PT Network Attack Discovery 11 (Linux) - Network Detection and Response (NDR/NTA) System
Please visit the original link: https://sysin.org/blog/pt-network-attack-discovery/ to view the latest version. Original work, please keep the source when reprinting.
Author homepage: sysin.org

Positive Technologies
PT Cyber Attack Discovery
Makes Hidden Threats Visible
product description
PT Network Attack Discovery is a network detection and response (NDR/NTA) system used to detect attacks at the network perimeter and within. The system makes hidden threats visible, detects suspicious activity even in encrypted traffic, and helps investigate incidents.
- Provide network visibility
PT NAD recognizes more than 85 protocols and parses the 30 most common protocols up to L7 level (sysin). Get a complete view of what's happening in your infrastructure to identify security flaws that trigger attacks.
- Detect hidden threats
The system automatically detects attackers' attempts to penetrate a network and identifies the presence of hackers on the infrastructure based on various indicators, including the use of hacking tools and the transmission of data to the attacker's servers.
- Make SOC more effective
PT NAD provides security operations centers with complete network visibility: understand whether an attack was successful, reconstruct the kill chain, and collect evidence. To this end, PT NAD stores metadata and raw traffic to help quickly find sessions and identify suspicious sessions, and supports traffic export and import.

PT NAD users can view threat data in a single source
