First, multiple choice (a total of 30 questions, each question 5 minutes)
1. The following statement about PHP garbage collection, the error is?
A, on / off garbage collection may be achieved by modifying the configuration php
B, opening and closing can gc_enable () and gc_disable () in the program.
C, PHP in the garbage collection mechanism, will greatly improve system performance.
D, after opening the garbage collection mechanism, for the case of a memory leak, you can save a lot of memory space, but due to the garbage collection algorithm run time-consuming, open garbage collection algorithm increases the execution time of the script.
Reference answer: C
Answer Analysis: garbage collection mechanism in PHP, will only increase in time consumed in recycling algorithm is indeed running. But in normal (smaller) the script should simply not affect performance.
(Join the group 677 079 770 for more answers to interview questions.)
2. The tree structure is divided?
A, and binary tree complete binary tree
B, full binary tree and binary tree
C, ordered and unordered tree tree
D, btree and search tree
Reference answer: C
Answer Analysis: order and disorder tree tree.
3. Data entry and data elements of the relationship is wrong to say?
A, the data element is a basic unit of data
B, a data item may be a plurality of data elements
C, the data item is indivisible minimum unit of data
D, the data object is a collection of data elements of the same nature
Answers: B
Answer Analysis:
Element: is the basic unit of data, is typically considered as a whole and in the processing program. A data element may be composed of a number of data items. Data entry is indivisible smallest unit of data. Item is the description of the characteristics of a particular aspect of objective things. Data objects: is a collection of data elements of the same nature, is a subset of the data. The character set C = { 'A', 'B', 'C, ...}
4. In HTTP 1.1, the meaning of the status code 404 is (), if the return "file not found" message, the function header is available, which is the statement ()
A, refusal to implement, header ( "Location: http://www.sijiaomao.com/404.php");
B、未授权,Header("HTTP/1.1 404 Not Found");
C, refuse to perform, Header ( "HTTP / 1.1 404 Not Found");
D, unauthorized, header ( "Location: http://www.sijiaomao.com/404.php");
Answers: B
Answer Analysis: refusal to implement the status code is 403, header ( "Location: XXXX") The default is to do 302 jumps state, so the answer is B.
5. The establishment of a composite index a_b_c in mysql with a, b, c three fields, may I ask which of the following query efficiency worst?
A、select * from test where a=10 and b>50
B、select * from test where a=10 and b>10 order by c
C、select * from test where a=10 and b=10 order by a
D、select * from test where a=10 and b = 10 order by c
Answers: B
Answer Analysis: leftmost matching principle: the composite index contains a, a_b, a_b_c. When the composite index only in the front of the field for the precise inquiry, will spend a composite index behind, in the event inaccurate query will not use the composite index. A options, use a_b index. B options, use the a_b index, and there is order by c it is the worst efficiency. C option, using a_b index. D options, use a_b_c index.
6. sql statement to return a result from the execution takes the longest time to the middle part of which step
A, from the network layer to mysql php
B, mysql statement parsing, optimization, execution plan
C, execution
D, returns the result
Reference answer: D
Answer Analysis: the greater the amount of data query results returned longer, far more than other aspects of the elapsed time.
(Join the group 677 079 770 for more answers to interview questions.)
7. With regard to the principles of design patterns to follow, to say wrong is that?
A, a combination of superior inheritance
B, for the realization of programming
C, open for extension, closed for modification
D, reducing the coupling between objects
Answers: B . Answer Analysis: Design mode (object-oriented) has seven principles, namely: 1. Open - Closed Principle 2. Principle 3. The functions of the single Dependency Inversion Principle 4. Demeter (also referred to as the principle of minimum knowledge) 5. Interface 6. synthesis segregation principle / polymerization multiplexing principles 7. Richter substitution principle
8. A site used lvs + keepalived do clustering, load balancing algorithm is RR, but the site back when landing, has been prompted to log overtime, can not be used, how can we solve this problem?
A, the site will not load balance requests background
B, modify the load balancing algorithm wlc
C, LVS parameter set, the parameter is added persistence_timeout
D, load balancing algorithm to modify ip hash </ p> <p> <br/>
Reference answer: C
Answer Analysis: Slightly
9.CSRF attack description is wrong?
A, CSRF need to have JavaScript code
B, CSRF attacks malicious code located on third-party sites
C, filtering user input to prevent malicious code injection to a site, but it has no law to prevent malicious code from running on third-party sites
D, CSRF meet the same origin policy
Answers: A
Answer Analysis: XSS attacks require JavaScript code, CSRF attack does not require JavaScript code.
