Why should SSH login with empty password be prohibited?
The reason why SSH login with empty password is prohibited is for security reasons. If SSH logins with empty passwords are allowed, then anyone can gain access to the system by trying to log in to the system with an empty password, which is obviously very unsafe.
In addition, accounts with empty passwords may also be exploited by malicious users, such as by injecting malicious code, performing illegal operations, etc., thus posing security threats to the system.
Therefore, prohibiting SSH empty password login can protect the security of the system and avoid unauthorized access and potential malicious attacks.
Risk description
Detection type: Prohibit SSH empty password login
Risk level: High risk
Configuration modification
To disable SSH login with empty password, you can follow these steps:
-
Open a terminal or SSH client and log in to the SSH server as root or a user with administrator privileges.
-
Navigate to the SSH configuration file directory. On most Linux systems, the default SSH configuration file directory is
/etc/ssh/
cd /etc/ssh
- Edit the sshd_config file, we can open the file using any text editor such as vi or nano.
sudo vi /etc/ssh/sshd_config
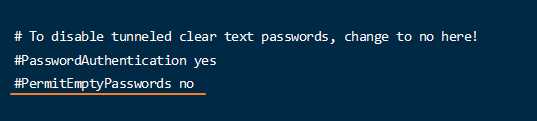
- Find and modify
PermitEmptyPasswordsoptions in the file. By default, the value of this option isyes, which allows empty password logins. Remove the comment character#in front of it and change the value tono, save and close the file.
One-click modification command
sed -i 's/PermitEmptyPasswords yes/PermitEmptyPasswords no/g' /etc/ssh/sshd_config
- Restart the SSH service for the changes to take effect. We can restart the SSH service using the following command:
service ssh restart
# 或者
systemctl restart sshd