With the new version of PT NAD, you can use the new analysis module to detect attacks (sysin), collect the latest information about network hosts, and gain centralized visibility into detected threats in a single source.
Detect malicious activity in east/west traffic
PT NAD analyzes north/south and east/west traffic and detects lateral movement, attempts to exploit vulnerabilities, and attacks against end users on domains and internal services.
PT NAD test
Threats in encrypted traffic
Lateral movement
Use hacking tools
Exploit vulnerabilities
Malware activity
past attacks
Malicious evasion of security tools
Connect to an automatically generated domain
Failure to comply with information systems policies
How PT NAD maps to MITER ATT&CK
Learn how PT Network Attack Prevention, a network detection and response system, identifies 117 adversary techniques described in MITER ATT&CK.
Even modified malware can be detected
PT NAD alerts on all dangerous threats and even detects modified versions of malware. To characterize the full spectrum of cyber threats, our experts continually explore the latest malware samples and hacking tools, techniques, and procedures. Every rule they create covers an entire malware family.
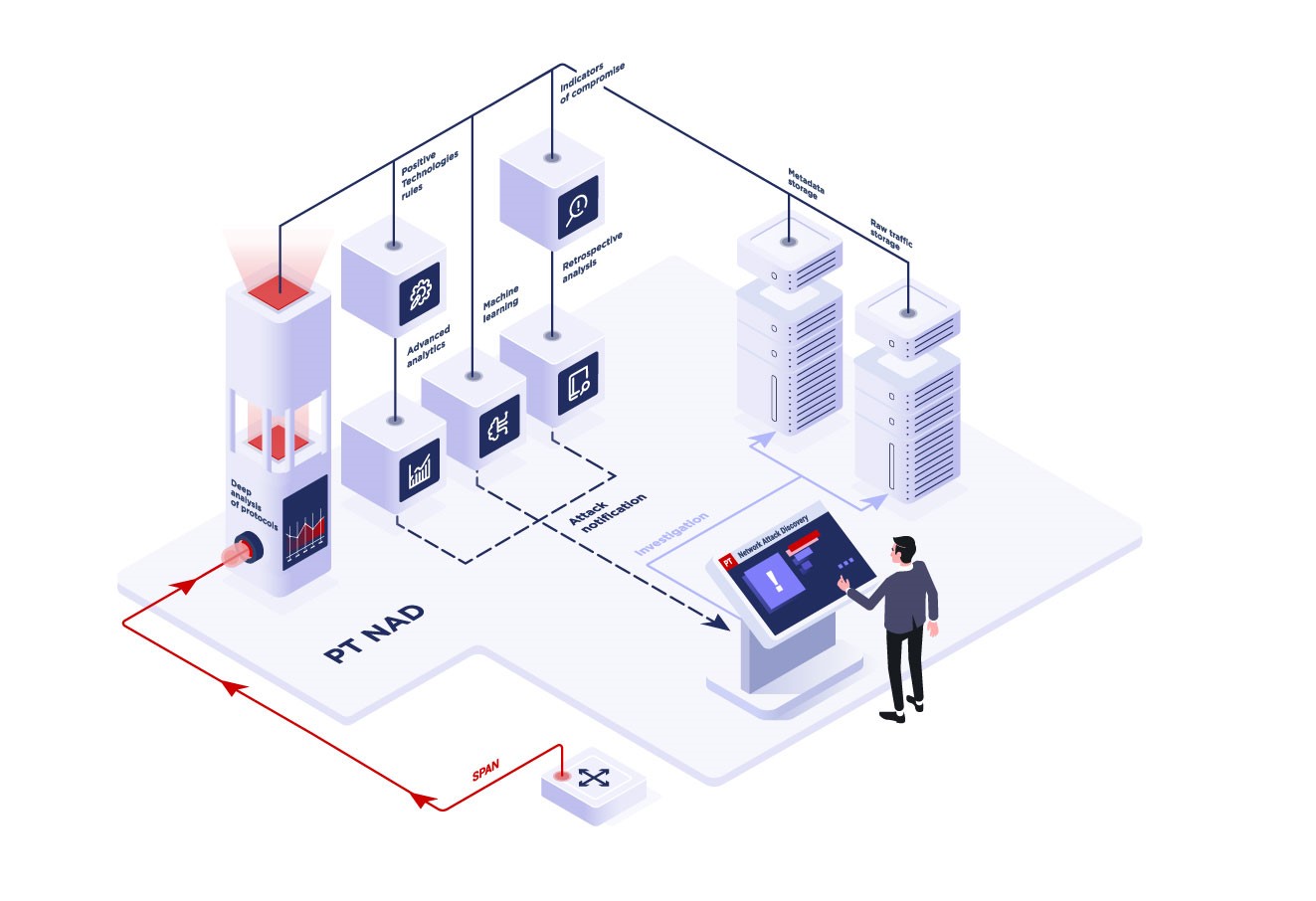
How it works
PT NAD captures and analyzes traffic (sysin) for perimeter and internal infrastructure. This allows detection of hacker activity at the earliest stages of network penetration and during attempts to gain a foothold on the network and launch attacks.
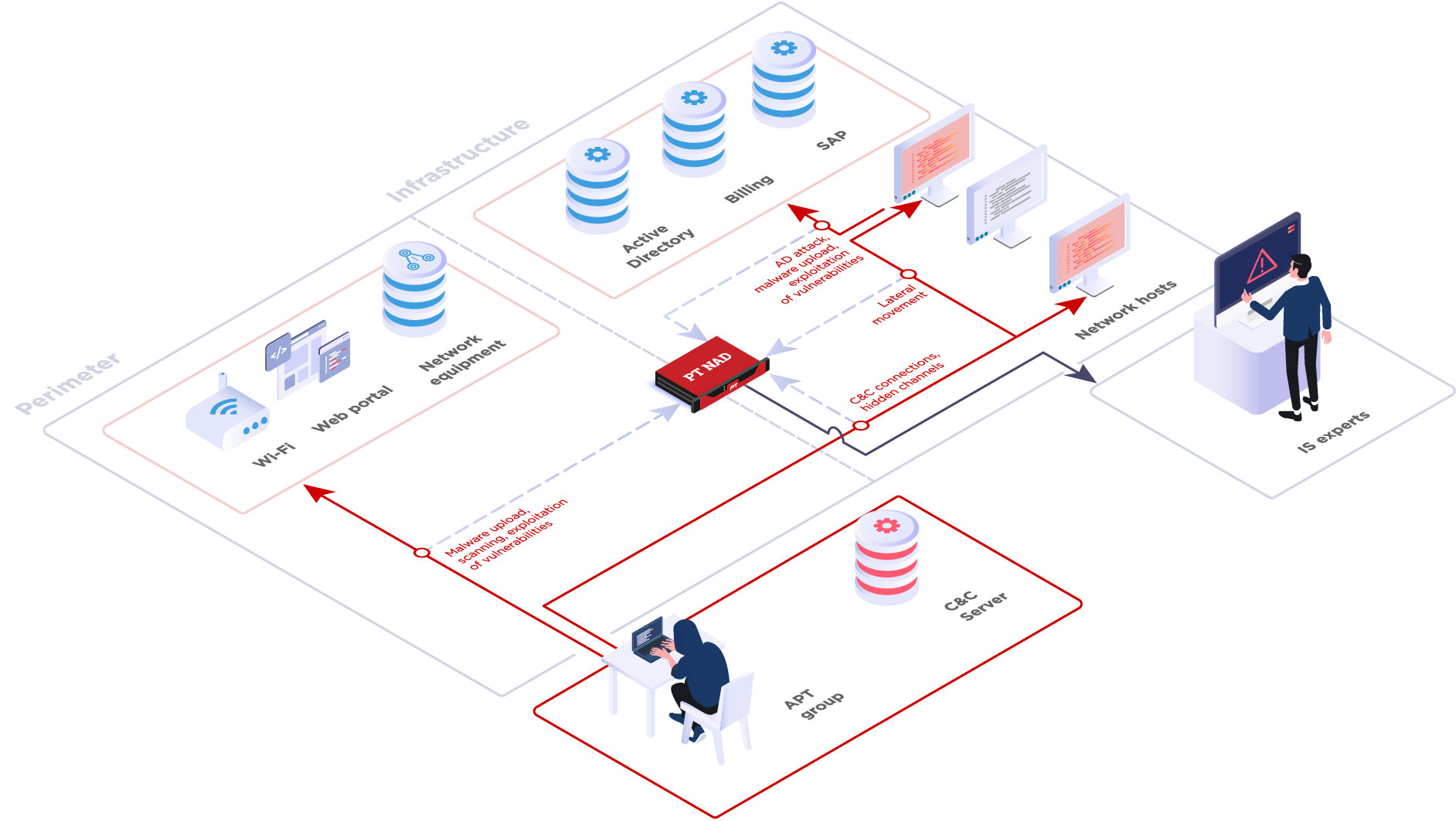
Keep attacks private
PT NAD is a local solution. All data is stored on client infrastructure and never leaves company boundaries. Information about attacks and damage is not transmitted externally, minimizing reputational risk.
