IE browser remote code execution risk vulnerabilities (CVE-2019-1367) problems encountered reinforcement
I. Background
Internet Explorer, Microsoft is the launch of a web browser. A great amount of users. September 23, Microsoft released an emergency security updates, fixes IE browser affect a remote code execution vulnerability. Threat analysis team found the vulnerability by Google, the opposition alleged that the vulnerability Yizao use.
Second, Vulnerability Description
This vulnerability is caused by InternetExplorer script engine handles memory objects in the way of memory corruption. To exploit this vulnerability, an attacker would have to guide the user to open a malicious Web site has hosted vulnerability. Exploit this vulnerability can cause an attacker to gain privileges of the current user, and execute arbitrary code. If the current user has administrative privileges an attacker can perform various operations on the system, or even modify data from creating new accounts that have full privileges to install the program.
Third, the impact version
10 Windows, Windows 8.1, Windows 7, Windows Server 2012 / R2, Windows Server 2008, Windows Server 2016, Windows Server 2019 version of IE11, IE10 version of Windows Server 2012 and Windows Server IE9 version 2008.
Specifically affected versions and the corresponding patch please view Microsoft's official https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1367
Fourth, the suggested fix
1, install the patch
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1367
2, mitigation measures
For 32-bit system, the administrator inputs a command prompt command as follows
takeown / F% windir% \ system32 \ jscript.dll
cacls% windir% \ system32 \ jscript.dll / E / P the Everyone: N
for 64-bit systems, administrator command prompt, type the following command:
takeown /f%windir%\syswow64\jscript.dll
cacls% windir% \ SysWOW64 \ jscript.dll / E / P the Everyone: N
Fifth, the repair method - installing patches
1. Determine the IE browser version
In IE "Tools" - "on the Internet Explore (A)", the corresponding pop-up window, as shown below, is the red circle marked IE browser version.

2, view the operating system version number
By "Win" + "R" key to open the operating field, enter "cmd" carriage return, the pop-up window, enter "winver" carriage return, the pop-up window operating system version information, as shown below, the operating system is the red circle marked version.

3, select the appropriate patch file in the patch download page
Depending on the operating system version, IE browser, select the appropriate version of the patch file, click on the right "Security Update". 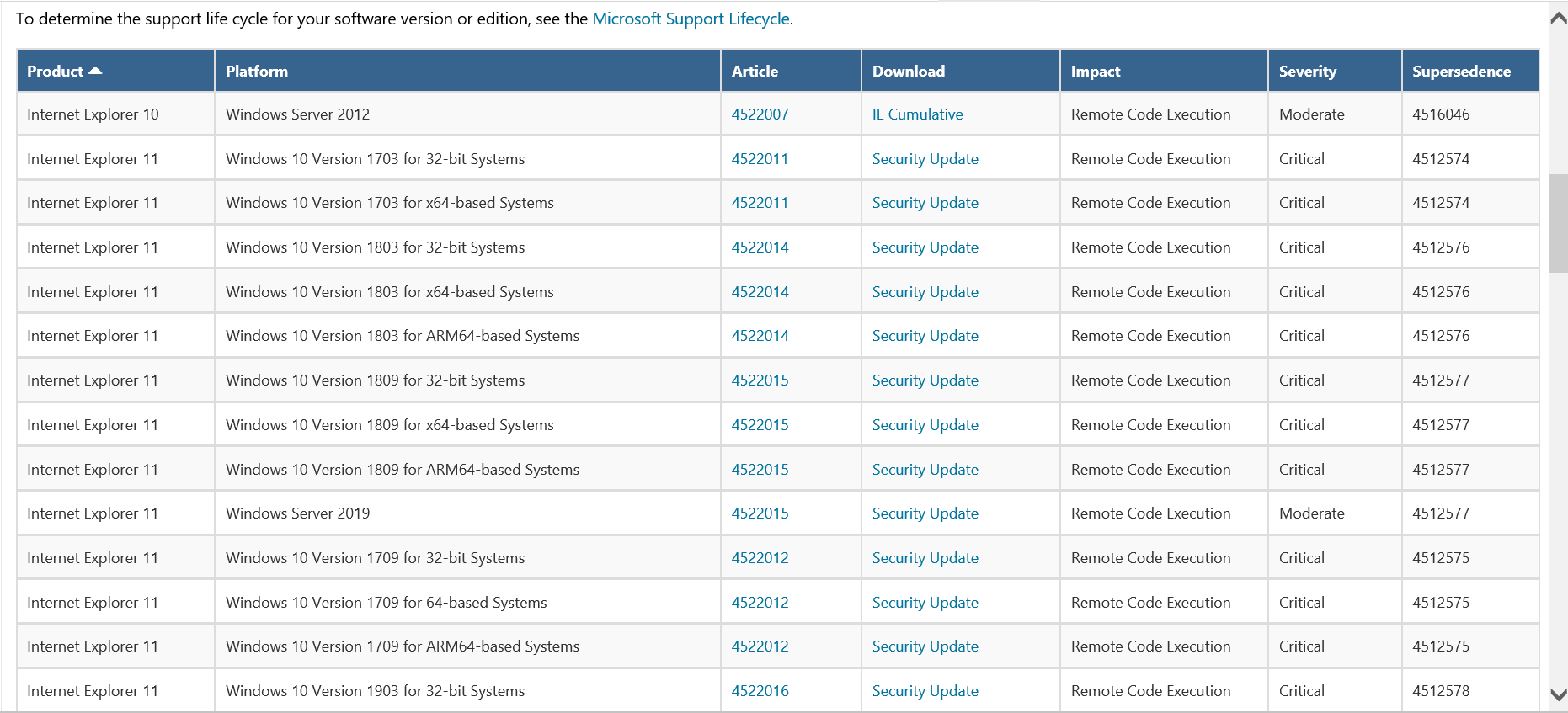
4, downloaded the patch, the patch is installed, restart the system after completing installation
5, see the browser patch version (updated version) to ensure the successful installation of the patch
Sixth, the problems occur when you install the patch
1, win7 64 sp1 patch installation prompts "Setup Error" error code 0x80240037

