gogo
introduce
A highly controllable and scalable automation engine for red teams. The characteristics are as follows:
```Free port configuration 支持主动/主动指纹识别to extract key information, such as titles, certificates and custom extraction information. Regular and 支持nuclei poc,poc目录:https://chainreactors.github.io/wiki/gogo/detail/#_6harmless scanning. Each added POC has been manually reviewed. 可控的启发式扫描Super performance, fastest speed, and takes up very little space. Memory and CPU. 最小发包原则,解决少地发包获取最多的信息Supports DSL. You can customize your own gogo through simple configuration. It 完善输出与输出设计almost does not rely on third-party libraries. It is written purely in native go. You can also use the complete vulnerability/fingerprint identification function on Windows 2003.
Effect, a simple task
gogo -i 81.68.175.32/28 -p top2 [*] Current goroutines: 1000, Version Level: 0,Exploit Target: none, PortSpray: false ,2022-07-07 07:07.07[ ] Start task 81.68.175.32/28 ,total ports: 100 , mod: default ,2022-07-07 07:07.07 [*] ports: 80,81,82,83,84,85,86,87,88,89,90,443,1080,2000,2001,3000,3001,4443,4430,5000,5001,5601,6000,6001,6002,6003,7000,7001,7002,7003,9000,9001,9002,9003,8080,8081,8082,8083,8084,8085,8086,8087,8088,8089,8090,8000,8001,8002,8003,8004,8005,8006,8007,8008,8009,8010,8011,8012,8013,8014,8015,8016,8017,8018,8019,8020,6443,8443,9443,8787,7080,8070,7070,7443,9080,9081,9082,9083,5555,6666,7777,9999,6868,8888,8889,9090,9091,8091,8099,8763,8848,8161,8060,8899,800,801,888,10000,10001,10080 ,2022-07-07 07:07.07[ ] Scan task time is about 8 seconds ,2022- 07-07 07:07.07 [+] http://81.68.175.33:80 nginx/1.16.0 nginx bd37 [200] HTTP/1.1 200[+] http://81.68.175.32:80 nginx/1.18.0 (Ubuntu) nginx 8849 [200] Welcome to nginx! [+] http://81.68.175.34:80 nginx 宝塔||nginx f0fa [200] 没有找到站点[+] http://81.68.175.34:8888 nginx nginx d41d [403] HTTP/1.1 403 [+] http://81.68.175.34:3001 nginx webpack||nginx 4a9b [200] shop_mall[+] http://81.68.175.37:80 Microsoft-IIS/10.0 iis10 c80f [200] HTTP/1.1 200 c0f6 [200] Security entrance verification failed [*] Alive sum: 5, Target sum : 1594 ,2022-07-07 07:07.07[*] Totally run: 4.0441884s ,2022-07-07 07:07.07
注意事项
(Important) Excessive concurrency may cause damage to routing switch equipment. For example, some home routing equipment may crash, restart, overheat, etc. if the concurrency is too high. Therefore, in the scenario of external network scanning, it is recommended to use it on Alibaba Cloud, Huawei Cloud and other VPS. If scanning foreign assets, it is recommended to use it on foreign VPS. If the network device performs poorly for local use, it will cause a lot of packet loss. If network scanning is required, the configuration quantity needs to be adjusted according to the actual situation. 如果使用中发现疯狂报错,很大概率是io问题(例如多次扫描后io没有被正确释放,或者fightproxifier以及类似代理工具使用报错),可以通过重启电脑,或者虚拟机中使用,关闭代理工具解决.如果仍无法解决请联系我们。It should also be noted that although the upx-compressed version is small in size, it may be soft-killed and may not run on some machines. 一般情况下无法在代理环境中使用,除非使用-t参数指定较低的速率(默认梯度为4000)。gogo itself is not offensive in any way and cannot exploit any vulnerabilities. ``Be sure to obtain authorization before using gogo. Gogo combats all illegal hacking activities.
Project address: https://github.com/chainreactors/gogo
How to learn hacking & network security
As long as you like my article today, my private network security learning materials will be shared with you for free. Come and see what is available.