Example
Security policy compliance
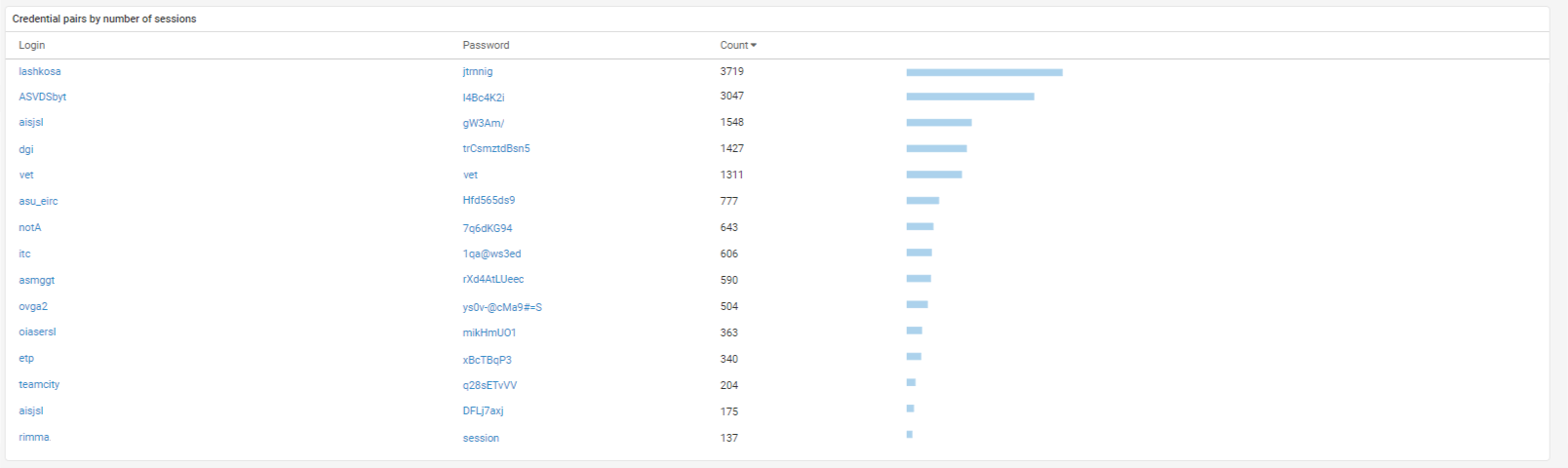
PT NAD detects IT configuration flaws and non-compliance with security policies, which may otherwise provide an entryway for attackers. Filters help quickly identify credentials stored in clear text, weak passwords, remote access utilities, and tools that hide network activity. Pin filters of interest in separate widgets for quick reference. Here is a widget that displays all non-encrypted passwords:
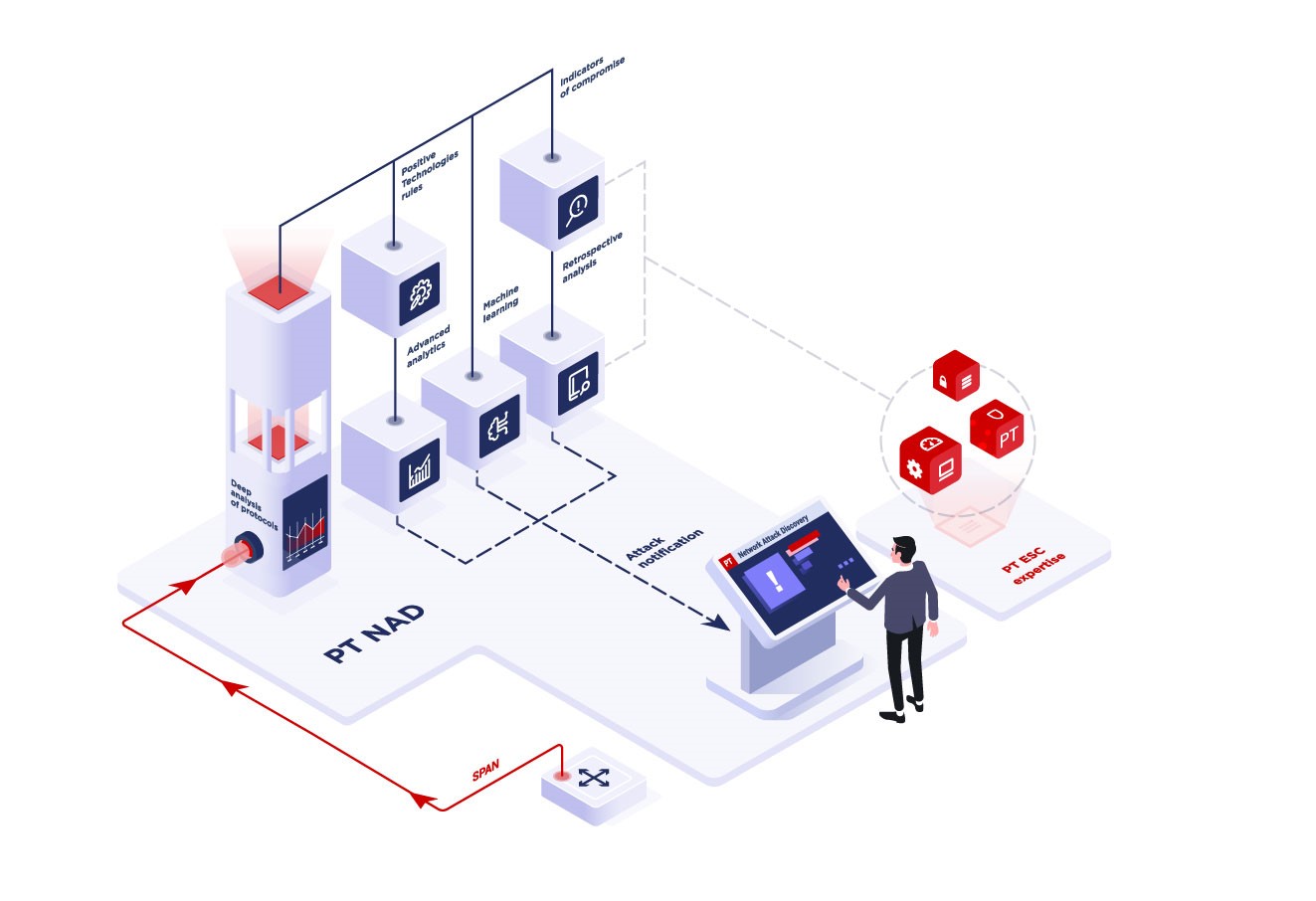
Detect attacks at the perimeter and within the network
With embedded machine learning technology, advanced analytics, unique threat detection rules, indicators of compromise and retrospective analysis, PT NAD can detect attacks at their earliest stages and after attackers have compromised the infrastructure.
The PT Expert Security Center updates rules and compromise indicators (sysin) twice a week. Updating the database does not require a continuous connection to the Positive Technologies cloud.
Advanced analytics modules identify sophisticated threats and network anomalies. Unlike attack detection rules, they consider many parameters of attacker behavior and do not rely on the analysis of a single session.
attack investigation
Because PT NAD maintains copies of raw traffic and session data, forensic investigators can:
- Localized attacks.
- Rebuild the kill chain.
- Detect vulnerabilities in infrastructure.
- Take steps to prevent similar attacks.
- Gather evidence of malicious activity.
Threat hunting
PT NAD is ideal for threat hunting and detecting hidden threats that standard network security tools miss. Security analysts with the necessary skills and infrastructure-specific knowledge can empirically test hypotheses. Therefore, PT NAD can determine if a hacking group, insider threat or data breach is indeed present and, if the hypothesis is confirmed, appropriate proactive measures can be taken.

