1. Algorithm
In the application of high concurrency, the current limit is not open around the topic. Limiting our API can guarantee service availability for all users, can prevent network attacks.
Usually development of high concurrent systems have a common limiting: limits the total number of concurrent (such as a database connection pool, thread pool), to limit the number of concurrent transient (e.g. the nginx limit_conn module, intended to limit the number of concurrent connections instantaneous), within the limit of the time window average rate (such as Guava's RateLimiter, nginx's limit_req module, limiting the average rate per second); there are other restrictions, such as a remote interface call rate, MQ limit consumption rate. Also in accordance with the flow restrictor may be network connections, network traffic, CPU, or other memory load.
Limiting algorithm
Do restrictor (Rate Limiting / Throttling), apart from the simple control concurrency, if you want to accurately control the TPS, the simplest approach is to maintain Counter in a unit of time, such as determining the unit time has elapsed, then the Counter is reset to zero . This practice is considered no good boundary processing unit time, such as the former first millisecond in the last millisecond of one second and the next second it triggers the greatest number of requests, which is the place within two milliseconds twice the TPS.
Commonly used algorithms smoother flow restrictor has two: leaky bucket algorithm and the token bucket algorithm. Many traditional service providers such as Huawei, ZTE have similar patents, the reference method for packet token bucket of the flow restrictor .
Leaky Bucket Algorithm
Leaky bucket ( the Leaky Bucket ) algorithm is very simple idea, water (request) to the drain into the first bucket, bucket water at a constant speed (rate responsive to the interface), the inflow rate when the water overflows through direct Assembly (access frequency response over the interface rate), then reject the request, it can be seen leaky-bucket algorithm can impose restrictions on the data transmission rate.
There are two variables can be seen, it is the size of a barrel, how much water (burst) can be saved when the sudden increase in traffic support, and the other is the size of a bucket vulnerability (rate). Because the leakage rate of leaky bucket parameters are fixed, so that, even if the network resource conflict does not exist (no congestion occurs), the port can not leaky bucket flow rate burst (Burst) to. Therefore, the leaky bucket algorithm is inefficient for the presence of bursty nature of traffic is.
Token bucket algorithm
Token bucket algorithm (Token Bucket) and opposite effect Leaky Bucket algorithm and the same direction, more readily understood. Over time, the system will be a constant 1 / QPS time interval (if QPS = 100, the interval is 10ms) in the bucket added Token (imagine leaks and loopholes contrary, there is a constant increase in the tap water), if the bucket is full a plus not a. The new request comes, will each take a Token, if it took no Token can be blocked or denial of service.
An additional benefit is the token bucket can easily change the speed. Once the need to increase the rate, the token bucket rate of demand increase placed. Generally the timing (for example 100 milliseconds) increased the tub to a certain number of tokens, the number of the real-time algorithm Some variants should increase the computational token. Guava in RateLimiter uses a token bucket algorithm design ideas See How IS the Designed at The RateLimiter, and Why? , See detailed algorithm source code .
