1. Virus found
Recently, because of his personal website set up to do a version update, ready to do the deployment server. Connect to the server when obviously feel time consuming than ever to be a long, long time before the response came.
After the test network is no problem, then the top command look process, the results are shown in FIG.
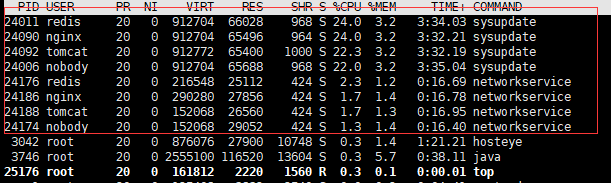
Uniform process, and it did not done such a deployment. Found wrong, then immediately use the kill command to kill these processes. Magical things happen, like a tumbler of these processes, like, kill a few commands in the past they once again stood up.
2. solve the problem
The problem was immediately reflected to Baidu, we conclude that it is a virus mining sysupdate
2.1 Positioning virus
1. Use the top command to obtain the process ID (PID)
2. Use command ls -l proc / {process ID} / exe derived file location
2.2 Clear virus
1. Use the rm command to directly remove, will find tips not be removed, should be used to lock the file chattr command
Use the command: chattr -i {filename} to delete normal
2. In the / etc / directory also found a daemon also be deleted the file /etc/update.sh
3. Check the file back door as well as free dense logged /root/.ssh/authorized_keys also be deleted
4. Check the crontab -l cron job to clear the suspicious task
Finally, the server is restarted, check if there are abnormal
3. Summary
The event may be due to the virus mining redis service is not password caused due redis has not officially put into business, so had this oversight.
This is probably the details determine success or failure.
Security is no small matter, I hope we can avoid such problems can occur well resolved.