Main features
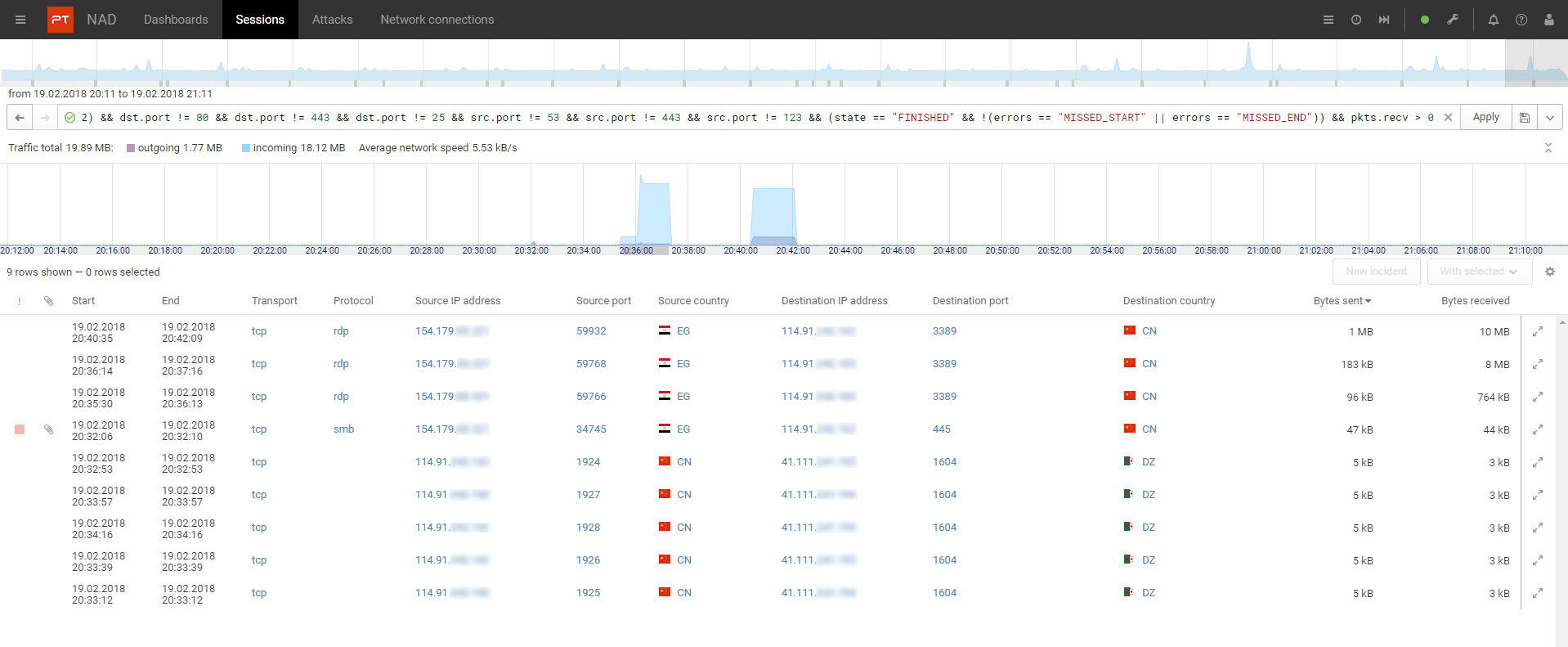
Session filtering
Filtering sessions provides a way to find malicious activity, signs of compromise, and configuration errors. PT NAD can quickly sort conversations by any of 1,200 parameters and display details for each message.
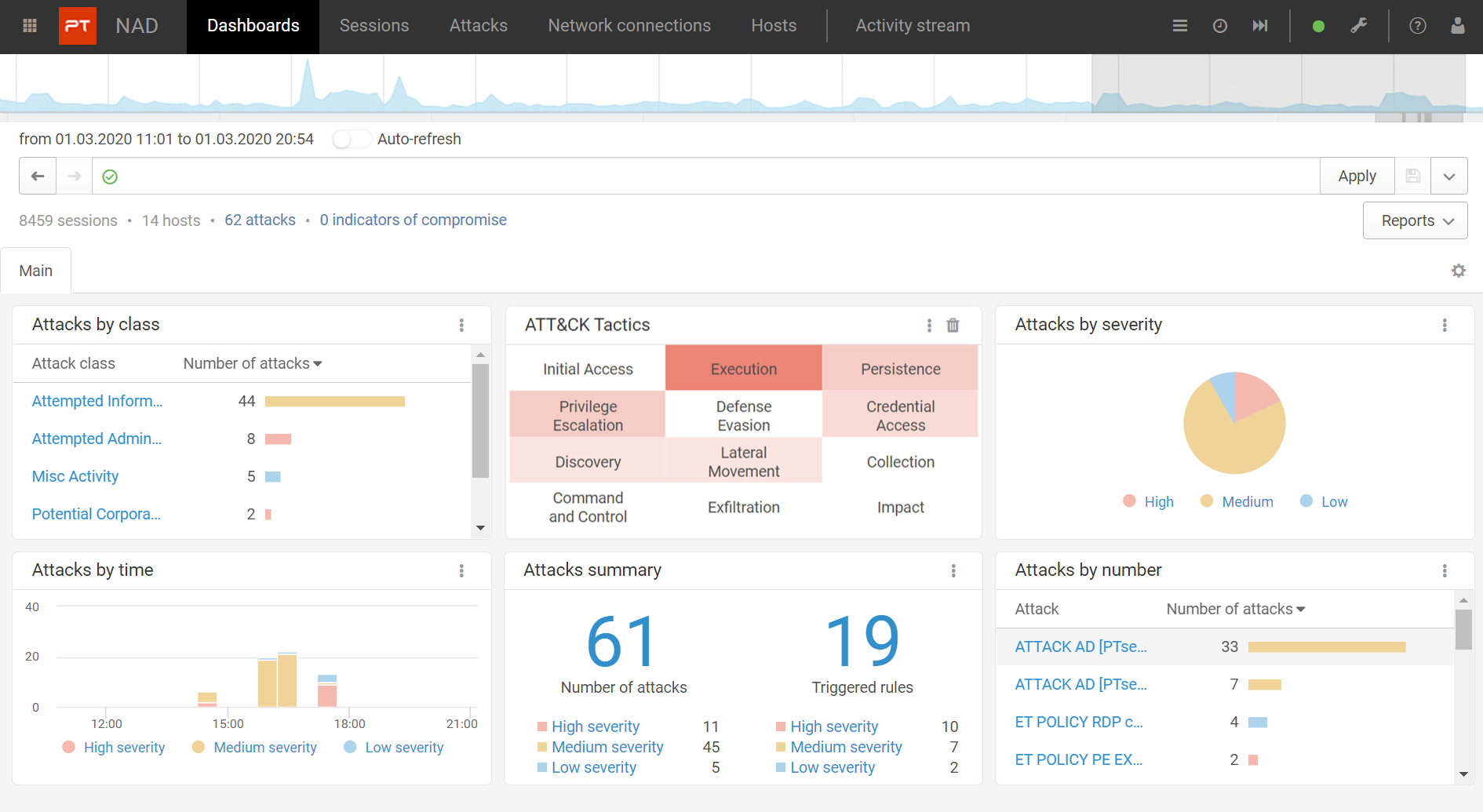
Attack Detection
The system notifies of events and automatically assesses how dangerous they are (sysin). The dashboard provides key information about all attacks: how many, what type of danger, how dangerous it is, and when it occurred. For any attack click to view details.
