It reminds us this is really blasting. . . . Well, I do not quite believe that he is very bad at this poor old man
Look at the code

1. The first sentence is prescribed reporting error level is 0 , that is, Disable error Reporting ( not report an error )
2. The second sentence is to store session data, that is, to a server information on a web page, here we come
3. The third sentence is require function: also cited flag.php mean, however, and include different is that it will stop execution if an error page and include will continue
4. Then an if structure, first determine $ _SESSION [ 'the nums'] is empty or was NULL , if not then let $ _SESSION [ 'the nums'] = 0 , $ _SESSION [ 'Time'] = Time () time () function returns the number of seconds since the Unix epoch (January 1 1970 00:00:00 GMT) from the current time , $ _SESSION [ 'the whoami'] = 'EA'.
5 and then a if judgment, when the session value is +120 later than the current time on the implementation of the session_destroy () function: destruction session
6.value to post incoming form
7. Create a from a to z let equal the array str_rand
8. generates two random str_rand then let them connect assigned to str_rands
9. an if structure, if whoami first and second bit array equal, and the variable value of the hash value from the fifth to the ninth bit is equal to 0 then let the nums. 1 + , so whoami value equal str_rands, then print out str_rands
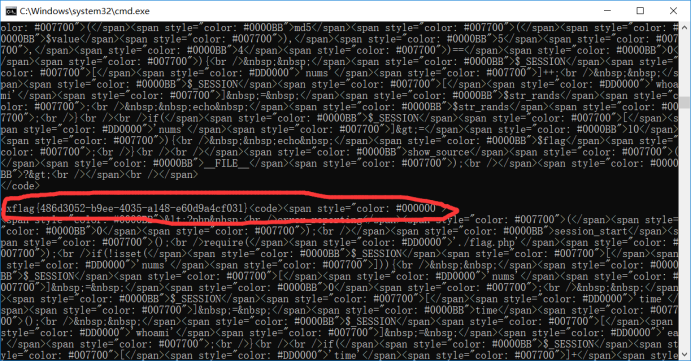
10. If nums values is greater than 10 , the print flag
Browse entire sections of code, which means the whole process is that we need to open a web page 2 is completed within minutes, and then the value of the value of ae , nums value to +1 , then generates a random number, if value and this value is equal to make nums again +1 iteratively repeated until nums greater than 10 outputs flag
So here blasting using a script (script attached a dalao of)
import requests url = "http://53617f45ee114de4945b1fc8661d2c36844810d2d02f4882.changame.ichunqiu.com//?value[]=ea" al = ['abcdefghijklmnopqrstuvwxyz'] s = requests.session() r = s.get(url) for i in range(20): url = "http://53617f45ee114de4945b1fc8661d2c36844810d2d02f4882.changame.ichunqiu.com//?value[]=" + r.content[0:2] r = s.get(url) print r.content
Note: url into your own web page links
You can get the flag up