10. With regard to PHP mode modifier statement is wrong?
A, i case-insensitive match
B, m ^ beginning of the string will only match
C, x blank and # comments will be ignored
D, and the replacement string as php execution code evaluator
Answers: B
Answer Analysis: m is an enhanced line anchor mode, the front and rear \\ n will be considered as the beginning and end
11 6.3 push successively different elements, there are () different Stack Sequence
A、A、4
B、B、5
C、C、6
D、D、7
Answers: B
Answer Analysis: for n different elements into the stack, the stack number of the sequence is 6 \ 5 * \ * 4/4 \ 3 * \ * 2 \ 1 * 5, i.e. the number of Cattleya
(Join the group 677 079 770 for more answers to interview questions.)
12. A plurality of threads operating simultaneously a data, in order to ensure the accuracy of the data, the operation portion can be changed to the data ()
A, write-only
B, read-only
C, asynchronous
D, synchronization
Reference answer: D
Answer Analysis: read-only data, then it is also how to operate.
How 13.HTTP agreement work?
A, resolve the domain name -> dns get through IP-> establishing a TCP connection -> get request to the server -> return information
B, dns get through IP-> establishing a TCP connection -> get request to the server -> return information
C, resolve the domain name -> dns get through IP-> get request to the server -> establishing a TCP connection -> return information
D, resolve the domain name -> get request to the server -> dns get through IP-> establishing a TCP connection -> return information
Answers: A
Answer Analysis: resolving a domain name -> dns get by IP-> establish a TCP connection -> get the request to the server -> return information.
14. The following statement about the HTTP method, the error is?
A, a server to be compatible with HTTP1.1, as long as the realization of GET and HEAD methods to resource
B, PUT let the server with the main part of the request to create a new document named by the URL requested, or if the URL already exists, you replace it with a dry this subject
C, POST is used to input data to the first server. In fact, often we use it to support HTML form. Data is typically completed form is sent to the server, and the server sends it to the place to go.
D, TRACE method of requesting the web server to inform its various functions supported. What method can query the server support or resources which methods for some special support.
Reference answer: D
Answer Analysis:
HTTP method
a server to be compatible with HTTP1.1, as long as the GET and HEAD methods to achieve resource can
GET is the most commonly used method, commonly used to send a request to the server resources.
HEAD and GET similar, but the server in response to the value returned headers, does not return the main part of the entity
PUT allow servers to the main part of the request to create a new document named by the URL requested, or if the URL already exists, this body to replace it with a dry
POST is used to input data to the first server. In fact, often we use it to support HTML form. Data is typically completed form is sent to the server, and the server sends it to the place to go.
TRACE initiates a loopback diagnostic purposes in the server, the server the last station and will snap back a response and carries TRACE original request packet it receives in the response body. TRACE method is mainly used for diagnosis, for verifying whether a request to do so through a request / response chain.
OPTIONS method request to the web server to inform its various functions supported. What method can query the server support or resources which methods for some special support.
DELETE requests the server to delete the specified resource request URL
15. The following JavaScript code is run results ()
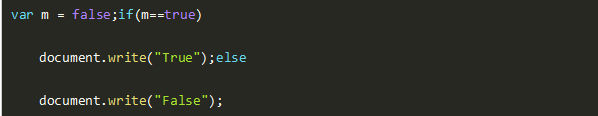
A、true
B、False
C、false
D、True
Answers: B
Answer Analysis: slightly.
16. With regard to the request header header argument is wrong
A, Upgrade: HTTP / 2.0 protocol version switch
B, Rang bytes = 0-2000 request a piece of content, such as 0 to 2000 bytes available for download breakpoints
C, Vary using the cached version, generally used for proxy server
D, X-Requested-With asynchronous request
Reference answer: D
Answer Analysis: Vary use the cached version, typically a proxy server Rang bytes = 0-2000 request section of memory, such as 0 to 2000 bytes, breakpoints can be used to download the source address Referer Upgrade: HTTP / 2.0 protocol version switching X-Requested -With ajax request.
17. The correct size of the array is about PHP
A, hash Bucket size, a minimum of 8 to 2x growth.
B, initial array does not allocate space to the element
C, who changes the elements of the array are subject to change
D, after the expansion table need not do anything
Answers: A
Answer Analysis: HashTable size is not fixed, when nNumOfElements> nTableSize time, will HashTable for expansion in order to accommodate more elements. (It may add a value, but an array capacity expansion for many reasons: to increase 2x)
18. In MySQL, can be used to create a new database of SQL statement ()
A、CREATE DATABASE
B、CREATE TABLE
C、CREATE DATABASES
D、CREATE DB
Answers: A
Answer Analysis:
A correct option, create a library statement: CREATE DATABASE database name.
B option CREATE TABLE, is to create a table of the statement.
C and D option syntax error.
(Join the group 677 079 770 for more answers to interview questions.)