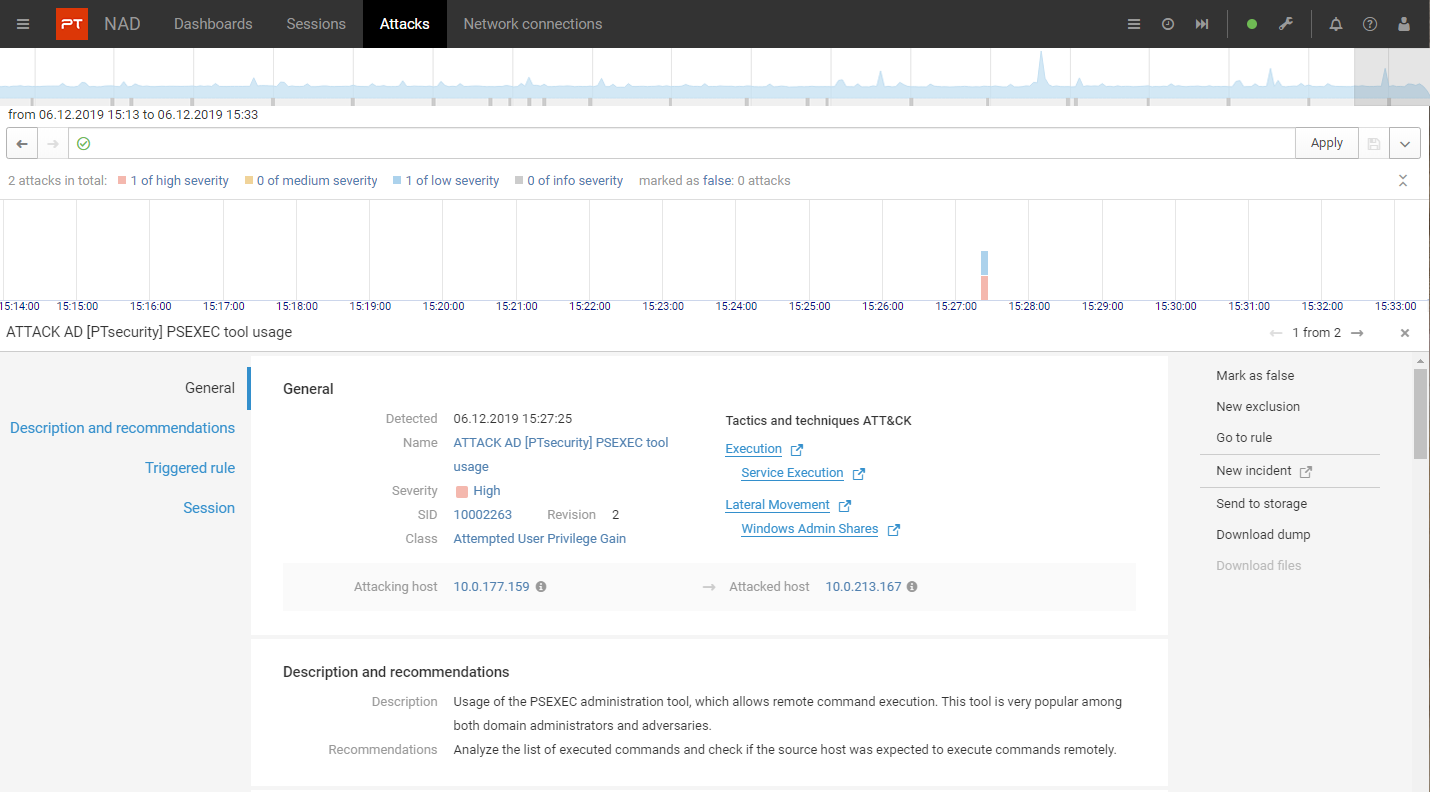
Replies at a Glance
Information for each attack shows affected hosts, event time, session data, and Hacking Tools, Techniques, and Procedures (TTP) MITER ATT&CK classification. Armed with attack stage information, you can take the right steps to get the job done.
