Reprinted from learning https://blog.csdn.net/hyg0811/article/details/102366854#23_2MSL_131
[Read before thinking]
1. Draw a schematic three-way handshake and four-way handshake?
2. Why is the time of connection is three-way handshake?
3. What is the half-connection queue?
4.ISN (Initial Sequence Number) is fixed it?
The three-way handshake can carry data thing?
6. If the third handshake lost client server will be how to deal with?
What 7.SYN attack?
8. Why do we need four wave?
9. Four waving release link. 2MSL sense of waiting for?

1. The three-way handshake
Three-way handshake (Three_way Handshake) actually refers to establish a TCP connection, the client and the server needs to send a total of three packets. The main role is to carry out three-way handshake to confirm both the ability to receive and transmit capability is normal, specify your own initialization sequence number is transmitted back to prepare for reliability. Essentially connect to the server specified port TCP connection establishment, connection and synchronize both the sequence and acknowledgment numbers, exchange TCP window size information.
At first client is Closed state, the server is in Listen state.
Conduct three-way handshake:
- The first handshake: the client to the server sends a SYN packet, and indicates the client's initialization sequence number ISN (c). At this time, the client is SYN_SEND state.
The first portion of the sync bit SYN = 1, the initial sequence number seq = x, SYN = 1 segment can not carry data, but to consume a sequence number.
- The second handshake: After the server receives the client's SYN packet, will own SYN packet as a response, and also specify your own initialization sequence number ISN (s). While the client will ISN + 1 as the value of the ACK, he said he has received the client SYN, while the server is SYN_REVD state.
In the acknowledgment message segment SYN = 1, ACK1, confirmation number ack = x + 1, the initial sequence number seq = y.
- Third handshake: the client receives the SYN packet, send an ACK packet answer, of course, is the same as the server's ISN + 1 as the value of ACK, it said that it has received the server's SYN packet, then the client in ESTABLISHED state. After the server receives the ACK packet, also in ESTABLISHED state, this time, the two sides have established a connection.
Acknowledgment packet ACK = 1, an acknowledgment number ack = y + 1, number seq = x + 1 (initial seq = x, the second segment so to +1), ACK segment may carry data, do not carry data number is not consumed.
The first end of the transmission of the SYN active open (active open), receiving the next sends back a SYN SYN other end of a passive open (passive open.
In socket programming, the client performs connect (), will trigger a three-way handshake.

1.1 Why do you need three-way handshake, the two can not I?
Clarify this issue, we need to figure out what the purpose is three-way handshake, can not only to achieve the same purpose with two-way handshake.
- The first handshake: the client sends a packet network, server received.
So that the server can be concluded: the ability to send client receiving capacity of the server is normal.
- The second handshake: server contract, the client received.
So that the client will be able to conclude: reception capacity of the server, the ability to send, receive clients, the ability to send is normal. But this time the server can not confirm receipt of the client's ability is normal.
- Third handshake: the client contract, the server received.
So that the server can be concluded: the client receives, the ability to send, the server's own sending, receiving ability is also normal.
Therefore, three-way handshake to confirm both the reception and transmission capacity is normal.
Imagine if two-way handshake, the following scenario occurs:
If the client makes a connection request, but the connection request packet loss does not receive confirmation again Muyu client retransmit a connect request. Later received a confirmation, a connection is established. After the data transmission is completed, the connection is released, client connection requests were issued two segments, wherein a first lost, the second server arrived, but the first lost segment and only certain network node long stay, and delayed until some time after the connection is released before reaching the server, and the server mistakenly believe that the client has issued a new connection request, then the client as a confirmation segment agreed to establish a connection , do not use three-way handshake, as long as the server sends a confirmation to establish a new connection, and this time the client ignores the server sent a confirmation nor sending data, the server waits until the client sends data, a waste of resources.
1.2 What is a semi-connected?
After the server first received the client's SYN, will be in SYN_RCVD state where the two sides have not fully established the connection, the server will request at this state of the connection in a queue, we call this queue is called a half connection queue .
Of course there is a full connection queue is already completed three-way handshake to establish a connection will be placed in full connection queue. If the queue is full there is packet loss may occur.
