In reptiles crawling the site, often encountered some anti-crawler technology, such as:
- Plus cookie, authentication UserAgent
- Captcha, as well as verification is difficult to break slide
- js signature verification, to encrypt data processing
Js for encrypting
the encrypted cipher text is transmitted, but the encryption function or process must be completed in the browser,
i.e. js code will certainly be exposed to the user
by reading the encryption algorithm, the encryption process can be simulated, so as to achieve crack
how js judgment site does not use encryption, very simple, such as the proper way translator
- 1. Open the Word [Translator] Web page: http: //fanyi.youdao.com/
- 2. Right [check], select [Network]
- 3. Enter the word []
- 4. In the request, find the Form Data on translations, you can see two notes have the following js encryption
“salt”: “1523100789519”, “sign”: “b8a55a436686cd8973fa46514ccedbe”,
Analysis js
- Be sure to follow the order, otherwise there will be a lot of useless things interference
- 1. Open the Word [Translator] Web page: http: //fanyi.youdao.com/
- 2. Right [check], select [Network]
- 3. Enter the word [], [] grab js code
- Operating Screenshot:
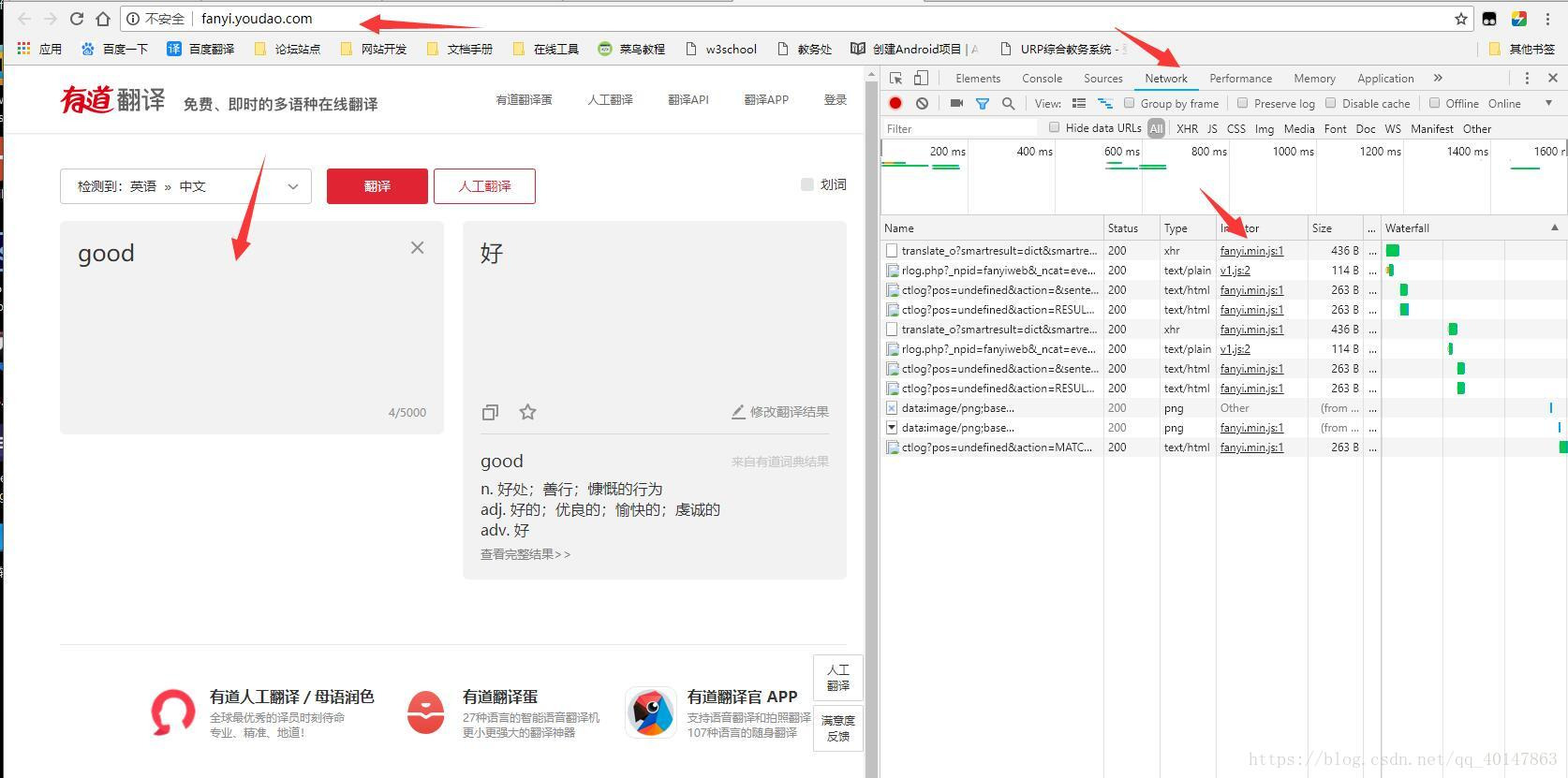
- js code we get the line of code, the code is compressed min, we need a format conversion