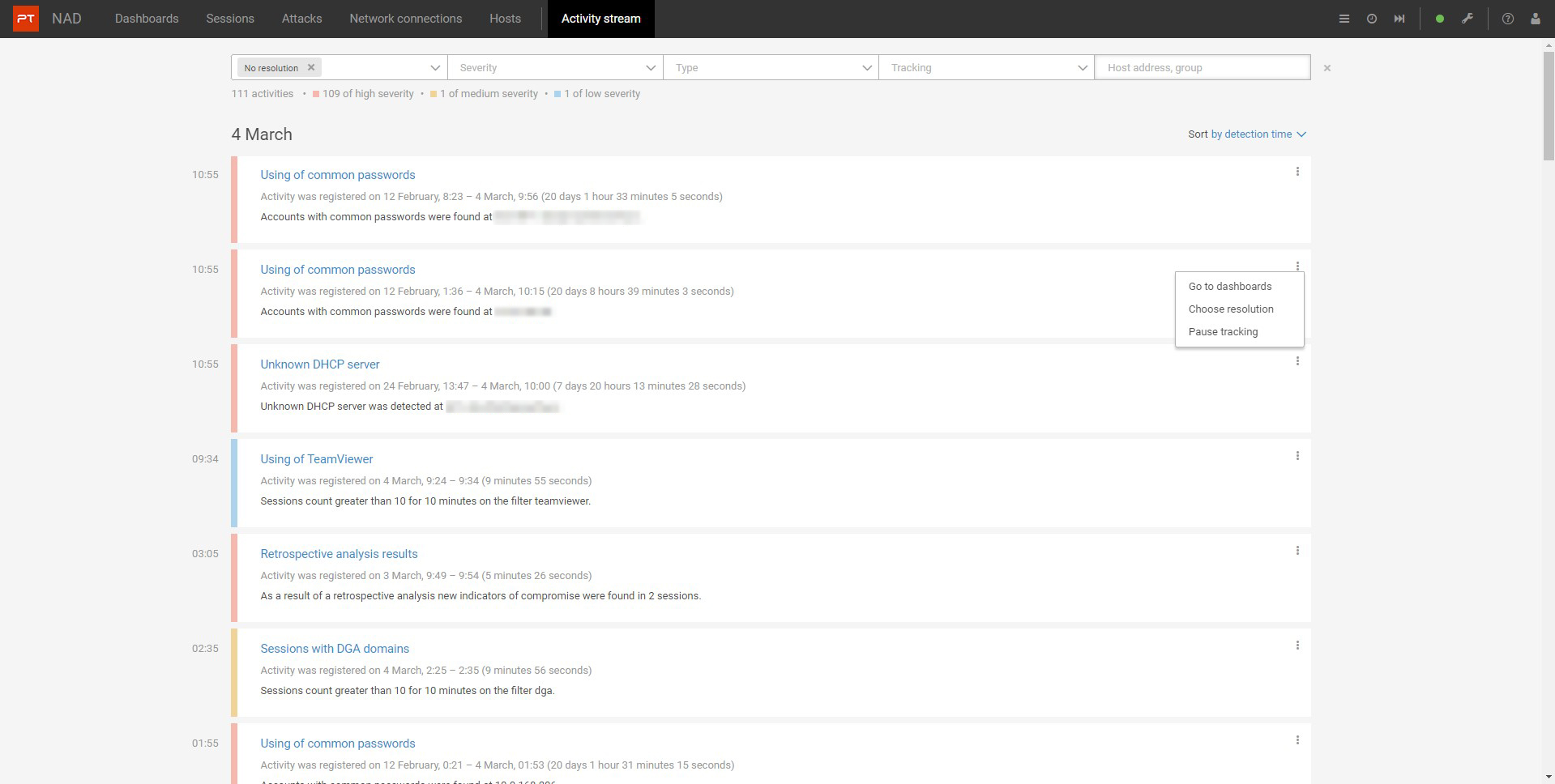
Learn about new attacks and threats from a single
source Activity Feed collects lists of identified threats into one location, consolidates messages about similar activities into one, and allows you to manage them. You can mark the issue as resolved or no longer track such activity.