Add one point here about the number of SYN-ACK retransmission problem:
After the server transmits SYN-ACK packet, if no acknowledgment packet client, the server first retransmission waiting period client not receive an acknowledgment packet, a second retransmission. If the maximum number of retransmissions of retransmissions exceeds a predetermined system, the connection information deleted from the system half-connection queue.
Note that each retransmission waiting time is not necessarily the same, the general will be exponential growth, such as the time interval of 1s, 2s, 4s, 8s ...
1.3 ISN (Initial Sequence Number) is fixed it?
When the period is to establish a connection transmits his SYN, he is connected to select one of the initial number. ISN change over time, so that each will have a different connection ISN. ISN can be seen as a 32bit counter, plus 1 each 4ms. Such aims to prevent selection number in the network has been delayed packet is transmitted to the later, resulting in a connection of one of her make the wrong interpretation.
Three-way handshake is one of the important functions of client and server exchange ISN, in order to let each other know how when data is subsequently received data in accordance with the serial number of the assembly. If the ISN is fixed, it is easy for an attacker to guess the subsequent acknowledgment number, so ISN is dynamically generated.
1.4 three-way handshake may carry data?
In fact, the third time to shake hands, it can carry data. But, first, second handshake can not carry data .
Why did this happen? Imagine, for example, the first handshake can carry data, and if someone wants to malicious server, that he always in the first handshake SYN packets into large amounts of data. Because the attacker simply ignore accept the vice weapons, the ability to send is normal, and then repeat the crazy hair SYN packet, then it makes the server takes a lot of time and memory space to receive these messages.
In other words, the first handshake can not put data in which a simple reason for this is to make the server more vulnerable to attack. And then the third, then the client is already in the ESTABLISHED state. For clients runoff, he has established a connection, and have been known to receive server, normal transmission capacity, we are able to carry data also nothing wrong.
1.5 SYN attack what?
Resource allocation server is allocated in the second handshake, and the client's resource allocation when it completed three-way handshake, the server commit vulnerable to SYN flood attack. SYN attack is forging a large number of client IP address does not exist in a short time, and continue to send SYN packet server, sever back to confirm the package and wait for client confirmation, since the source address does not exist, therefore sever the need to constantly re-issued until the timeout SYN, SYN packet to the forged connection queue is not occupied for a long time, leading to the normal request queue is full are discarded due to network congestion or even cause system failure . SYn attack is a typical Dos / DDos attacks.
SYN attack detection is very convenient, when you see a large number of semi-connected state on the server, in particular, the source address is random, basically concluded that this is a SYN attack. The system may be used on the command comes netstats linux / unix SYN attack detected.
netstat -n -p TCP | grep SYN_RECV
Common defense SYN attack methods as follows:
Shorten time-out (SYN Timeout) time
Increase the maximum number of connections and a half
Filtering gateway protection
SYN cookies technology
2. Four waving
Establish a connection requires three-way handshake, and terminate a connection to go through four wave. This is indicated by the TCP half-close result (half-close) a. The so-called half-closed, in fact, provides a TCP connection, while still receiving end from the other end of the data at the end of his sent.
Removal of TCP connections required transmit four packets, so called four wave into (Four-way handshake), the client or the server may initiate waving operation.
At first both in ESTABLISHED state, if the client to initiate a shutdown request. Four waving process is as follows:
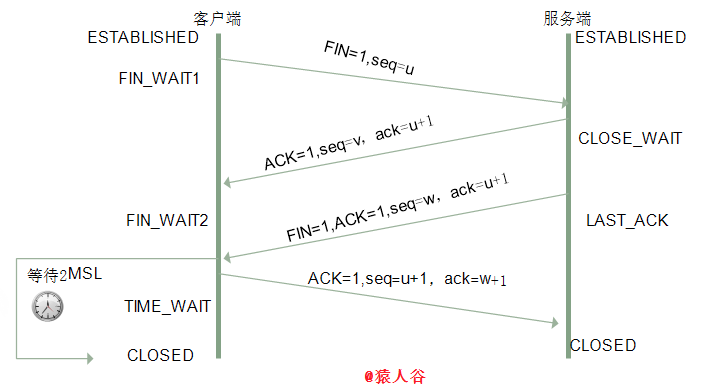
- The first wave: the client sends a FIN packet, the packet will assign a serial number. At this time, the client is FIN_WAIT1 state.