Solution:
Reference https://www.cnblogs.com/UUUz/articles/9305652.html
2, modify download the patch suffix, unpack, run the following command
dism /online /add-package /packagepath:"C:\Users\Administrator\Desktop\cab\IE11-Windows6.1-KB4522007-x64.cab" 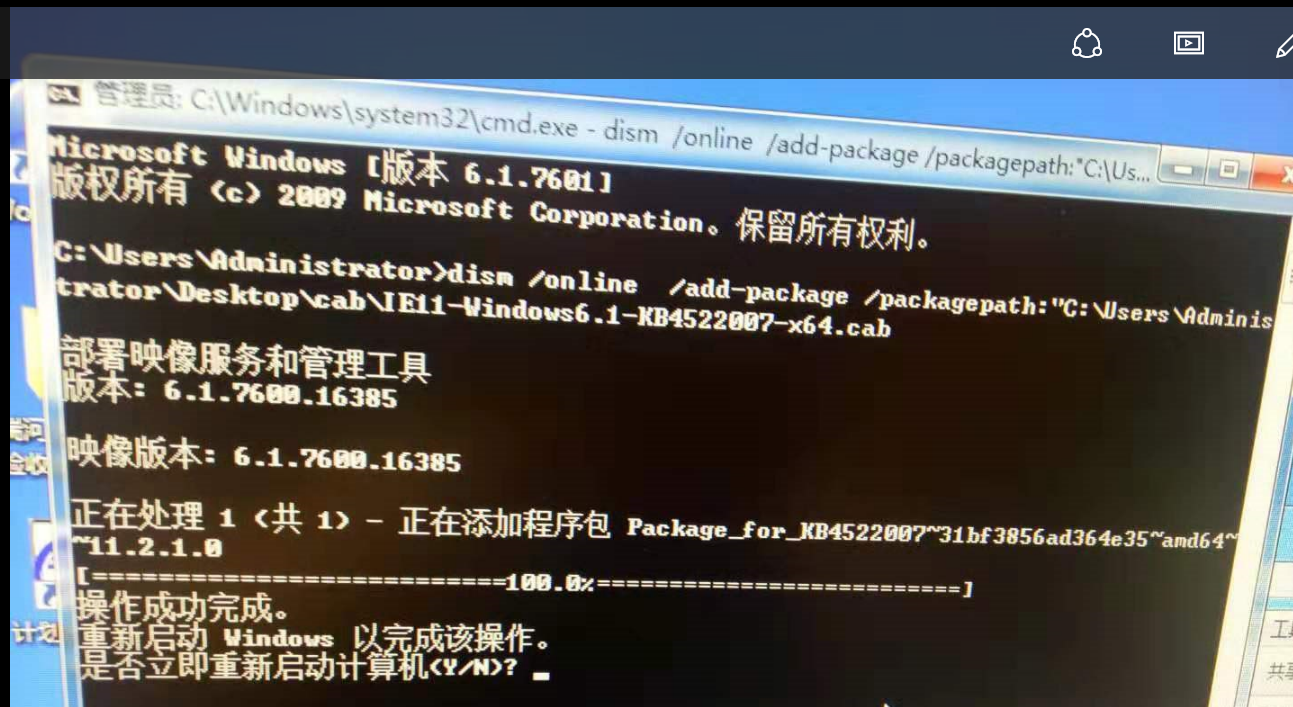
3、windows server 2008 R2 SP1安装时提示"无法建立到信任根颁发机构的证书链",错误码0x800b010a
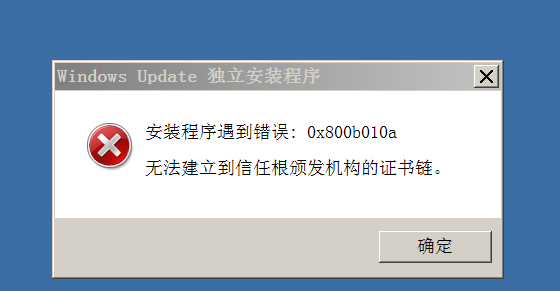
4、根据网上的资料添加证书,但是不知道添加什么证书,哪位大神知道,还望指点一下小弟~~ 
-----------------------------------------------------------------------------------------
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1367