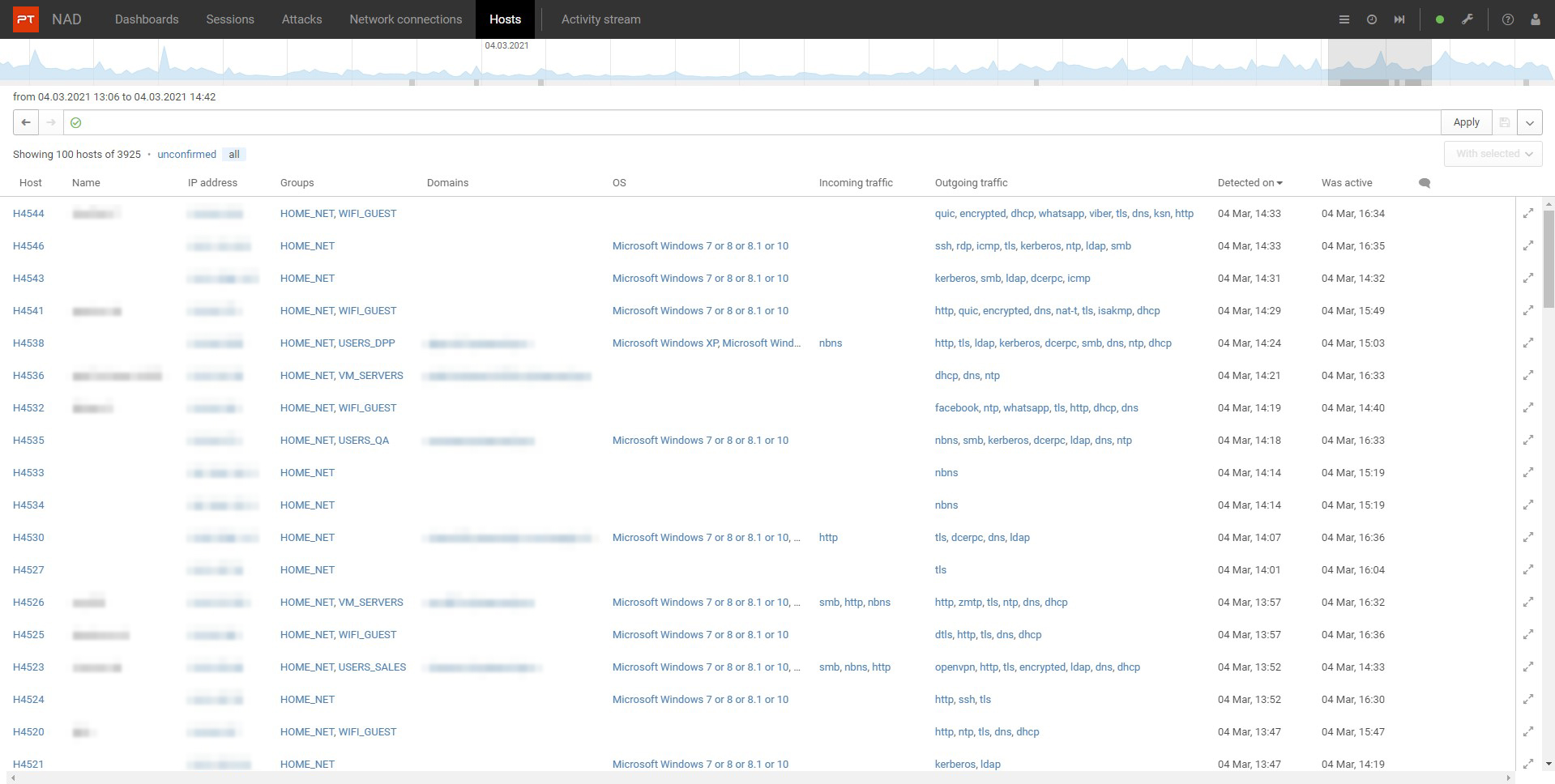
Monitoring Network Hosts
PT NAD users now have up-to-date information about network hosts (sysin). Host changes are also tracked. PT NAD users will know if a new host has appeared on the network, if application protocols have changed, or if the operating system has changed. Such data can also help identify suspicious activity.
Integrate with SIEM and sandbox solutions
By leveraging powerful integrated support, users can manage events and detect malicious content in file traffic.
System Requirements
Software requirements
PT NAD is compatible with 64-bit server versions of the following operating systems:
- Debian 10 Buster
- Astra Linux Special Edition 1.7
Operation of Linux kernels up to version 5.10 inclusive is guaranteed. It is recommended that you install PT NAD on a clean operating system.
The operating system in which you want to install PT NAD must meet the following requirements:
- No swap partition or file.
- Required mount points are created.
- No antivirus scanners running.
- No user with the login nad.
Mount points
| Mount point | Type of data carrier | Server (in case of multiserver configuration) | Used for |
|---|---|---|---|
| / | SSD | Any | PT NAD modules and OS |
| /es | SSD | Main and additional with the Elasticsearch module | Storing traffic metadata |
| /pcaps | SSD | Additional with the sensor | Storing the original copy of traffic |
It is recommended to use the Google Chrome or Mozilla Firefox browser to work with the PT NAD interface.
download link
PT Network Attack Discovery 11.0 for Debian
Baidu network disk link: https://sysin.org/blog/pt-network-attack-discovery/