A, ssh two login ways
1, user login password
Username Password Log ways: The client needs to know the login user name and password for the server, for example: 192.168.0.1 server root user password is 123456. It can connect to the server via root login and password 123456 directly. This login account information directly exposed to the server.
linu Server Login: ssh username @ server IP address

2, login key pair: the local client creates a key pair, public key to the remote server first generated key pair, when the client sends a connection request to the remote server, a client's public key transmitted together to the server, when the server receives the public key, the server queries the local end is not stored in the client's public key, and if not, the connection request is rejected. If so, the server sends a "challenge" message to the client, and the client is encrypted with the public key, for example, 123456. After the client's public key encryption becomes abcdef. At the same time it would send the public key of the server to the client. After receiving questioned Information Server customers will pass the client's private key to decrypt the information challenge. For example, abcdef 123456 to be decrypted. The client encrypts the challenge decrypted information received by the server's public key, the question information back to the server. For example, encrypted to 123456 qwerty. After the server can decrypt the information received by the private key question for questioning server information. If the information decrypted and sent to the same information before their own clients. Remote connection request is allowed.
Linux server remote login:
Create a key pair on the client, and then submit the public key to the server. Then use telnet command to log on.
Creating keys

Upload client secret key in the public key to the server

Telnet client to test server
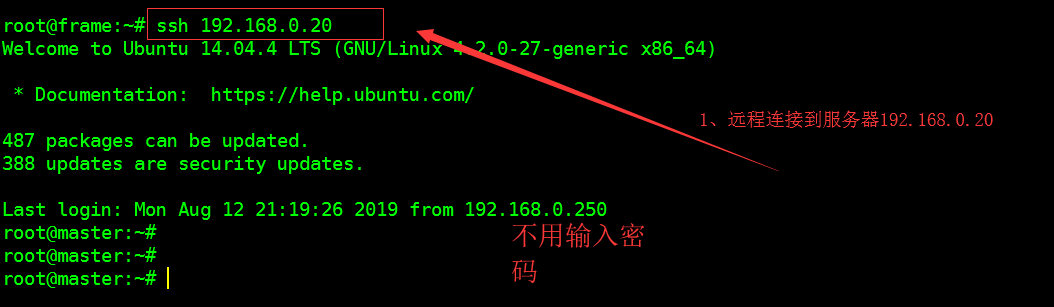
Two, ssh service profile
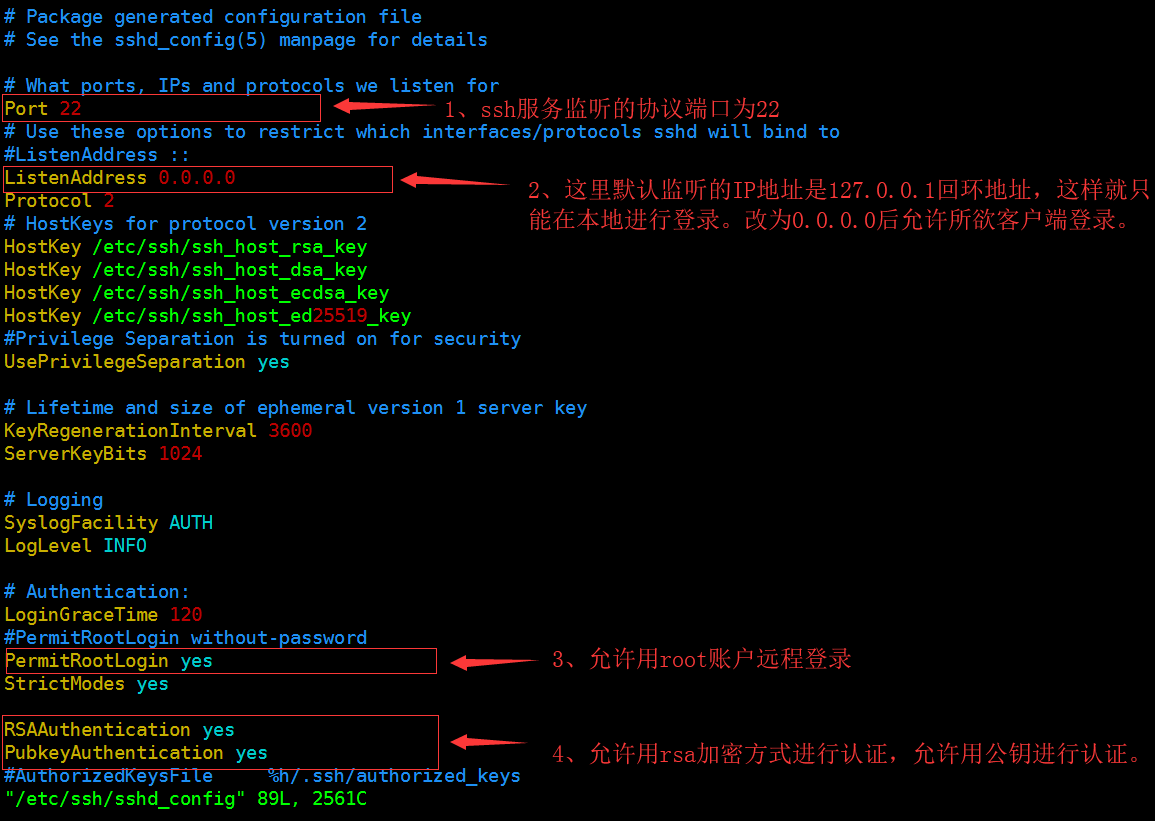
ssh service configuration files in / etc / ssh / sshd_config, can be edited by vim / etc / ssh / sshd_config.
1, ssh monitor card
ssh default monitoring the local network card, so would not be able to remotely log in. So we need to modify the configuration of interception
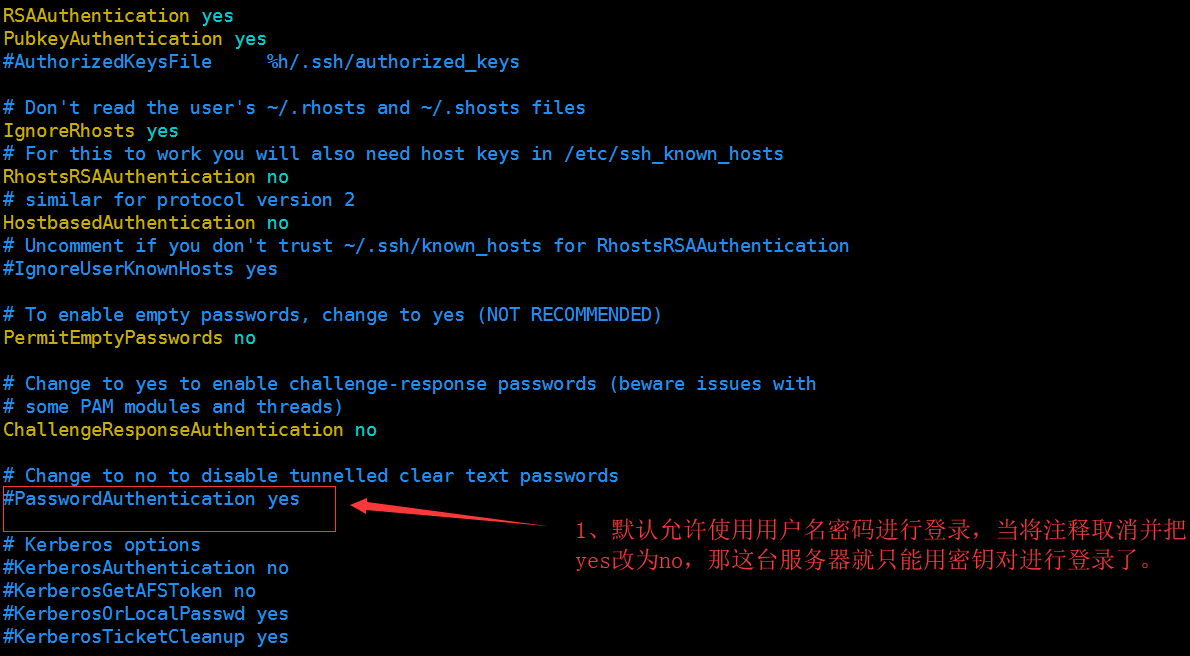
Before you disable the user name password, the key must be configured to log in, otherwise it can only be registered on this machine. If the server is okay locally, if the server in the field trouble.