
Students who need it can contact them via private message. It is recommended to pay attention to the subscription account platform in the lower right corner of the above picture to download it.
What we bring to you today is the Guangzhou Pazhou Algorithm Competition - Transmission Channel Hazard Target Detection Algorithm. This competition question is based on deep learning technology to automatically detect channel hazards in transmission lines. Participants are required to design efficient and accurate algorithms and consider a variety of equipment. Types and interference factors are used for model construction, training and inference.
01
—
Introduction to competition questions
With the rapid development of my country's energy industry, it has brought huge challenges to the operation and maintenance of power transmission channels, promoting the rapid development of intelligent operation and maintenance technologies such as drones. In order to solve the problem of high labor cost and low efficiency in identifying defects and hidden dangers in pictures of transmission and distribution lines taken by a large number of drones, artificial intelligence technology is widely used in the energy industry. This competition aims to automatically find hidden dangers, accurately locate them, return detection results, and visualize them based on images captured by drones and deep learning technology.
This competition aims to promote the development of technological innovation, improve the efficiency and accuracy of power system monitoring in the Guangdong-Hong Kong-Macao Greater Bay Area, reduce human errors and risks, and improve the production safety and stability of the power system. The difficulty faced by the competition is that power transmission channel detection has complex scenes and there are many interference factors, such as weather changes, background environment, equipment performance, light, etc., which have a greater impact on image quality. In addition, different models, towers of different ages, equipment types and other factors will lead to different types and shapes of targets, which puts higher requirements on the recognition ability of the algorithm. The following is a schematic illustration:

02
—
Interpretation of competition questions
The technical direction of this competition is computer vision, mainly target detection technology. The hidden dangers in the transmission channel in this competition mainly refer to bird's nests and foreign objects in wires (balloons, kites, garbage, etc.). These foreign objects may cause short circuits, grounding and other faults in the transmission lines, leading to line outages and affecting the reliability and stability of power supply.
The difficulty of the competition questions is:
2.1 It is necessary to find pictures with hidden dangers, accurately locate the hidden dangers, and indicate the type of hidden dangers;
2.2 There are various forms of hidden dangers, which require high robustness of the algorithm, such as many styles of balloons and many types of garbage;
2.3 The relationship between foreign objects and the location of the equipment is diverse. For example, some kites do not directly contact the wires, but are connected to the wires through the kite wire.
Participants need to organize and clean the known data sets, build models, implement target detection functions, and output the results to the specified path in the specified format. The following is a schematic illustration of a complex scenario:

This competition question calculates F1-Score based on the test results provided by the participating teams. The detailed calculation formula is:
Precision: that is, the proportion of true examples (TP) to all positive examples (TP+FP) classified as positive. The formula is: Precision = TP / (TP + FP);
Recall rate Recall: the proportion of true examples (TP) to all true positive examples (TP+FN), the formula is: Recall = TP / (TP + FN);
F1-Score: Combines Precision and Recall, the formula is: F1-Score = (2 * Precision * Recall) / (Precision + Recall).
03
—
Competition question data set
The data sets for this competition come from multiple sources and are captured using a variety of equipment such as high-definition cameras and ordinary cameras. The data comes from various types of transmission line equipment, with backgrounds including cities, rural areas, mountains, roads, farmland, etc. The data set contains 1,000 images of power transmission channels and is approximately 3GB in size. Participants can split the training set and verification set by themselves.
The types of targets in the data set include bird's nests, kites, balloons, and garbage. The pictures are in jpg format and the annotation files are in xml format. Each object in the dataset is annotated with professionally accurate bounding boxes and categories. The unique advantages of the data set are: wide range of data sources, large quantity, clear categories, and accurate bounding box annotation. These characteristics make this data set suitable for the development and application of hidden target detection algorithms in complex scenarios. At the same time, the amount of data is large enough to effectively improve the robustness and generalization performance of the algorithm, thereby achieving better application results. Participants can train and test algorithms based on this data set, and design algorithms based on the unique characteristics of the data set in order to achieve better detection results and performance.
