One. Dual use file upload
Double meaning by uploading files to upload two or more files to breakthrough
Use:
File upload vulnerability in the presence of a double page, view the upload page.
Method: (1) f12 find post the form to upload, action attribute is specified detection upload page, usually written by the absolute path, such as: xxx.asp / xxx.php.
(2) completion url: https://www.xxx.com/xxx.php(asp)
(3) construction of local post submission form
1 <form action="https://www.xxx.com/xxx.asp(php)" method="post" 2 name="form1" enctype="multipart/form‐data"> 3 <input name="FileName1" type="FILE" class="tx1" size="40"> 4 <input name="FileName2" type="FILE" class="tx1" size="40"> 5 <input type="submit" name="Submit" value= "Upload" > . 6 </ form >
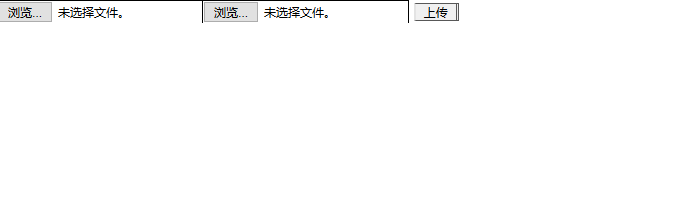
Just change the action when using the value of the specified upload page.
(4) The upload file is qualified (.jpg; .png; .gif, etc.); second word is uploaded or Trojan webshell
So that you can break through the upload limit, Trojan successfully uploaded to the server.
principle:
Uploading Point supports multiple file uploads, but only for the first file but do filter
Therefore, only the first upload a file extension for testing, for the second file is not detected directly uploaded to the server.
Look for a file upload vulnerability exists Dual Code
1 for i=0 to ubound(arrUpFileType) 2 if fileEXT=trim(arrUpFileType(i)) then 3 EnableUpload=true 4 exit for 5 end if 6 next
Beginning EnableUpload = false, but after entering the for loop above, it is judged that the file type is legitimate. If legitimate, EnableUpload value is True, so when the first file is a legitimate file, the file is not detected in the future.
Double file upload vulnerability is a relatively old vulnerability, its repair is very simple, it is only support a file upload.
Today we see this loophole, though aware of the use of methods, but the use of the principle still do not understand, so I picked a closer look at this loophole.
In fact, many using the method: You can also capture during the upload, a copy of the response packet, and then change the filename any name, such as: filename1 would also be a breakthrough upload limit.