19. A data structure for use in a large number of external sort is ()
A、hashtable
B、B+Tree
C、RB-tree
D、skip list
Answers: B
Answer Analysis: external sort refers sorting large files, i.e. on the recording stored in the external memory to be sorted, a file to be sorted can not fit in memory, require multiple exchange of data between the memory and the external memory, to achieve the sort the purpose of the entire file. The most common external sorting algorithm is a multi-way merge sort, is about to be broken down into the original file can be loaded disposable portion of the plurality of human memory, respectively, to complete each section into memory sort. Then, the sub-file were already sorted merge sort. Large-scale data storage, the realization index query such a practical context, the number of elements in a tree node storage is limited (if the number of elements in a lot of words, find degenerates into a linear internal nodes searched), which results in a binary search tree As the depth of the tree structure caused by excessive disk I / O read and write too often, leading to poor query efficiency, how to reduce the depth of the tree (of course, can not reduce the amount of data queries), a basic idea is this: a multi-fork tree (tree nodes due to the number of elements is finite, the number of natural sub-tree of the node is limited). So we propose a new search tree structure - multiple search tree. According to inspire balanced binary tree, naturally, think of balancing multiple search tree structure, which is B ~ tree (B tree).
20. The following about PHP string argument is wrong?
A, PHP binary string of safety
B, PHP string up to 2G
C, PHP strings can be serialized
D, PHP string can use \ 0 to end
Reference answer: D
Answer Analysis: Because binary safe PHP string is different with the C language so I do not recognize \ 0
21. The following data structures, can dichotomy is to find ().
A, stored sequentially ordered linear form
B, linear list
C, binary list
D, ordered linear list
Answers: A
Answer Analysis: No
22.is_numberic () function is the meaning?
A, the value is not determined incoming values
B, and converted to an integer value passed
C, to convert the incoming numerical value
D, is not judged incoming values decimal
Answers: A
Answer Analysis: is \ _numeric - whether a variable is a number or a numeric string
23. Which is not the main entrance script work yii?
A, define the global constants
B, comprising [[Yii]] class files
C, load the application configuration
D, loading filter
Reference answer: D
Answer Analysis: Main entrance document as follows: defining global constants; registration Composer autoloader; includes
\ [Yii
\ [Yii
\] types of documents; loading the application configuration; creates an application instance and configure; call
\ [yiibaseApplication :: run ( )
\ [yiibaseApplication :: RUN ()
\] to process the request.
24. The following code will call display_result ()?

A, error
B, correct
C, compiler errors
D, no answer
Reference answer: C
Answer Analysis: $ x = "display"; $ x '\ _ result' '()'; function display \ _result () {echo 'ok';} this way it is not being given.
25.PHP of three modules which are not included?
A, the kernel
B, zend engine
C, spreading layer
D, parsing layer
Reference answer: D
Answer Analysis: PHP total of three modules: the kernel, zend engine, as well as the expansion layer
26. The following statement regarding opcode is wrong?
A, opcode extension module is Php
B, with a buffer cache can xcache apc or the opcode php
C, opcode is intermediate language compiled after the php scripting language.
D, after the opcode cache can speed up the running speed of the site
Answers: A
Answer Analysis: opcode is intermediate code after the Php script compiler.
(Join the group 677 079 770 for more answers to interview questions.)
27. With regard to the operating mechanism php error is:
A, php a total of three modules: the kernel, the Zend engine, spreading layer
B, PHP and Apache connected through SAPI
C, Zend engine can convert a source file into a binary file to run
D, operation mysql function not included in the kernel php
Reference answer: C
Answer Analysis: Zend engine converts the source file into opcode code, and then run on a virtual machine
28. Hackers use buffer overflow vulnerability to attack, for this threat, the most reliable solution is ()
A, install a firewall
B, installation, user authentication system
C, install system patches
D, install anti-virus software
Reference answer: C
Answer Analysis:
C: install the system patch
29. As the business grows, traffic information systems and data traffic increases rapidly, using load balancing (Load Balance) method to avoid system performance resulting decline or even collapse. The following account of load balancing, the error is ().
A, load balancing is typically implemented by a server-side installation of additional software
B, and load balancing to increase throughput of the system does not
C, load balancing may be performed at different location, different network structures of the server cluster
D, load balancing enabling users will be able to access the appropriate server via an IP address or domain name
Answers: B
Answer Analysis: Knowledge load balancing assessment
30.SMJ binary byte order is correct?
A、0101 0011 0100 1010 0100 1101
B、0011 0101 0100 1101 0100 1010
C、0101 0011 0100 0100 1010 1101
D、0011 0100 0100 1010 0011 1101
Answers: A. Answer Analysis: SMJ convert binary to 010100110100101001001101
Share content limit from time to time :( join the group 677 079 770 for more answers to interview questions and learning materials.)
★ Tencent Senior PHP Engineer written questions
★ one hundred million PV high concurrency scenarios order handling
★ laravel development Lynx mall Component Services
★ banners TV video broadcast infrastructure project combat

