Article Directory
First, the user information file
User information file storage path is /etc/passwd, look at the contents of the file with vim:
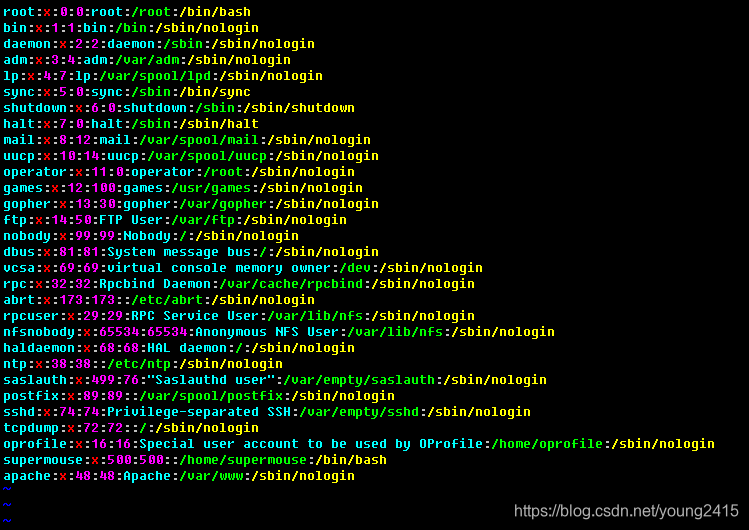
At first glance it seems dazzling, no clue. But never mind, we can use the help command to man 5 passwdlook at the role of passwd profile.
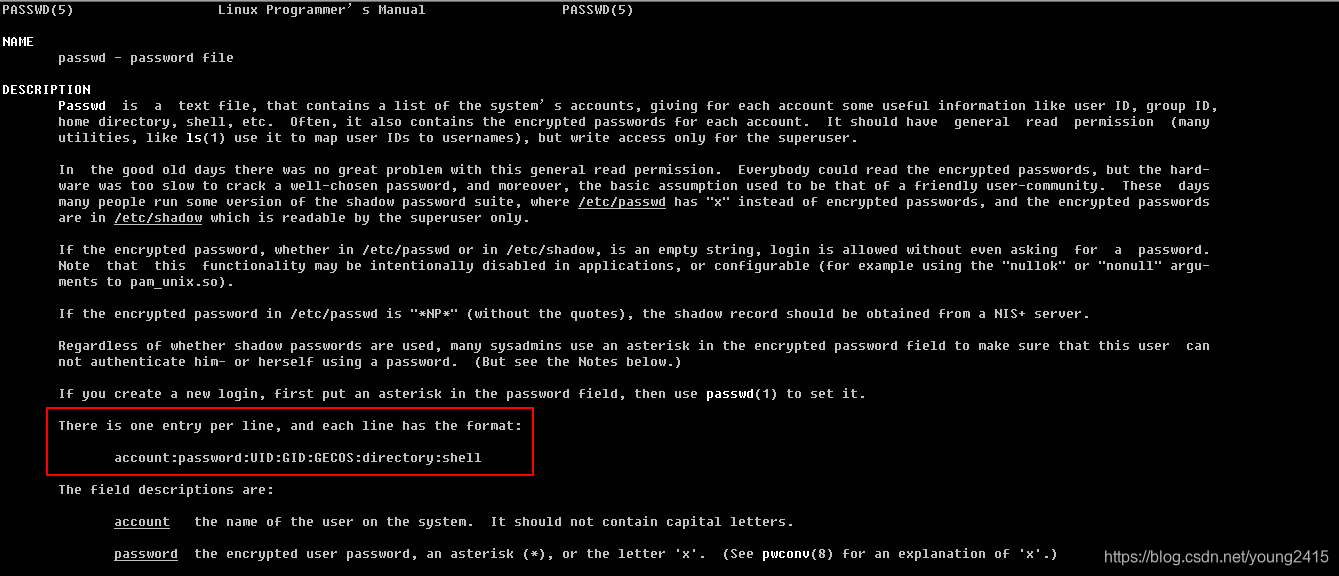
Figure out mainly in the circle of the two lines, it tells us that each line passwd file on behalf of a user configuration, and user information format of each is as follows:
account:password:UID:GID:GECOS:directory:shell
You can see, each user information has seven fields, separated by colons between fields, respectively, explain the meaning of the following seven fields:
-
The first field: user name
-
2 fields: password flags. If the password flag is x, on behalf of the user has a password, the password file is stored in
/etc/shadowthe; if the password flag is empty, the system assumes the user has no password, no password at login you can log in, but only in this way able to log on locally, not via telnet. -
Field 3: user ID. ID representing different ranges of different types of users:
-
- 0: superuser
- 1-499: User (pseudo-user)
- 500-65535: ordinary users
Pseudo-user is for the system to start some order or service call, it is essential for the system, these users do not delete!
In fact, the system is to identify different users by user ID. If you want to become a regular user superuser, just put the user's ID can be changed to 0, then the system will all the same user ID as a user to look at.
-
Field 4: GID (initial user group ID)
-
Each time a user is created, the system will create a group and the same user name, that user belongs to the default group. Users can change the initial group, but only one; there is a concept of an "add-group" means a user can join a number of other groups, and these groups have rights, additional groups of users can have multiple .
If you want to know the user's initial group ID in the end which corresponds to a group, you can view the
/etc/groupfile. -
5 fields: Notes.
