Start the drone
question
- File contains vulnerability
- PHP pseudo-protocol
Problem solving process
Click "tips"
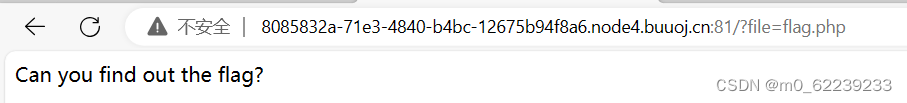
The first step - view the URL address and page source code
知识点:File contains vulnerability
According to ?file=flag.php we can infer that there is a file inclusion vulnerability.
The analysis is as follows: The remote PHP file is included in the URL address here, which means that the attacker can pass in arbitrary code.
F12 View page source code, no flag found.
But the file name here is flag.php. It is guessed that the flag is most likely in the source code of the flag.php file.
We can view the source code of flag.php through the PHP pseudo-protocol.
The suffix of PHP files is ".php" (PHP files can contain text, HTML, CSS and PHP code)
Step 2 - Construct the payload
php://filter can obtain the source code of the specified file. So we use php://filter to construct the payload:
格式:php://filter/convert.base64-encode/resource=文件路径
构造payload:
?file=php://filter/convert.base64-encode/resource=flag.php
What this sentence means is that we use base64 encoding to read the source code of the file flag.php
So what needs to be base64 encoded?
Because when the php://filter stream is combined with the file inclusion function, the php://filter stream will be executed as a php file. So we generally base64 encode it to prevent its execution and read the file source code.
If it is passed in without base64 encoding, flag.php will be executed directly, and we will not be able to see the contents of the file.
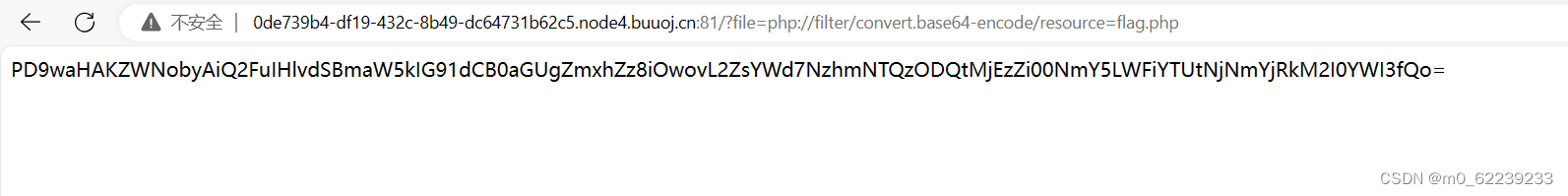
At this time, the page will display the base64-encoded content of the source file flag.php.
Base64 is a common encoding used to convert binary data into printable ASCII characters.
Step 3 - Base64 decode the obtained characters
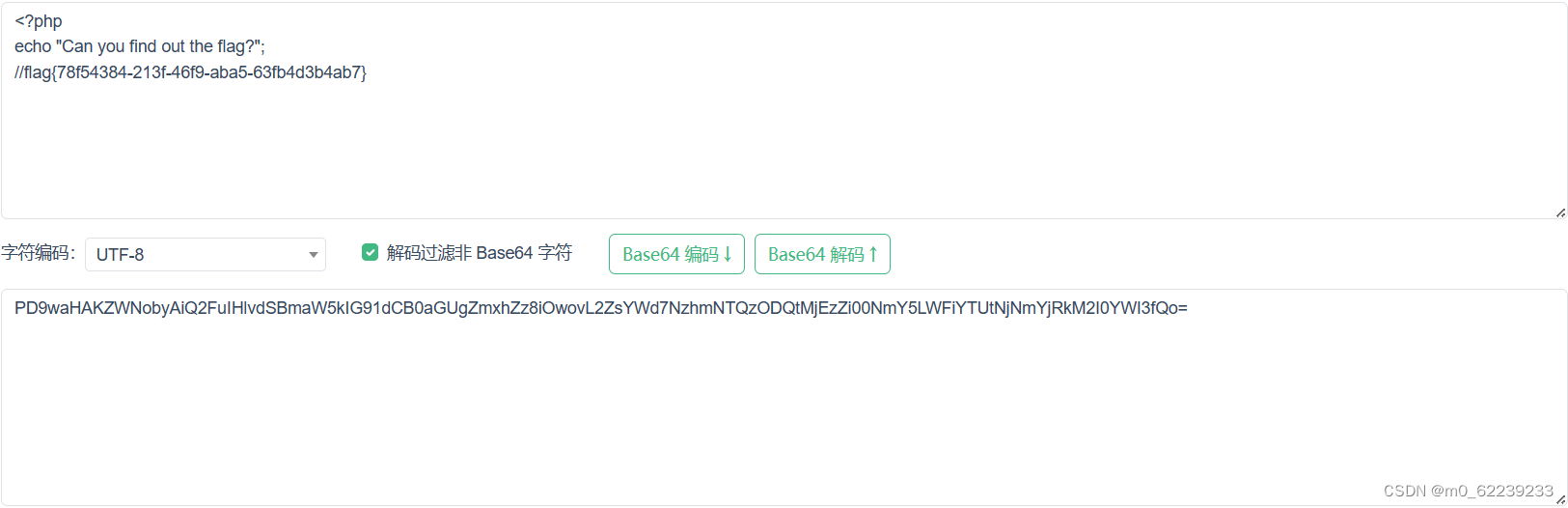
Get flag successfully
flag{78f54384-213f-46f9-aba5-63fb4d3b4ab7}
Summary of ideas
Question type:
- File contains vulnerability
Steps to do the question:
- A file inclusion vulnerability was found by analyzing the URL address.
- Use php://filter to construct the payload (base64 encoding) and obtain the encoded content of the file source code.
- Perform base64 decoding to obtain file source code