- 4. Open the online code formatting web site: http: //tool.oschina.net/codeformat/js
- 5. The row copied js code format, paste form, click [Format]
- Operating Screenshot:
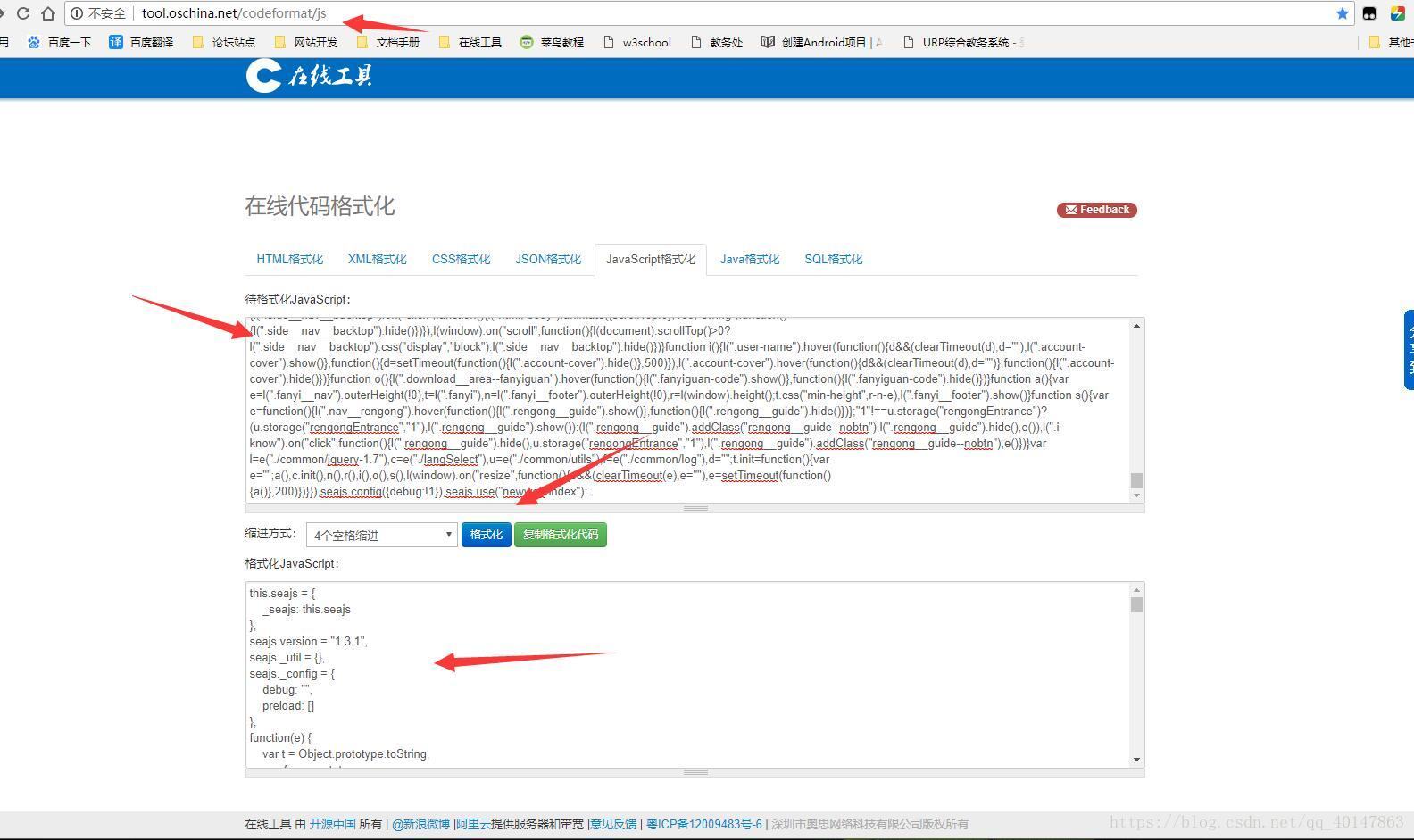
- Then formatted js code, can be copied to a search code encoder, spare
- Preparation of the first two editions
- V18 Case Files:
- https://xpwi.github.io/py/py%E7%88%AC%E8%99%AB/py18js2.py
# 破解js加密,版本2 ''' 通过在js文件中查找salt或者sign,可以找到 1.可以找到这个计算salt的公式 r = "" + ((new Date).getTime() + parseInt(10 * Math.random(), 10)) 2.sign:n.md5("fanyideskweb" + t + r + "ebSeFb%=XZ%T[KZ)c(sy!"); md5 一共需要四个参数,第一个和第四个都是固定值得字符串,第三个是所谓的salt, 第二个参数是输入的需要翻译的单词
Python学习交流群:857662006 ''' from urllib import request, parse def getSalt(): ''' salt的公式r = "" + ((new Date).getTime() + parseInt(10 * Math.random(), 10)) 把它翻译成python代码 ''' import time, random salt = int(time.time()*1000) + random.randint(0, 10) return salt def getMD5(v): import hashlib md5 = hashlib.md5() md5.update(v.encode('utf-8')) sign = md5.hexdigest() return sign def getSign(key, salt): sign = "fanyideskweb" + key + str(salt) + "ebSeFb%=XZ%T[KZ)c(sy!" sign = getMD5(sign) return sign def youdao(key): # url从http://fanyi.youdao.com输入词汇右键检查得到 url = "http://fanyi.youdao.com/translate_o?smartresult=dict&smartresult=true" salt = getSalt() # data从右键检查FormData得到 