-
6 fields: the user's home directory. That is the position of the user's initial login. Average user's home directory is
/home/用户名/super user's home directory/root/. -
7 field: Shell after login. Shell is a Linux command interpreter. If you want to disable a user, the user can change the command interpreter in addition to
/bin/bashany other than string, so that the user can not log in. If you want to lift off, his command interpreter and then changed/bin/bashit.
Second, the shadow file
As the name suggests, this file is the shadow file Recall user information file storage path is /etc/shadow.
File permissions is 000, but the root user unlimited permissions, you can read the contents of the file. Let's look at the contents of a file with vim:
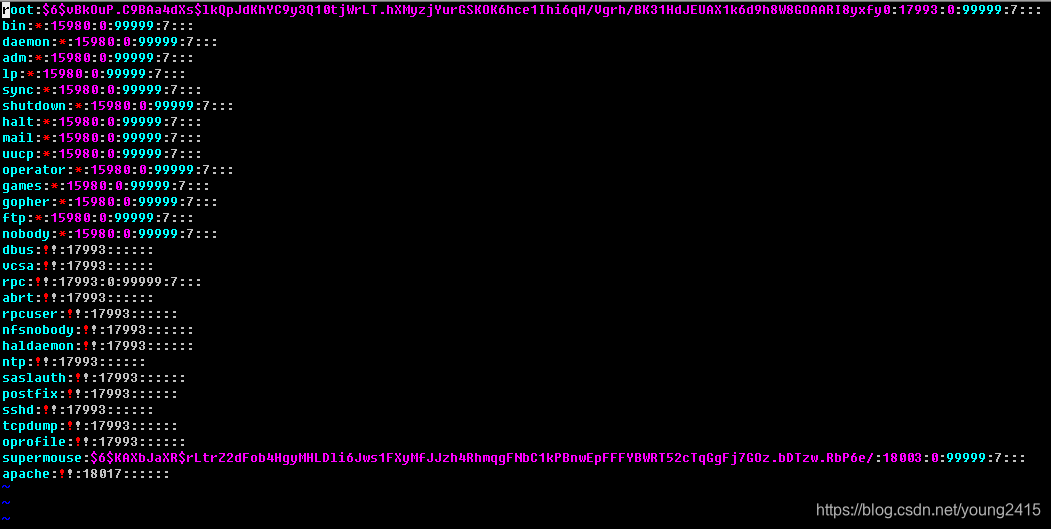
Like user information file, the file is also Each line represents a user, the difference is that each line of the file has nine fields, following an explanation of the meaning of the nine fields.
-
The first field: user name.
-
2 fields: the encryption password. SHA512 hash encryption algorithm encryption algorithm, if the password is a bit "!" Or "*" means no password, can not log on.
-
3 fields: password last modified date. Using 1 January 1970 as the standard time. With each passing day the timestamp plus one.
-
4 fields: allows you to modify the password date interval to "day" as a unit. For example: If it is 0, it means there is no limit; if it is 10, it means that if the password is changed today, to wait until after at least 10 days to change the password again.
-
5 fields: password expiration, but also to "day" as a unit
-
6 fields: Password modify the number of days before the warning expires. That is, assuming the fifth field is 90, the sixth field is 7, then from the first 83 days after the change password every time you log on, Linux will warn, remind you to change your password.
-
7 fields: grace days after the password expires. If it is empty or 0, indicating that the password immediately expire, the user can not log in; if it is -1, which means the password expiration will never fail, users can still continue to use the password to log in.
-
8 fields: User period, expressed as a time stamp. The first is the number of days from January 1, 1970 start of the count. Valid until after the user, regardless of the user's password to never expire, you can no longer log in.
-
For people, the time stamp may not be so intuitive, we are more accustomed to represent the date by date. Fortunately, there are Linux-related command can transform date and time stamp of.
date -d "1970-01-01 17993 days" //把16066转换成日期 echo $(($(date --date="2019/05/05" +%s)/86400+1)) //把2019/05/05转换成时间戳 -
9 field: Reserved.
Third, the group information file
Group information in the file is stored in groups of related information, stored path /etc/group.
In Linux, each create a user creates a group name with the user name the same group as the initial set of the user.
Windows is created for each user, will default on the Users group.
With vim look at the contents of the file:

each line of the file on behalf of a group, each group with four fields of information, the following details about the meaning of each field:
- 1 fields: group name.
- 2 fields: password flags. Password here refers to the group password. Group files are stored in password
/etc/gshadowin. What role does the group password? Originally a member of the group is only the root user can add and delete when the root user to a group set up a group administrators and group password, group administrators can add and subtract in the past, the group members. As a result equivalent to the fate of a group leader, this leader can exercise the right to remove the root user to add group members. But this will reduce the security of the system, it is not recommended to use the group password. - 3 fields: GID. That group ID.
- Field 4: additional user group.
Fourth, other documents related to user management
The user's home directory
The user's home directory is the initial position of the user's login.
- Average user:
/home/用户名/the owner and group of all user permissions 700 - Super User:
/root/, owner and group are the root user privileges is 550
User's mailbox
path:/var/spool/mail/用户名
User Template directory
path:/etc/skel/
When you create a user, the directory files are copied to the user's home directory. You can also manually create some customized files in the directory, when you create a user-defined file will be copied to the user's home directory.