7/lads.zip
lads.exe / S / * hidden stream file in the root directory is detected * /
3. Clear ADS streams.exe use this software to clear https://files.cnblogs.com/files/rainbow7/streams.zip
streams.exe -d <File>可以添加-s参数来一次性递归清除E盘下所有寄生的交换数据流文件(慎用,尤其是对系统盘一定不要随便使用递归清除,系统本身的一些数据流也会被一起清除掉)*/
E:\
. 0x4 steps do questions:
Subject to the three hex contents of the file to open in the following figure, the beginning of the three documents are the 0304, 0102, 0506, which made me immediately think of the three components of the zip archive, compressed source data file area, the compressed source file directory area. It marks the end of the compressed source file directory, but each file is missing a mark of 50 4B. Hand to add on the line.
Use 010Editor to put together three decimal file, then save it as a .zip file .
Extract the files out and have a 2.txt a 2.txt 1.jpg file contents: 1.txt behind 1.jpg 1.txt hidden behind 1.jpg, use binwalk run out is a simple tips pictures, see the hex is a
jpg file tail end no problem, then follow the prompts to find my NTFS NTFS data streams steganographic method of exchange.
Special Note: If the original file is compressed, then use software other than WinRAR to extract result in loss of data flow within the package. So be sure to use WinRar unzip the file
when I re-extracting zip file using win, then see Ntfs Streams Editor software but the results did not find what I want, then find the topic and asked for a moment before we know the topic is broken, I went to
But last title success did not change, then change to a title, for a practice easier. Below I've put into the data stream type 1.txt >> 2.jpg: 1.txt, and then as everything had happened.
Two different approaches:
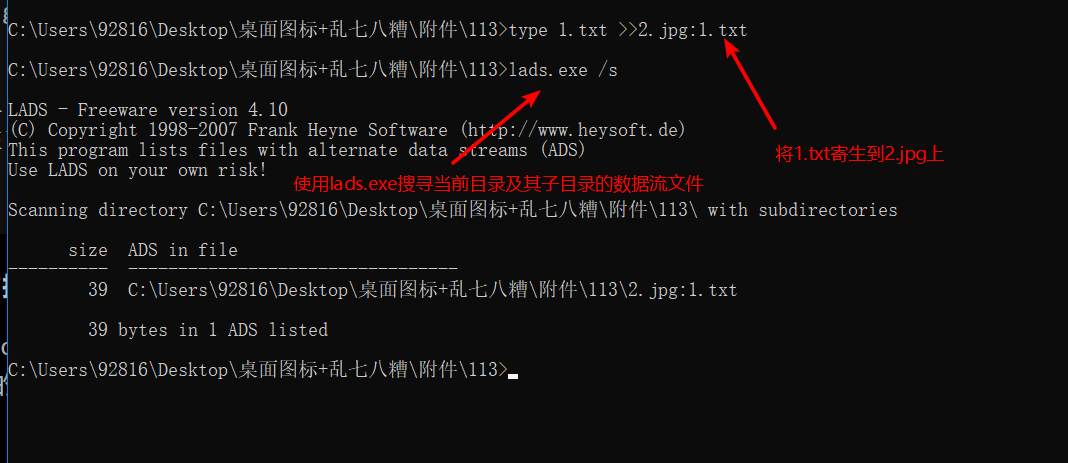
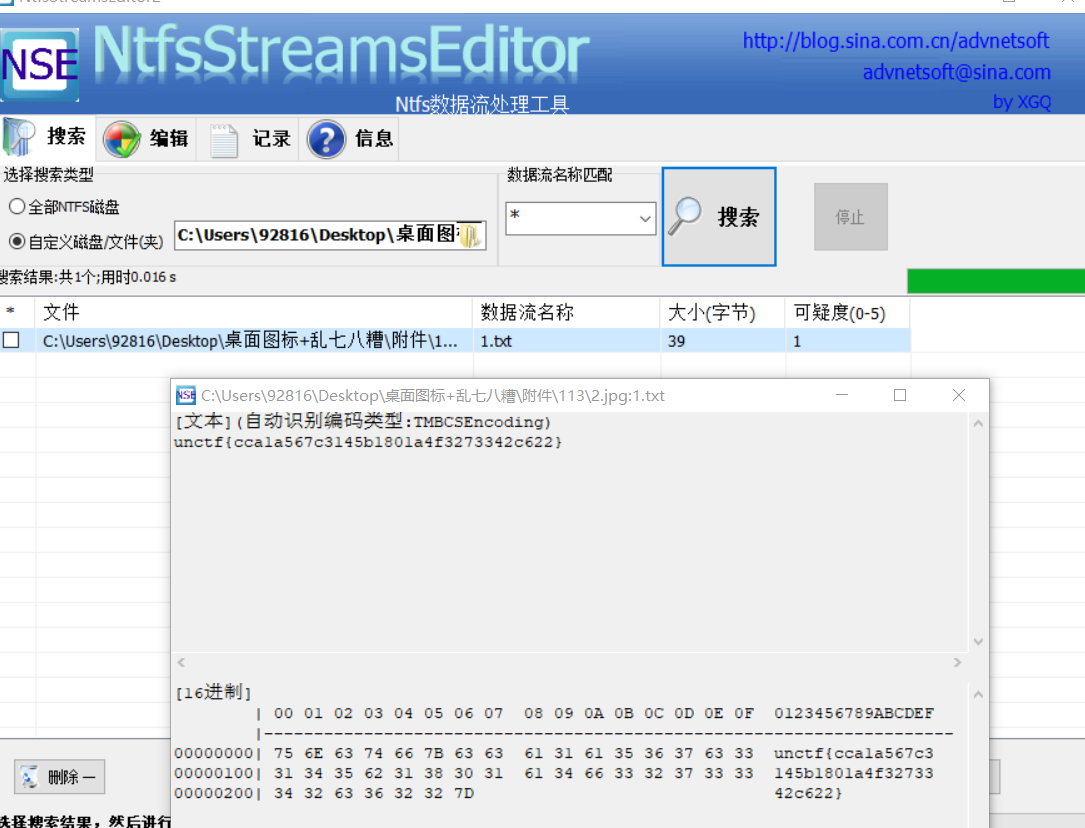
This article I wrote solving learning process, exchange of knowledge about the NTFS data streams, please go to Baidu search also learn, as there is an error content also requested treatise.
--- end --- restore content