data = { "i": key, "from": "AUTO", "to": "AUTO", "smartresult": "dict", "client": "fanyideskweb", "salt": str(salt), "sign": getSign(key, salt), "doctype": "json", "version": "2.1", "keyform": "fanyi.web", "action": "FY_BY_REALTIME", "typoResult": "false" } print(data) # 对data进行编码,因为参数data需要bytes格式 data = parse.urlencode(data).encode() # headers从右键检查Request Headers得到 headers = { "Accept": "application/json, text/javascript, */*; q=0.01", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "keep-alive", "Content-Length": len(data), "Content-Type": "application/x-www-form-urlencoded; charset=UTF-8", "Cookie": "[email protected]; OUTFOX_SEARCH_USER_ID_NCOO=366356259.5731474; _ntes_nnid=1f61e8bddac5e72660c6d06445559ffb,1535033370622; JSESSIONID=aaaVeQTI9KXfqfVBNsXvw; ___rl__test__cookies=1535204044230", "Host": "fanyi.youdao.com", "Origin": "http://fanyi.youdao.com", "Referer": "http://fanyi.youdao.com/", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.75 Safari/537.36", "X-Requested-With": "XMLHttpRequest" } req = request.Request(url=url, data=data, headers=headers) rsp = request.urlopen(req) html = rsp.read().decode() print(html) if __name__ == '__main__': youdao("girl")
运行结果
返回翻译后的值,才算是成功
注意
按照步骤,熟悉流程最重要
---------------------
原文:https://blog.csdn.net/qq_40147863/article/details/82079649