Is issued connection release segment (FIN = 1, number seq = u), and then stops sending data, the initiative to close the TCP connection into FIN_WAIT1 acknowledgment (1 termination wait) state, waiting for the server.
- Second handshake: After the server receives the FIN, ACK message is sent, and the sequence number value of +1 as the client sequence number of the ACK packet indicating that the packet has been received in the client, while the server is CLOSE_WAIT status.
I.e., the server receives a connection release message sent after the segment acknowledgment segment (ACK = 1, an acknowledgment number ack = u + 1, number seq = v), the server enters the CLOSE_WAIT (closed waiting), this time in a semi-TCP connection status, client-to-server connection release. When the client receives the acknowledgment server, enters the FIN_WAIT2 (2 termination waiting) state, waiting for the connection release message sent by the server segment.
- Third wave: If you would like to disconnect from the server, and the client as the first wave, send FIN messages, and specify a serial number. At this time, the server is LAST_ACK state.
I.e. no data server order sent by the client, the server sent a connection release segment (FIn = 1, ACK = 1 , number seq = w, confirmation number ack = u + 1), the server enters LAST_ACK (final confirmation )status. Waiting for confirmation of the client.
- The fourth wave: The client receives the FIN, the same as the response sends an ACK, the server and the sequence number value of +1 as its sequence number of the ACK packet, then the client is in the TIME_WAIT state. You need a while after the service to ensure that the client receives their own ACK packet will enter CLOSED state, the server receives an ACK packet, then the connection is closed, in CLOSED state.
That is, after the client receives the server connection release segment, this issue acknowledgment segment (ACK = 1, seq = u + 1, ack = w + 1), the client enters the TIME_WAIT (wait) state. At this time, TCP is not relieved, the elapsed time required latency timer set after 2MSL, client before entering the CLOSED state.
Receive a FIN only means that no data is flowing in this direction. The client does the active close and enters TIME_WAIT1 is normal, the server typically performs passive close, will not enter TIME_WAIT state.
In socket programming, any execution close () operation to produce hand-waving operation.
2.1 waving Why four?
Because when the server receives the client's connection request SYN packet, it can be sent directly SYN + ACK packet. Wherein the ACK message is used for response, SYN etc is used to synchronize the packet . But the connection is closed, when the server receives FIN packet, it might not turn off immediately socket, we can only respond to a first ACK packet, telling the client, "you send FIN messages I received, only I wait until all messages are sent over the server, I can send FIN messages "and therefore can not be sent together. It requires four wave.
2.2 2MSL wait state
TIME_WAIT state is also known as the 2MSL wait state. Each TCP implementation must choose a specific segment maximum survival time (Maximum Segment Lifttime), he is no segment is discarded before the maximum time within the network. This time is limited, because TCp segment of the IP packet transfer within the network, and the IP datagram has the TTL field of survival time limit.
Reduction of a specific implementation MSL given value, the processing principle is: when performing a TCP active close, and sends back the ACK last, the connection must stay in the TIME_WAIT state time is twice MSL. This allows TCP to send the final ACK ACK prevent this loss (the other end of the timeout and retransmit the final FIN) again.
Another result of this is that this wait 2MSL TCP connection during 2MSL waiting define the connection socket (client's IP address and port number, the server's IP address and port number) can not be reused. This connection can only be used again after the end of 2MSL.
Four waved 2.3 release, wait 2MSL meaning of?
MSL (Maximum Segment Lifetime), meaning "the longest segment life," he was any messages present on the network the longest time, over this time the message will be discarded.
In order to ensure the last ACK segment sent by the client to reach the server. Because this ACK may be lost, resulting in LAST_ACK state FIN_ACK server can not receive messages. Server timeout retransmission this FIN_ACK, then the client retransmit once confirmed, restart waiting time timer. Finally, the client and the server can be normal shutdown. Assume that the client does not wait 2MSL, but after sending ACK released immediately shut down, once the ACK is lost, the server can not be properly connected into the closed state.