This article discusses the implementation of integrated gateway
2. Create a gateway project
For details, see: the Spring Cloud Gateway gateway
Adding pom on this basis in
<!--RequestRateLimiter限流--> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-data-redis-reactive</artifactId> </dependency>
3. Configure class
package com.common.config; import org.springframework.beans.factory.annotation.Qualifier; import org.springframework.cloud.gateway.filter.ratelimit.KeyResolver; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.Configuration; import org.springframework.context.annotation.Primary; import reactor.core.publisher.Mono; /** * @Title: * @Auther: * @Date: 2019/8/28 17:13 * @Version: 1.0 * @Description: */ @Configuration public class RequestRateLimiterConfig { @Bean @Primary KeyResolver apiKeyResolver() { //按URL限流 return exchange -> Mono.just(exchange.getRequest().getPath().toString()); } @Bean KeyResolver userKeyResolver() { //按用户限流 return exchange -> Mono.just(exchange.getRequest().getQueryParams().getFirst("user")); } @Bean KeyResolver ipKeyResolver() { //按IP来限流 return exchange -> Mono.just(exchange.getRequest().getRemoteAddress().getHostName()); } }
4.yml Configuration
application.yml
Spring: file application: name: gateway8710 Cloud: gateway: default - filter: routes: - ID: user- Server predicates: - the Path = / Java / ** Filters: - StripPrefix. 1 = # restrictor filter, using the built-in token gateway algorithm - name: RequestRateLimiter args: # average rate per second token bucket fill, i.e., the line is equivalent to allowing the user to handle the average number of requests per second Redis-limiter.replenishRate-rate: 10 # token bucket capacity, allows a the maximum number of requests completed within seconds redis-rate-limiter.burstCapacity: 20 # Parser for the name of Bean object keys of limiting. It acquires the SpEL expression Bean Spring objects from a container according to # {@ beanName}. Resolver-Key: "# @ apiKeyResolver {}" URI: LB: //-Service-Helloword ": # URI http://192.168.111.133 : 8708 / Project / Hello" Redis: #Redis index database (default 0) Database : 0 # connection time (ms) springboot2.0 the type of the parameter is Duration, It should be specified when the unit configuration timeout: 20S # password password: Test Cluster: # a maximum acquisition failure redirects max-redirects: 3 # test environment Redis Nodes: - 10.0.0.1:6380 - 10.0.0.2:6380 - 10.0.0.3:6380 - 10.0.0.1:6381 - 10.0.0.2:6381 - 10.0.0.3:6381 Lettuce: the pool: # Connection pool maximum number of connections (negative values no limit) max-Active: 300 # maximum blocking latency connection pool (negative values no limit) max-the wait: the -1s # connection pool maximum idle connection max- iDLE: 100 # minimum connection pool idle connections min-iDLE: 20 is Server: Port: 8710 Eureka: Client: the serviceUrl: # to registration center defaultzone: http://192.168.111.133 : 8888 / Eureka / instance: # intervals 1s, is sent to the server once a heartbeat, prove that they are still "alive" Lease-Renewal-interval the-in-seconds the: 1 # tell the server if I within 2s it does not give you the heart, on behalf of my "dead", I will be kicked out. lease-expiration-duration-in- seconds: 2
Directory structure is as follows
5. Start Testing
Jmeter need to do with concurrency test, within one second start 30 processes repeatedly send requests 10,000 times.
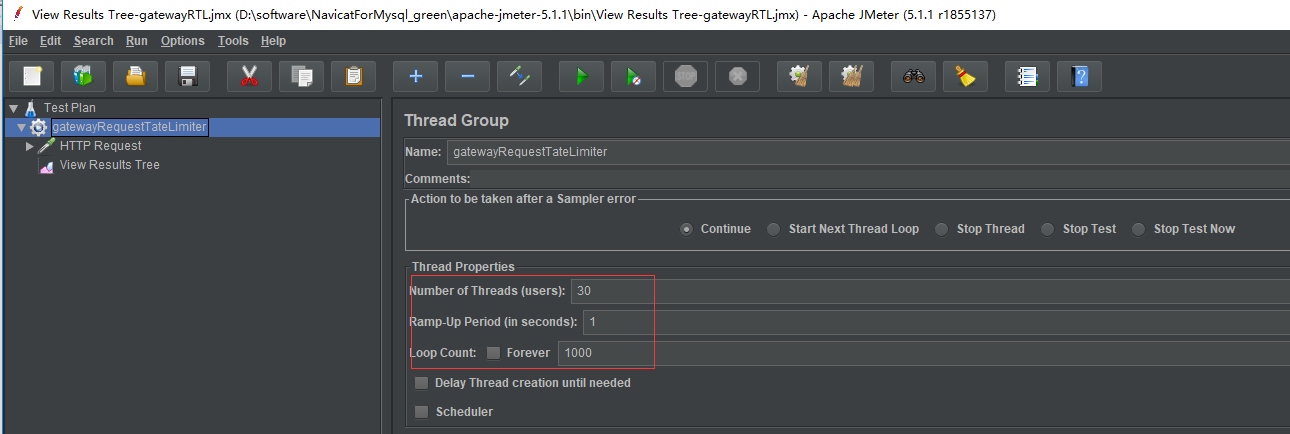
The test results, not grab the token request 429 returns, limiting side corresponds to an average request: 10 / s