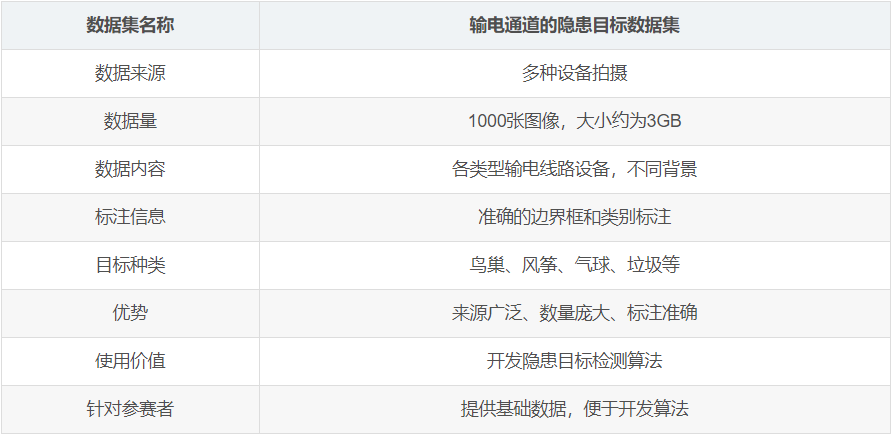
The specific format of the data set is described as follows:
File name description: The image files in the data set have ".jpg" as the suffix, and the file has the same name, but the suffix is ".xml";
File encoding instructions: Annotation files are encoded in UTF-8;
Data format description in the file: The annotation file is in XML format, and the format is as follows:
<?xml version="1.0" encoding="utf-8"?>
<annotation>
<filename> 0000001.jpg</filename>
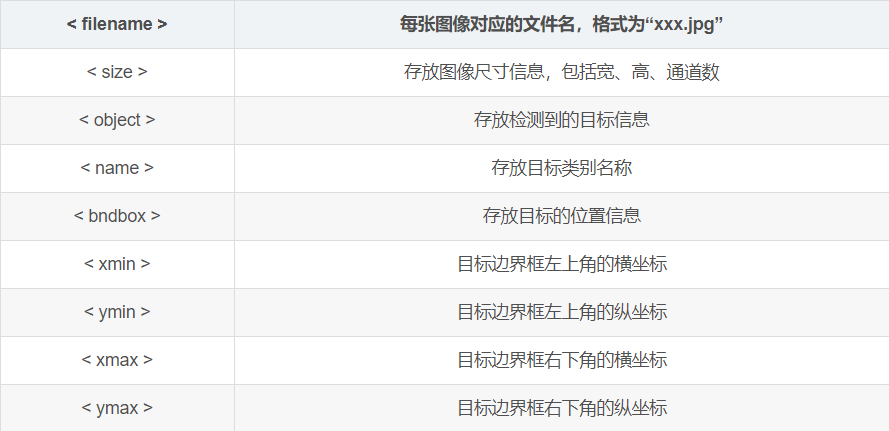
<size>
<width>1080</width>
<height>1080</height>
<depth>3</depth>
</size>
<object>
<name>balloon</name>
<bndbox>
<xmin>100</xmin>
<ymin>200</ymin>
<xmax>300</xmax>
<ymax>400</ymax>
</bndbox>
</object>
<object>
<name>trash</name>
<bndbox>
<xmin>700</xmin>
<ymin>500</ymin>
<xmax>800</xmax>
<ymax>700</ymax>
</bndbox>
</object>
</annotation>
The meaning of each field in the annotation file:
04
—
References
Text information:
YOLOv5 tutorial from source code download to running nanny level
https://blog.csdn.net/weixin_39424706/article/details/128152481
Video material:
Artificial Intelligence: Models and Algorithms Deep Learning and Its Applications
https://www.icourse163.org/course/FUDAN-1205806833?from=searchPage&outVendor=zw_mooc_pcssjg_
Live replay of the competition briefing session:
Live replay of competition question briefing session
https://aistudio.baidu.com/aistudio/education/lessonvideo/4485650
05
—
Conclusion
The above is all the contents of the Guangzhou·Pazhou Algorithm Competition-Transmission Channel Hidden Danger Object Detection Algorithm. The label of this competition question is target visual prediction, and the competition time is 2023/04/25-2023/09/30. Interested young knights can follow the progress of the subsequent competition, or use the data set provided by this competition question to develop algorithms and iterative improvements.
Transmission channel hidden danger target detection algorithm baseline
https://blog.csdn.net/m0_63642362/article/details/130596222