1. Learning roadmap
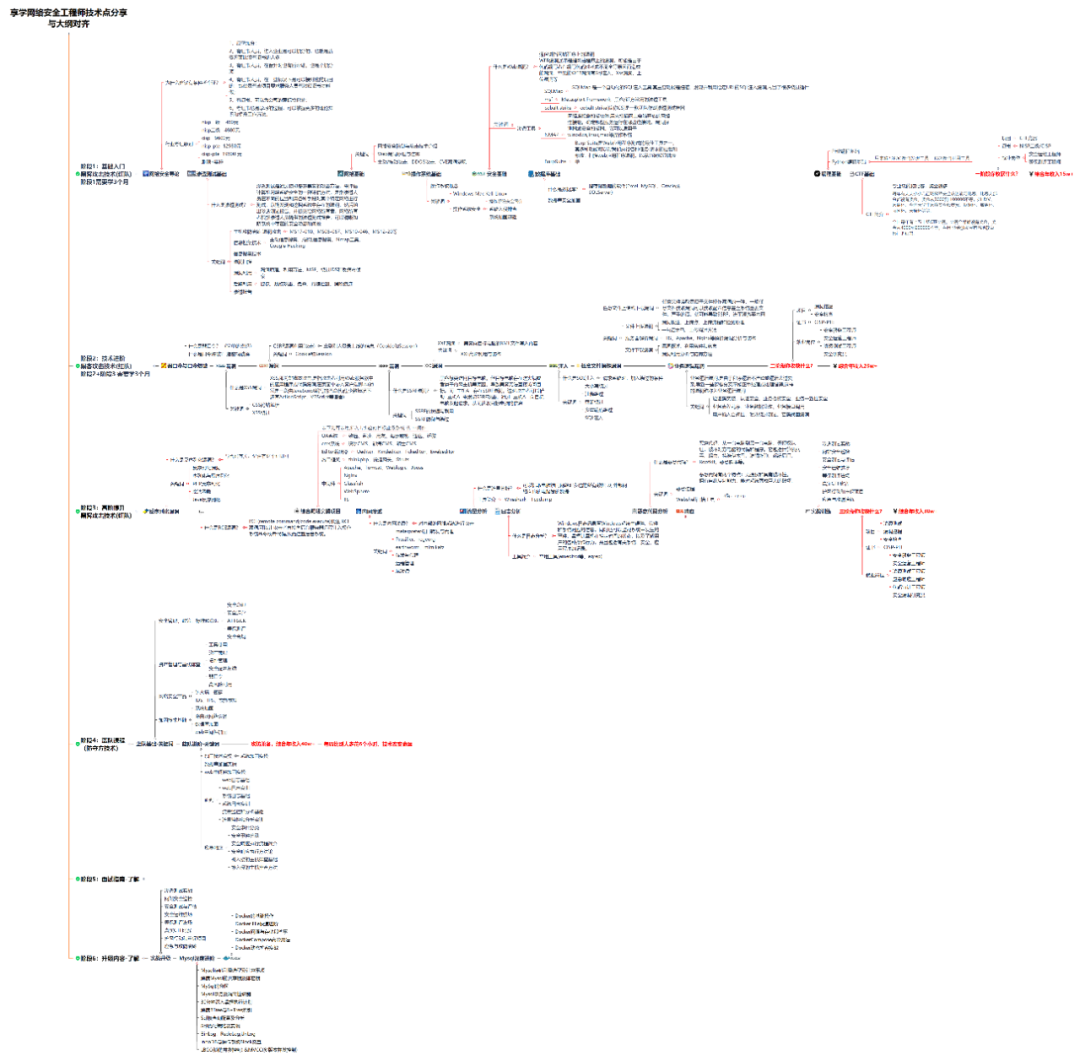
There are a lot of things to learn about attack and defense. I have written down the specific things you need to learn in the road map above. If you can complete them, you will have no problem getting a job or taking on a private job.
2. Video tutorial
Although there are many learning resources on the Internet, they are basically incomplete. This is an Internet security video tutorial I recorded myself. I have accompanying video explanations for every knowledge point in the roadmap above.
The content covers the study of network security laws, network security operations and other security assessments, penetration testing basics, detailed explanations of vulnerabilities, basic computer knowledge, etc. They are all must-know learning contents for getting started with network security.
(They are all packaged into one piece and cannot be expanded one by one. There are more than 300 episodes in total)
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
3. Technical documents and e-books
I also compiled the technical documents myself, including my experience and technical points in participating in large-scale network security operations, CTF, and digging SRC vulnerabilities. There are more than 200 e-books. Due to the sensitivity of the content, I will not display them one by one.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
4. Toolkit, interview questions and source code
"If you want to do your job well, you must first sharpen your tools." I have summarized dozens of the most popular hacking tools for everyone. The scope of coverage mainly focuses on information collection, Android hacking tools, automation tools, phishing, etc. Interested students should not miss it.
There is also the case source code and corresponding toolkit mentioned in my video, which you can take away if needed.
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
Finally, here are the interview questions about network security that I have compiled over the past few years. If you are looking for a job in network security, they will definitely help you a lot.
These questions are often encountered when interviewing Sangfor, Qi Anxin, Tencent or other major companies. If you have good questions or good insights, please share them.
Reference analysis: Sangfor official website, Qi’anxin official website, Freebuf, csdn, etc.
Content features: Clear organization and graphical representation to make it easier to understand.
Content summary: Including intranet, operating system, protocol, penetration testing, security service, vulnerability, injection, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logical vulnerability, tools, SQLmap, NMAP, BP, MSF…
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.