For two reasons:
1. To ensure that most of the client sends an ACK segment can reach the server.
The ACK segment may be lost, the other end is in a state of LAST_ACK not receive SIN_ACK segment confirmation has been sent, the server timeout retransmission FIN_ACK segment, and the client can receive the weight in time 2MSL FIN_ACK segment pass, and then confirm that the client retransmission time, restart the timer 2MSL Finally, the client and server into the CLOSED state, if the client does not wait for a period of time in a state TIE_WAIT, but sending the ACK packet segment immediately after the release of the connection, you can not receive FIN_ACK segment retransmission server, it will not send a confirmation message segment, the server can not enter CLOSED state is normal.
2. To prevent the "expired connection request segment" appear in this connection.
The client after sending the last ACK segment, then after 2MSL, it can be all segments in this connection duration generated disappeared from the network, the next new connection does not appear in this the old kind of connection request segment.
2.4 Why TIME_WAIT state to go through 2MSL CLOSE to return to the state?
In theory, four packets have been sent, you can go directly CLOSE state, but the network is unreliable, it is possible to lose the last ACK. So TIME_WAIT state is used to retransmit ACK packets may be lost .
3. Summary
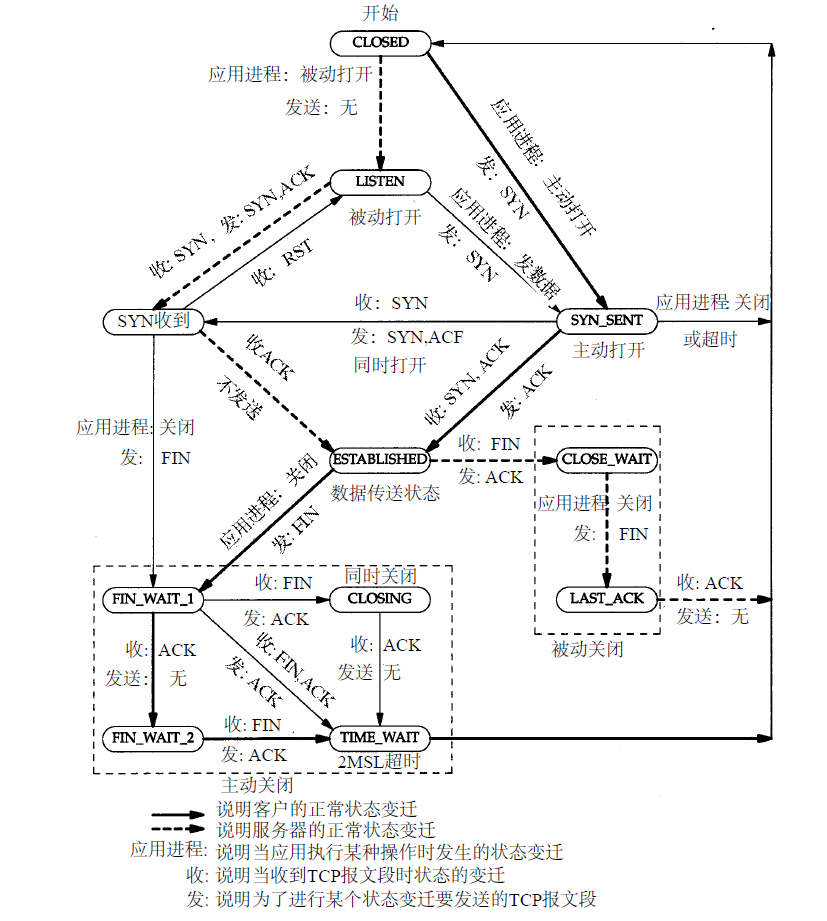
"TCP / IP Detailed Volume 1: The agreement" with a TCP state transition diagram, is typical, three-way handshake and help you understand the status change of wave four. As shown below, the thick solid line arrows indicate the normal client state changes, the thick dashed arrows indicate the normal server transitions.